 Leadership
Leadership
Do you have a VDI solution in use at your business? Be that something like CITRIX, VMware View or Remote Desktop Services (VDI mode or Server Based Computing SBC) mode?
Well let’s consider this with regard to cyber essentials.
In a recent update post:
The following was stated:
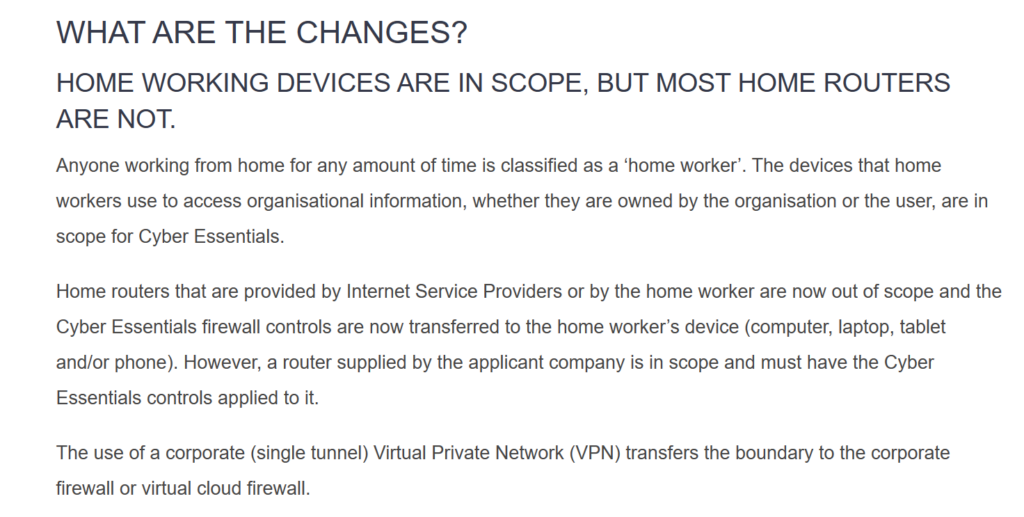
At first I read this as a change to home workers devices (I’m not a great fan of BYO personally) but It appears that’s always been the case (honestly the scenarios I’ve worked with for customers that have needed Cyber Essentials have never included non corporate assets (maybe I’m lucky!) so this scenario hadn’t really entered my head.
But let’s consider this:
A VDI environment is largely deployed for remote access to organizational assets and services from NON organizationally controlled devices. (it’s not the only model but that’s been my experience over the last 20 odd years).
The Cyber Essentials Standard
Ok so let’s consider this scenario. Our organization is a hospital and it has deployed VMWARE Horizon View for VDI, it’s public facing and staff are allowed to use:
- Personally Owned Devices
- IT has MFA (they use an MFA app on smart phones which are personally owned)
So we have a home worker using a personal device.
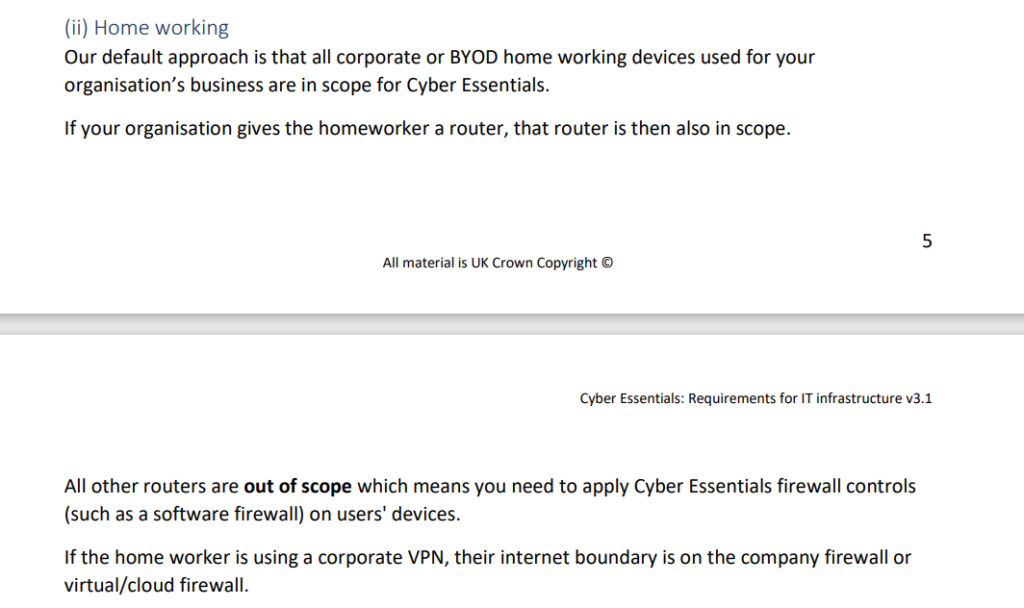
This device would be IN SCOPE.
