 CTF
CTF
History of NULL bind
Back in the early Active Directory days NULL bind was actually enabled by default, these days you can get a rootDSE NULL bind out of the box but on Windows Server 2019 you can even disable this!
So why would I want to enable NULL bind? Well, some legacy apps may need it but generally speaking you don’t want NULL bind enabled.
The lesson here is DO NOT copy what I am doing here! Simples!
Enabling NULL bind in Windows Server 2019
So, to start let’s load ADSI edit:
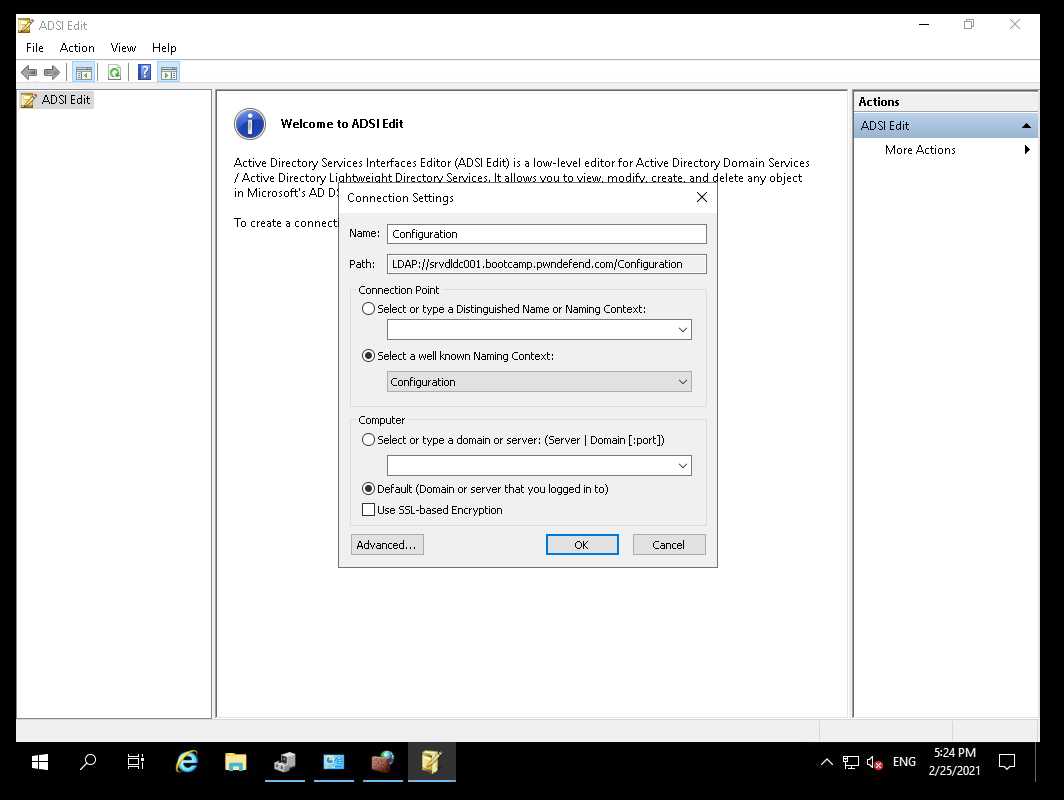
Next, we right click on ADSI Edit and click connect and we select the configuration partition:
Now we can look at the configuration partition objects.
