 Defense
Defense
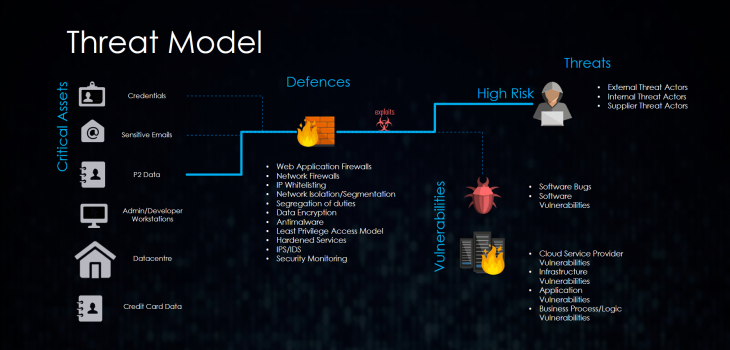
Threat Modelling 101
What is a threat?
https://csrc.nist.gov/glossary/term/threat
According to those clever people at NIST it is:
“Any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, or individuals through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service. Also, the potential for a threat-source to successfully exploit a particular information system vulnerability.” Read more “Threat Modelling 101”