 Defense
Defense
What is a threat?
https://csrc.nist.gov/glossary/term/threat
According to those clever people at NIST it is:
“Any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, or individuals through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service. Also, the potential for a threat-source to successfully exploit a particular information system vulnerability.”
What is a model?
https://www.merriam-webster.com/dictionary/model
Well, I never thought I’d be thinking about Zoolander and threat modelling but then again. you remember the fuel station scene, right?
Combine the two
Ta Da – we have a threat model! My jokes are on fire today. Ok so back to business, threat modelling is the process of understanding our threats and the routes they make take or leverage against us.
Formal Threat Modelling Methods
- Process for Attack Simulation and Threat Analysis (P.A.S.T.A)
- STRIDE
- TRIKE
- OCTAVE
- DREAD
- And more
These are all great models, some of which can be taken to a very detailed level, so make sure your threat modelling process and framework is supporting your business objectives, is relevant to the audience and supports the ultimate objective of securing your organisation and its systems, it’s about that more than the modelling process.
There’s loads of tools and frameworks out there:
https://threatdragon.org/login
https://github.com/mike-goodwin/owasp-threat-dragon-desktop/releases
Basic View
- What do you have?
- What is is worth to you?
- Who might try to tamper, steal, abuse or deny access to this?
- What vulnerabilities do or might exist?
- Who has access to this?
- What controls or countermeasures can be put in place?
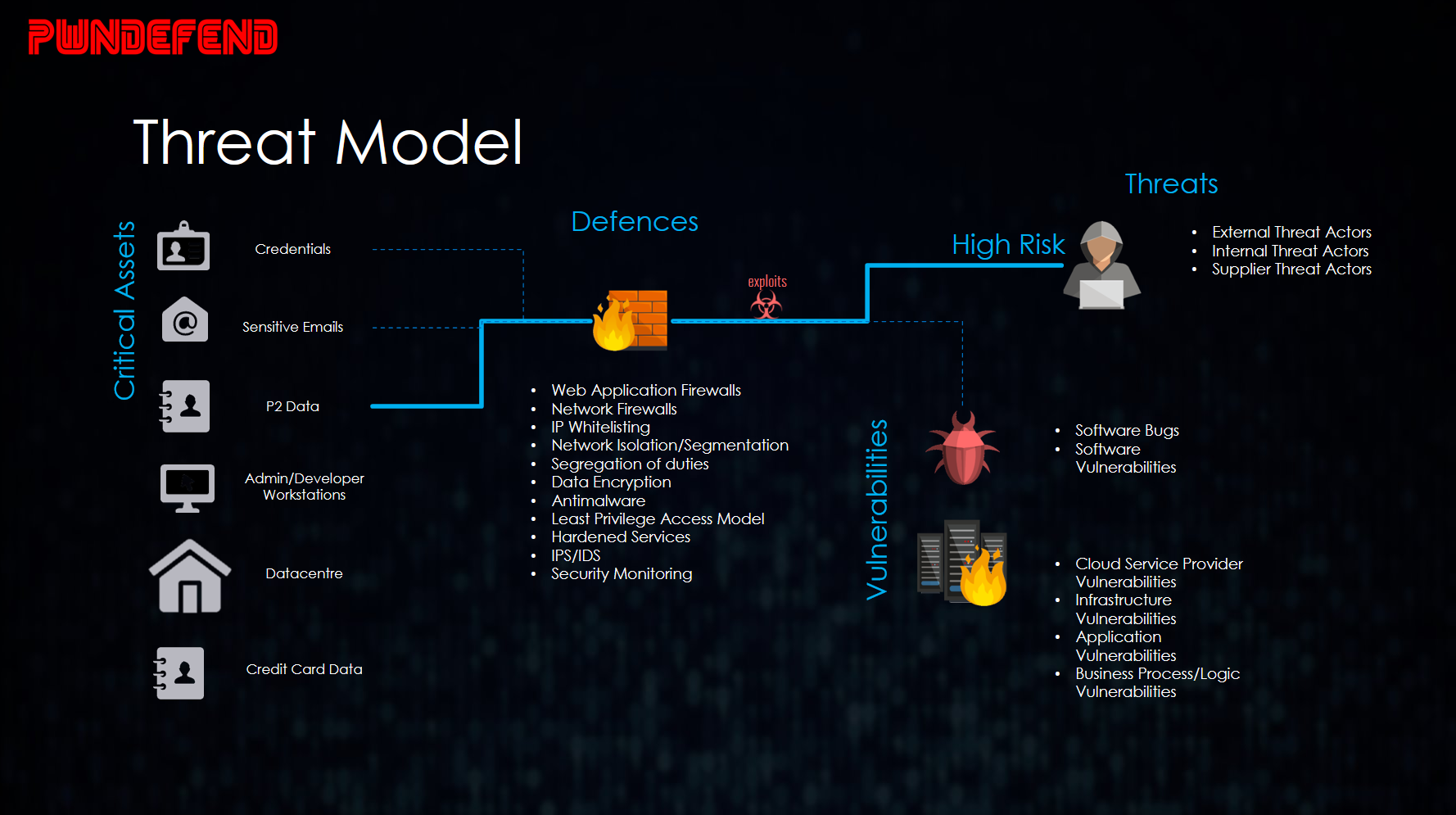
A picture paints a thousand words
I myself like to create threat profiles, create attack maps, and then create threat modelling pictures, charts, and spreadsheets. I also like to do research against the industry I’m working with to ensure my understanding of the threats is relevant and abstracted to the right level.
A common challenge I see with organisations is that when the security maturity and experience levels aren’t high keeping people’s attention and focus is a challenge. So again, I try and use appropriate levels of theory with practical application. You can always develop something further if required. That being said, it depends on the context, if you want to defend against nation state threat actors you probably want to be going for a detailed approach off the bat, however remember, complexity can be the enemy so right size your efforts.









