 Defense
Defense
Securing the crown jewels
At the heart of most organisations are a Windows server active directory domain (or multiple of these), yet one of the most common findings when we review organisations security postures are there are significant weaknesses in their active directory deployments, both from an architectural, operational and security perspectives.
Active directory provides a range of functionality to organisations, from authentication, authorisation as well as supporting services such as printer and share listing, DNS, people/information lookups and integration for 3rd party services. It’s the very hub that links most modern networked systems together and now it’s expanded beyond the corporate walls into the cloud with integration into Azure Directory Services as part of Azure or Office 365.
Essentially Active Directory can be considered a castle whereby crown jewels are held! This may be in the form of credentials/identity or by nature of granting access to business systems that hold sensitive data (such as using AD integration to log into an HR or Finance system).
This security game is complex but discovery of AD issues doesn’t need to be!
Windows security is not a simple affair, someone telling you otherwise is probably trying to over egg their sales pitch! However, it doesn’t have to be rocket science either, from the Sysinternals suite, the Microsoft security baselines through to a range of third party products there’s a wealth of material out there on AD security, but when you consider there are maybe 3000+ group policy configurations possible and a whole range of forest/domain and directory configurations it’s not a 2 second job! But wait, we’ve got something special in the toolbox! PingCastle!
PingCastle is an active directory and windows auditing toolset which is available for use either through a commercial services organisation or internally (e.g. for use to audit internal systems).
It can be downloaded from https://www.pingcastle.com/
Auditing your directory services
I could draw all manner of different stages here based on Demmings PDCA or similar framework. The key point here is that we have a process to follow, for a tool is a tool and we need to be able to leverage the tool to provide business value! (easier to say than do sometimes!). PingCastle has a formal methodology which can be found here: https://pingcastle.com/methodology/
For the purposes of this article I’m going to outline how I’ve run AD audit projects in the past, so this is my take on the world (thought I believe it’s fairly similar to the formal PingCastle approach).
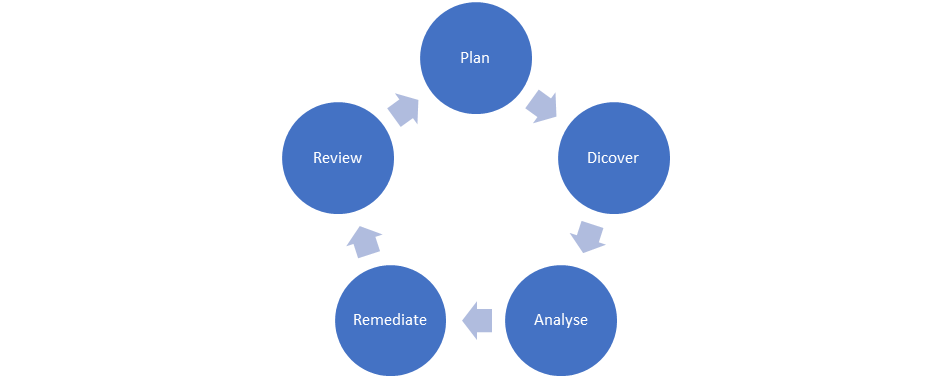
Plan
The planning phase for an Active Directory audit shouldn’t be too difficult, but it’s worth ensuring you involve the right people from your organisation and that the overall flow of the project is understood. It’s also important because the data this tool will generate, when consolidated into a report is going to be become a sensitive document, so we should ensure we have the appropriate authorisation to proceed. We also need to think about what the output will mean to us and what we are going to do with it, we may have to involve a range of stakeholders in the organisation to enable us to act upon the findings. We must remember that technology and security is just as much about people and communication as it is about 0’s and 1’s! Underestimate this at your own peril!
Key areas to consider are:
- Who are the stakeholders?
- What is the target scope?
- All domains? A single domain? A specific forest?
- Who is responsible for each domain?
- What will happen with the findings and how will remedial actions be taken (if required)?
- How often audits will be conducted?
- Who will conduct them?
- What access rights will be required?
