 Defense
Defense
CVE-2020-5902 Defensive Guidance (FAST publish)
This week’s been a whirlwind, once again teams of people scrambled to help defend networks from criminals trying to abuse CVE-2020-5902.
If you want to see this in action check out my video on youtube!
The main issue (other than the vulnerability itself (path traversal and unauthenticated remote code execution) is exposing management interfaces to the internet (or other insecure/untrusted networks). Yesterday we looked at IOCs in the “/var/log/audit” file.
Now a sensible attacker who has ROOT level access would have likely cleared their tracks! However, a good sysadmin would have the logs shipped off the device!
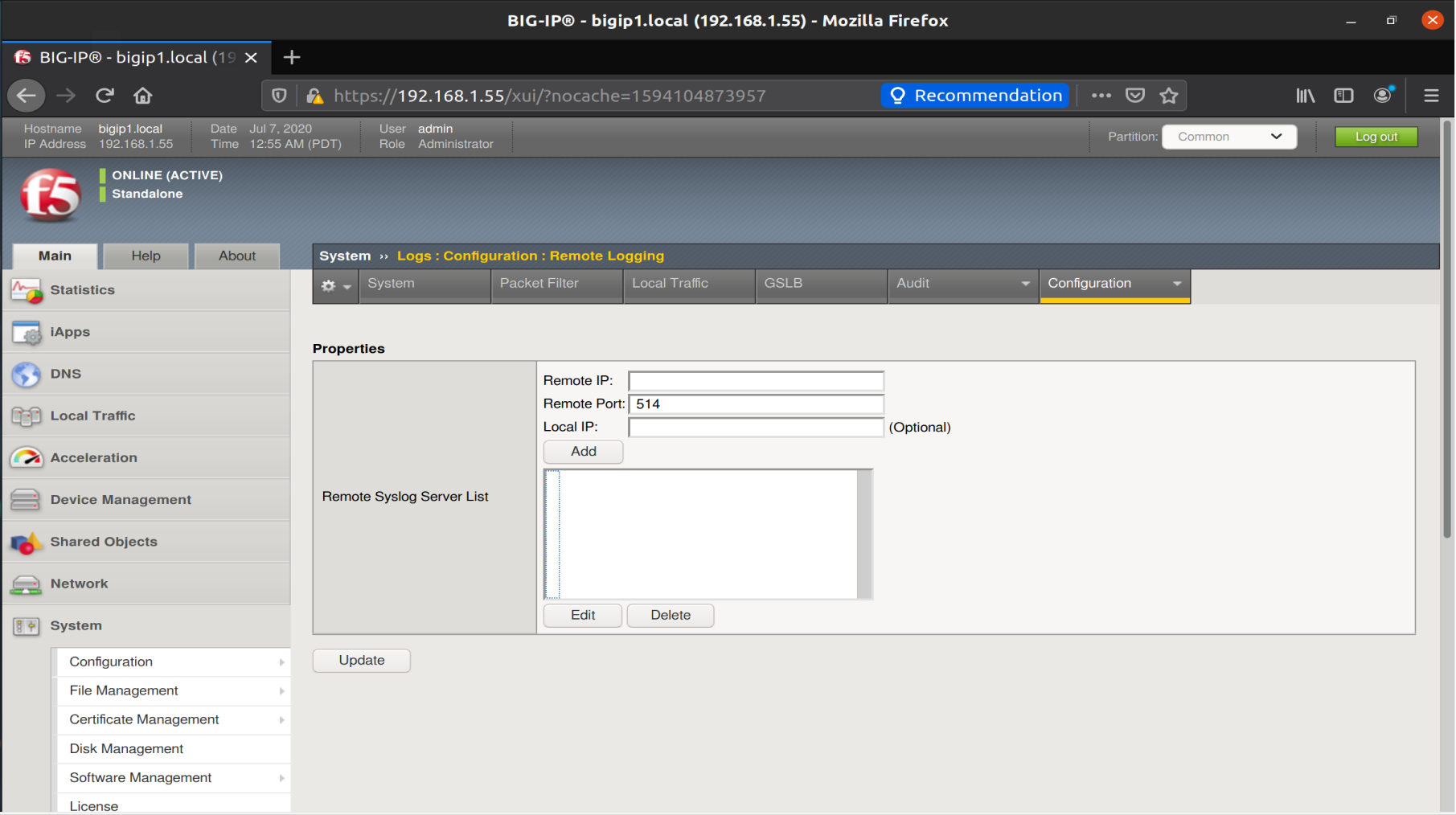
We can configure a forwarder to a remote SYSLOG server.