The router would be OUT OF SCOPE
The VDI connection is being connected via an HTML5 Client.
Now let’s consider this as well
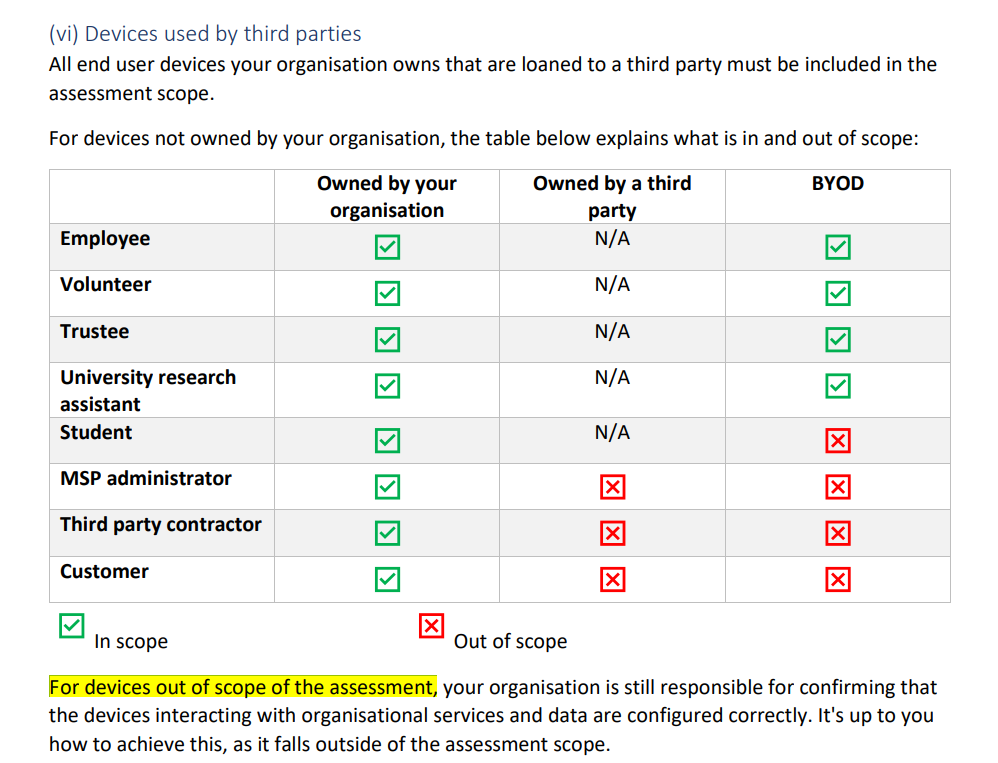
“For devices out of scope of the assessment, your organization is still responsible for confirming that
the devices interacting with organizational services and data are configured correctly. It’s up to you
how to achieve this, as it falls outside of the assessment scope.”
Looking at this I (and it might be wrong about this) I can see the following challenges:
You have no technical way of ensuring the personally owned device:
- Meets the standard
You also largely don’t have a way to assure it either, you can’t audit the devices as you don’t have access (they are not managed and not owned by your organization).
If we look the table above, I can however see that if you are a CUSTOMER and NOT an EMPLOYEE the devices would be out of SCOPE, however you are required to be “responsible for confirming that
the devices interacting with organizational services and data are configured correctly”
As such the only control I can think of deploying is a logical policy based control:
“All devices that are used to connect to the infrastructure must meet or exceed the standards for Cyber Essentials.” Essentially you would need to deploy a terms and condition of use etc.
You could do some logical segmentation and setup a company that hosts VDI services and therefore your main organizational staff would therefore NOT be EMPLOYEES but customers, but you would still need a policy based control to state the above.
If anyone has any other ideas of how to design, assess, audit and assure against this requirement please feel free to drop me a message on LinkedIn or Twitter! I’d love to hear peoples ideas! ( I have some ideas about technical magic (it’s not magic it’s science) we could potentially deploy using WAFs and checking user agents but they are far from robust in my head)
Resources
Thought Exercise
If you wanted to explore this, head over to Microsoft Azure and look at Virtual Desktops…. then think about if they meet the Cyber Essentials standards out of the box? and if not, what can you do to ensure they would?