Discover
The discovery phase with PingCastle is much simpler than with a multi-tool approach (trust me I’ve deployed many tools and had to sift through data, PingCastle removes a lot of the fiddly manual work required). Now that we’ve got the planning phase complete, we can look at running an audit. I’m going to walk through this in the lab (this is the very quick but fun part of the discovery)!
I made a video of a previus version, the process is the same so if you want to see how quick you can do this pleas check out our video here:
Firstly, we are going to download PingCastle:
https://pingcastle.com/download/
Once that’s downloaded, we are going to deploy to the target environment. We may be required to deploy multiple times depending upon the environment and network setup.
Once downloaded we extract the zip file:
Now from a domain joined machine with appropriate access (you can run this as a domain user however it’s possible custom permissions may obscure some tests) we can run the PingCastle.exe binary:
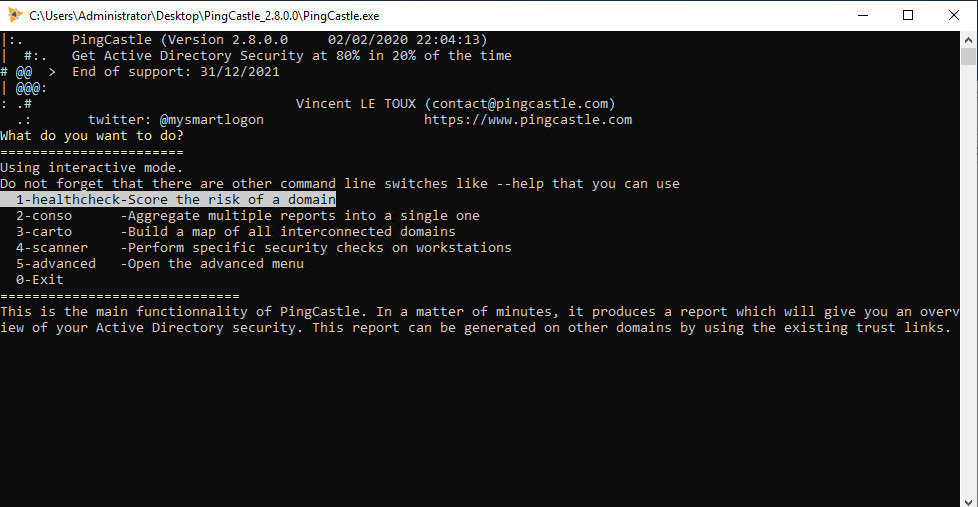
We now have a range of options:
- Healthcheck (1)
- Consolodate (2)
- Map (3)
- Workstation Scanner (4)
- Advanced (5)
- Exit (0)
In this post I’m going to focus on running a Domain Health check, so we simply can press ENTER:
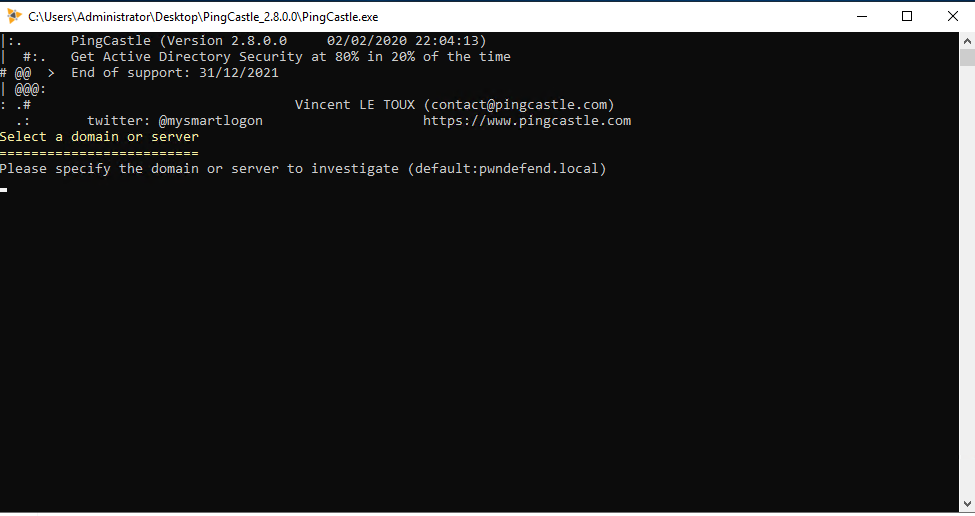
The current domain has been obtained (pwndefend.local) so we simply press ENTER
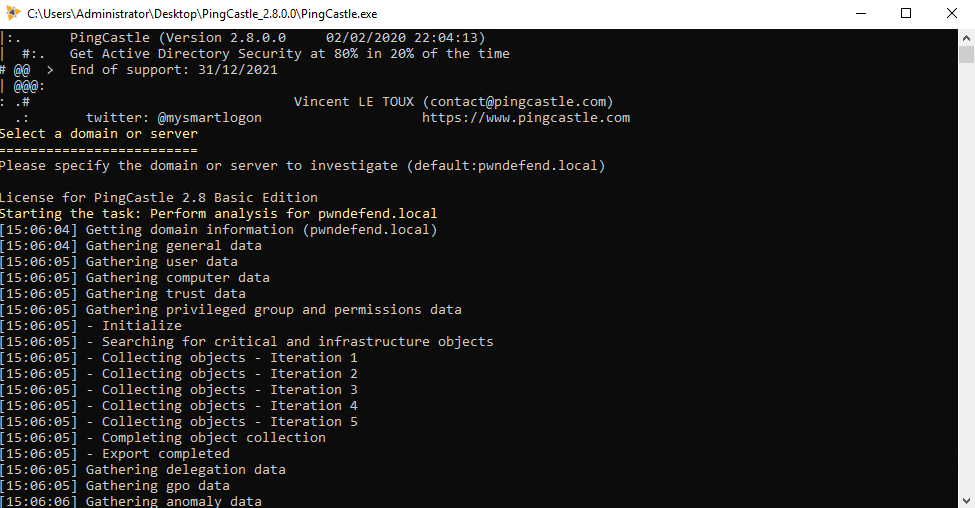
