 Threat Intel
Threat Intel
This is an evolving post and will likely be updated over time. Online “community” or “criminal gangs” etc. can be fluin and dynamic, thinking of them in rigid structures and trying to compare them to “In Real Life (IRL)” organisationas directly doesn’t really work. They work generally in a collective fashion. No masters and no slaves etc.
“Hacker” Groups
I don’t really like to use the term “hacker” in this sense, perhaps hacktivist or criminal groups is the right fit, however, words aside there is the question: Who is KILLNET, are they a threat and who are they a threat to?
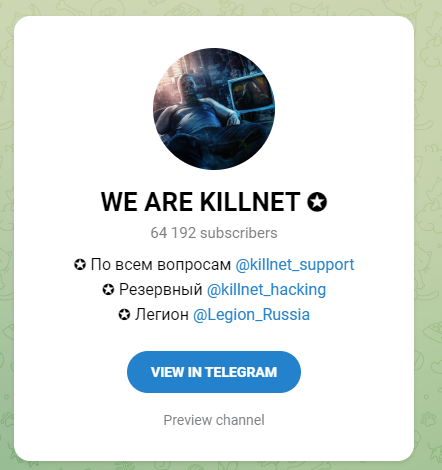
Who is KILLNET?
KILLNET was suposedly formed as a resonse to the IT ARMY of Ukraine (Ukraine Cybe Army) (formed late Feb) which is odd given the first post from KILLNET was on January the 23rd and IT ARMY of UKRAINE setup their telegram on Feb 26th.
The number of “members” of KILLNET is probably hard to determine, in their “main” telegram channel they have over 60K members. This isn’t really that many though.
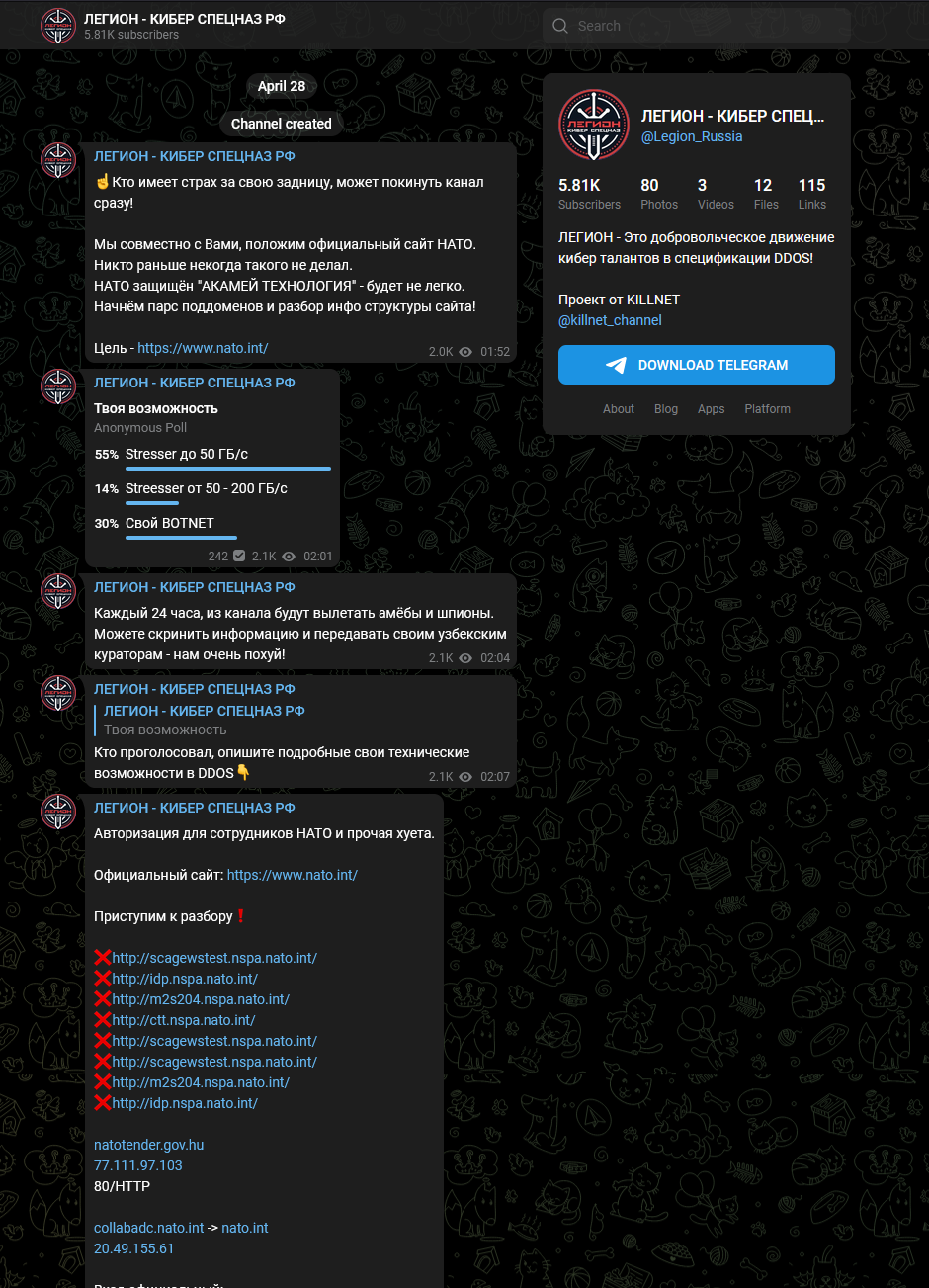
There’s also the fact it’s split into killnet hacking and Legion Russia, and then further into other subgroups.
High Level Assessment
Given how “easy” attribution and monitoring threats in cyberspace is (NOT) it’s hard to say:
- Who operated the group
- Who is active in the group
- What their capabilities are at a given point in time
However I’ve put together a high level summary view based on what i’ve seen so far.
|
Group Name |
KILLNET |
|
Estimated Skill Level |
Low |
| Estimated Capability Level |
Low |
| Risk Estimate |
Low |
| Historic Impact Estimate |
Low |
|
Country/Regional Alignment |
Russia |
| General Cyber Threat Assessment level | Low (if you aren’t in the target bracket and/or if you have CDNs/DoS Protections) |
|
Known for |
Denial of Service (DoS) |
|
Alternate Names/Pseudonyms |
“Cyber Army of Russia” |
