 Defense
Defense
This weeks been an interesting one, I’ve been doing quite a bit of research recently with my friend Simo from Defused defusedcyber.com. Simo has built a new emulated honeypot platform, and anyone that know’s me knows I love honeypots, deception and intel sharing to help defenders and to impose cost on the baddies! (technical terms here ok!)
So what’s the deal? Right so going back a bit, in October a payload was noticed against Fortinet devices:
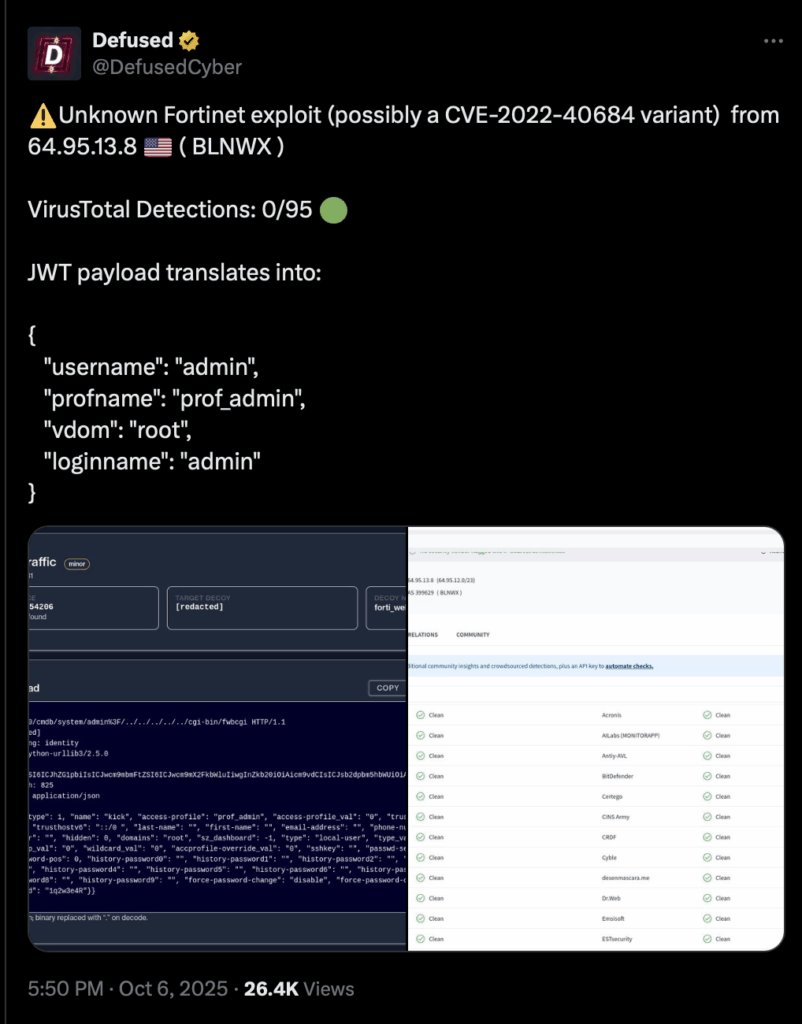
https://twitter.com/DefusedCyber/status/1975242250373517373?s=20
Turns out this may be a zero pay path traversal vulnerability (shocked, a vulnerability in this is unheard of /S)
Payload Details
So this is already public and already being sprayed over the internet, there’s always a concern here when we think about how much intel to share/publish etc. So I’m not going to write the full details but I will give enough to help with detection logic (someone else is free to do more, that’s their own choice!)
The TA appears to send a payload to the following URL Endpoint via an HTTP POST request
/api/v2.0/cmdb/system/admin%3F/../../../../../cgi-bin/fwbcgiInside this is a payload to create a user account.
Suspected IOCs
So what suspected IOCs we do we have?
We have some usernames, passwords, the endpoint and some source IPs
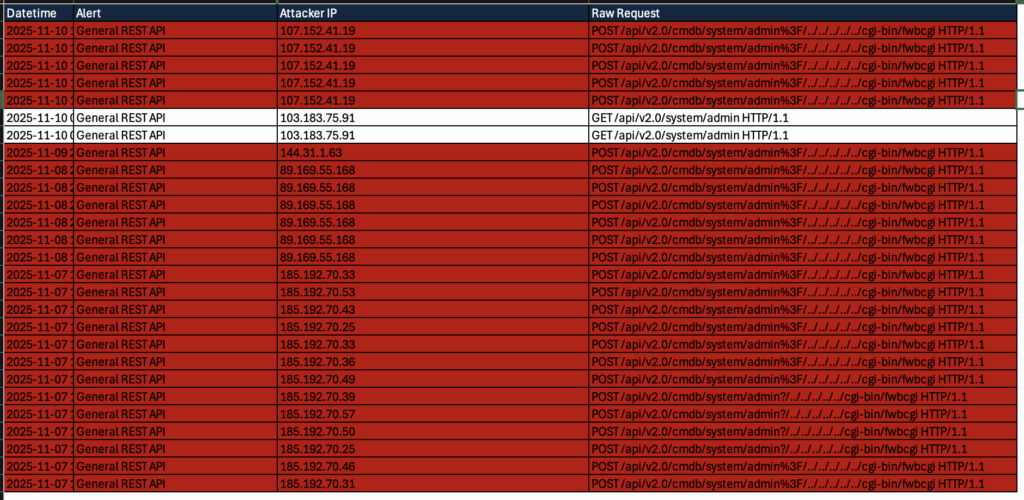
IPs
107.152.41.19
144.31.1.63
89.169.55.168
185.192.70.33
185.192.70.53
185.192.70.43
185.192.70.25
185.192.70.36
185.192.70.49
185.192.70.39
185.192.70.57
185.192.70.50
185.192.70.46
185.192.70.31
64.95.13.8Usernames & Passwords
Extracted from the payloads we have found the following so far:
| Username | Password |
|---|---|
| Testpoint | AFodIUU3Sszp5 |
| trader1 | 3eMIXX43 |
| trader | 3eMIXX43 |
| test1234point | AFT3$tH4ck |
| Testpoint | AFT3$tH4ck |
| Testpoint | AFT3$tH4ckmet0d4yaga!n |
Affected Products
- WatchTowr have tested this against Fortinet FortiWeb.
