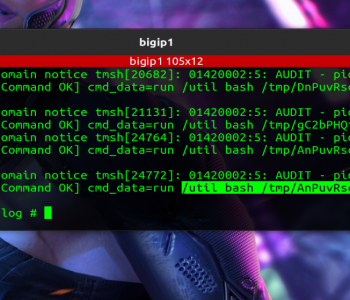
Defense
Defense
Lack of HTTPS does not automatically mean that you…
An industry mainly filled with good people but too many sharks
It’s becoming more and more common, I see content posted online, I hear people in meetings (hell I’ve been invited into some ‘opportunities’) and the basic theme seems to be:
- Fill your profile with as many buzzwords as possible
- Try and make your organisation seems legit and have links to the police and security services
- Call out crazy stuff like the lack of HTTPS as “TOTALLY COMPROMISED”
- Ignore science
- Post sales adverts under Security Services and Police posts to leach ‘authority’
- Constantly use statistics to back up their position
- Use social swarming (multiple people from the same company will rally around to defend/attack someone who questions the narrative)