|
Website |
killweb.io |
| Currently Targetting | Romania |
| Broadly Targeting | Countries supporting Ukraine/The West/NATO |
| Possible Future Targets | Italy (based on telegram posts), POLAND |
|
Assessment Confidence |
Low-Moderate |
| Summary | The pottential for impact could be high for a specific org if they are targetted and have not taken steps to put in place DoS protections. The nature of these style of groups means the capability and skill levels can be significantl varied and dynamic. It should be noted that the risk level to your organisation may signifcantly vary based on geography, political alignment, nature of business and the infrastrctuure, capabilities and controls you have in place to mitigate DoS etc. |
The groups noise level vs confirmed impact leads me to believe currently this group is not a significant threat to organisations. Whilst there appears to be intent and motivation, I would be surprised given the inception date and the lack of “confirmed” activity outside of claimed denial of service that this group pose a significant threat beyond any other generic hacktivist or criminal organisation at this time. Clearly that may change, online groups can just as easily change tactics and personnel due to their fluid nature.
Their MO appears to be DoS against very specific orgs, if you are a likely candidate for “targeting” it would be prudent to take measures against the DoS and ensure you have adequate controls and practised proceedures in place to absorb, mitigate or respond to a DoS attack.
Who are KILLNET?
KILLNET appears to be a loosely grouped together PRO RUSSIAN group of actors.
What have they done?
They have claimed to have conducted Denial of Service (DoS) Attacks.
Have they had any real negative impact?
Currently the only real significant impact I’ve seen is they are in mainstream newspapers. They don’t appear to be highly effective from achieving cyber impact.
