 Defense
Defense
Weapons Free
Cyber warfare, it may sound like something out of a fictional book or science fiction film but in the modern digital age it is a reality. 24 hours a day around the world there are information wars occurring ranging from civilian domestic style events through to military operated campaigns.
Honeypot Data
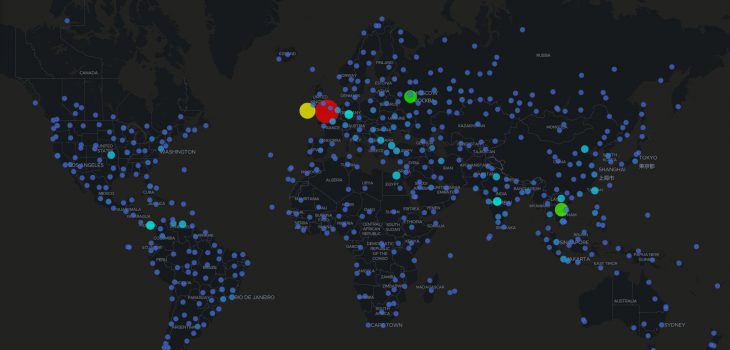
I run a range of honeypots from a t-pot instance through to bespoke services created to look good enough to fool even someone with a keen eye. I then use open-source intelligence gathering and data enrichment techniques (just as we would during an investigation) to look back at the attackers.
Looking at our aggressors
Aggressor infrastructure is a range of node types often you will see very similar patterns:
- Victim Servers (commonly with RDP exposed)
- Botnets (VCRs, IoT devices etc.)
- Proxies and VPNs
- Static Proxies & VPNS
- TOR
- Rotating Proxy Services
- Command and Control Infrastructure
Common Foes
Cybercrime has a distinct advantage over traditional crime in that it has no boundaries, and you don’t need to be physically adjacent. Different countries have different stances on cybercrime. Commonly you will see the following countries named:
- China
- Russia
- Iran
- North
- Korea
You may hear of these countries referred to as CRINK. Its important to recognise that there are geo-political and legal considerations to be made when dealing with cross border cybercrime.
What is the definition of a Cyber Attack?
Honestly, that depends on who you ask. I have seen people refer to port scans as cyber attacks (a poor take in my opinion) through to physical damage caused by malicious abuse of computer systems (e.g., Stuxnet).
Common cyber threats include:
- Phishing
- Credential Stuffing
- Denial of Service (DoS) or Distributed Denial of Services (DDoS)
- Credential Theft
- Brute Force Attacks
- Identify Theft via methods involving computers
- Resource Theft (e.g., Crypto mining)
- Ransomware
The tools, techniques, and practises for these may vary but they all result in the abuse of a digital system for someone else’s gain.
The NIST definition of a cyber-attack is as follows:
An attack, via cyberspace, targeting an enterprise’s use of cyberspace for the purpose of disrupting, disabling, destroying, or maliciously controlling a computing environment/infrastructure; or destroying the integrity of the data or stealing controlled information.
The key point here for me is the intent elements (something shockingly lacking from the current UK Computer Misuse Act (CMA)) as we see purpose and malicious being mentioned. An intentional malicious act involving the use of digital systems to me is a key element of understanding the difference between a mistake, research, and a cyber-attack. (getting that understanding right is key in my opinion if we are ever going to be able to get off the back foot)
Policy, Military, or Intelligence Services
Broadly speaking we have three type of services, civilian (police), military (a range of agencies or services e.g., Army, Specialist Regiments etc.) and the intelligence services.
So that means we need to consider cyber from different perspectives such as:
- Criminal
- Espionage
- Act of War
Real Life Incidents and Kill Chains
Lockheed Martin (famously) registered the CYBER KILL CHAIN as a trademark which describes 7 stages of activities to describe the actions of threat actors as part of a cyber incident which looks something like this:
- Recon
- Weaponization
- Delivery
- Exploitation
- Installation
- Command Control (C2)
- Action on Objectives
(see https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html)
The reality is that incidents are not linear and are not always ‘one hit’ events so there is a cycle from both an attacker and defender perspective. You will also find chains; one orgs incident might also be a platform for the attacks to continue downstream and conduct additional operations against different organisations. All in all, when you combine the complexity of computer systems, the vast potential of threats, the massive variety in potential avenues and routes you can likely see how this is starting to become very murky at the technical level. But what if we also then consider the physical domain? Not only do we have to consider cyber-attacks on equipment and services (think Stuxnet) but also what about responses?
A Kinetic Response
We now live in an age where kinetic response to cyber threats have been publicly acknowledged:
https://www.cyberscoop.com/hamas-cyberattack-israel-air-strikes/
https://en.wikipedia.org/wiki/Junaid_Hussain
This opens up a world of debate about the cross over between kinetic warfare and cyberwar. It means we now have to consider questions such as:
- Are pre-emptive kinetic strikes to prevent large impact cyber-attacks acceptable?
