Field Notes – Just Patch
Windows update stuck at 0% download status
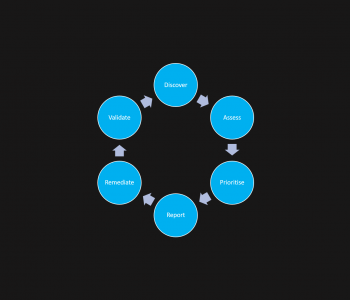
Often is we find an environment missing software updates it’s easy for someone without hands on experience to say, ‘just patch’. Outside of change requests, outside of authorisation, maintenance windows, roll back plans, communications etc. there is also the fact that ‘just patching’ isn’t that simple. Even for fairly standard patching tasks using Windows Updates you sometimes hit a snag. Today I’m looking at exactly that issue on a server, so I thought I’d post the steps to resolve an issue but also, I think this is a nice way to highlight the realities of patching.
We show a GUI and command line (PowerShell) method to achieve this result (the PowerShell isn’t fancy but I figured you could go away and upgrade that if you fancied some fun). Windows update sometimes has issues (does not all software!) and it is sometimes that we need to help it along the way, so let’s get too it! Read more “Field Notes – Just Patch”