That being said the romanian security directorate has issued guidance:
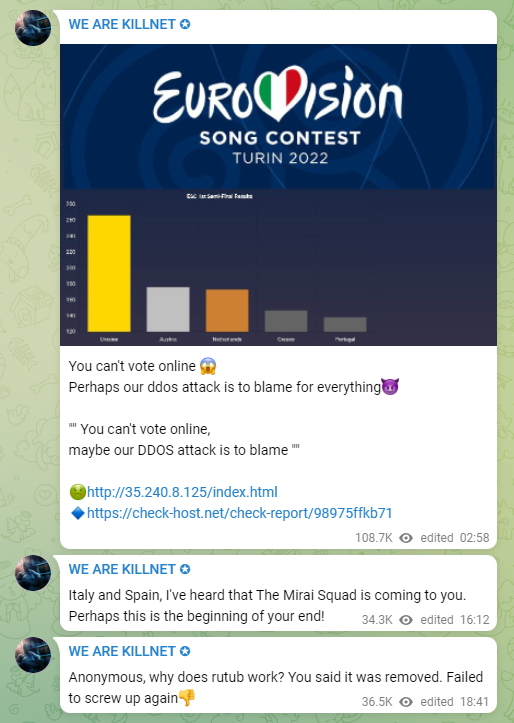
They have claimed to attempt to cause disruption to the EUROVISION song contest, but this failed (oh no! anyway!):
Russian hackers declare war on 10 countries after failed Eurovision DDoS attack | IT PRO
Italian police block Russian hackers during Eurovision | News | IBC
this seems entirely not news worthy, but that’s just well my opinion!
There is an incident or two in Romania:
Romanian government says websites attacked by pro-Russian group – The Record by Recorded Future
Now this looks like DoS:
The https://dnsc.ro/ site isn’t currently online from the UK (will check from Romania soon) so that might indicate some impact (or another event!)
Who are they aligned to?
- Their telegram channel is written in the Russian language.
- Their messaging is PRO Russian.
When did they appear?
Their telegram channel was created on January 23rd 2022
Links
https[:]//twitter.com/KILLNET_LEGION
Possible Affiliates
Capability Level
The reason why i’ve currently rated the capability/skill as low is for a number of reasons:
- They don’t appear to be equiping “members” in an adanced manner
- A number of the attempted DoS “attacks” have failed
- Currently I’ve not seen evidence of custom tooling
- The volume of members does not appear to be high
Contrast this with the Ukraine Cyber Army which has 350 Thousand Telegram channel members, deploys custom tooling to aid it’s members and who have had demonstrable impact on it’s targets.
