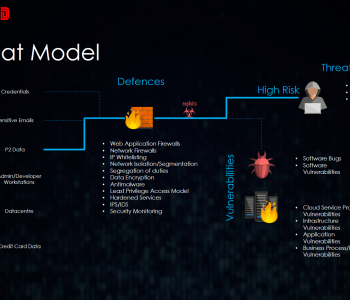
Defense
Defense
Changing a security posture requires changing your own behaviours
I’m sure you will have had a marketing firm or some random sales person on Linkedin tell you that security should be simple and that their product will save you from all the ATPs and nation state hax0rs under the sun. However let’s get real, thats almost certainly not true and also security isnt simple or we’d all be out of jobs and everyon woulndn’t be getting owned all the time.