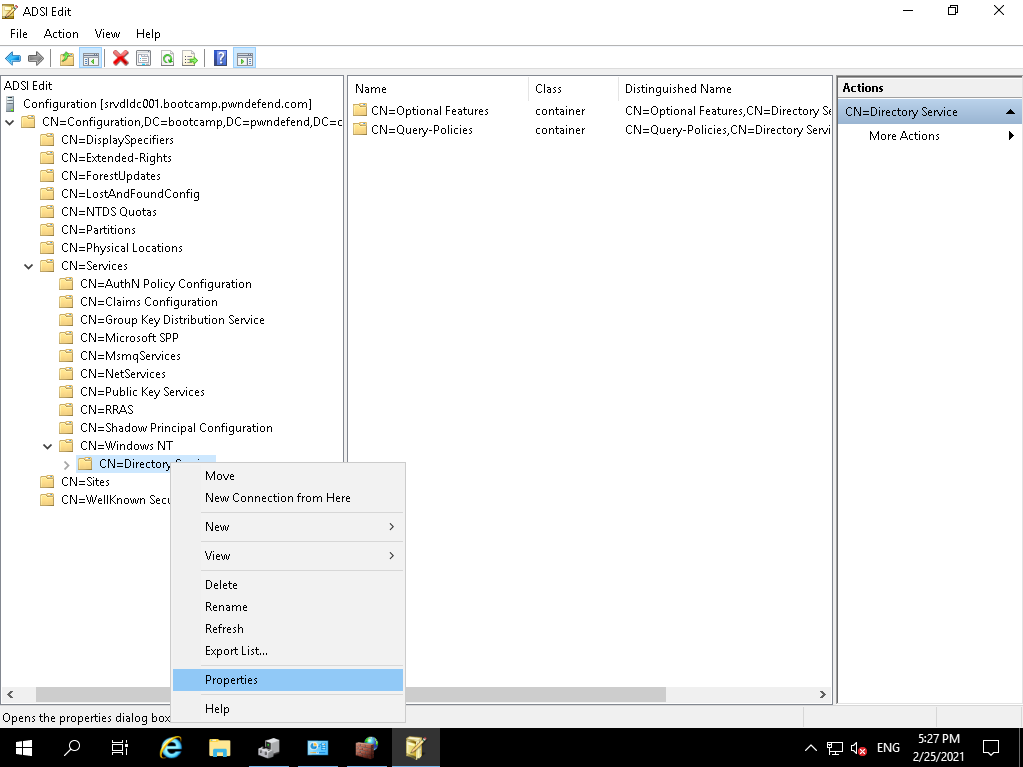
We want to expand CN=Services, CN=Windows NT and then right click on CN=Directory Services and click properties:
Now out of the box this was set to NOT SET. So we want to ENABLE this with a 0000002 value: 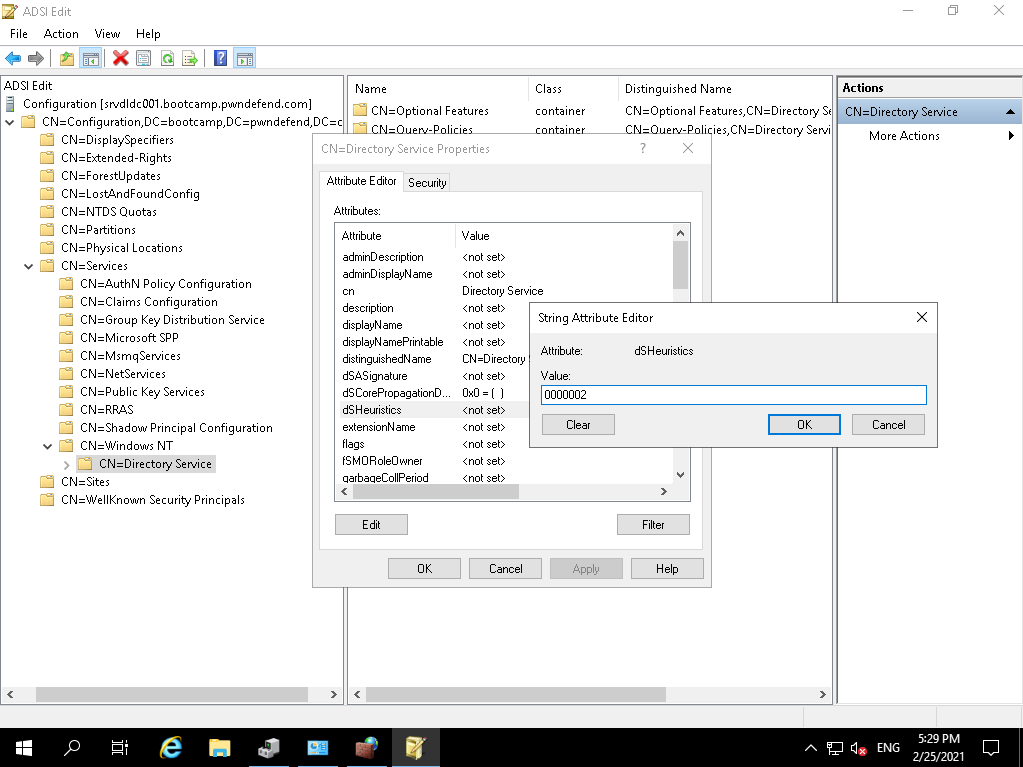
This will enable anything with EVERYONE or NT AUTHORITY\ANONYMOUS LOGON to read all of the standard LDAP objects and attributes. For more info on this object see:
Heading over to ADUC we can see we need to configure this (enable advanced mode):
