Leadership
Leadership
Anyone that knows me, knows I love maturity assessments and tools (I’ve built a few, and run LOADS more) so this morning when I saw this on LinkedIn I had to start to get some understanding! I’ve not even had a cup of tea, but let’s see what this looks like!
https://learn.microsoft.com/en-gb/assessments/93dfb79b-71af-404d-897e-3928ecfb92b1/
Now there’s a framework behind this:
This is part of a wider framework (CAF) Microsoft Cloud Adoption Framework for Azure – Cloud Adoption Framework | Microsoft Learn

Start with envision (target) is in line with the Gartner EA approach, which focuses on target state first. Please do bear in mind, you can envision all you want, if you don’t understand the current state and transition architecture then you will probably run into major problems (see many failed public sector monolithic IT programs over the years)
Microsoft Assessments frequently asked questions (FAQs) | Microsoft Learn
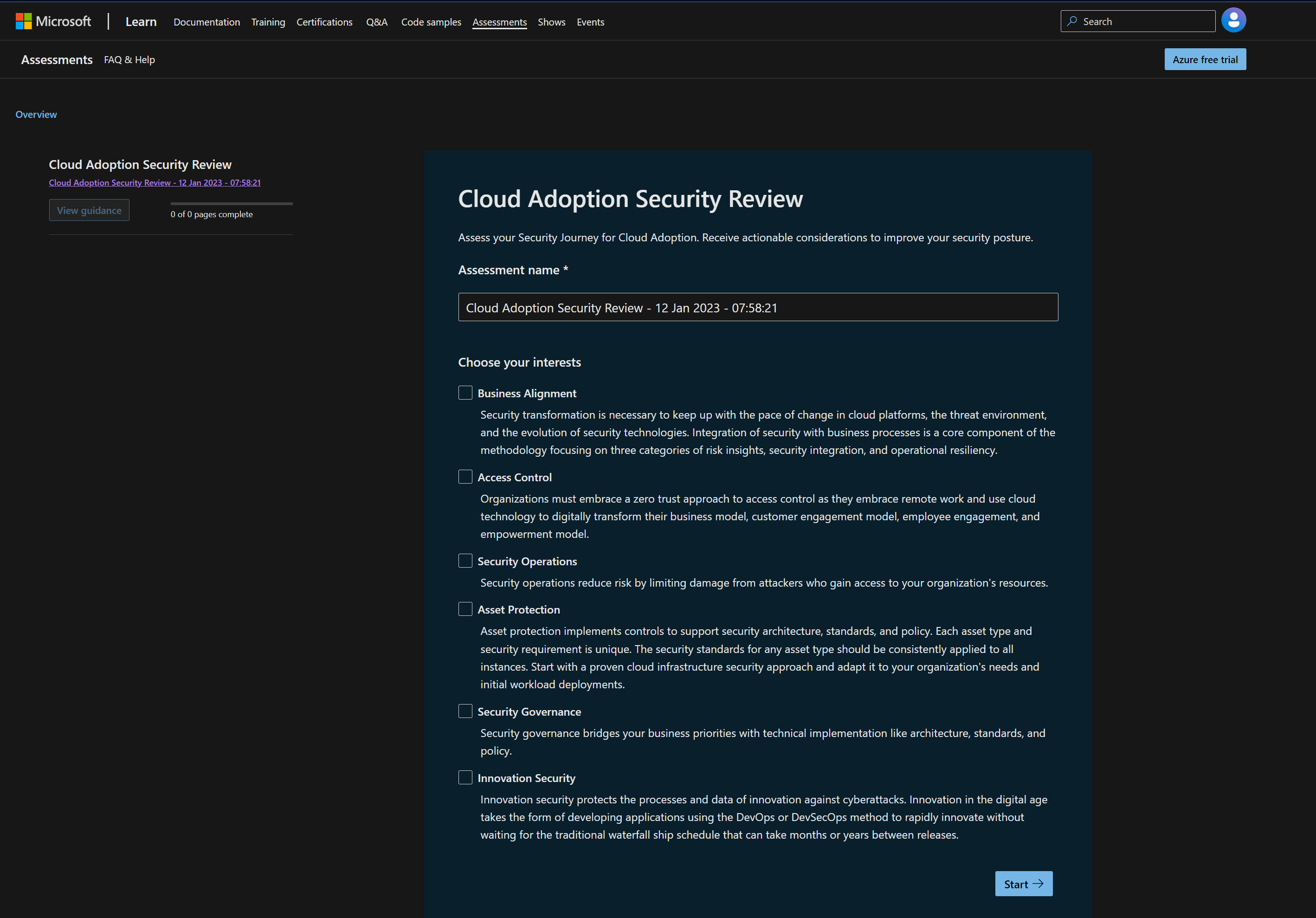
Ok, well I’m interested in all of these!
