Defense
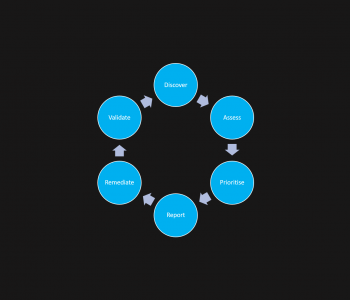
Defense
Aggressively Defending Information Systems
Taking a more active approach
You may have seen my post on hacking back and how it’s a nightmare that screams inexperience when I hear it (don’t get me wrong there are very limited times when it might be useful from a national defence perspective/intelligence services but that isn’t really ‘hacking back’ in my book, they are already working that space so it’s not a retaliation) however I’ve been spurred on this morning by a tweet I saw from @1njection:
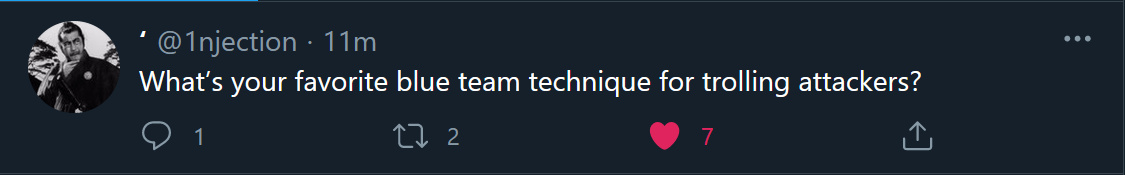
After tweeting a quick reply, I thought I had put together a quick blog on aggressive active defences! (not wordy much). Read more “Aggressively Defending Information Systems”