Hunting for common Active Directory Domain Services Exploitations
Ok this morning I woke up really really early! I then went on a bit of a KQL thread on twitter, and then IRL work destroyed my plans to play in the lab. However I’m publishing this in its current state [use at own risk etc.] because I think it might help people! So let’s get to it:
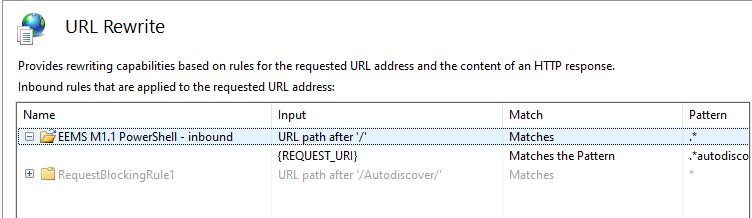
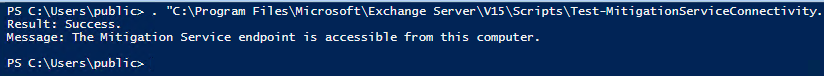
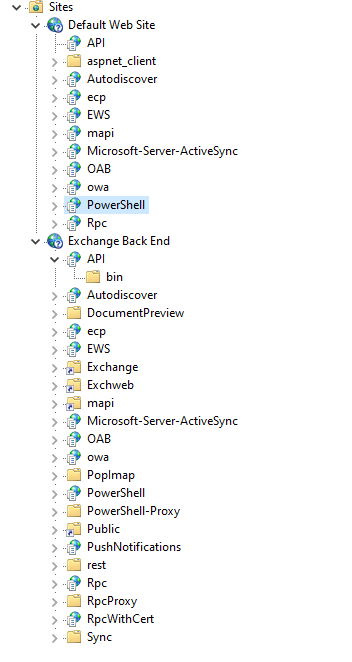
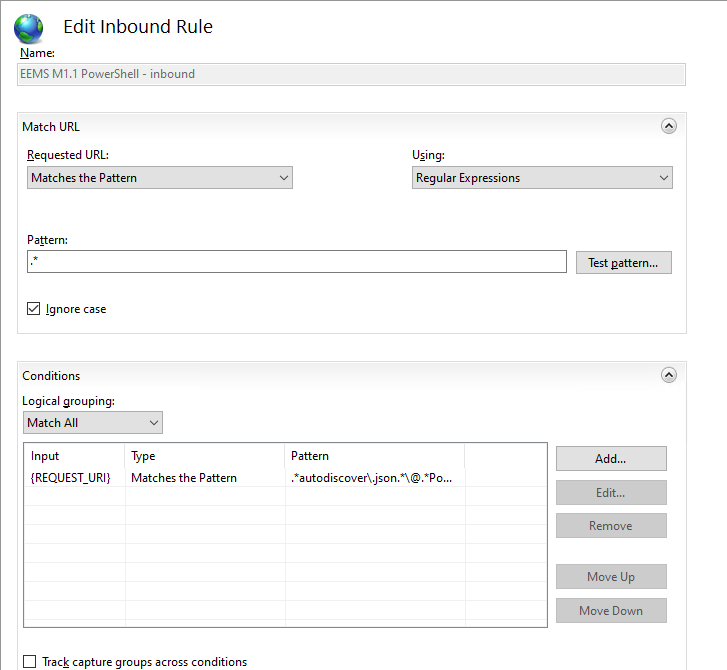
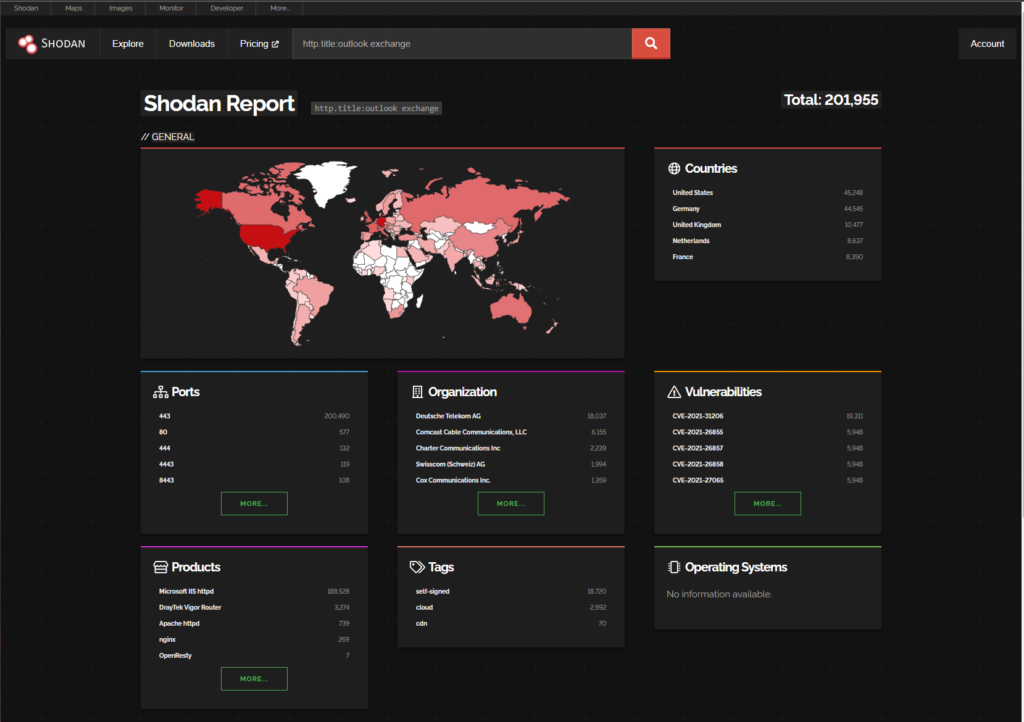
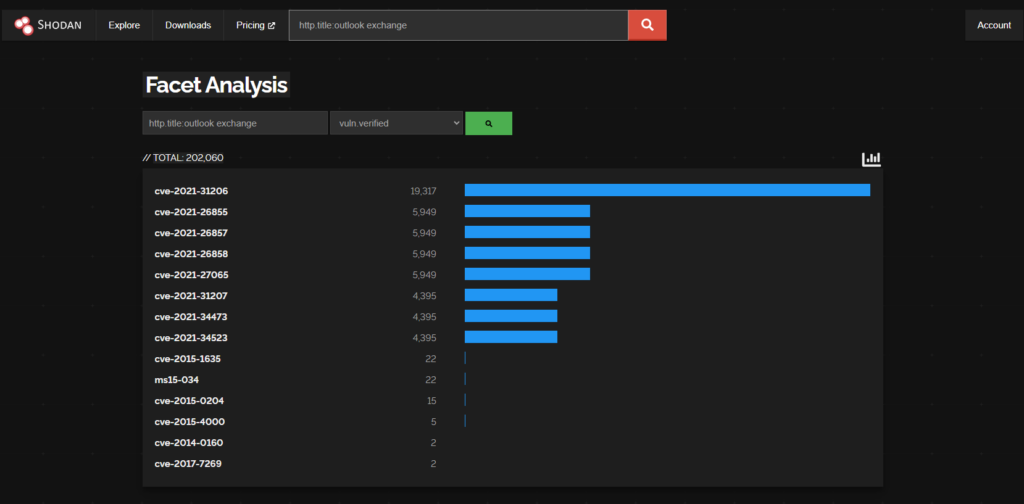
These queries can help you identify 3 common active directory attack techniques from logs on a domain controller (this does not rely on ADCS logs etc.)
Read more “Hunting for common Active Directory Domain Services Exploitations”