 Threat Intel
Threat Intel
Thousands of ESXi hosts around (some of the) globe have been encrypted by cyber criminals. This post is a fast publish showing some of what has occurred, it’s impact and now includes limited remedial advice.
If you have been affected by this ransomware event there is an attempted recovery script by CISA
https://github.com/cisagov/ESXiArgs-Recover/blob/main/recover.sh
Situation
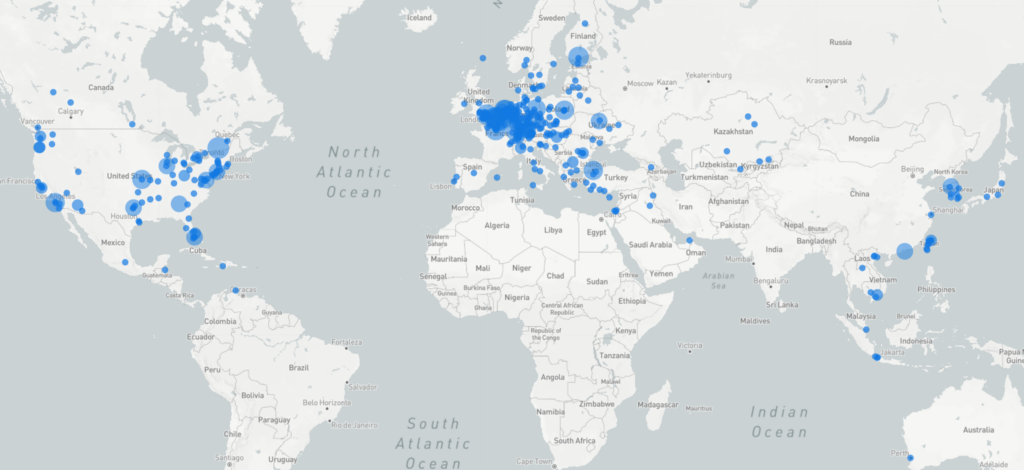
Thousands of hosts in Western countries have been ransomwared:
https://www.shodan.io/search/facet?query=http.title%3A%22How+to+Restore+Your+Files%22&facet=org

Initial Access Vector
Unknown but possibly exploiting OPENSLPD:
- CVE-2019-5544
- CVE-2020-3992
- CVE-2021-21974 (this is the one everyone is reporting but we haven’t seen forensic evidence of this)
https://www.cert.ssi.gouv.fr/alerte/CERTFR-2023-ALE-015/
Why don’t we know? well these hosts aren’t heavily monitored and logs/evidence of the OPENSLPD service being exploited seems to be on the LOW side. People are also (rightly) focusing on restoration of service vs forensic analysis at this stage.
Patient Zero
So at the weekend I found some entries going back to October but I woke up today to find this chap had found one back even further!
(nice work dude!)
