 Guides
Guides
Did you ever read about ransomware actors? They often use mega upload to exfiltrate data! So I figured, why would we not detect this with MDE?
I mean sure we should probably block this with a custom indicator using Web Content Filtering and sure it would probably get blocked by Protective DNS but let’s say for whatever reason you don’t have those in place, let’s look at a really simple query to find mega connections in MDE:
// Mega upload Query
DeviceNetworkEvents
| where Timestamp > ago(1h)
| where ActionType == "ConnectionSuccess"
| where RemoteUrl endswith "mega.io"
or RemoteUrl contains "mega.nz"
or RemoteUrl contains "mega.co.nz"
or RemoteUrl contains "megapay.nz"
| sort by Timestamp desc There we go, now that’s been written for a detection query, so for threat hunting you probably want to look at 30d or 90d, however it’s a starting point!
Where else could we look? Well we could also look at Cloud App Security right! We can also block in MCAS. See so many ways to get in the way of things, not that these controls are bulletproof… but every little helps right!
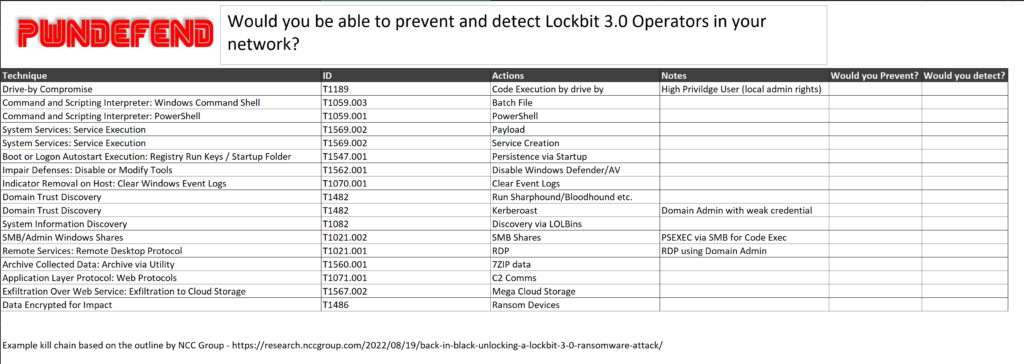
See the more we look at cyber incidents timelines and “KILL CHAINS” the more we can look at how to identify, protect, detect and respond! Cyber isn’t simple, but with sustained effort, it does at least impose cost on an attacker!









