 Defense
Defense
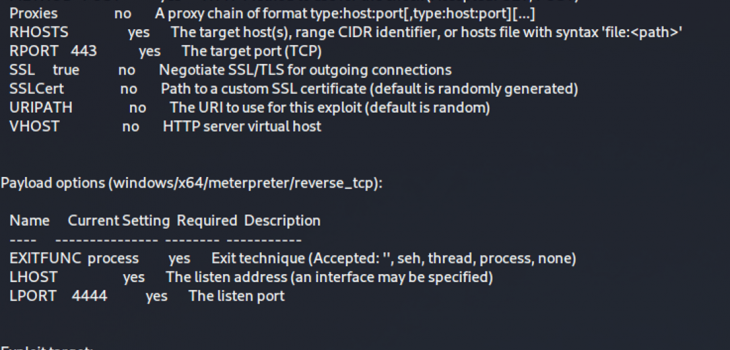
The last two weeks we’ve seen major activity around the world with defenders and criminals rushing to respond to the recent zero day vulnerability patches and then the race to reverse engineer the kill chain to create an explot. We saw a PoC fairly early but it required that you reverse engineer some exchange DLLs and/or TAP the 443 to 444 interface on an exchange server to work out how to weaponise it. Things however have progressed, 8 hours ago we saw a metasploit module go online:
We’ve got this spun up in the lab and are testing. So far we now have a working RCE exploit in the wild (python) and now an MSF module.
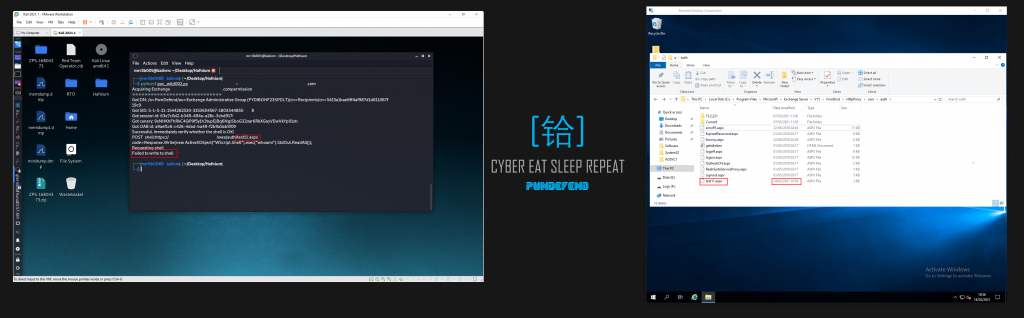
The main attack vectors we are seeing are:
- Webshell takeover
- RCE Exploitation of the vulnerabilities
Actions on we have seen so far include:
- Phishing
- Crypto mining
- Ransomware deployment (DearCry)
- Account/Active Directory Takeover/Resets
- Defence disablement
For the exploits to work the attacker needs:
- A valid mailbox
- The exchange server to be vulnerable or not well defended
- The valid mailbox can be administrator (so a single mailbox name can produce an RCE)
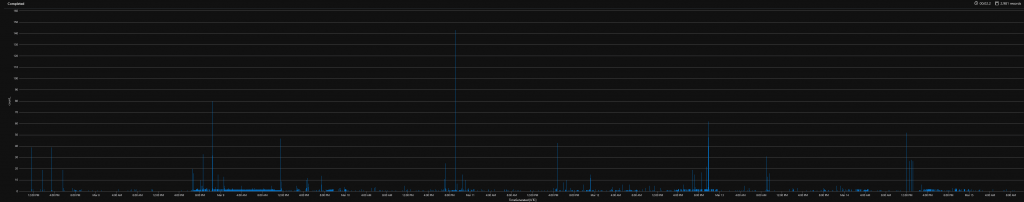
HoneyPot Activity
We aren’t seeing alot of evil in the honeypot we deployed. We have mainly got security firms scanning using get requests for common webshells and looking for signs of vulnerabilities. So far we haven’t caught a criminal. The HoneyPot is located in the UK, we will continue to monitor and update on the situation.
Summary
It’s been reported that activity from Hafnium for this kill chain occured as early as January the 3rd, we’ve seen UK activity on the 27th January and given the timeline of events, the ease of exploitation and the massive range of vulnerable Exchange servers still online I can foresee this being a bumpy ride for a number of organisations.
The key actions here are to ensure you have patched, that your exchange services are running antimalware, that you conduct a thorough investigastion and digital forensic analysis. If a threat actor has got RCE then they will likely not have simply dropped a webshell and forgotten about it!