And now we have a report generated! That’s amazingly simple, that’s 4 click and 2 presses of ENTER and we have a heath report!
We can now see a report file in the directory:
This output both an HTML document and an XML file. We are going to open the HTML file:
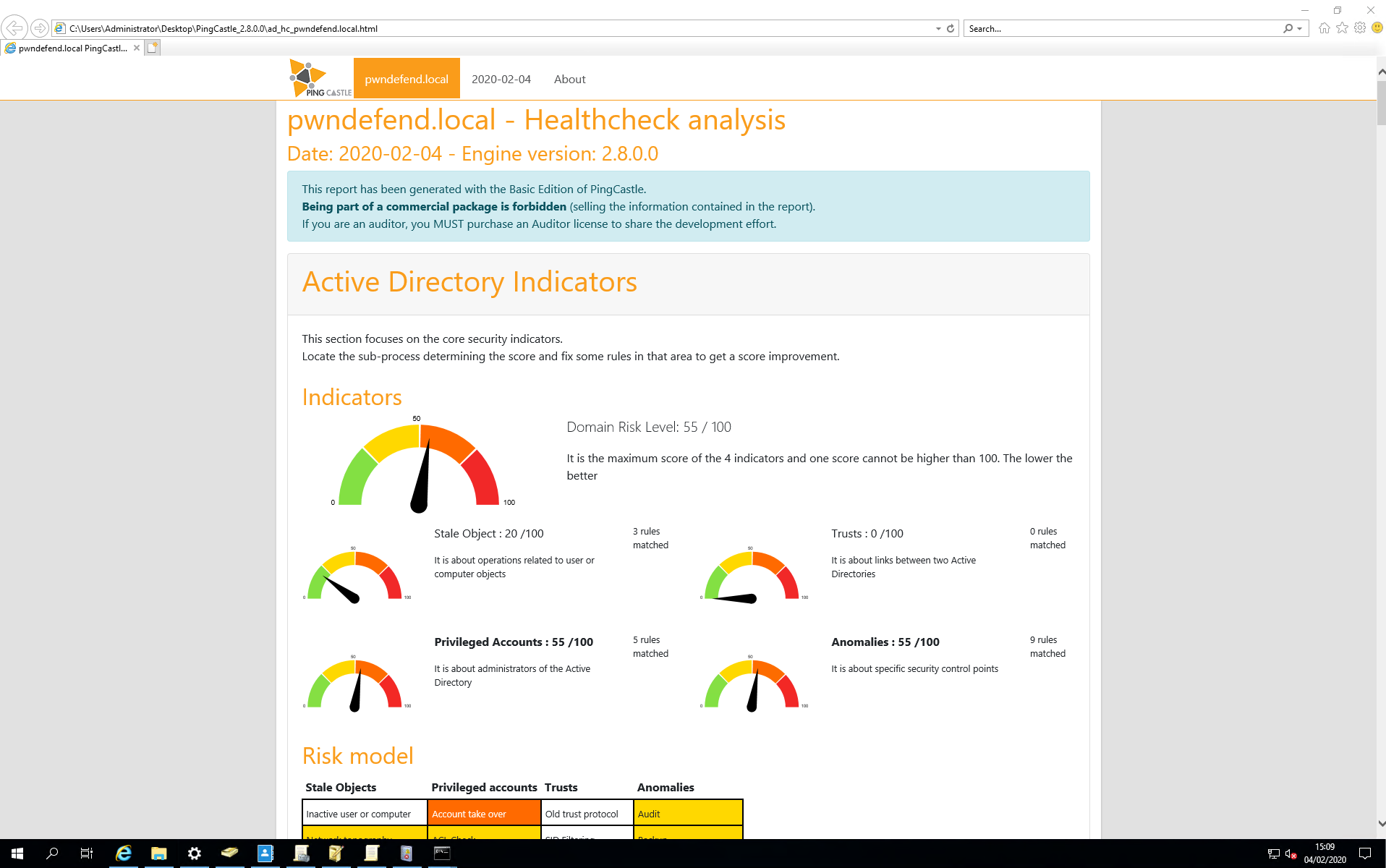
And here we have a summary report on the domain health.
Analyse
Now we have a report we need to understand what is in it! Using page down I counted 18 presses, so it’s a few pages and that’s without expanding some sections, so whilst the process has been greatly simplified, don’t mistake that for everything being simple! We need to start looking at the findings and understanding what they mean to us, what we could change and how that might impact us.