We believe this host:
https://trends.shodan.io/search?query=title%3A%22How+to+Restore+Your+Files%22#facet/ip
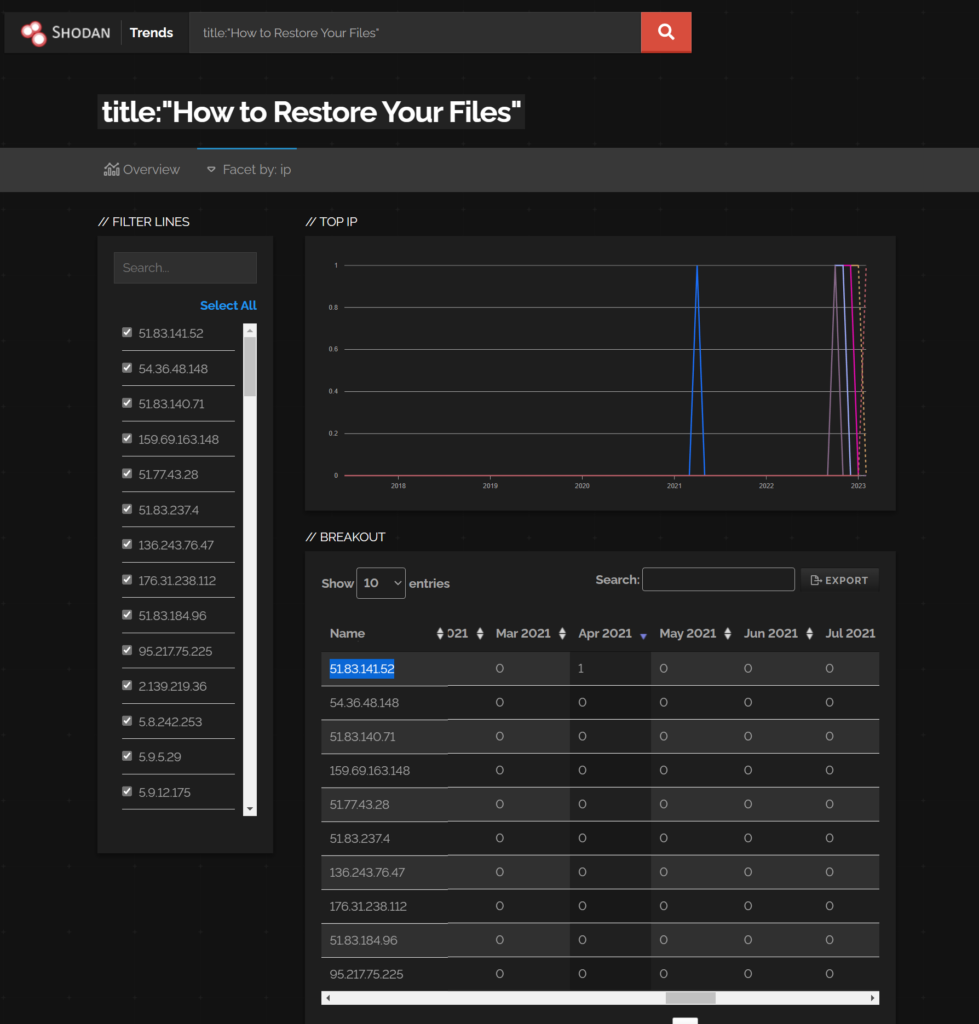
was the first host to have this chain tested on it.
https://trends.shodan.io/search?query=title%3A%22How+to+Restore+Your+Files%22&language=en#facet/ip
Threat Actor/s
Unknown but likely aligned or politically/physically in/adjacent to Russia/China/Iran/N. Korea/India/South America/Africa (this is a broad list of countries/regions that were not affected despite having vulnerable servers exposed)
Timeline
- 23rd February 2021 – VMWARE issues a patch for OPENSLPD – this states you must be NETWORK ADJACENT (this might be wrong!)
- April 2022 – A single host has been detected as being encrypted with what appears to be this ransom note
- October 2022 – A Backdoor was detected by Juniper
- October 2022 – A group of hosts were encrypted
- Friday 31/01/2023 ESXi hundreds/thousands of hosts started to display ransomware notes on the HTTPS service for ESXi and SSH MOTD
Payment Tracking
Each host has a unique BITCOIN. wallet address. At time of writing only .5 of a bitcoin is known (to me) to have been paid (the criminals) It’s now reported that ~ 50K USD has been paid
Response & Recovery
Response is complex, isolate, contain and eradicate is easy to say, sometimes harder to do given the number of variables. This post isn’t covering detailed ESXi recovery steps, Recovery may be simple, or it may be complex or you might not be able to (i mean paying is an option but a risky AF one)
You may be able to restore VMs by rebuilding VMDK descriptors…
You may find some useful info in the forums (be careful etc.)
