 Threat Intel
Threat Intel
What do we know?
Adversary: Unknown, likely Criminal Actor/s
Initial Access Vector: Unknown/Unproven
Impact: ~3K+ Hosts have had Remote Code Execute and their ESXi logon pages changed (plus had encryption routines run to encrypt virtual machines, with varying success). A Second encryption routine has been deployed to some hosts; the threat actor is expanding/changing capabilities.
Risk: Further impact, Additional Threat Actors Exploit the vulnerability
What should people do?
- Review for unauthorized access.
- If found, isolate, contain and eradicate threat. There is a link to CISA guidance/script in references
- Patch, harden and reduce attack surface of ESXi infrastructure.
References
https://www.greynoise.io/blog/exploit-vector-analysis-of-emerging-esxiargs-ransomware
https://github.com/cisagov/ESXiArgs-Recover
Potential Attack Surface
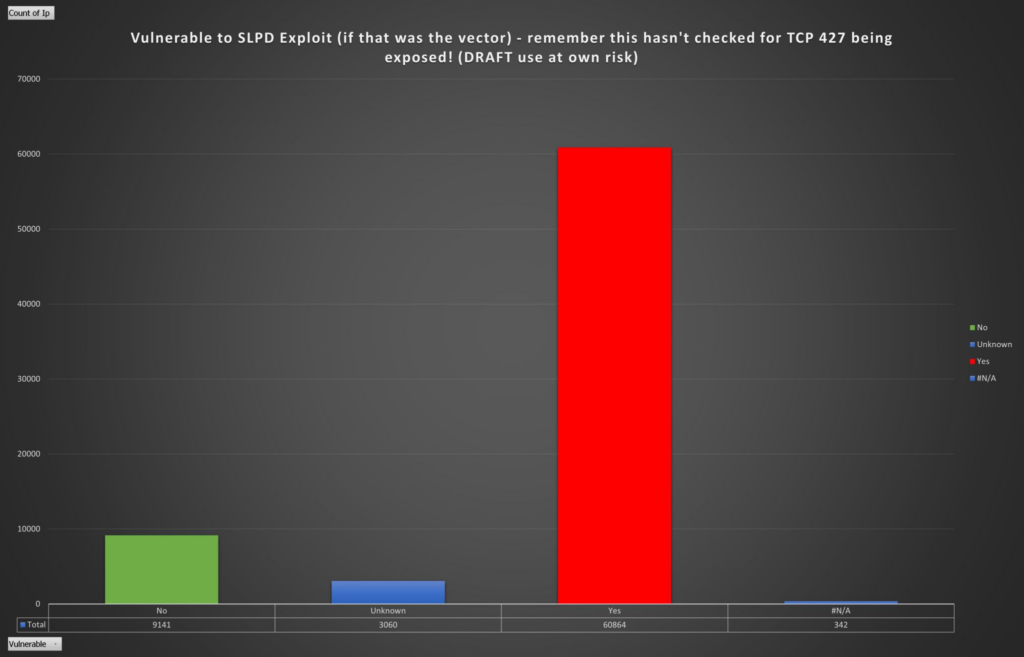
To generate a view on potential risk and attack surface, I’ve taken a set of data from Shodan. I’ve enumerated each IP and each specific build string, I’ve then categorized these against an excel sheet I made from the build data from VMware. There will be some variables here, and this doesn’t cover off port exposures (at this time) but it does show there are a lot of builds that are not “up to date” in the wild and exposed to the internet (what about inside networks?)