In this lab I’m going to FORWARD to a recently deployed SPLUNK enterprise server (running on UBUNTU)
| wget -O splunk-8.0.4.1-ab7a85abaa98-linux-2.6-amd64.deb ‘https://www.splunk.com/bin/splunk/DownloadActivityServlet?architecture=x86_64&platform=linux&version=8.0.4.1&product=splunk&filename=splunk-8.0.4.1-ab7a85abaa98-linux-2.6-amd64.deb&wget=true’ |
Now let’s install the deb file with dpkg
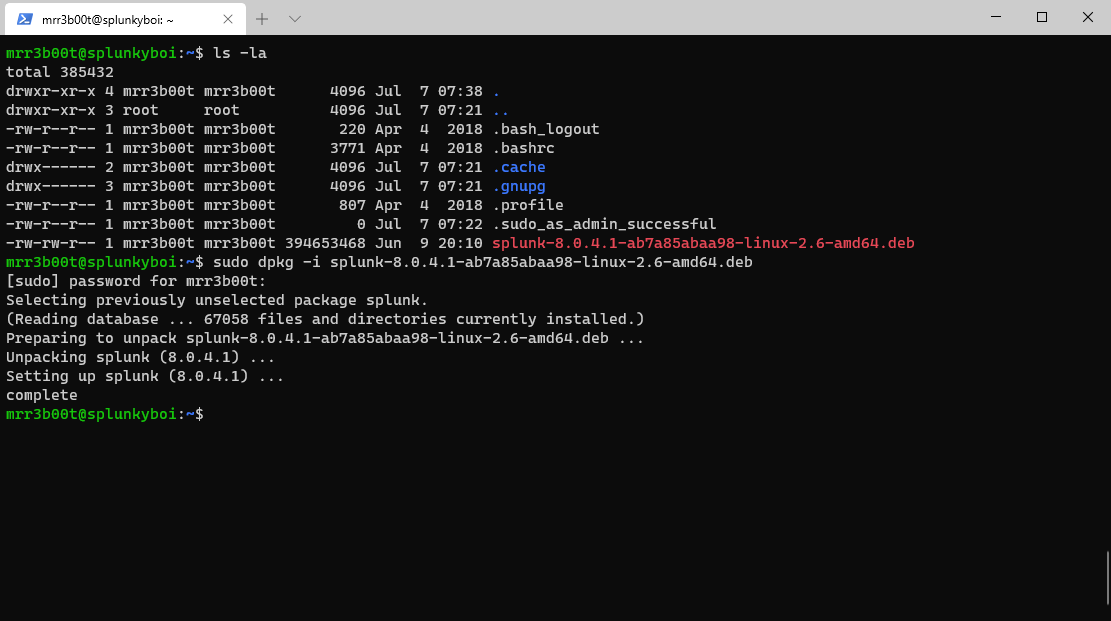
| sudo /opt/splunk/bin/splunk enable boot-start |
Now we need to setup splunk
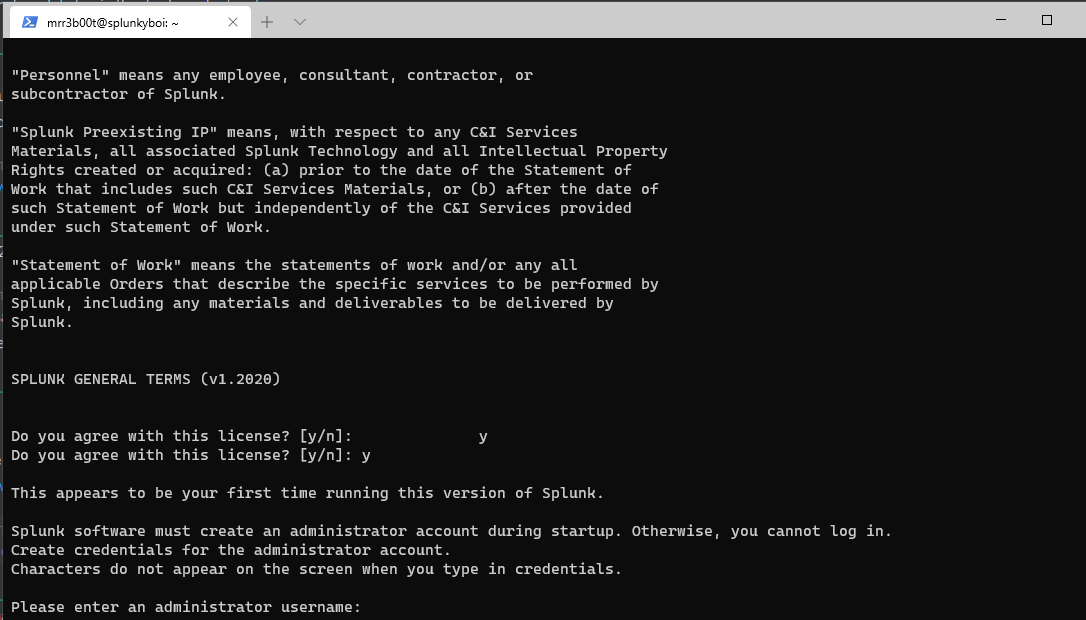
(configure a username and password)