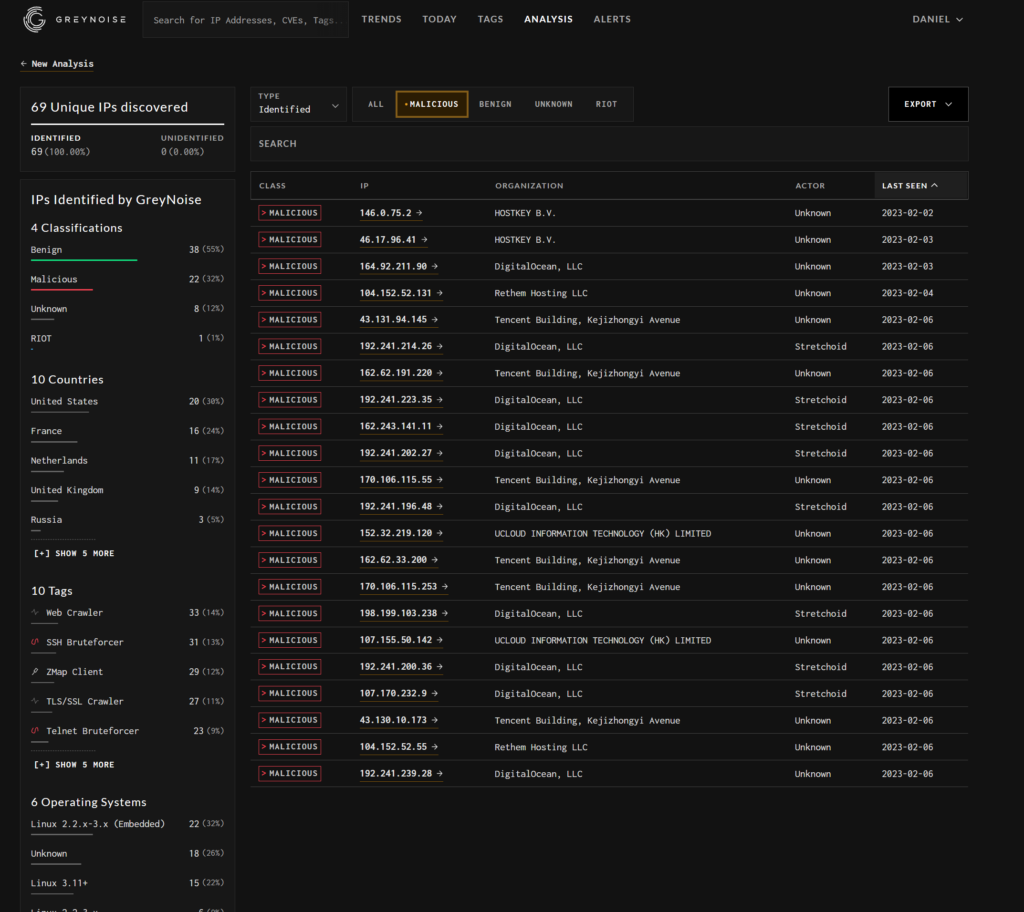
IP IOCs
This list is a subset from
https://github.com/fastfire/IoC_Attack_ESXi_Feb_2023/blob/main/ip.md
It has been enriched and had some of the “known good” IPs taken out
I think some IPs in here are not criminals but people doing mass scanning (researchers) but I can’t confirm this so I’ve left the list as is:
| 104.152.52.131 104.152.52.55 107.155.50.142 107.170.232.9 146.0.75.2 152.32.219.120 162.243.141.11 162.62.191.220 162.62.33.200 164.92.211.90 170.106.115.253 170.106.115.55 192.241.196.48 192.241.200.36 192.241.202.27 192.241.214.26 192.241.223.35 192.241.239.28 198.199.103.238 43.130.10.173 43.131.94.145 46.17.96.41 103.75.201.219 104.152.52.233 106.75.190.21 106.75.64.29 119.42.54.188 172.105.73.148 176.58.124.251 89.248.163.200 |
