 Threat Intel
Threat Intel
Off the back of Operation Endgame (great work everyone involved!) we have some more data to show what many of us in the cyber industry know but isn’t so easy to show people. So I figured this might help explain part of how and why infostealers are a problem but also I look at how we might be able to use this takedown to help feed into a risk modelling process.

What is an info stealer?
Malware that is installed/executed on systems that steals information! I know, right but let’s think about what is stolen:
- Usernames/Emails
- Passwords
- Bitcoin Wallet IDs
Now stealers get deployed through a range of techniques:
- Backdoored legit software via malvertising (malicious advertising e.g. google adverts)
- Phishing emails
Who gets hit?
Now this is harder normally to quantify, each antimalware company gets a slice of a view of what they see, the browsers see some things through google safe browse API and Edge APIs etc. The EDR companies see things etc.
But with this latest takedown and arrest we have a dataset in the public. So I’ve started to do a small cleanup activity and then have started to look at how this looks at from a contextual pov.
What gets hit?
Personal Devices? Corporate Devices? It really depends. I have seen a mix personally but honestly we don’t know the full picture. I’d guess more home/personal PCs than corporate ones, feel free to send me data analysis if that’s a wrong assumption.
Dataset Analysis
In the dataset the count of domains was > 330K domains!
In the collection there are over 44 Million set of credentials!
Now a key thing to note here, you might have in someone’s home PC, a set of credentials like:
name @ workplace dot domain
A member of staff might have signed up for amazon using a work email, or getting their grocery shopping with a work account. So a corporate email existing in an info stealer log != the corporate credentials. We should not however discount, credential re-use etc.
I did some analysis on a specific sector and used OSINT to estimate staffing levels:
| Credential % vs Estimated Employee Count |
| 2.000% |
| 1.857% |
| 1.160% |
| 1.075% |
| 1.000% |
| 0.800% |
| 0.656% |
| 0.600% |
| 0.600% |
| 0.533% |
| 0.514% |
| 0.500% |
| 0.333% |
| 0.309% |
| 0.280% |
| 0.273% |
| 0.229% |
| 0.140% |
| 0.133% |
| 0.133% |
| 0.133% |
| 0.125% |
| 0.120% |
| 0.111% |
| 0.100% |
| 0.097% |
| 0.080% |
| 0.079% |
| 0.067% |
| 0.067% |
| 0.060% |
| 0.057% |
| 0.050% |
| 0.045% |
| 0.040% |
| 0.033% |
| 0.030% |
| 0.030% |
| 0.029% |
| 0.024% |
| 0.023% |
| 0.017% |
| 0.015% |
| 0.013% |
| 0.005% |
The range is from 0.005% to 2% and if we look at the mean (average) we get 0.324%
For another slice I get this (different vertical):
| Percent |
| 1.257% |
| 0.800% |
| 0.650% |
| 0.588% |
| 0.533% |
| 0.527% |
| 0.500% |
| 0.400% |
| 0.395% |
| 0.367% |
| 0.350% |
| 0.338% |
| 0.267% |
| 0.229% |
| 0.225% |
| 0.225% |
| 0.222% |
| 0.211% |
| 0.150% |
| 0.150% |
| 0.135% |
| 0.120% |
| 0.117% |
| 0.113% |
| 0.111% |
| 0.110% |
| 0.100% |
| 0.090% |
| 0.080% |
| 0.080% |
| 0.070% |
| 0.067% |
| 0.067% |
| 0.057% |
| 0.057% |
| 0.057% |
| 0.054% |
| 0.053% |
| 0.050% |
| 0.040% |
| 0.033% |
| 0.029% |
| 0.025% |
| 0.020% |
| 0.018% |
| 0.017% |
| 0.013% |
| 0.013% |
| 0.013% |
| 0.010% |
| 0.009% |
| 0.003% |
That’s a range of 0.003% through to 1.25% with an average of 0.20%
Broadly speaking what we are seeing from the one stealer family, <2% based on an our sampling. From a risk point of view that’s not nothing.