Start the service at boot
| sudo service splunk start |
Visit the service using a web browser (it will be on port TCP 8000)

We are going to add a data source from the network
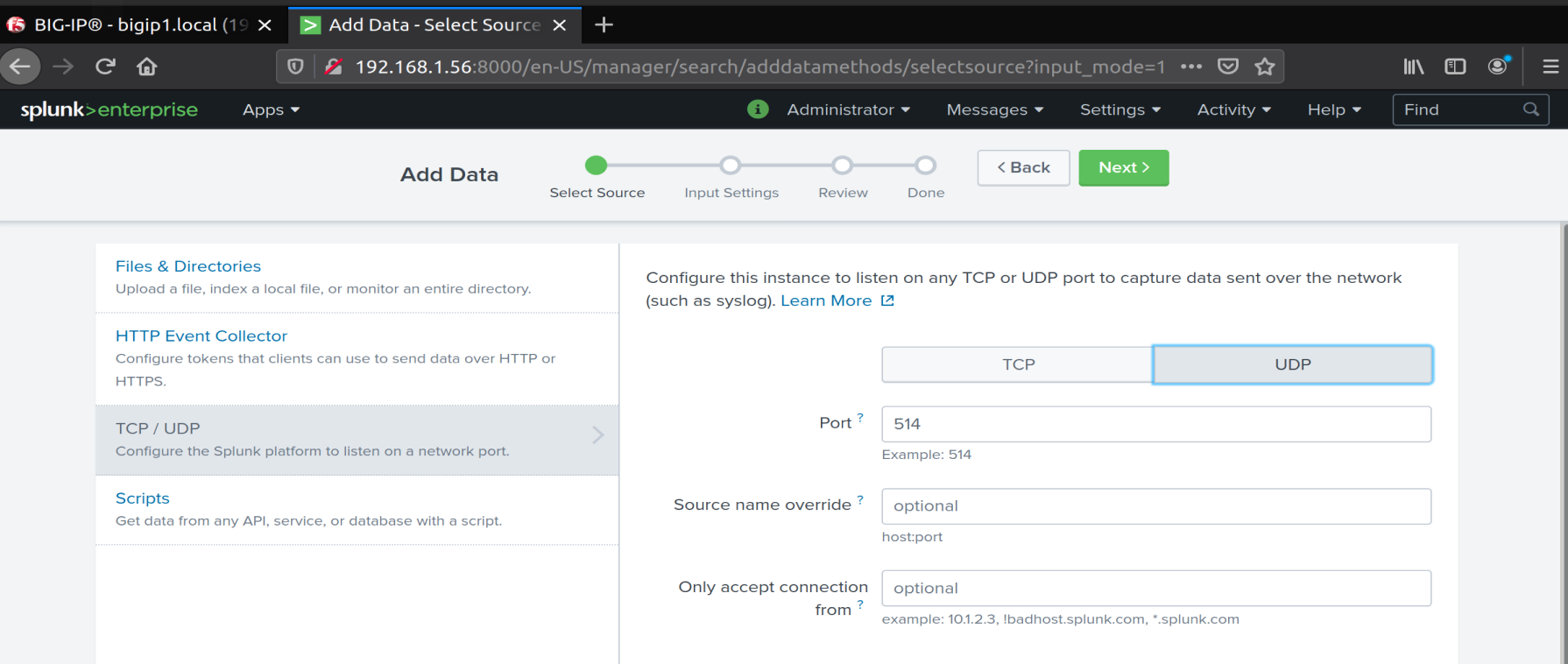
We configure a UDP listener on UDP 514
We configure the source as SYSLOG