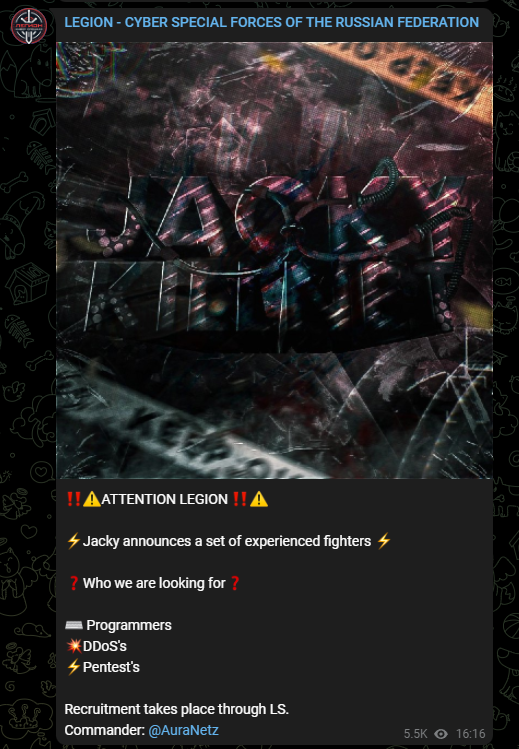
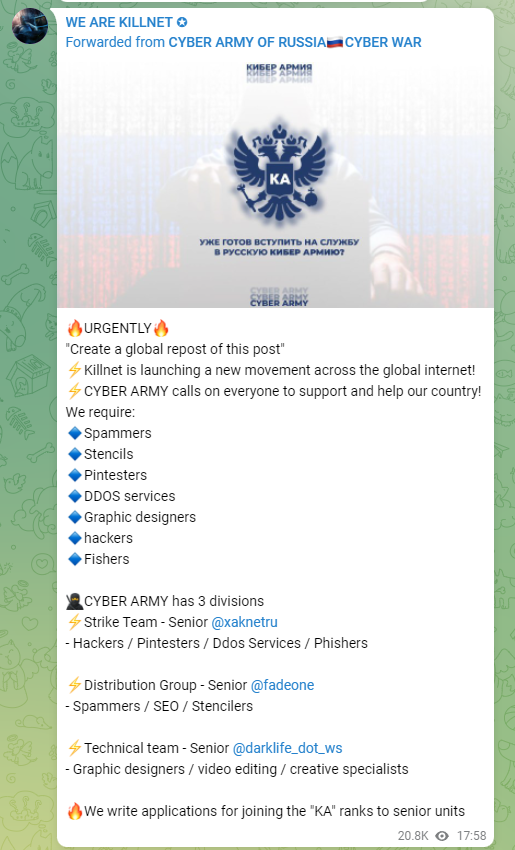
On May 17th 2022 they are advertising for Programmers, members to perform DDoS and Pentesters (everyone in CYBER has a skills gap right!):
DoS IoC Analysis
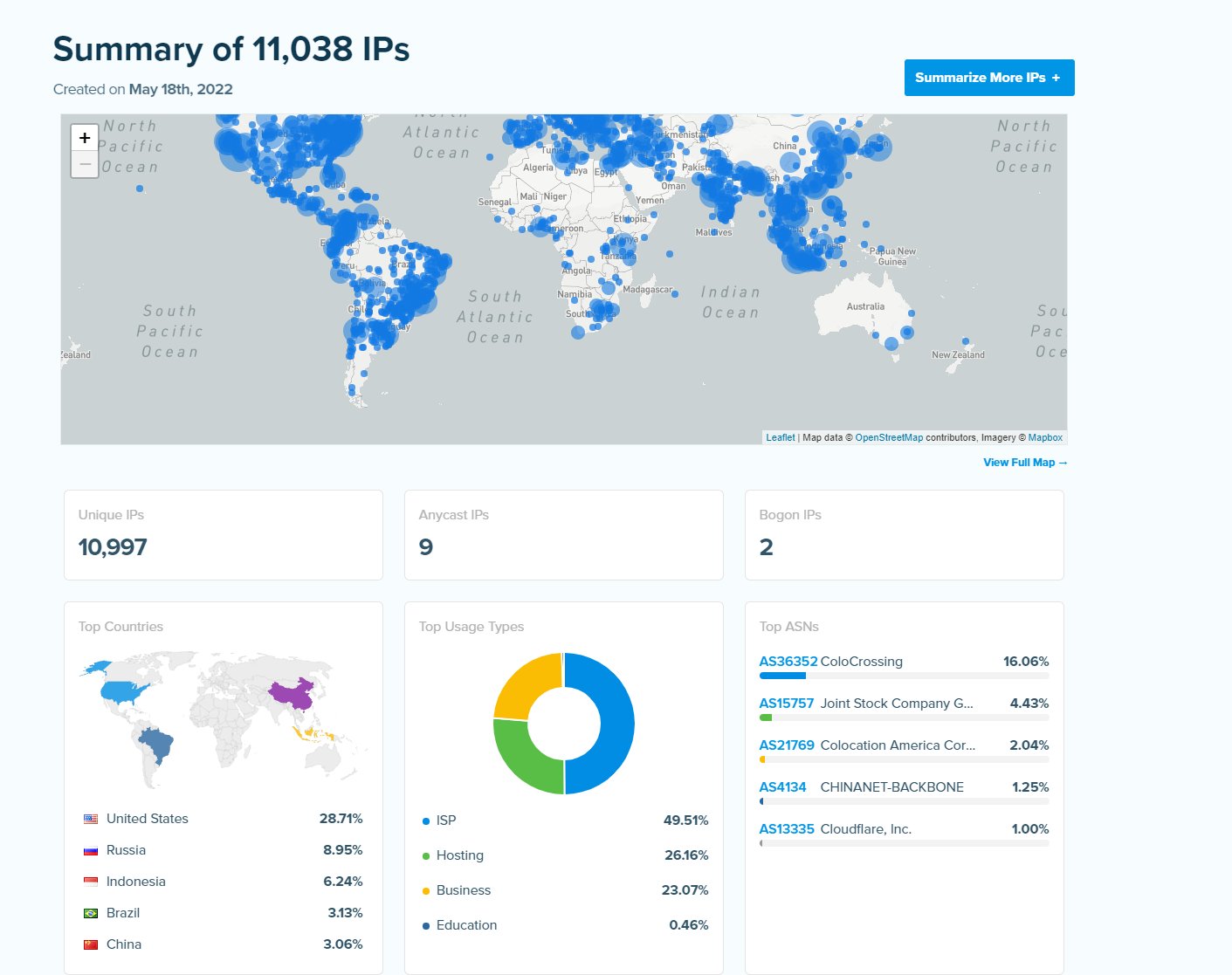
We are conducting metadata analysis on public IOCs from a limited successful Denail of Service (4 hoours downtime) reportedly by KILLNET. A quick analysis using Greynoise and IPINFO shows that some of these appear to be beniign, some are known “bad” in greynoise etc. Outside of that we can see evidence of traffic from proxies and “unknown” IPs at a scale that appears to line up with the DoS position.
The romain goverment site is now geofenced for internal romaining traffic only.
The DoS sources appear to be from ~11K IPs, we have not yet enriched all of these however a sample from a clust of IPS shows that a proxy network was leveraged which resides in: AS36352
This is currently listed as: COLOCROSSING
COLOCROSSING do not appear to have a great reputation in the community and are beleived to have been reported to have been hosting infrastrcuture that may have been used in previous DoS attacks.
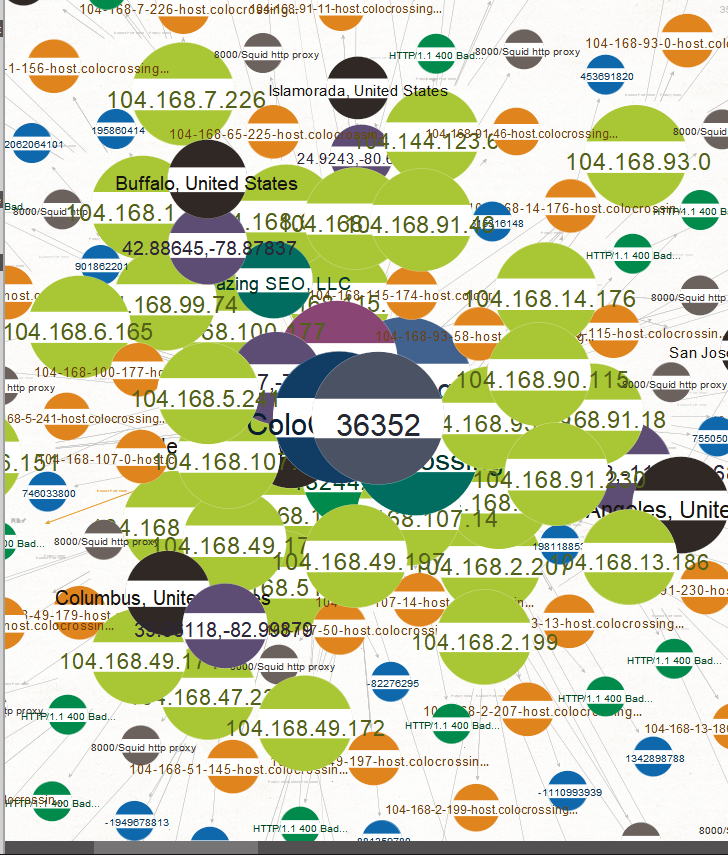
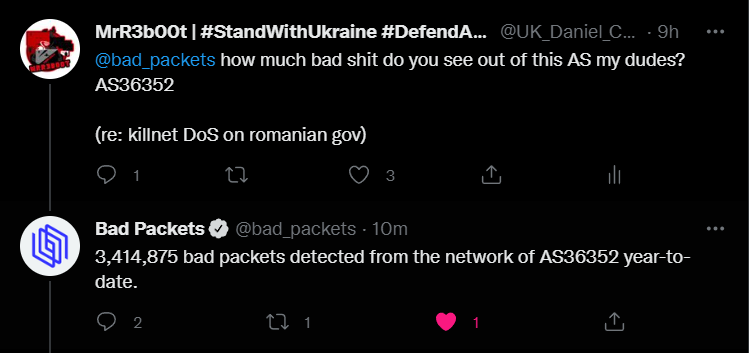
This hosting provider and AS has historic evidence of abuse. An example of that is here: DraftKings Continues Pursuit of DDoS Attackers – Flushdraw.net
As such it’s probably not a bad idea to block traffic from this AS.
