 Leadership
Leadership
Armed with my trusty sidekick, this morning I thought I would see what an LLM would make if I asked it to create public comms for common cyber incidents…. for basically every scenario… it really wanted to tell everyone no data was accessed! Which is amazing, because in almost every incident I’ve seen: Data is accessed!
In a business email compromise (BEC) scenario…. the clue is in the name, it’s already a compromise of confidentiality!
In a ransomware event, there’s clearly a range of scenarios, if you managed to stop the attack within seconds then sure maybe you might find broadly that data is not accessed (clearly there is the username/password and then whatever interfaces they manage to connect to)… but largely speaking if someone is inside your network and they are fast they probably have accessed sensitive data, and then likely they will have exfiltrated it. Don’t believe me? give it a go during a security assurance exercise!
Now, what seems to be a macro pattern that we see of ‘expert comms’ during cyber incidents? well it often looks a bit like this:
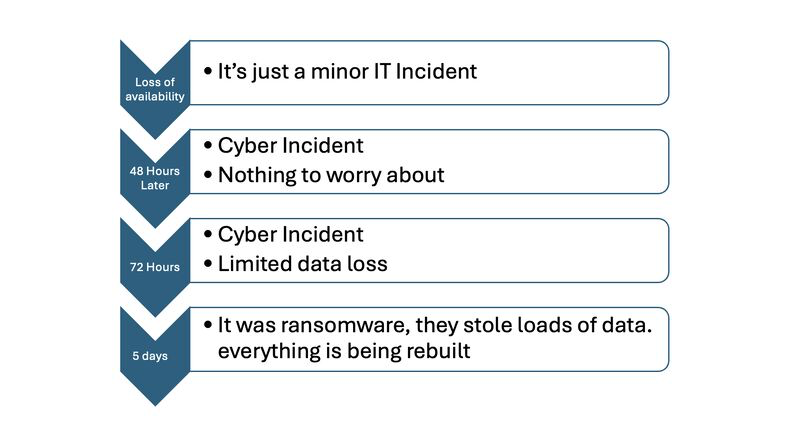
Now there are totally valid reasons for at 0 hour and in the first few days to not be able to create a reasonable and accurate impact assessment, however, if you walk in and all your PCs are showing ransomware encryption event wallpapers the high likelihood is, you aren’t going to be data loss free! So let’s task GROK to create a realistic set of comms to common incidents!
So this required three attempts and I had to be quite forceful! GROK really really seemed to want to say: there is not impact! I wonder why that is? is that based on science of incidents? or is that based on SPIN and communications that often downplay, deny and deviate from reality?
So let’s see, what if people were a bit more honest?
Customer Communication Statements for Cybersecurity Incidents
1. Phishing Attack Leading to Credential Theft
We recently detected a phishing attempt that compromised employee login credentials. We’ve acted swiftly by resetting passwords and enforcing multi-factor authentication (MFA) to secure the affected accounts. Given the nature of this incident, it’s possible that some data was accessed before containment, and we are actively investigating to determine if any customer data was impacted. We urge customers to stay alert for phishing attempts and report anything unusual to our support team.
2. Ransomware Infection via Exploit Kit
Our systems identified a ransomware infection on an internal device. We isolated the device and stopped the threat before it could encrypt critical data or spread further. However, ransomware attacks often involve data theft prior to encryption. We are investigating whether any customer data was accessed or stolen and will keep you updated as we confirm the full scope of the incident.
3. Insider Threat with Data Exfiltration
We discovered an insider incident where an employee accessed internal data without authorization. We immediately revoked their access and isolated their device to limit further risk. Due to the nature of insider threats, it’s possible that customer data was exfiltrated, and we are conducting a detailed investigation to confirm the extent of any data exposure. We are fully committed to resolving this matter and protecting your information.
4. Supply Chain Compromise
We identified a security issue in a third-party software component integrated into our systems. We’ve isolated the affected component and are collaborating with the vendor to address the vulnerability. Given the complexity of supply chain attacks, we are investigating whether any customer data was accessed or impacted. We’ll provide updates as we work to ensure the security of our systems.
5. Advanced Persistent Threat (APT) with Lateral Movement
Our security team detected a sophisticated cyberattack attempting to navigate our network. We contained it by isolating affected systems and enhancing network segmentation. APTs often aim to steal data discreetly, so we are thoroughly investigating to determine if any customer data was accessed. We’ll continue to strengthen our defenses and keep you informed throughout this process.
6. DDoS Attack Targeting Critical Services
Our services faced temporary disruptions today due to a distributed denial-of-service (DDoS) attack. We mitigated the issue with traffic filtering and rate limiting, restoring normal operations quickly. Since DDoS attacks focus on disrupting service rather than accessing data, we have no evidence that customer data was compromised. We apologize for the inconvenience and are reinforcing our systems to prevent future disruptions.
7. Zero-Day Exploit Against Public-Facing Application
We discovered an unknown vulnerability in a public-facing application and have taken it offline to prevent exploitation, isolating the server from the internet. We’re working urgently to patch the issue and restore service. Depending on the exploit’s scope, it’s possible that customer data was accessed, and we are investigating to confirm. We’ll update you once we’ve fully resolved the situation.
8. Business Email Compromise (BEC)
We detected a business email compromise (BEC) incident affecting an employee account. We’ve isolated the account and reset all credentials to prevent further misuse. BEC incidents often involve accessing sensitive email data, so we are investigating whether any customer information was exposed. Please remain cautious of suspicious emails and report them to our support team as we resolve this issue.
Now I’m not suggesting these are ‘the thing’ and that these are good/bad/ugly. What I am trying to show is that, there’s a big delta between what responders see in incidents and what is in public communications. Is that a good or bad things? How do you stand with the state of Cyber incident comms today?