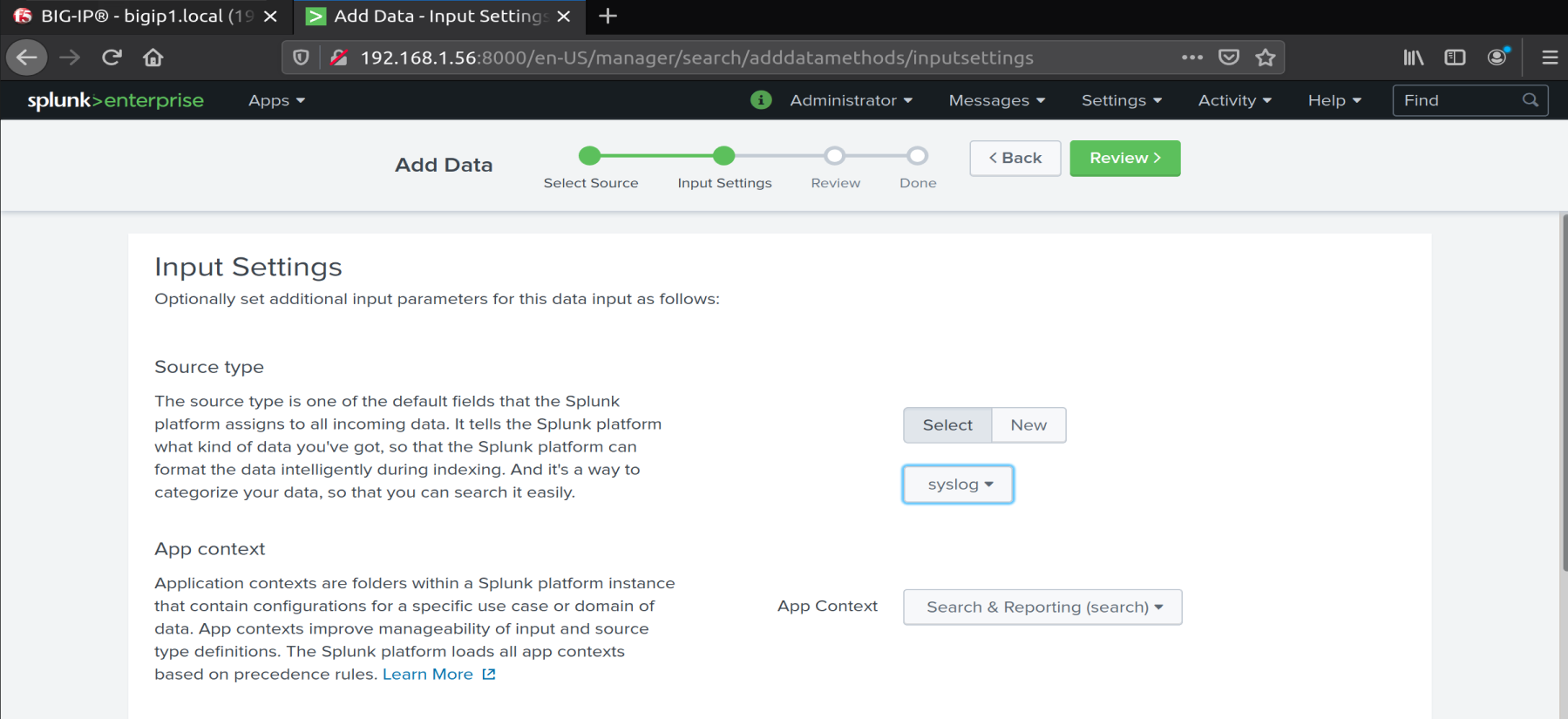
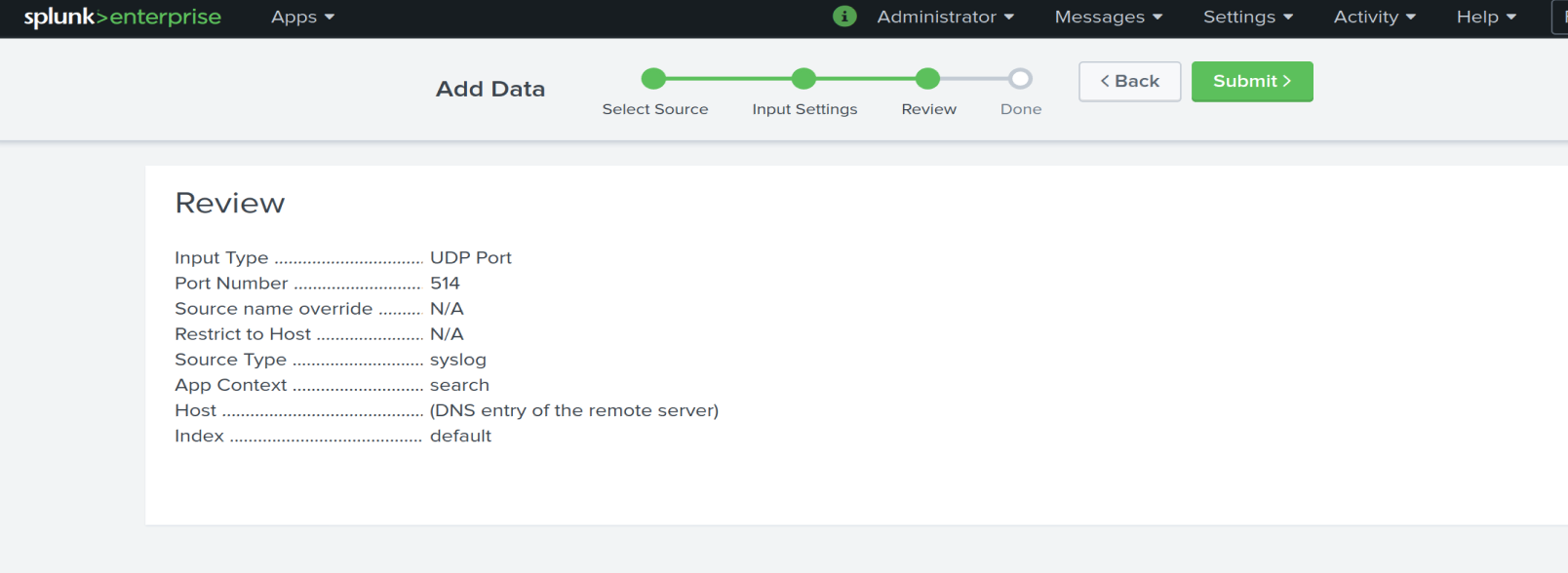
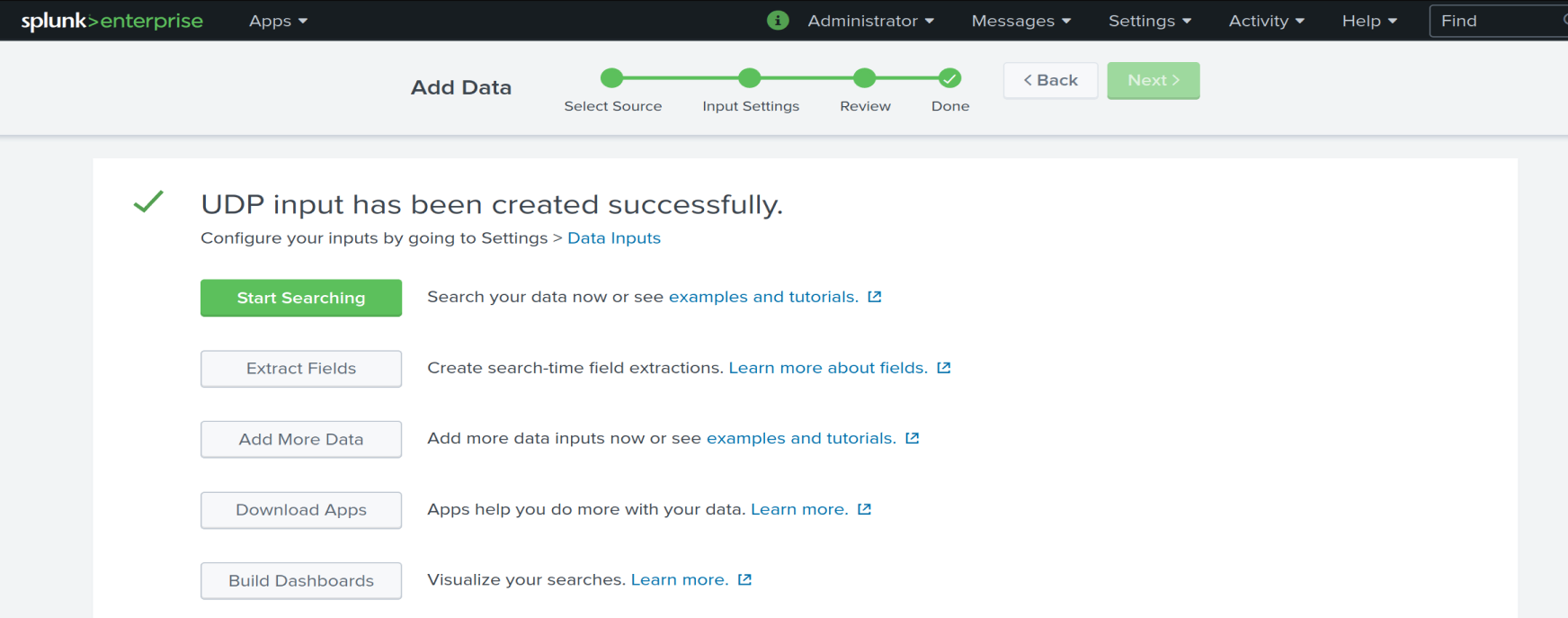
Success!
Now let’s configure our server to send AUDIT Logs
To start with we configure remote logging:
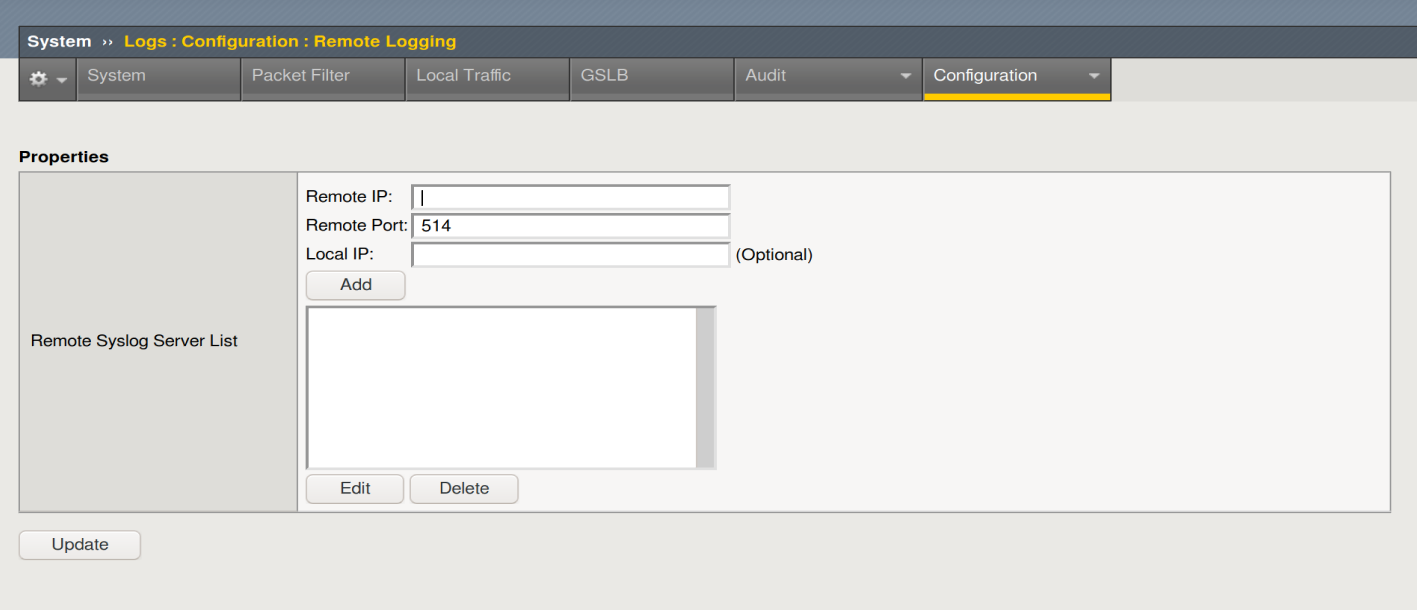
We enter the IP and click Add