Sample Evidence
Targets
According to this article:
The Killnet group threatens to cyberattack nearly 300 other sites in Romania – HotNews.ro
The list of targeted sites so far is:
realitatea.net
tvdiaspora.ro
etnictv.ro
dibitv.ro
mioritatv.ro
orizont.tv
ercis.ro
romaniatv.net
b1tv.ro
antena3.ro
tvgo.orange.ro
kanald.ro
tvgo.orange.ro
digi24.ro
tvrplus.ro
alephnews.ro
smartv.media
alephbusiness.ro
agro-tv.ro
primatv.ro
netstreaming.eu
nasul.tv
trinitas.tv
credo.tv
sperantatv.ro
alfaomega.tv
a7tv.ro
angelustv.ro
stirileprotv.ro
mooz.tv
radiozu.ro
ercis.ro
btv.ro
inedittv.ro
live.novapress.ro
ogradatv.com
profit.ro
jobtv.ro
twitch.tv
tezaurtv.ro
qubtv.ro
atomictv.ro
informatiatv.ro
twitch.tv
musceltv.ro
realitateasportiva.net
realitateastar.net
hd365.tv
tvtotal.ro
moldovatv.ro
autenticmediatv.ro
dottotv.ro
tvarad.ro
46.4.14.12/btvlive
dobrogea.tv
liratv.es
intermediatv.ro
curiertv.ro
exclusivtv.ro
rochannel.ro
kisstv.ro
protvplus.ro
privesc.eu
grt.md
trm.md
jurnaltv.md
realitatealive.md
tv8.md
n4.md
tezaur.mlbfan.org
publika.md
zonam.md
btv.md
eacea.ec.europa.eu
isjiasi.ro
isjcj.ro
ismb.edu.ro
edu.ro
ies-info.ro
britishcouncil.ro
isjb.ro
isjtulcea.ro
ise.ro
goethe.de
cylex.ro
ilr.ro
institutlevant.ro
insse.ro
colegiulgoethe.ro
lyceefrancais.ro
isjbrasov.ro
confucius.institute.ubbcluj.ro
edupedu.ro
usm.md
isjilfov.ro
isj.tm.edu.ro
wellbeing-institute.ro
isjdolj.ro
insp.gov.ro
destepti.ro
isjbn.ro
distanta.ro
isjbraila.ro
isjneamt.ro
sper.ro
proteo.cj.edu.ro
isjneamt.ro
univ-ovidius.ro
isj.hd.edu.ro
