 News
News
################################
Monday AM 16/01/2022 – Customers and Friends are reporting this issue is still occuring, just done a test and run MS v1.1. script, it found 0 apps to fix and applied zero fixes. My custom hacky script found a range of shortcuts to restore. I have a feeling this problem might drag on a little. there are timing issues with script application and CONFIG application + Defender update rules which means this might still affect machines. I’ve watched a machine delete icons this morning!
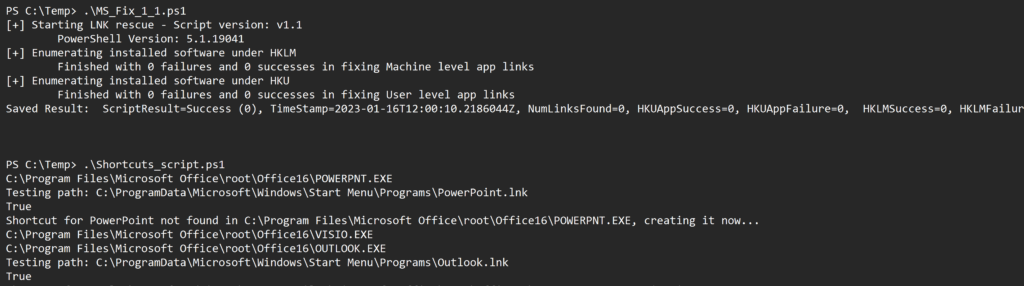
################################
This morning we’ve seen lots of people have .lnk files deleted from their user profiles, locations include:
- Desktop
- Start Menu
- Taskbar/Quick Launch
In the event log we have seen:
EVENT ID: 1121
SOURCE: Microsoft-Windows-Windows Defender/Operational
Looking at the defender logs:
“C:\Program Files\Windows Defender\Support” (you need elevated privs)
or
“C:\ProgramData\Microsoft\Windows Defender\Support” (thanks LZ ur a dude!)
If we look at MPLOG*
|
cat MPLog-* | findstr /I “desktop” | findstr /I “.lnk” |
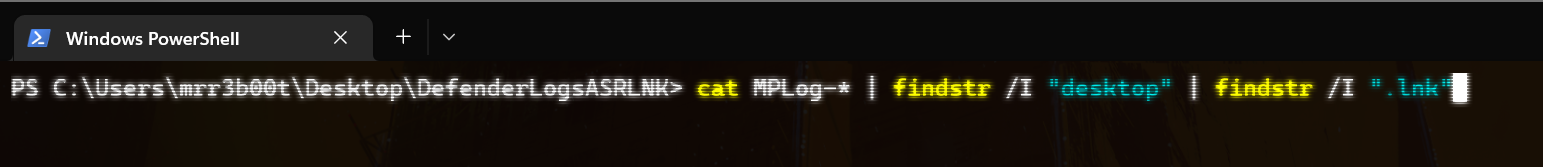
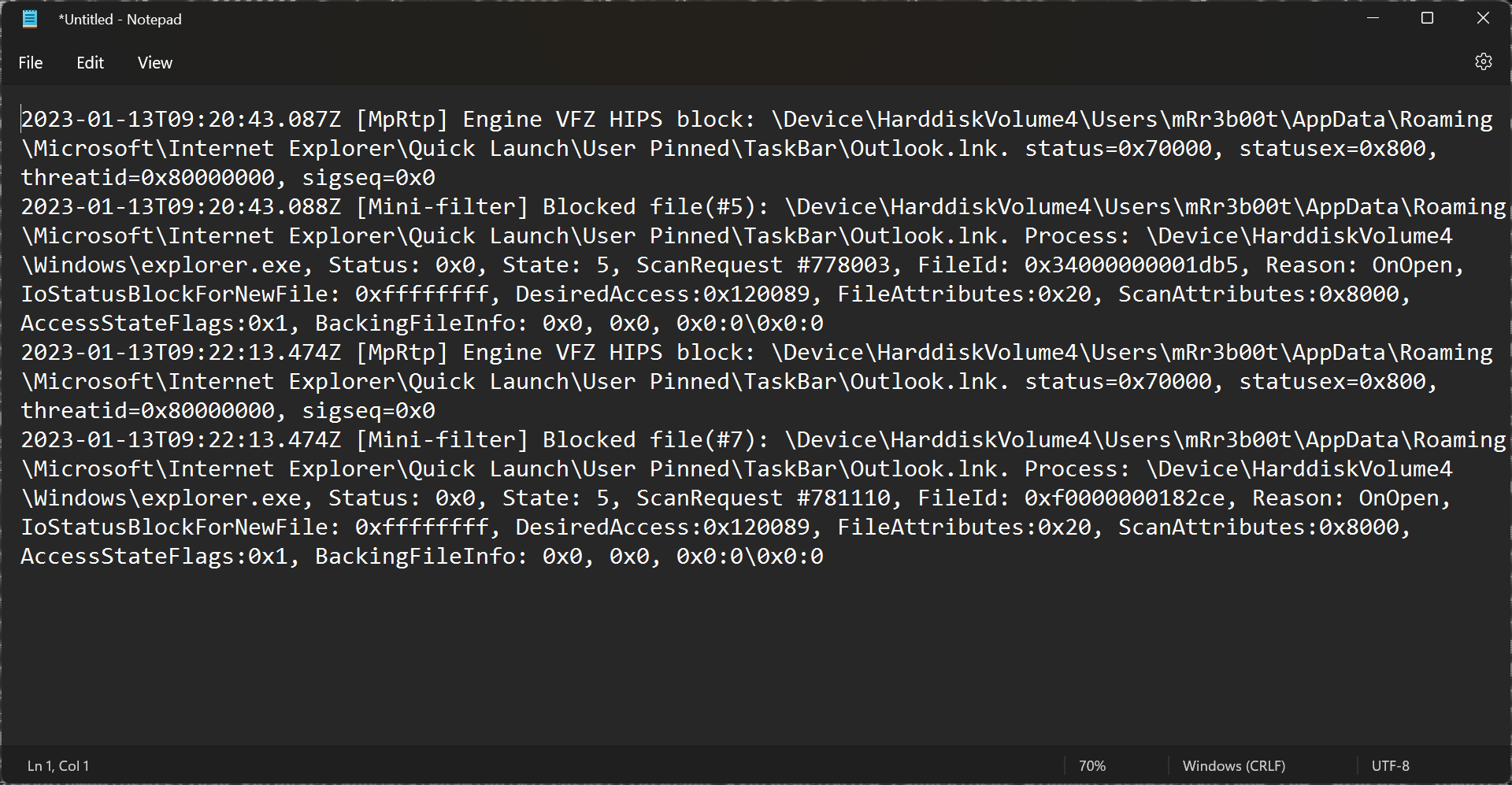
We can see a range of lnk files:
Here’s some sample data
| 2023-01-13T09:23:53.966Z [MpRtp] Engine VFZ HIPS block: \Device\HarddiskVolume4\Users\Public\Desktop\Microsoft Edge.lnk. status=0x70000, statusex=0x800, threatid=0x80000000, sigseq=0x0 2023-01-13T09:23:53.966Z [Mini-filter] Blocked file(#26): \Device\HarddiskVolume4\Users\Public\Desktop\Microsoft Edge.lnk. Process: \Device\HarddiskVolume4\Windows\explorer.exe, Status: 0x0, State: 5, ScanRequest #783324, FileId: 0x1000000091bec, Reason: OnOpen, IoStatusBlockForNewFile: 0xffffffff, DesiredAccess:0x120089, FileAttributes:0x20, ScanAttributes:0x8000, AccessStateFlags:0x1, BackingFileInfo: 0x0, 0x0, 0x0:0\0x0:0 |
KQL Example
DeviceEvents
| where ActionType == "AsrOfficeMacroWin32ApiCallsBlocked"
| sort by Timestamp
