 Education
Education
DNSSEC (Domain Name System Security Extensions) has been around since the mid-2000s and technically works well: it cryptographically signs DNS records so resolvers can verify that the answer they got really came from the authoritative server and wasn’t tampered with. Despite that, adoption and real-world deployment remain surprisingly low outside a few countries (notably .se, .nl, .cz and some others). Here’s why it never took off broadly, and why the rise of DNS over HTTPS (DoH) has made many people conclude that pushing DNSSEC further isn’t worth the effort anymore.
Why DNSSEC never achieved widespread adoption
- Complexity and operational brittleness
- Key rollovers (ZSK/KSK) are painful. A single mistake (expired key, wrong timing, bad DS record in parent zone) causes the entire domain to go dark for all validating resolvers. High-profile outages (e.g., .gov incidents, large registrars breaking zones) scared people off.
- Most DNS operators are small ISPs, enterprises, or registrars who don’t have crypto/DNS experts on staff.
- Almost no client-side validation for years
- Until ~2018–2019, almost nothing on the client actually checked DNSSEC signatures:
- Windows didn’t validate by default until very recently.
- macOS/iOS never did (Apple explicitly refused).
- Android never did.
- Browsers never did.
- The only serious validating resolvers were Cloudflare 1.1.1.1 (2018), Quad9 (2018), and a few ISPs (mostly in Europe). For the average user, DNSSEC provided zero observable benefit.
- No protection against the real threat most people care about
- DNSSEC only guarantees authenticity and integrity of records. It does not provide confidentiality. A passive attacker (or your ISP, coffee-shop Wi-Fi, etc.) can still see every domain you look up.
- The big visible DNS attacks people worried about (Kaminsky-style cache poisoning) became much harder anyway after widespread source-port randomization and later DNS cookies.
- Chicken-and-egg problem with incentives
- Registrars/registries had to sign zones → extra cost and risk.
- Resolvers had to turn on validation → extra CPU and risk of breaking users.
- End users got no visible benefit, so nobody pushed hard.
- Some TLDs still aren’t signed or have broken chains
Even in 2025, many country-code TLDs and some generic ones have incomplete or broken trust chains, which further erodes confidence.
Why DoH (and DoT) made DNSSEC largely irrelevant for most practical purposes
DNS over HTTPS (and DNS over TLS) flipped the game in 2018–2020:
- Confidentiality became the #1 user demand
People suddenly cared a lot more about stopping their ISP or local network from seeing their DNS traffic than about cryptographic proof that “google.com really resolves to a Google IP”. - DoH centralized resolution
Firefox (2019) and later Chrome/Edge started shipping DoH by default to Cloudflare or NextDNS. Those public resolvers do validate DNSSEC, so the average user now gets DNSSEC protection indirectly — but they get it whether the zone is signed or not (the resolver just logs a validation failure and serves the data anyway in most cases). - DoH + opportunistic encryption is “good enough” for almost everyone
- Encrypted traffic: yes ✓
- Integrity/authenticity: mostly (via the big public resolver’s validation) ✓
- No key-management headaches for millions of domain owners: ✓
- The remaining DNSSEC-only benefits are niche
The only things DNSSEC still gives you that DoH doesn’t are:
- End-to-end validation without trusting a third-party resolver (e.g., Cloudflare).
- Protection against a malicious or compromised public resolver deliberately lying.
Most users and even most enterprises decided they’re fine trusting Cloudflare/Google/Quad9.
- Regulatory and political pushback against DoH actually helped DNSSEC’s irrelevance
Some governments (UK, Germany, etc.) tried to block or discourage DoH because it broke their filtering. That made centralized DoH even more politically charged, but it also meant DNSSEC (which doesn’t hide anything) wasn’t going to solve the political problems anyone cared about.
Bottom line in 2025
- DNSSEC is still useful in specific high-security contexts (banks, some governments, internal enterprise networks) where you run your own validating resolver and want cryptographic proof without trusting a public DoH provider.
- For the general Internet, DoH (+ optional DNSSEC validation at the big resolvers) solved 95 % of the perceived DNS security problem with far less operational pain.