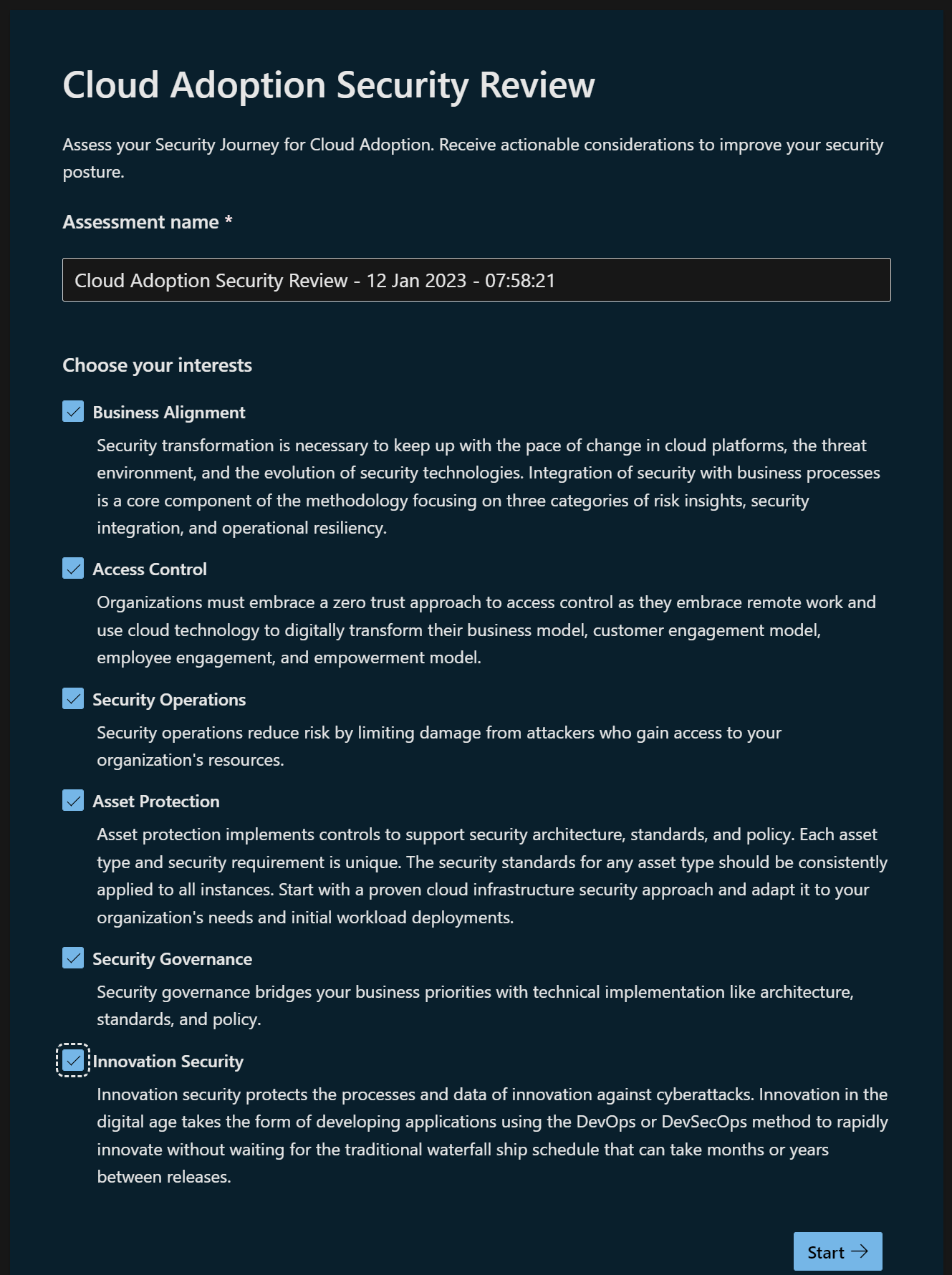
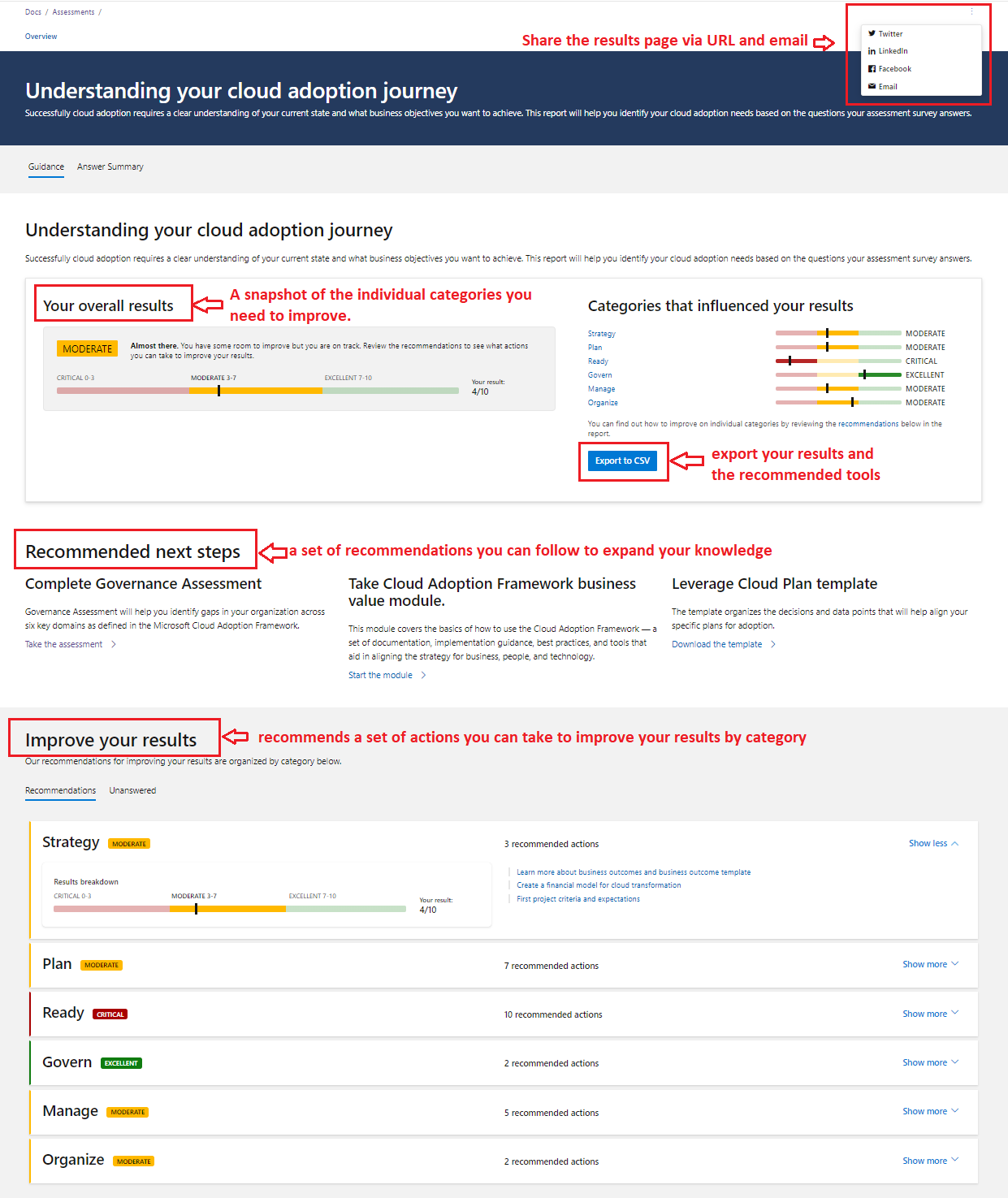
I pressed lots of buttons and managed to get to this 😉 which let’s me download the results XLS, so now I have the questions. There are 252 questions in this assessment, I think I need to get a cup of tea!
