Vulnerability Management Realities
Trust but verify
Someone tells you they have fixed something, now go and check! You might find that it is not actually fixed, or that the ‘fix’ made the issue worse (or makes new vulnerabilities appear). You might however also find that the vuln is gone.
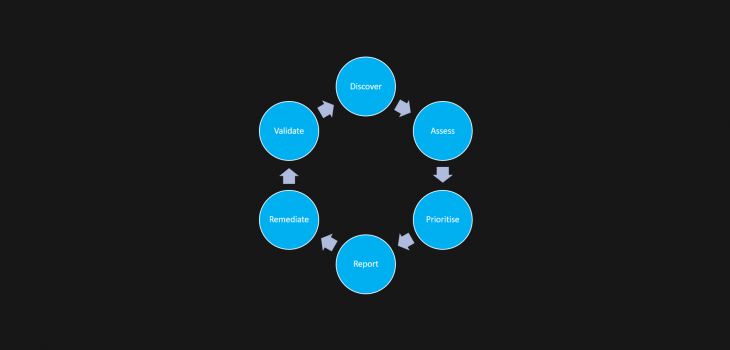
Wow so many options, but the reality is with this space is that you have to keep checking, you also need to validate.
Validation is key, people do not say that think it is fixed because they have not done something, we all have scenarios where we make a change, assume it works and then find out later that maybe a bit more testing would have helped (I have this too!). Read more “Vulnerability Management Realities”