CTF
CTF
mRr3b00t Learns to play HTB again!
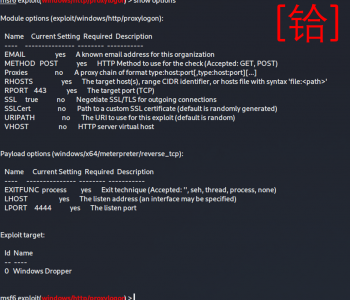
I rarely get a chance to play HTB these days 🙁 but today I thought i’d get back on it.. then I had a three hour battle with a graphics driver and Vmware Workstation so that basically ruined that idea…. but I thouht I’d try and remember how to CTF again.. and boy do you get slow fast! Well to try and help people and myself I’ve started to write down some notes to get my mind back into the CTF world of HTB!
Setup & Scope
Ok this is the setup phase. Let’s grab the details
- Take note of the machine name
- Remember most boxes are called .htb or .htb.local
- There’s not an “internet” dns inside the arena so you need to update hosts files
- Take note of the box author
- This is useful for OSINT
- Take note of the IP
- This is your scope
- Take note of the OS version
- Get you digital notebook ready