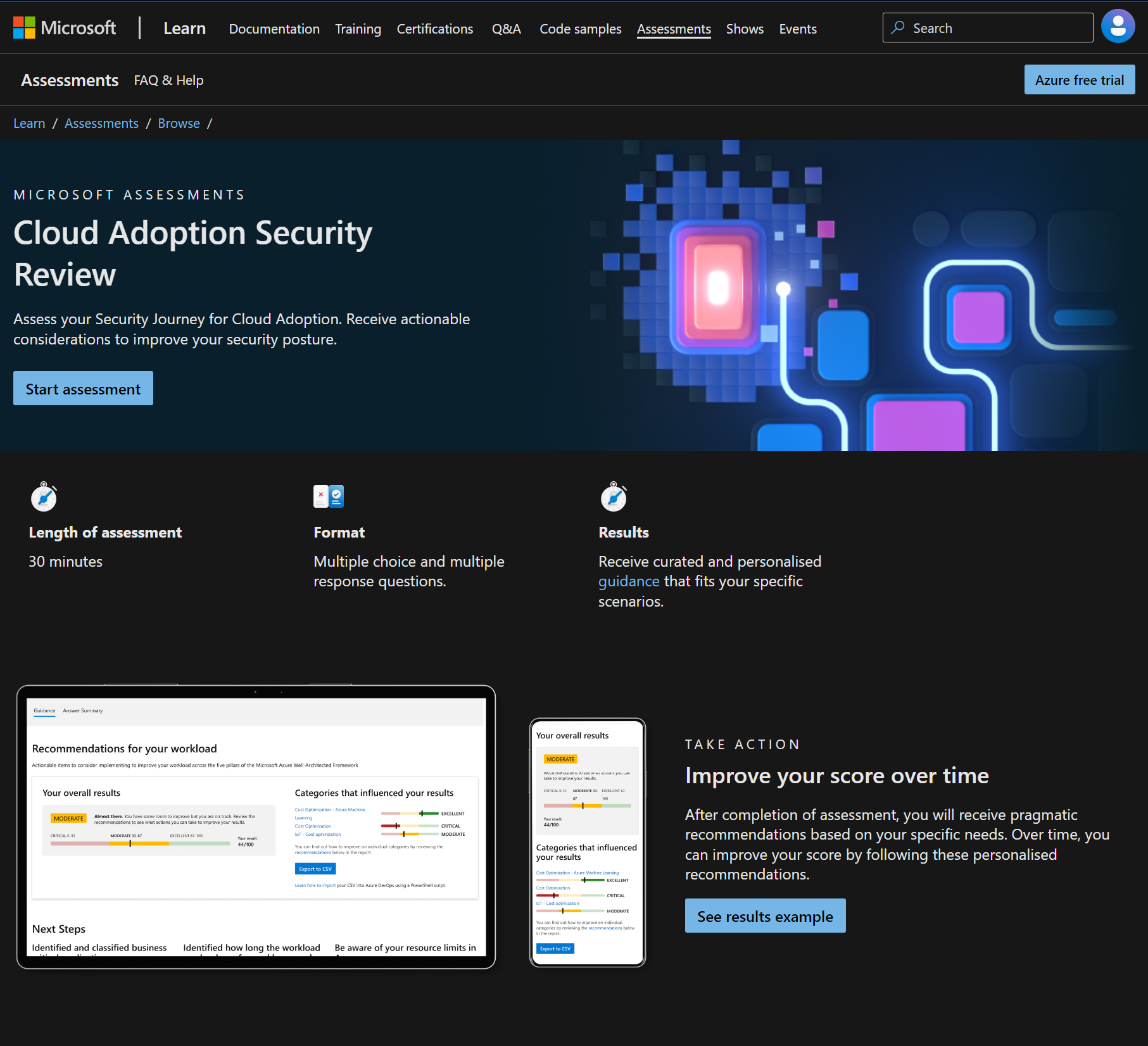
Cloud Adoption Security Review
https://learn.microsoft.com/en-gb/assessments/93dfb79b-71af-404d-897e-3928ecfb92b1/

Microsoft Assessments frequently asked questions (FAQs) | Microsoft Learn


Ok, well I’m interested in all of these!