- As a result, very few new zones are bothering to sign, key rollovers are increasingly neglected, and the whole ecosystem is slowly bit-rotting outside the few countries that signed early and automated everything.
So yes — DoH didn’t kill DNSSEC technically, but it killed the urgency and the business/social case for universal DNSSEC deployment. Most people now get “good enough” security without it, and the cost/benefit ratio for DNSSEC flipped negative for almost everyone else.
A r3b00t’s View
Wow ok, I used GROK for this and actually I quite like the result. A one shot FUD bust whilst I’m drinking a cup of tea!
So, DNSSEC as you can see is something that some FUD Cyber Charlatans may use to try and sell you crappy vulnerability scans, but you probably outside of very niche scenarios here me talk about DNSSEC (other than to fight the FUD)
Security solutions in the world are varied, if I had to give DNSSEC a rating, I’d give it 2/10. DoH I’d give 8/10 (or something like that).
If someone is telling you your organisation’s is at risk from ransomware from a lack of DNSSEC, I would suggest this is a major red flag and the person saying this is either: a summer, a fraudster or is seriously misinformed/mentally unwell etc.
If you see someone showing screenshots like this, avoid them like the plague!
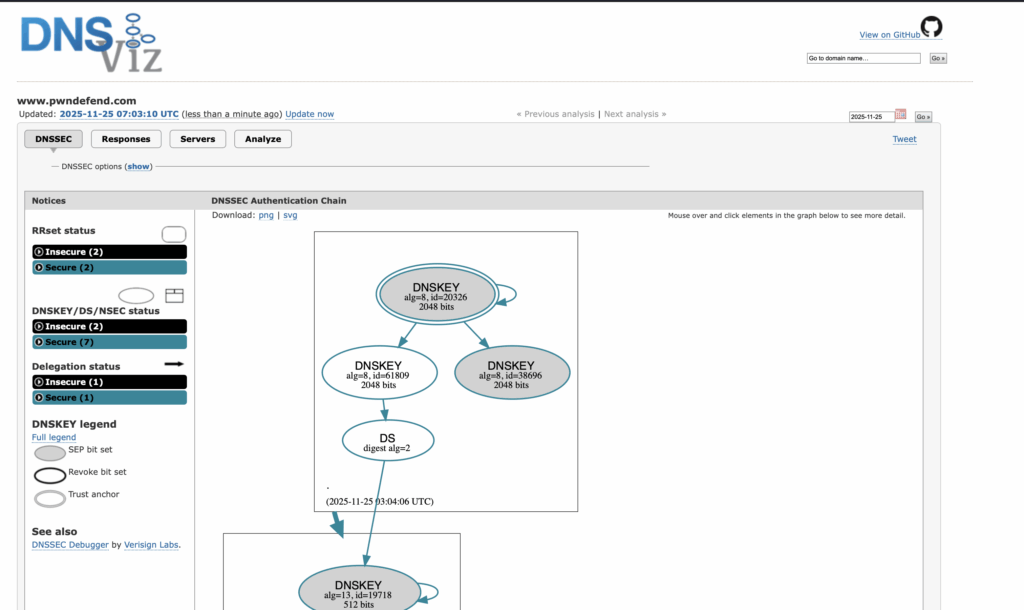
I don’t have DNSSEC configured, It’s not something I’m bothered about, the only authentication service on my domain is my WordPress site (this site) and that has MFA. The kill chain required to leverage DNS requires an attacker to MITM one person (me) in the entire world, hope I don’t use DoH (I do), hope my domain isn’t cached etc. and then do a reverse proxy, hope my browser doesn’t do an HSTS check (cached as I’m not in the pre-load list) and then…. Pwn all the things! (see a ridiculous scenario).
There you go, DNSSEC, can be useful in some scenarios, but largely, it’s not really a ‘thing’ to worry about outside of high threat/assurance scenarios (like a all things in security it depends). Most orgs/people are getting pwn3d by scammers and having crap passwords, there’s way more important (IMHO) plus as the blog says, DoH is actually getting adoptions vs DNSSEC which is largely a bit dead for general purposes. Remember you should be making informed risk decisions, not just doing things because someone on LinkedIn said so!