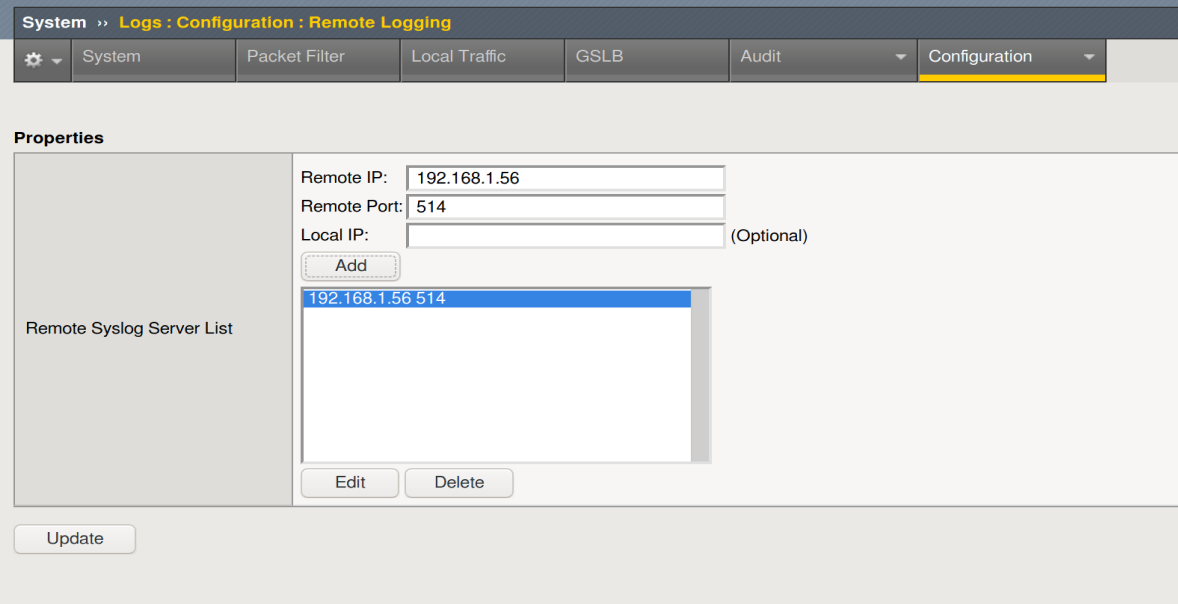
Then Update

Now back on the SPLUNK Server
We search for
| Source=”upd:514” sourcetype=”syslog” |
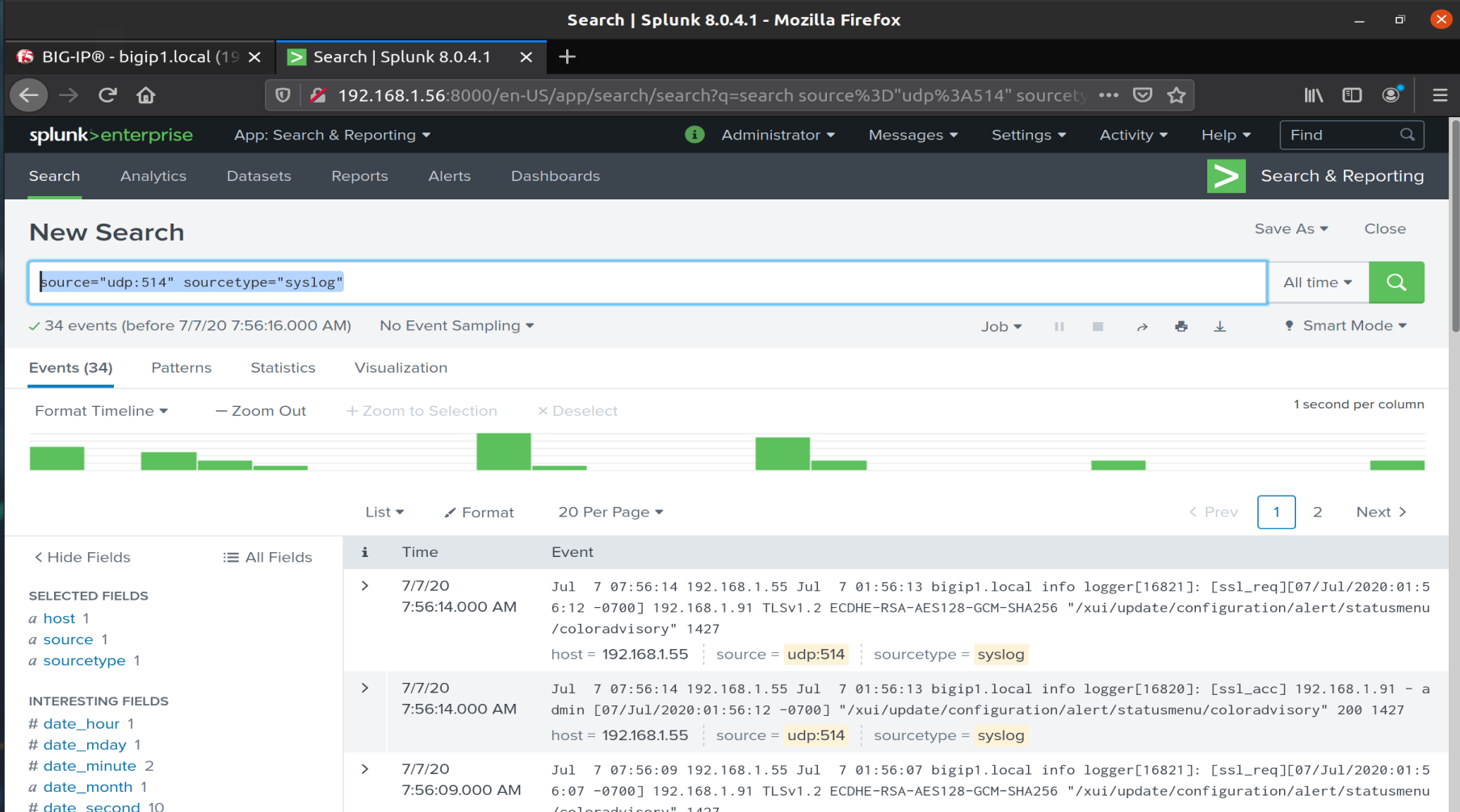
We launch the exploit and again we can see this in the logs:
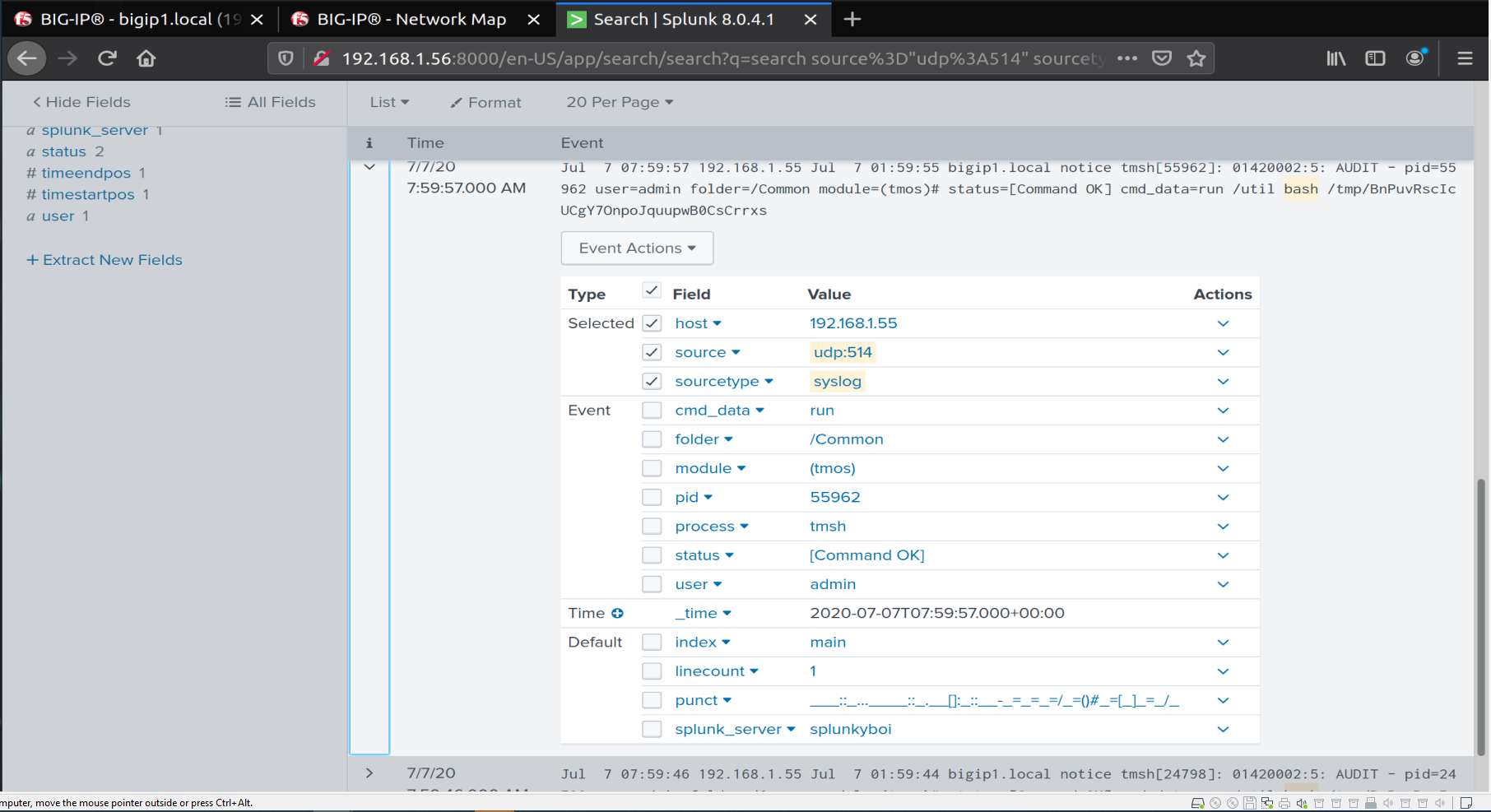