I pressed lots of buttons and managed to get to this 😉 which let’s me download the results XLS, so now I have the questions. There are 252 questions in this assessment, I think I need to get a cup of tea! Ok there are not that many It’s 36 (remove duplicates FTW) across 6 categories!
Categories
- Business Alignment
- Access Control
- Security Operations
- Asset Protection
- Security Governance
- Innovation Security
Questions
- Which security disciplines are supported by required individuals who have both the proper skillset and are actively engaged?
- How would you describe the business level support of security and risk management?
- Which of the following are included in your continuous learning & risk reduction efforts?
- Rank your security integration program maturity
- Rank your business resilience program maturity
- How is connectivity secured across your cloud platform?
- What security controls do you have in place to manage Azure Infrastructure?
- How are you managing end-user and application-level authentication?
- Are you leveraging Landing Zone guidance on how you are managing access control in terms of network security controls and zero trust access controls?
- Are you leveraging Landing Zone guidance on how you are securing privileged access?
- Have you performed a threat analysis of your platforms and workloads?
- “What practices and mitigations have you implemented for tools/configuration in use in the environment? “
- How are you monitoring security-related events in the Landing Zones?
- How is security validated and how do you handle incident response when breach happens?
- How is security and security operations integrated into the broader organization?
- How are you monitoring and reviewing access to your cloud?
- Are you leveraging Landing Zone guidance on how your security operations are structured?
- As part of your security operations which of the following do you currently do?
- How are you managing access control in terms of network security controls and zero trust access controls?
- How are you securing privileged access?
- How are you managing encryption and key management in Azure?
- Do you have a service enablement framework that takes into consideration the following?
- How are you protecting network access to your applications?
- How are you segmenting network traffic flowing to and between your cloud resources?
- How are you managing encryption of data at rest and in-transit?
- Are keys, secrets and certificates managed in a secure way?
- How do you manage the security posture of deployed assets?
- How do you detect and manage threats to your applications and services?
- What is your approach to centrally managing and monitoring across cloud service providers and on-prem?
- What considerations for compliance and governance have you made across your portfolio?
- Which of the following landing zone enhancements have you made to enhance security governance?
- Who is accountable for security governance?
- Are you leveraging Landing Zone guidance to have a service enablement framework that takes into consideration the following?
- Have you adopted a formal secure DevOps approach to building and maintaining software? (DevSecOps)