GreyNoise Enrichment
Ransom Note
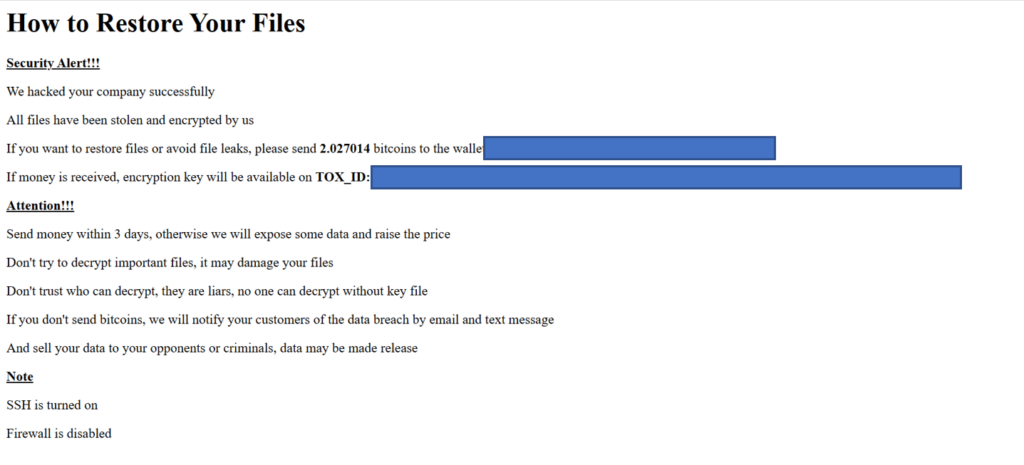
| How to Restore Your Files Security Alert!!! We hacked your company successfully All files have been stolen and encrypted by us If you want to restore files or avoid file leaks, please send 2.035639 bitcoins to the wallet {REDACTED} If money is received, encryption key will be available on TOX_ID: {REDACTED} Attention!!! Send money within 3 days, otherwise we will expose some data and raise the price Don’t try to decrypt important files, it may damage your files Don’t trust who can decrypt, they are liars, no one can decrypt without key file If you don’t send bitcoins, we will