Let’s start with the summary:
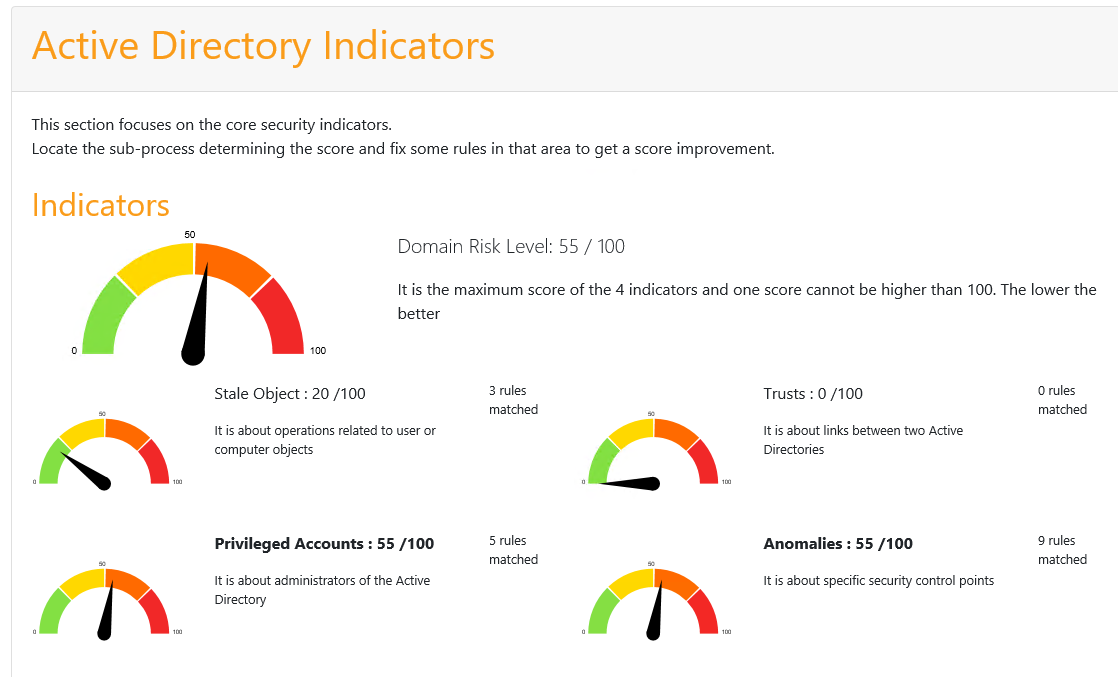
Now this lab domain hasn’t got too bad a score overall, but I built this with a range of known vulnerabilities so it’s far from perfect. I also wanted to show that as with all things in security, there is no silver bullet.
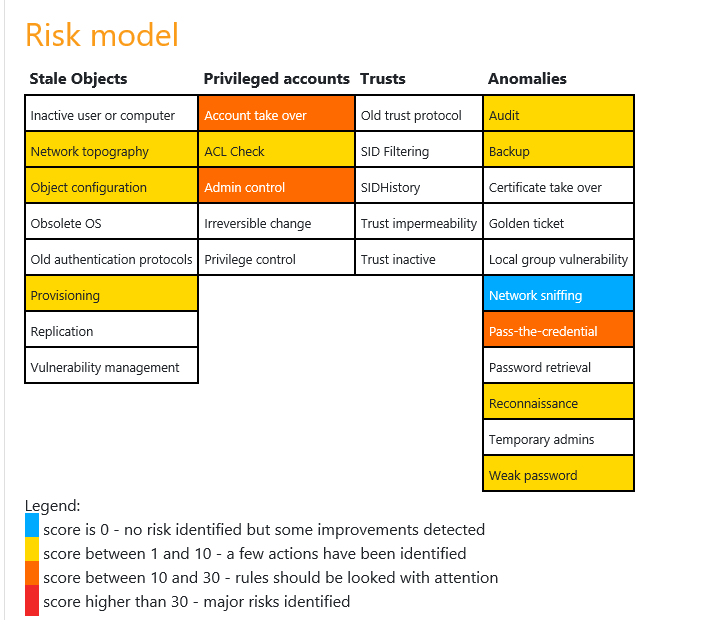
We can see a range of risks have been identified which include:
- Admin control
- Weak password
- Reconnaissance
- Account takeover
- Backup etc.
The devil is in the detail
Now each finding area is going to have specific detail in it, it’s important to focus less on overall ‘score’ than it is to ensure you understand the detail.