- How have you hardened your development environment and pipeline against compromise?
- How do you manage risk from re-use of existing code? (software supply chain risk)
I’ve got tea now, so watch this space!
Completing the Assessment

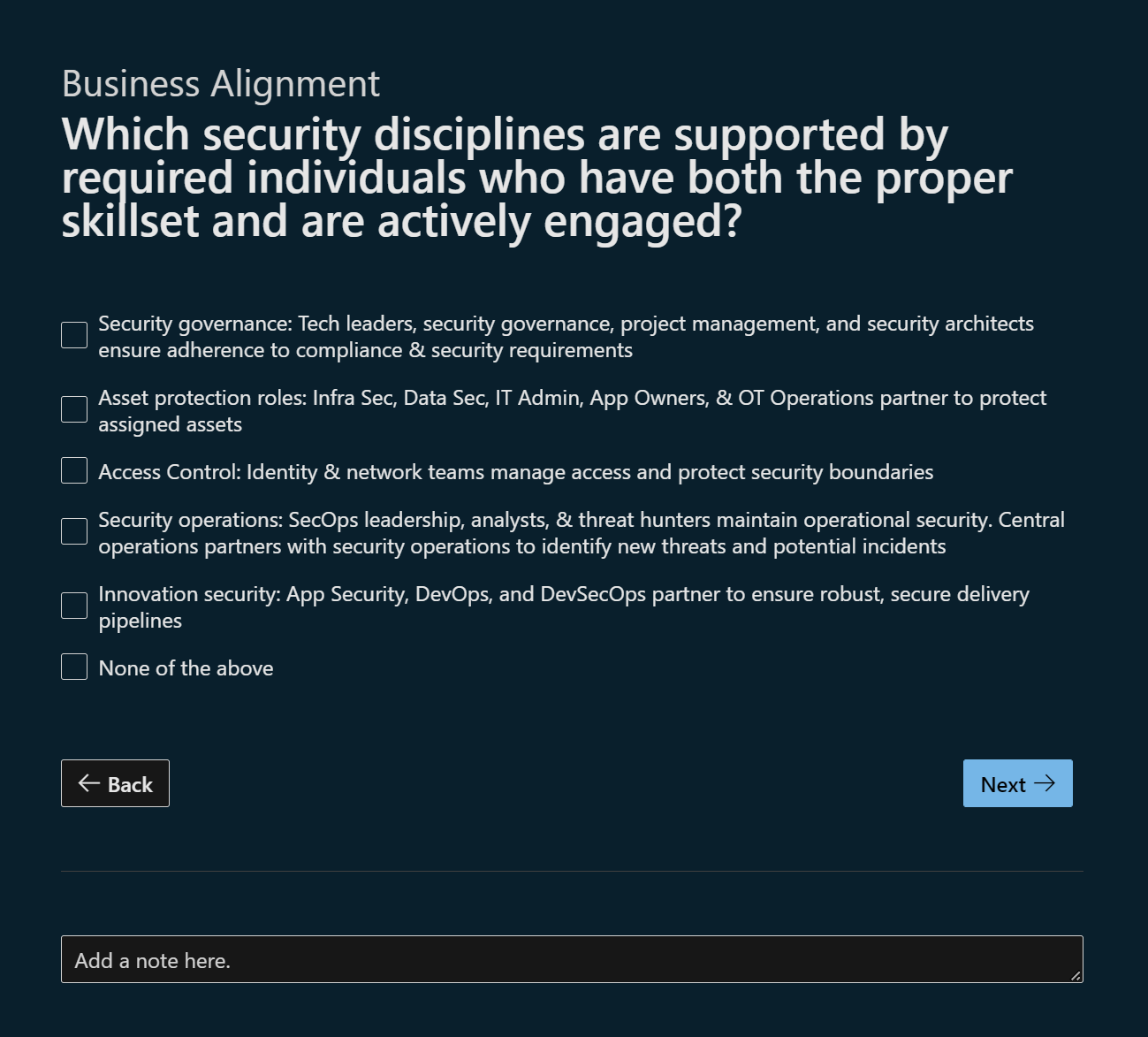
Ok so question 1, the actual question really is a question about what roles are being performed across the lifecycle:
- Security governance
- Asset protection roles
- Access Control
- Security operations
- Innovation security
So this is really 5 questions in 1, which if you are a fan of CMMI you might think “5” hmm I wonder…
Now my organisation is well, me! So I’m going to model this on a FICTIONAL (the legal people make me say that right!) customer organisation.
So first option:
“Security governance: Tech leaders, security governance, project management, and security architects ensure adherence to compliance & security requirements.”
The organisation “somewhat has this in place” they have leadership roles, the are however lacking in some skills (IMHO) and there are disconnects in communication therefore they re not actively engaged.
So for this I’m not going to tick it.
“Asset protection roles: Infra Sec, Data Sec, IT Admin, App Owners, & OT Operations partner to protect assigned assets”
There is a lack of integration between IT operations and security throughout the lifecycle. There are pockets of alignment in a number of products, however there are clearly gaps both in the specific products & services teams, but also with alignment to the security function.
So I’m not going to tick this.
“Access Control: Identity & network teams manage access and protect security boundaries”
Access control responsibilities are fairly well defined. An interesting observation, there are defined documented policies and processes, yet the Active Directory security posture (and identity management) is significantly weak. So how would you answer this? God we are on question one and even in isolation this is not a quick process for me to run through and I have a HIGH level of knowledge and understanding about the target organisation.
I’ll tick this, it’s fairly well defined from an alignment perspective (even thought we have concerns about effectiveness on the ground, that could be a legacy thing), next line please bob!
“Security operations: SecOps leadership, analysts, & threat hunters maintain operational security. Central operations partners with security operations to identify new threats and potential incidents”
Security in this organisation is largely is largely re-active, there is a SOC and security is considered, however across the estate and portfolio there is not consistent responsibility for security divested into the operations of services. The organisation lacks dedicated threat hunting capability (largely due to resource constraints). Oh god, do I tick this or not…… CISO advisory field note: if I say this is all in place and tick but then say we have resource constraints doe that work?
I’m going to tick this, we can explain the org roles and responsibilities are defined, we have skilled people and we are actively engaged however there is a resource constraint. It should still get the point across. Next please!