isj.educv.ro
institutulmontessori.ro
rist.ro
cnred.edu.ro
curtis.edu
edumanager.ro
iquads.ro
bari.mae.ro
iiccmer.ro
ices.acadiasi.org
lliacademy.ro
uad.ro
seminarulcaransebes.ro
scoala-sanitara-fundeni.ro
animv.ro
itsybitsy.ro
snspa.ro
deceit.site
sov.ro
mai.gov.ro
acttm.ro
brasovcity.ro
magazinulmilitar.ro
legislatie.just.ro
roarmy.adlunap.ro
scoalapolitie.ro
armataromaniei.ro
defense.ro
m.defenseromania.ro
rumaniamilitary.ro
military-shop.ro
military-surplus.ro
kaki.ro
m-force.ro
dpa.ro
navy.ro
armyacademy.ro
edu.ro
cybercommand.ro
mta.ro
camaraziimilitari.ro
armata-buzau.ro
armatasalvarii.ro
roaf.ro
geomil.ro
resboiu.ro
arhivelenationale.ro
echipamentemilitare.ro
mae.ro
forter.ro
sie.ro
afahc.ro
smmmsfa.ro
amazon.com
brcmn.ro
monitoruloficial.ro
historia.ro
spp.ro
romarm.ro
idr.ro
asap-romania.ro
bg15mc.ro
anmb.ro
careerromania.autoliv.com
clujarm.ro
dedeman.ro
kaufland.ro
auchan.ro
romania-auchan.ro
mega-image.ro
carrefour.ro
lidl.ro
issasupermarket.ro
profi.ro
penny.ro
supermercato.ro
metro.ro
posta-romana.ro
tribunalulbucuresti.ro
app-romania.ro
finantarepartide.ro
europarl.europa.eu
portal.just.ro
rezultatevot.ro
partidulnouaromanie.ro
proromaniaonline.ro
partidulverde.ro
pntcd.ro
pmponline.ro
surplus.ro
monitorulpartidelor.ro
romania.europalibera.org
ppusl.ro
udmr.ro
per.ro
partidul-pdu.ro
ctr.ro
pd.ro
eppgroup.eu
roaep.ro
nouadreapta.org
inovarepublica.ro
rotld.ro
lapartidlehliu.ro
activenews.ro
spitalgorj.ro
salvaticopii.ro
sanador.ro
hosptm.ro
spitalul-cantacuzino.ro
spitalulmonza.ro