- What is an appropriate kinetic response?
- What level of evidence and assurance is required?
- What are the international rules for cyber warfare?
- How does this all tie together with human rights?
And thousands if not more questions remain. I am not going to even pretend to think I have any real answers for these, each question brings a flood more questions.
Attribution is hard
This is a statement you will hear a lot from many industry professionals because quite simply it is true. Public virtual private networks (vpn), proxies, private tunnels, owned systems, and the very nature of code means that being able to attribute a cyber incident to a real-life person or entity is incredibly hard.
Circling back to our questions on Kinetic response the Grugq tweeted this:
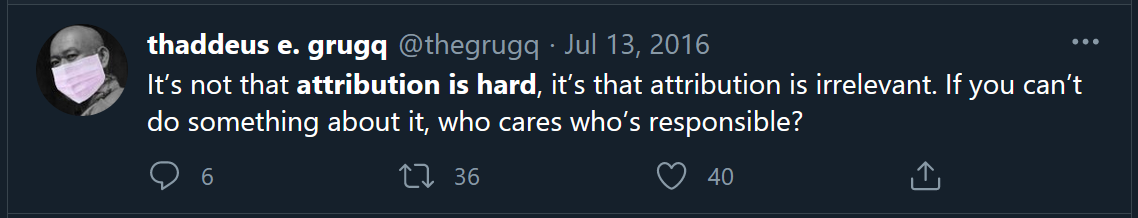
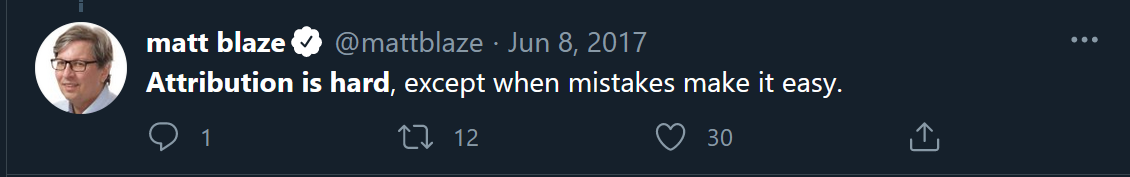
Whilst there can be some nuance in the view of “Attribution is hard” (because sometimes it is not!) in reality the time’s it is not hard are the exception not the rule.
A proportional response
Even if we could attribute back (in the cases where humans make mistakes so bad that it is conclusive who the perpetrator is) how can we determine the appropriate response? Do you know? Is there a clear definition of this? I would suggest that is a very grey and murky space.
An Eye for an Eye
It is an old saying but in the cyber real how do we feel about equal responses? Is an eye for an eye acceptable? They ransomware us so we ransomware them back? How do we draw the line? What if our actions in cyberspace cause damage in the physical domain?
When does police work and intelligence gathering turn into hostile activity? Do we send the army after criminals in everyday life? No, we send the police. The challenge with cyber security is that because it is a cross border affair that introduces a world of challenges.
A path of escalation
Take this as an example:
A known cybercrime gang operating from another country ransomware a hospital, the impact of this incident is massive and during the incident timespan some patients lose their lives.
What happens next? Do we rain hellfire missiles down?
If you think you know a good answer to this that does not lead to total war, I would love to hear it.
To me there needs to be restraint, there needs to be intelligence gathering and police work not military action. Before we run off to cyber war we need to actually learn as a race how to deploy technology in a safe and secure manner. Most organisations do not have the appropriate resources (funds) in their business plans let alone the skills needed to defend against common commodity cyber threats, the constant rush for ‘better, faster, cheaper’ and the abstraction (or ignorance) of complexity has left most organisations at quite significant risk from a range of threats (human error and cyber criminals being the most likely).
How can we be talking offense when I’m still seeing people and organisation get owned by fundamentally the same tactics and techniques that have been around forever?
Cyber Realities
So, do you still think that hacking back is a good idea? Do you think you could determine with a good degree of accuracy who your opposing force is and where they are actually operating from? Or would you more likely fire a ‘cyber weapon’ and hit an innocent bystander or another organisation or person that is simply an unwilling victim in the chain?
Do I think that hacking back is a good idea? For the majority of scenarios, hell no is the quick fast and consistent answer. There are however scenarios where I think hacking back is appropriate, the context and details for those however are incredibly complicated and I do not think I could even articulate clearly where I morally and ethically can explain how that works for me (at least at this time). I do not hack back, I do design scenarios in my company labs to explore this concept, but I am a white hat kind of guy and without a get out of jail card (a license to pwn if you were) I am leaving that very much in the hands of specialist units that are government sanctioned. It does not mean I will not keep exploring the concepts in the lab though.
Stay safe, stay legal and may the force be with you!