notify your customers of the data breach by email and text message And sell your data to your opponents or criminals, data may be made release Note SSH is turned on Firewall is disabled |
Mitigations
- Disable SLPD on ESXi
- Ensure you are running a supported and fully patched ESXi version
- Apply ingress filtering on all management services for the host/User a VPN etc.
References
https://github.com/fastfire/IoC_Attack_ESXi_Feb_2023
https://www.cert.ssi.gouv.fr/alerte/CERTFR-2023-ALE-015/
More to follow…
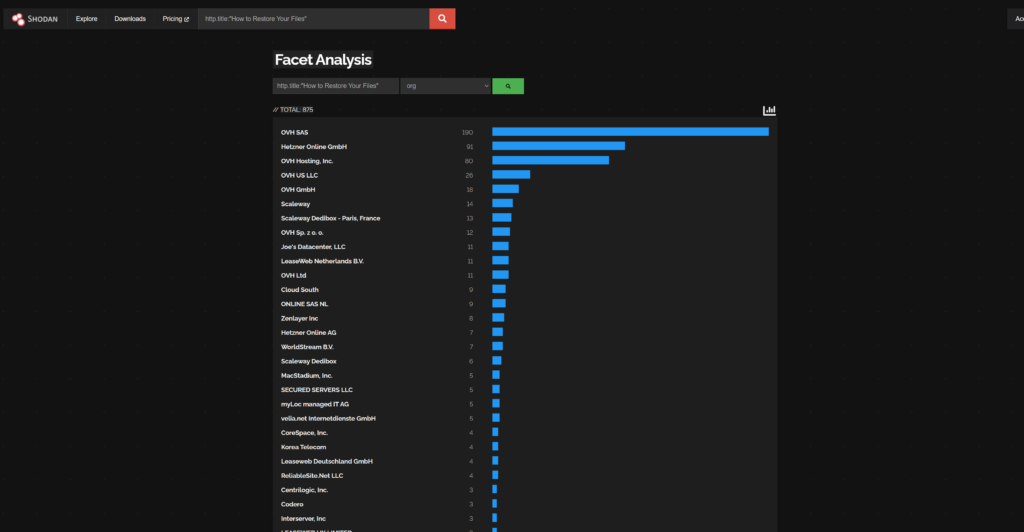
Orgs Affected (count of hosts by ORG name)
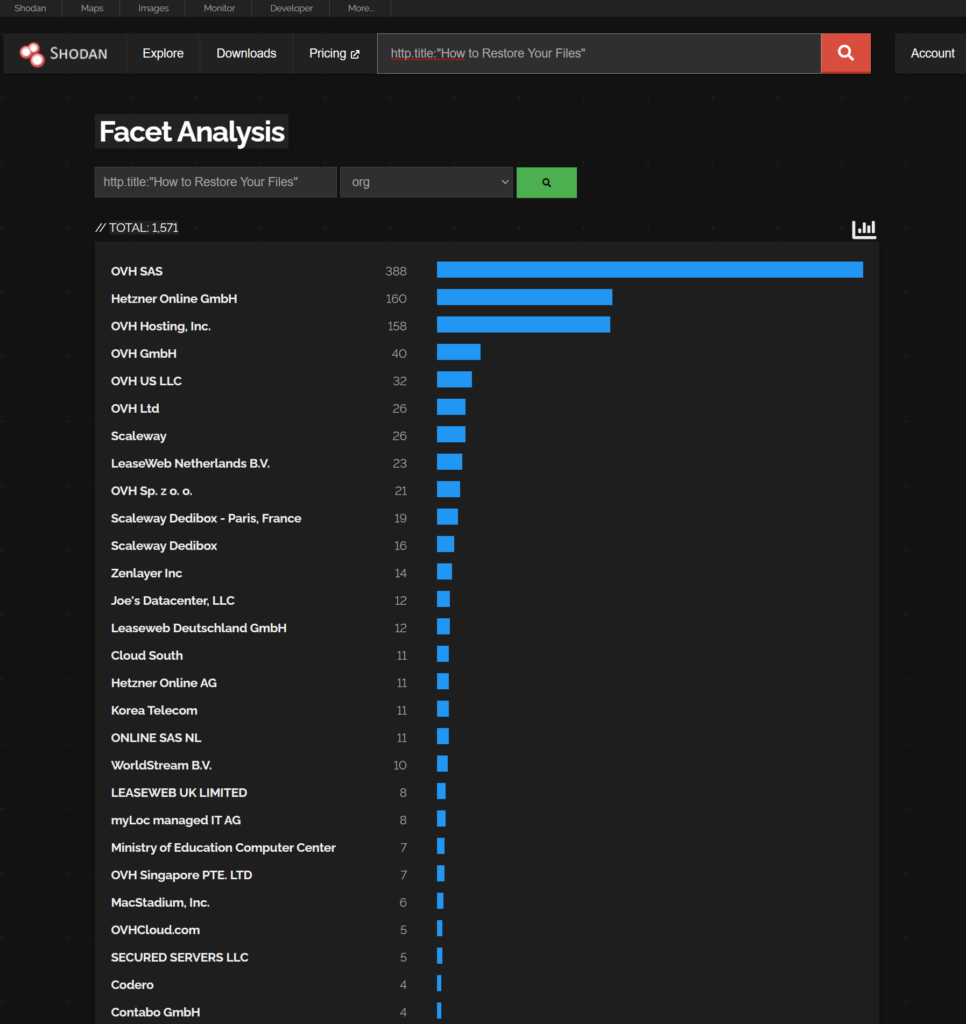
This is not a complete list but what is available in Shodan at the time or writing:








