ProxyLogon – A god mode backdoor even when used…
Imagine
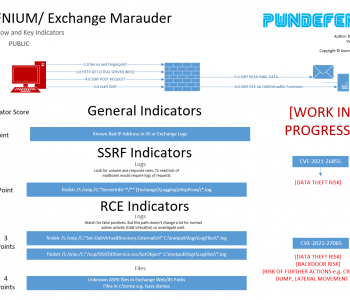
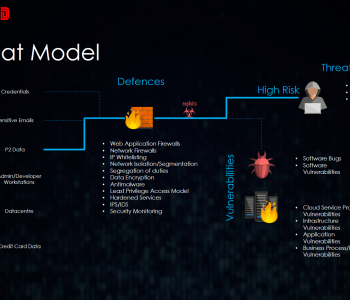
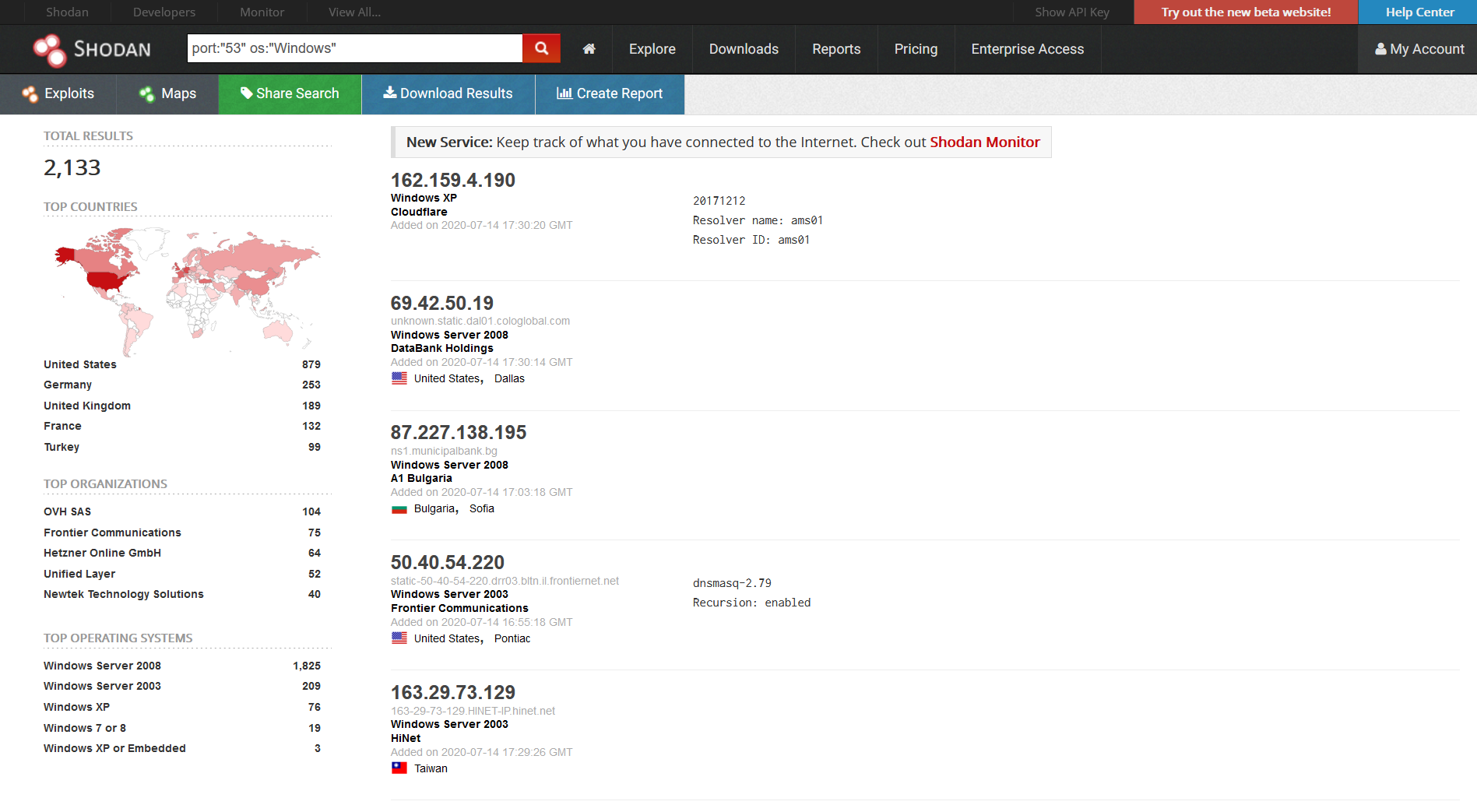
Imagine being able to read emails from any mailbox from a corporation! But everyone uses office 365… don’t they? Well ok even if that was the case (It’s not) then the RCE would come into play. An RCE into system level access to Exchange which is so heavily tied to active directory they are almost joined at the hip) is a killer foothold. However, you pain the scenarios they aren’t good!
All knowing and all powerful
Imagine if you could read everyone’s email! What could you do with this?
- Steal IP
- Steal data
- Steal credentials
- Extort, blackmail and bribe
The SSRF vulnerability enabling a threat actor to gain unauthenticated read access to mailboxes would be a killer tool for both nation state spies and criminals alike. Read more “ProxyLogon – A god mode backdoor even when used with READ only”