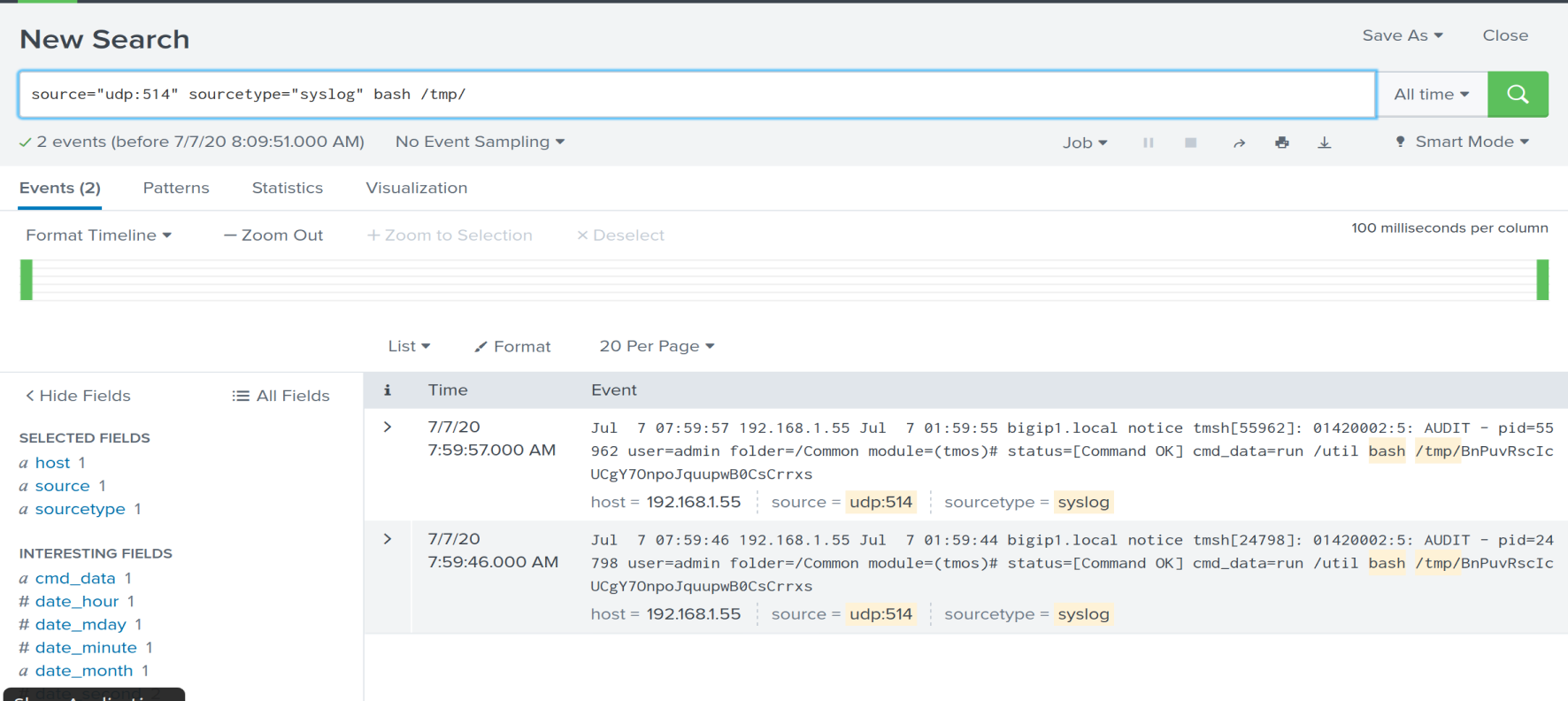
So here we have a method of shipping our logs from the BIG-IP to a SYSLOG server (in this instance I used SPLUNK).
Running a SYSLOG/SIEM solution isn’t a two minute job and there’s a lot more to think about, however the purpose of this was to show how you might use a remote SYSLOG server to monitor your F5 BIG-IP devices!
This isn’t the only method, there may even be SPLUNK integration (I’ve not had time to check!) but this was a quick way of showing you (as you might want to use another log tool like GrayLog etc.)
Be safe, be secure!