“Innovation security: App Security, DevOps, and DevSecOps partner to ensure robust, secure delivery pipelines”
Ok, we have CI/CD in some of our products but this is not enterprise wide, we are significantly lacking integration between CI/CD and security, it’s all very ad-hoc at present. I’m going to NOT tick this.
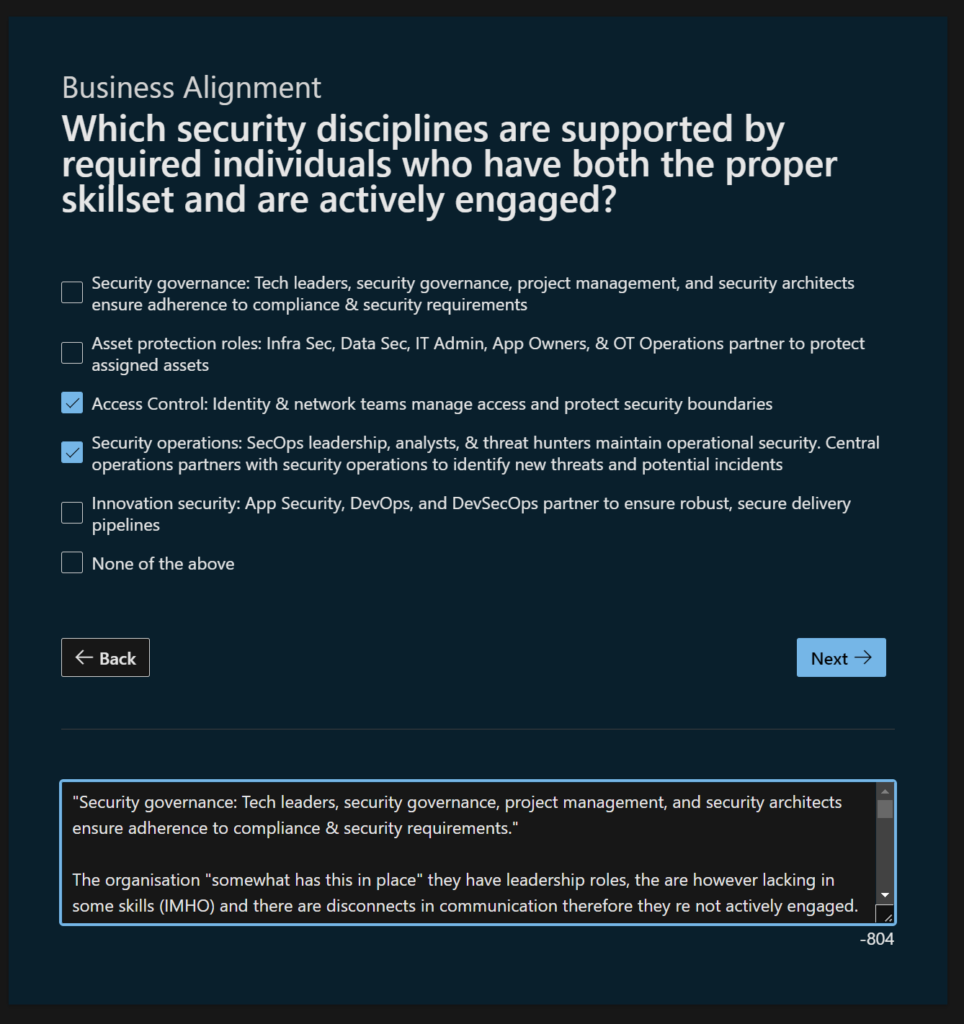
So there we have it, to answer Question one took me at about 15 minutes. There are 36 questions so I’d suggest an estimate is: 7 Hours at pace with FULL knowledge. I mean that’s a slog and to have full knowledge in an organisation is unlikely. More to follow! I need more tea…
Another day (15/01/2023) another question:
Business Alignment – How would you describe the business level support of security and risk management?