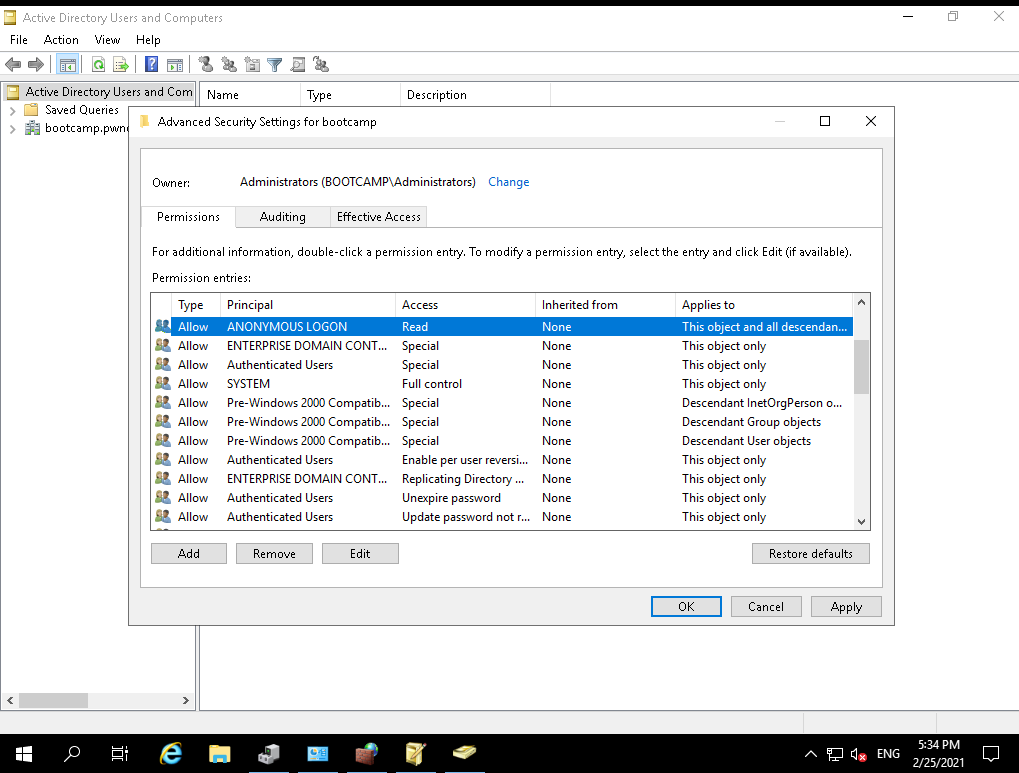
Using the security DACL editor we are going to give anonymous logon read access to all objects and child objects.
Lessons learnt
Don’t ever do this! Ever! It’s the most insecure way of getting an application to read LDAP data and leaves you vulnerable to username and well everything enumeration really. Why have I configured this? Well I build vulnerable systems so it’s fun to show how NOT to do things, or if you like building capture the flag games it can come in handy 😉