//| where FileName contains ".lnk"
//| summarize count() by DeviceName, AccountName
Actions I’ve taken
Disable the ASR Rule (or configure for audit mode etc.)
Attack surface reduction rules reference | Microsoft Learn
| Block Win32 API calls from Office macros | 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b |
There’s reports online of people without ASR rules being affected. More troubleshooting required!
Hopefully the people at MS don’t have too bad a time with this! Errors occur, this one might be painful. Let’s hope the impact is smaller than it could be!
There’s a tweet here from MS about it:
You can find this here:
Service health – Microsoft 365 admin center
There’s a threat on Reddit here:
Multiple users reporting Microsoft apps have disappeared : sysadmin (reddit.com)
LNK Files Removed From Paths
Paths that appear to have had links removed
- C:\ProgramData\Microsoft\Windows\Start Menu\Programs
- C:\Users\Public\Desktop
- %appdata%\Roaming\Microsoft\Internet Explorer\Quick Launch
It appears to have affected:
- Office Links
- Edge Links
- Chrome Links
- Adobe Reader/Pro Links
Strategies for Restoration
Here are some ideas (your millage may vary)
User Based
Ask users to re-create their user profile based:
- Start Menu
- Desktop
- QuickLaunch
As users to restore from OneDrive / Recycle Bin
Deploy centrally
- Common Applications Shortcuts into the start menu (admin rights required)
- Common Applications to c:\users\public\desktop (admin rights required)
- Common Applications to Quick Launch (as user)
there is also this option!
Re-deploy Windows! Nuke it from Orbit it’s the only way to be sure! (it was Friday the 13th after all 😛 ) (clearly this is a partial joke… but maybe not.. do what you feel you must etc.)

There’s some guidance/script from MS:
Recovering from Attack Surface Reduction rule shortcut deletions – Microsoft Community Hub
I don’t however think that restores userland shortcuts…. so it’s a half fix probably… #yikes