In this post I’m just going to highlight he is following password policy weakness:
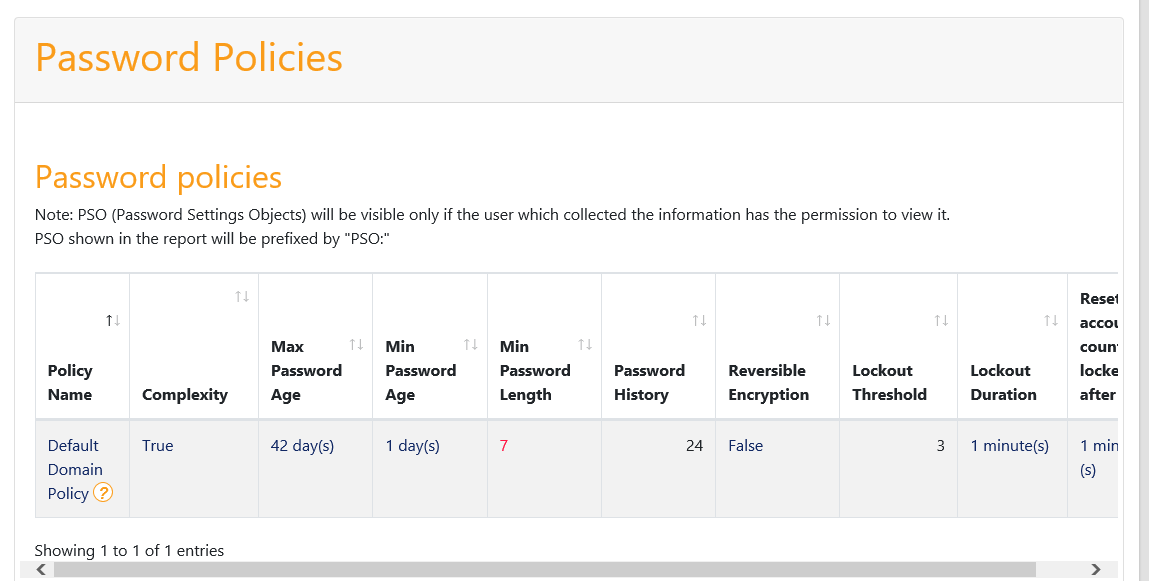
We can see here that the minimum password length is 7, so even with complexity that keepsake isn’t going to up well to a motivated attacker and this policy will likely be prone to human weaknesses. We are going to add to our remedial action list that we need to change our password policy. Now sure in AD we can change a GPO, we can implement fine grained policies and all of that can be done relatively simply, but we are likely here to have to involve a range of stakeholders, so we need to analyse the finding in relation to the current business context.
Each of the findings in the report needs to be reviewed and a task list created. This is going to feed into our remedial action plan. It’s important that each finding is contextualised not only from a business perspective but also the risk, threat and vulnerability should be fully understood. Knowing how a threat can abuse configurations is important to understand both the current state and future state configurations.
Remediate
One we have analysed the findings and contextualised to our situation we now have a list of remedial actions. We will now have to work out a remedial implementation plan. This may require integration with other parts of the organisation, it may require deployment to a test environment, creation of a change and release plan and gaining authorisations to deploy. We also must consider the likely impact and have a rollback or backup plan in case things don’t go as planned (we may change a configuration which affects a critical business system etc.)
This needs to be conducted in line with organisation policies and practises. That will vary from organisation to organisation, like I said, it’s important to communicate and have a backup plan!
Review
Following our planning, discovery, analysis and remediation we re going to want to run another discovery and analysis pass to ensure our changes are effective and to update our current state baseline. The number of iterations will vary for each organisation and their appetite for release iterations etc. It’s important however to continually report and communicate back to the stakeholders on the progress and the successes and failures. By doing so you will enable security posture improvement whilst ensuring people are fully appraised of the changes occurring.
Summary
Well that’s a very fast look at Active Directory auditing using PingCastle and a project/operational lifecycle of how to not only understand the current state but also enable and conduct remedial activity in a planned and controlled manner.
I can’t state how impressed I am with the PingCastle tool, it enables incredibly fast discovery, reporting and visualisation of directory and endpoint security, it takes lots of custom scripts and manual effort and really delivers value within seconds, not months! There’s lots of functionality in here so it’s important to understand, even though the tool is fast, your journey to having a more robust and secure directory service may take a little more elbow grease, but this tool is definitely one for the toolbox! It’s great at a technical level as well as enabling rapid business decision making so from me that’s a big thumbs up!
I must stress however that you need to look at your directory from multiple perspectives. The lab report score isn’t too bad however the domain is vulnerable to at least 6 routes to total compromise, so whilst there isn’t anthing majorly red in the report, this domain is far from secure!
I hope this post is helpful to you and that you can leverage this information to start ensuring your crown jewels are adequately protected from criminals and other threats! Stay safe and check back for more PwnDefend tips, tricks, reviews and intel!








