Fortiweb Vulnerabilities 2025
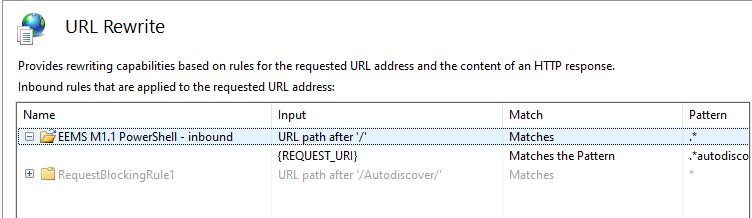
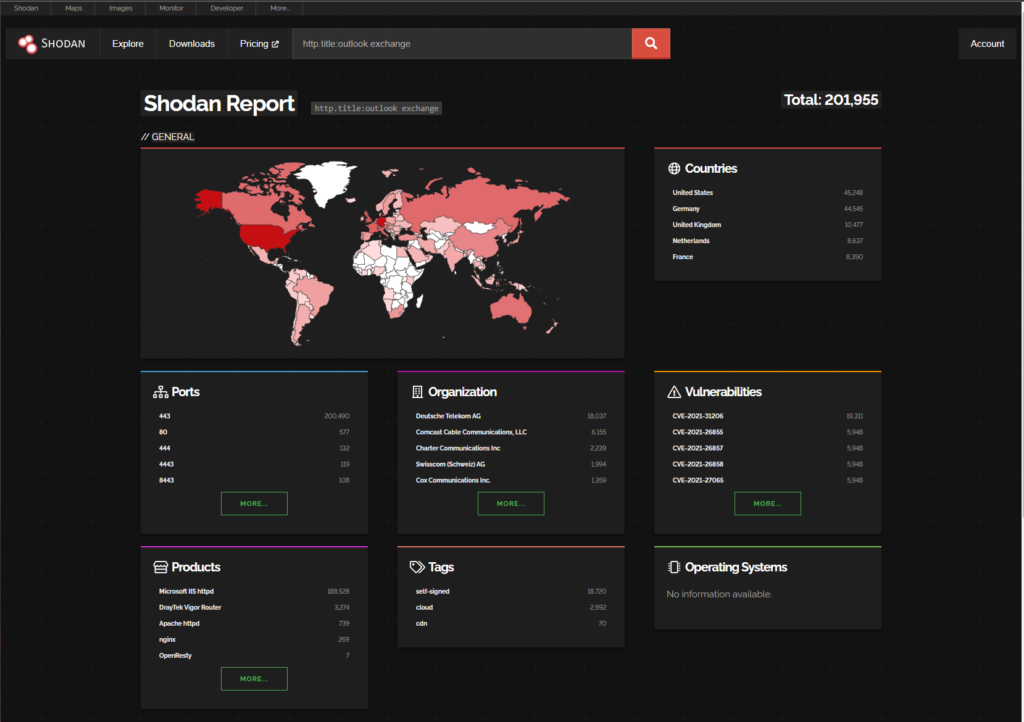
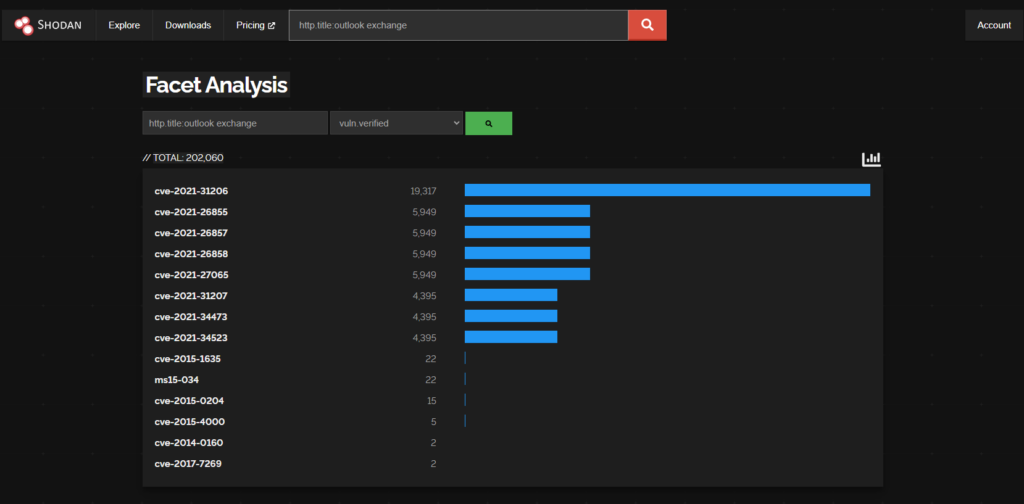
Given the recent discovery of a critical vulnerability (CVE-2025-64446) in the Fortiweb appliances (exploitable via the management interfaces) I thought I would have a look at what other vulnerabilities have been discovered/published and what Proof of Concept (PoC) exploits exist in 2025.
Read more “Fortiweb Vulnerabilities 2025”