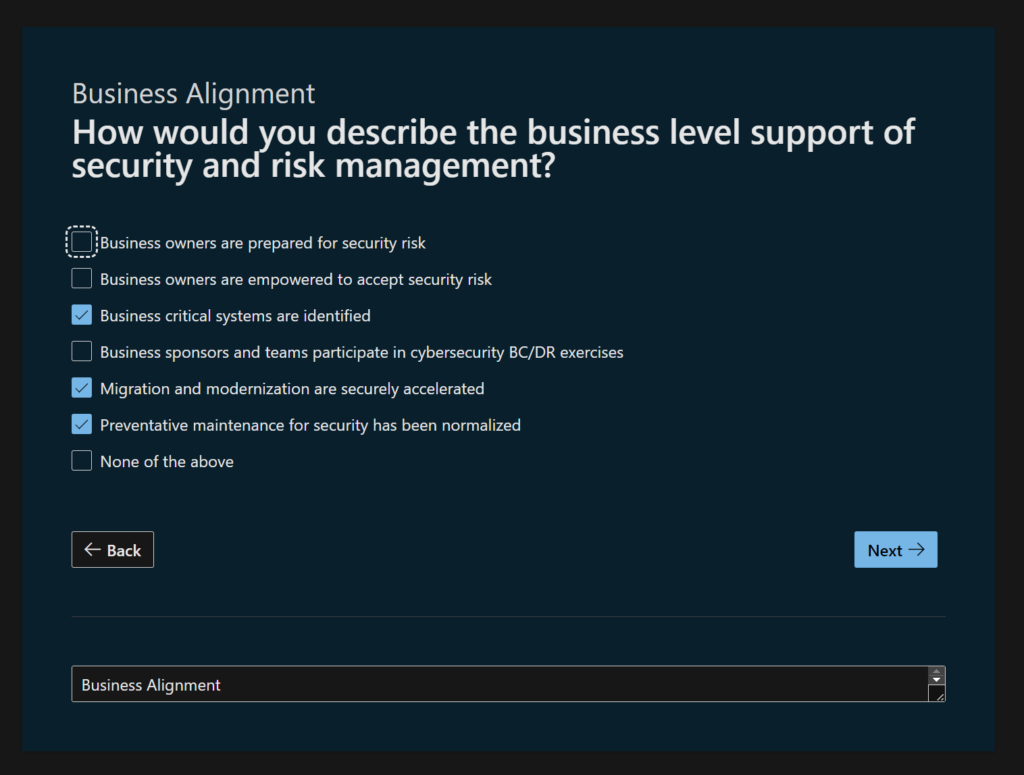
Business owners are prepared for security risk
In this DEMO org, the business owners are not really risk aware from a cyber security perspective. So it’s a NO for this one.
Business owners are empowered to accept security risk
I mean… they accept LOADS of cyber risk because they are unaware of it. So i’m not sure EMPOWERED is the right term. I’m going with a NO
Business critical systems are identified
Do they have an asset register? Yes. It has some critical systems identified. Let’s say YES
Business sponsors and teams participate in cybersecurity BC/DR exercises
When is the last time a BC/DR test was run? who was involved? It seems they might have not attended one in a while. So that’s a NO.
Migration and modernization are securely accelerated
(what does this even mean? no really!?) Like most organisations there is a a lot of assumption that NEW means its secure out of the box. I’m going to say NO i think.
I found a URL: https://learn.microsoft.com/en-us/training/modules/accelerate-azure-migration-journey/
God is this a sales thing? It’s very “Benefits of Azure”… wait 1….
Oh ok it says Defender for Cloud..
Start with a secure foundation
Simplify security with built-in controls
Detect threats early with unique intelligence
Azure Backup
Microsoft Sentinel
I think it means are we in future state initiatives, building security into the heart of products and services?
I’m going to say yes, this DEMO customer has a strong technical security posture.
Preventative maintenance for security has been normalized
(in English please! Normalized!? what is this) ok so yes, the organisation conducts preventative security maintenance on a regular basis and where possible leverages automation etc.
I’ll be honest I think I’d want to revisit the top of this question but it’s Sunday morning… IRL in an engagement the convo’s I’ve had running through questions like this can be amusing, when doing USA lingo assessment tool sessions, there’s often a few laughs and head scratchings about “what the bloody hell does that even mean”
Overall Q2, I think is useful to draw out some useful intel, I would suggest the lines each need sub questions to help uniformity of response and well to help people understand what is really being asked.
Q3 (maybe later today or in the week – yes this might be slow to complete but I have other things that are of greater importance right now)