reginamaria.ro
suub.ro
spitalultirda.ro
spitalcampina.ro
spitalulfilantropia.ro
spitalbarlad.ro
spitalul-elias.ro
stanleybet.ro
pariurix.ro
casino.com.ro
bogdancazino.ro
supercasino.ro
casinoonline.com
universuljuridic.ro
cora.ro
top-casino.ro
cazinoro.com
casino.org
unibet.ro
casino-netbet.com
trivago.ro
turistinfo.ro
romania-directbooking.ro
travelminit.ro
hotelsara.ro
anahotels.ro
continentalhotels.ro
ssr.ro
romania-actualitati.ro
romaniaradio.ro
virginradio.ro
europafm.ro
radiozu.ro
digifm.ro
guerrillaradio.ro
radioconstanta.ro
sts.ro
mai.ro mai.gov.ro
mapn.ro
gov.ro
politiaromana.ro
ms.ro
mfinante.ro
anaf.ro
jandarmeriaromana.ro
digi24.ro
www.engie.ro
www.orange.ro
protv.ro pntcd.ro
partidulaur.ro
vaccinare-covid.gov.ro
certificatcovid.gov.ro
romania2019.eu
mitropolia-banatului.ro
patriarhiaromana.ro
bcr.ro bnr.ro
raiffeisenbank.ro
bancatransilvania.ro
electricafurnizare.ro
ghiseul.ro
presidency.ro
psd.ro
pnl.ro
It might be interesting to see where that list came from, I’ve not found it in the Telgram channels so far (but i might have missed a sub group).
Summary
As you can see they are definatley not aligned with the WEST. However the volume of members when companred the UA Cyber Army is significantly smaller. The level of sophistication appears much lower as well as the level of tooling and co-ordination.
If you have any intel you want to share please get in touch. This was made during a cup of tea so take it for what it is, I might look at doing this against a range of groups.