- They report versions below 8.0.2 are affected.
To note: the API endpoint (or a similar one there’s a v2 vs 2.0 thing here..) appears to only be referenced for FortiWeb:
(this shows a /v2/ reference vs /2.0)
Some of the documentation is locked behind a subscription (not very helpful imho). Using GROK we can see the following summary:
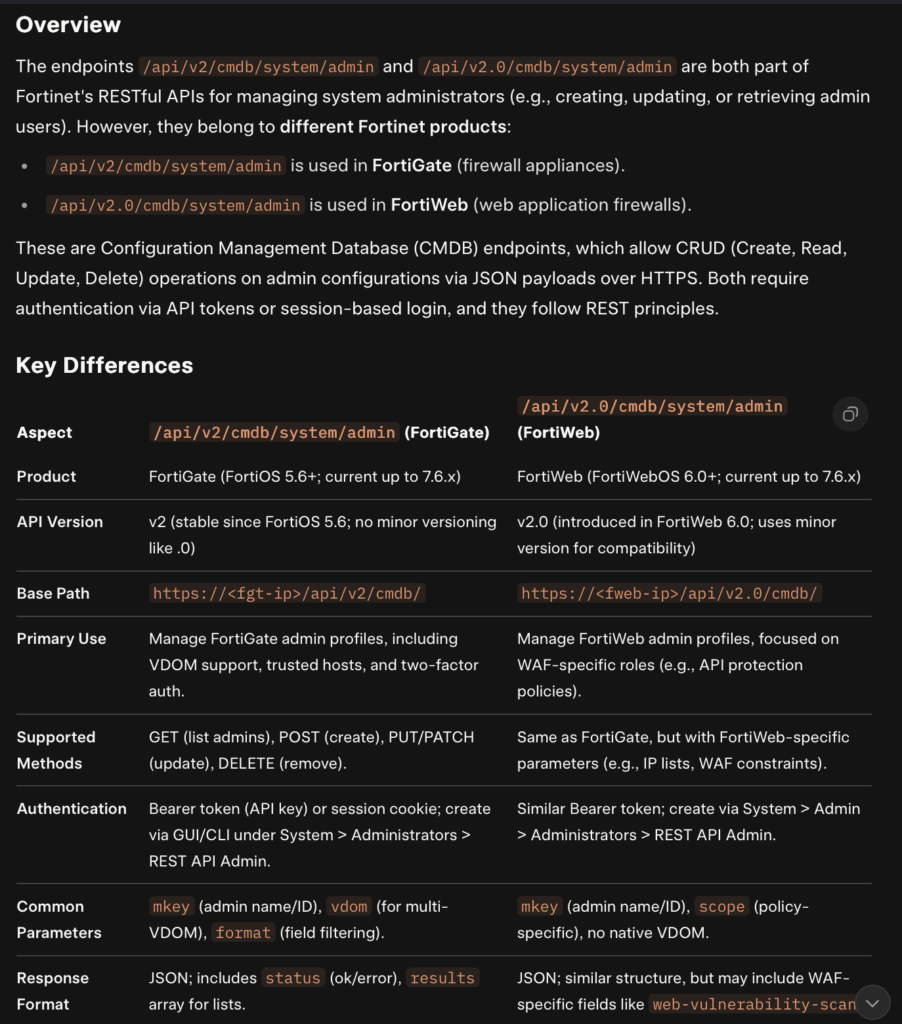
So it appears /v2.0/ is only used on FortiWeb (vs /v2/ is used on Fortigate)
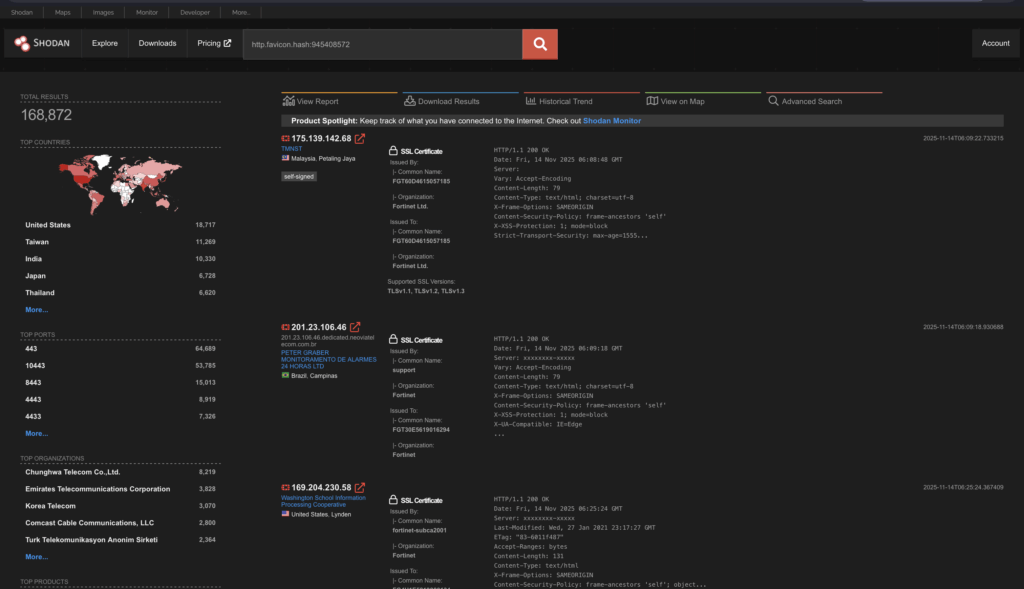
Shodan Exposure
Using www.shodan.io I have begun to search for exposure levels using:
https://www.shodan.io/search?query=http.title%3AFortiWeb
http.title:FortiWeb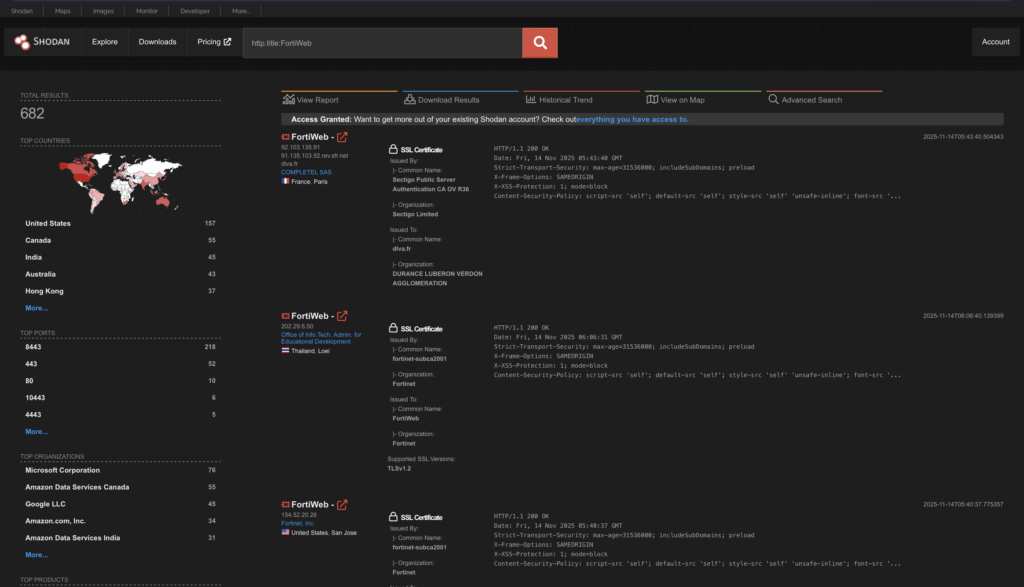
The volume in Shodan for FortiWeb looks relatively low. Especially when compared to Fortigate (I’ve picked a favicon hash, there may be more obviously):
https://www.shodan.io/search?query=+http.favicon.hash%3A945408572
Summary
This payload appears to create a local ‘admin’ level user account on the target device. I’ve not got a Fortinet firewall running so I’ve not been able to confirm the effect works myself. This is however looking like enough to the point, I believe the vendor has been notified and it looks ‘exploity’ enough for me to even consider writing about this, 0day or not this is being sprayed, we can see this in logs. The key thing as always is to not panic, if you have a Fortinet with an exposed management interface (WHY?) then I would suggest taking some time to go and investigate, I’ve written some general high level steps here:
Proof of Concept
WatchTowr demonstrate the exploit working here:
You can see in the demo, logon failed, payload sent followed by a successful logon.
Honeypots
If you are interested in Honeypots, go and check out what https://defusedcyber.com are doing! You can subscribe to intel feeds or deploy your own decoys! oh and give them a follow on Twitter: https://x.com/DefusedCyber if you feel like it!
oh and don’t forget to check out the latest UwU Underground Tune: https://x.com/i/status/1988653937843663152








