 Defense
Defense
For vendor guidance please see:
https://www.vmware.com/security/advisories/VMSA-2021-0002.html
CVE Refs: CVE-2021-21972, CVE-2021-21973, CVE-2021-21974
Introduction
There’s a new unauthenticated remove code execution (RCE) in vSphere 6.5, 6.7 and 7.0 which has just dropped. There’s a vendor patch and currently there is no known public exploit however the hunt will now be on and I can imagine that it’s hours and days until this is in the wild rather than weeks or months.
What to do about this?
Well for one don’t expose this service to the internet. unfortunately, thousands of people may have been asleep for this part of virtualisation 101 training as we can see these all over the world on Shodan (don’t worry they won’t all be vulnerable to this exploit)
https://www.shodan.io/search?query=title%3A%22vsphere+web+client%22
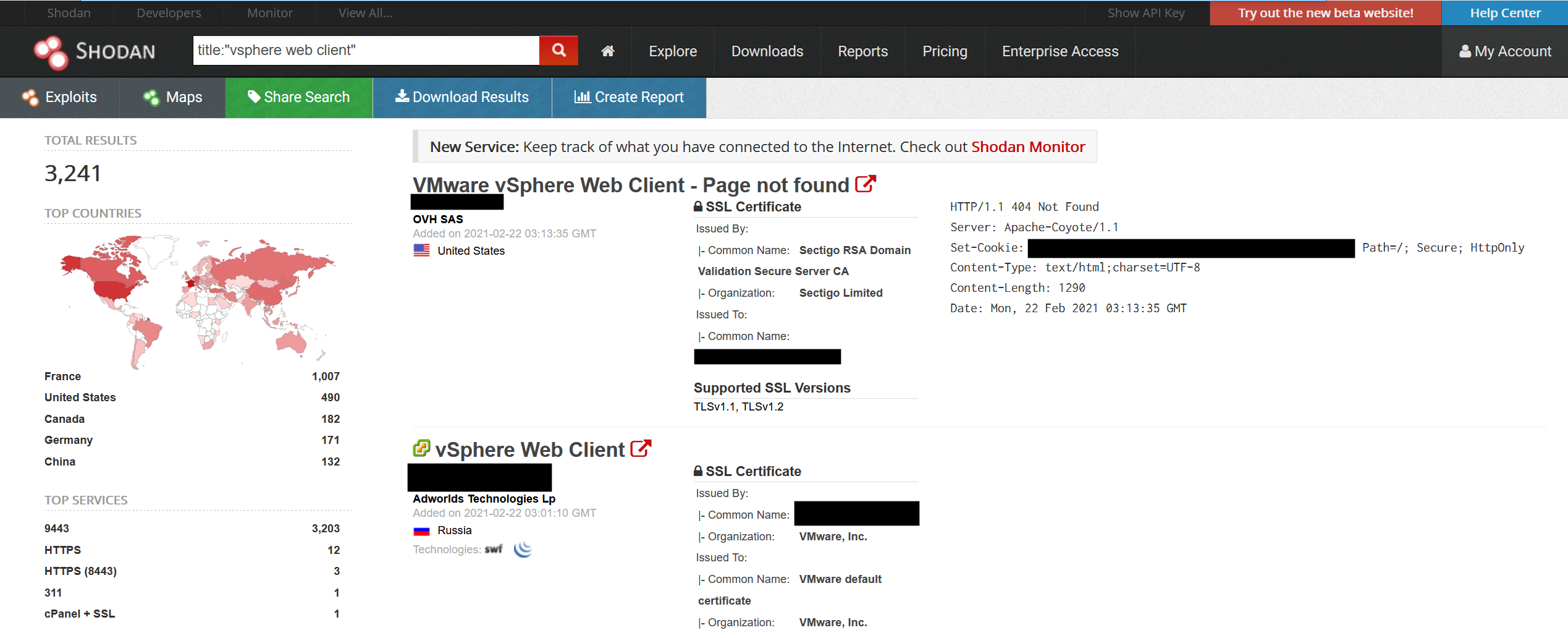
So, these are likely exposed on tcp 9443 or 443 however I’ve not done any fingerprinting so these may be versions that are not vulnerable (I’ve checked a few and they are using the non HTML5 gui so they are OLD!!!). I’m sure someone will post a nice hash or fingerprinting method shortly.
What do we do? Well review if these need to be internet facing for starters, shutting down that vector would stop them being exploitable from an internet facing perspective but then also patch the systems.
See nice and simple, use VPNs, jump boxes, and secure your critical infra and this type of vulnerability whilst major becomes far less of a headache. Leave this stuff exposed to the internet and you are either going to scramble resources or you might find yourself at the wrong end of a cybercriminal.
Remember stay safe, stay cyber secure and may the force be with you! and for gods sake stop exposing your critical infrastructure all over the internet, or don’t, but you can’t say we didn’t warn you!