Using the UK National Risk register matrices:
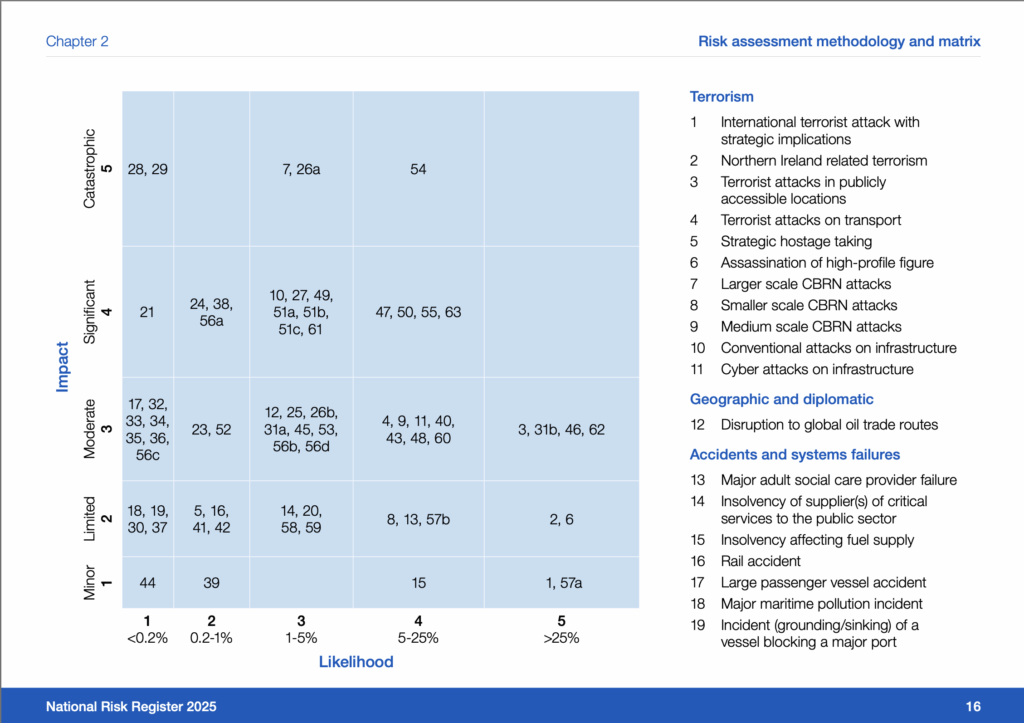
That sit’s into Category 1 or 2 Likelihood.
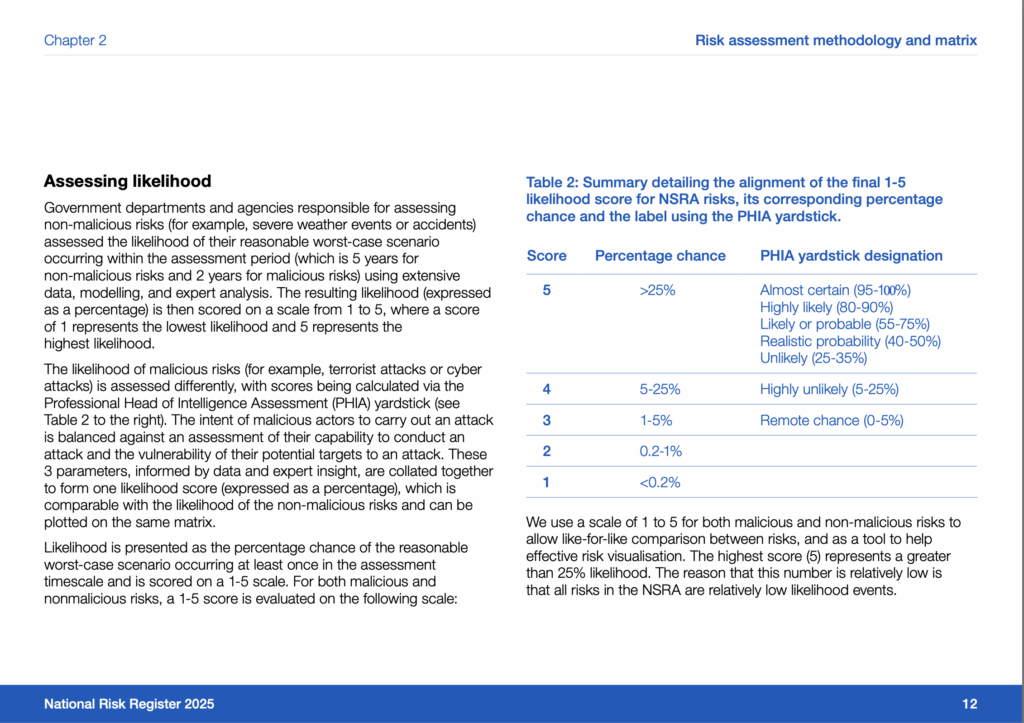
So on the PHIA yardstick that fits into ‘Remote Chance 0-5%’. Clearly assessing impact here is outside of the scope of this blog. Impacts could range from almost 0 to significant, depending upon a large range of variables.
Summary
Now clearly info stealer are a problem but also it’s clear that an email + credentials != corporate credentials (in all cases). You simply need to be inside the org or have validated the creds against a corporate auth provider… and well we aren’t criminals so we don’t do that!
It’s key that organisations implement controls to both protect, detect and respond. What does that look like in practise?
- Contextual/Conditional Access
- Breach monitoring
- Multi-Factor Authentication
- Risky Sign in detection and response
- EDR
- Antimalware
- Web Content Filtering
- Protective DNS
Identity threats are real, ensuring you have robust controls in this space makes sleeping much simpler! A no incident r3b00t life is a happy r3b00t life!
Remember, it’s easy to see a brand name etc. and jump to conclusions, hopefully this helps people understand about info stealers, the complexities of understanding the data and gives a view of prevalence (at least for this particular family). The details, as always… matter!








