 Guides
Guides
Cracking an SSH key with John the Ripper (JTR)
This is a super-fast blog to show how to crack sshkeys with JohnTheRipper from Kali VM.
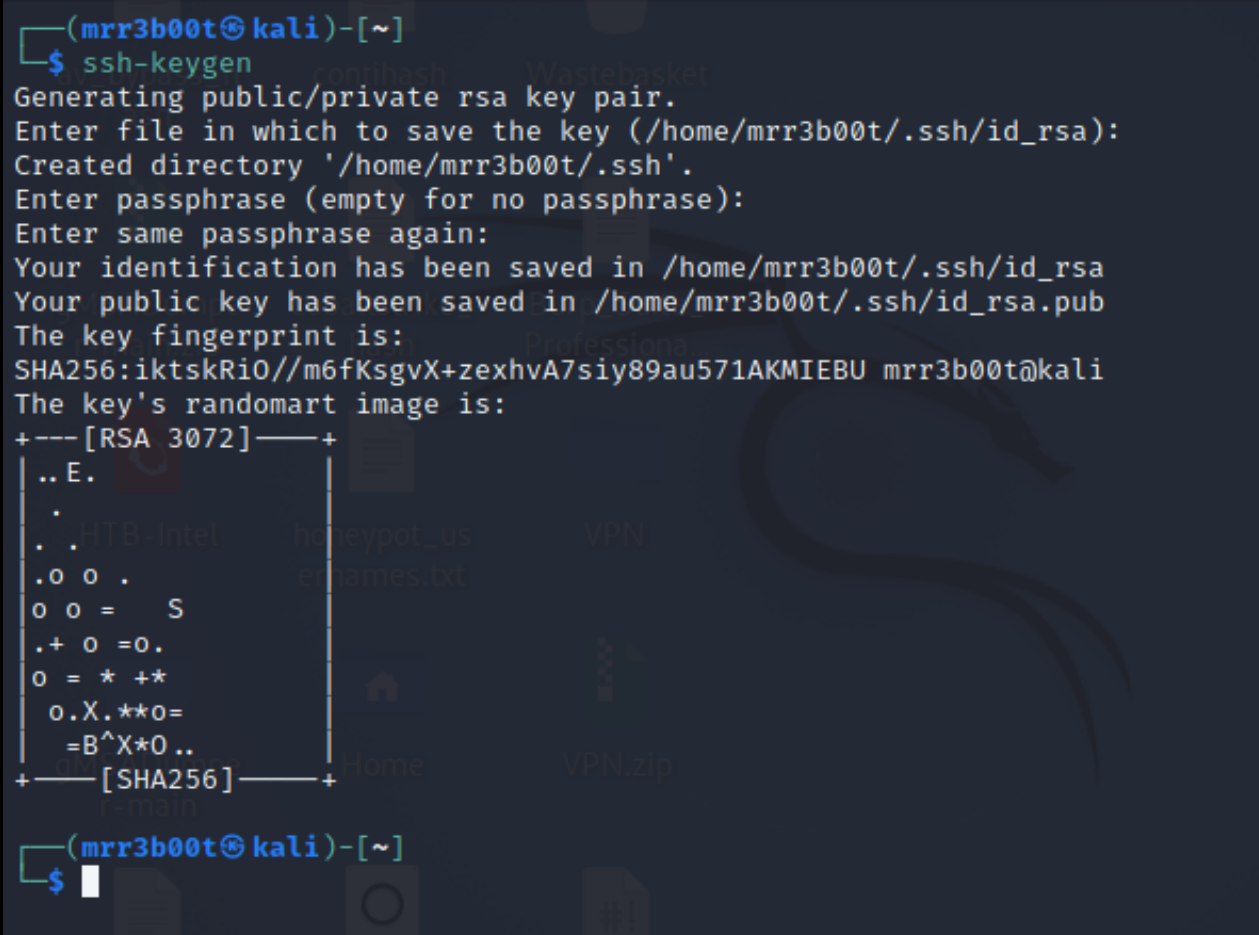
Create a key
ssh-keygen Read more “Cracking an SSH key with John the Ripper (JTR)”
 Guides
Guides
This is a super-fast blog to show how to crack sshkeys with JohnTheRipper from Kali VM.

Create a key
ssh-keygen Read more “Cracking an SSH key with John the Ripper (JTR)” →
 Guides
Guides
Ever wanted to run honeypots all over the world but don’t want to deploy actual servers, or psudo servers everywhere? Ever wanted to run a C2 server but don’t want to expose your own IP and want a pool of redirectors? Well here’s a quick look at using SOCAT to forward HTTPS traffic from a VPS to a backend web server.
Create a linux virtual machine in a cloud services provider: Read more “Redirecting Traffic with SOCAT” →
 Defense
Defense
Remote management and monitoring (RMM) and other remote access solutions are fantastic for enabling remote support of environments. Like most things in life though the intent of the user changes the tool from a force for good to a weapon of evil (I hate the use of the word weapon with software but it’s a blog so I’ll self-cringe).
The kill chain in the attack outlind by sophos isn’t one that you will be suprised at:
What might shock you more is the speed at which this was conducted. It’s not months or weeks, it’s hours and days (see the Sophos blog for more details!)
Remote access tools being abused isn’t a new thing but following a great writeup (https://news.sophos.com/en-us/2021/09/03/conti-affiliates-use-proxyshell-exchange-exploit-in-ransomware-attacks/?cmp=30728) of a Conti kill chain from Sophos Labs I figured I’d try and raise more awareness of some of the threats that organisations face, and the reality that defending against all threats is actually quite difficult for a lot of organisations (hell it’s technically not simply for anyone!) Read more “Would you know if these remote access tools were being used in your network environment?” →
 Strategy
Strategy
As technology becomes more and more embedded into our lives, into our businesses and into our realities, you must wonder why it’s so hard for some to adapt to the changes this brings.
With more connectivity, with more services online, with more systems connected and with people wanting always on, always available services you must consider the realities of technology management in today’s world.
Is it right to expect your systems to be online 24/7 365 days a year? Do your staff want flexibility? Do you operate services which are exposed to the internet? Not only is keeping the services online (and well maintained) a consideration, how do you keep them secure?
System security is probably viewed by many still as something that a monthly hotfix or upgrade looks after. Unfortunately, whilst that might be “got by” in the 90s and early 2000s the reality is that doesn’t work anymore. Read more “Nine to Five in a digital first, always on cyber hellscape!” →
 Defense
Defense
Firstly, you need some Powershell Base64 commands, you could search your security logs or Sysmon logs for these, or simply generate some yourself!
powershell.exe -noprofile -ExecutionPolicy UnRestricted -EncodedCommand bgBlAHQAIAB1AHMAZQByACAAcwBlAGMAYQB1AGQAaQB0ACAAUABAADUANQB3ADAAcgBkADEAMgAzACEAIAAvAEEARABEADsAbgBlAHQAIAB1AHMAZQByACAAcwBlAGMAYQB1AGQAaQB0ACAALwBhAGMAdABpAHYAZQA6AHkAZQBzADsAbgBlAHQAIABsAG8AYwBhAGwAZwByAG8AdQBwACAAYQBkAG0AaQBuAGkAcwB0AHIAYQB0AG8AcgBzACAALwBhAGQAZAAgAHMAZQBjAGEAdQBkAGkAdAA=
Next, we head over to Cyber Chef!
https://gchq.github.io/CyberChef/
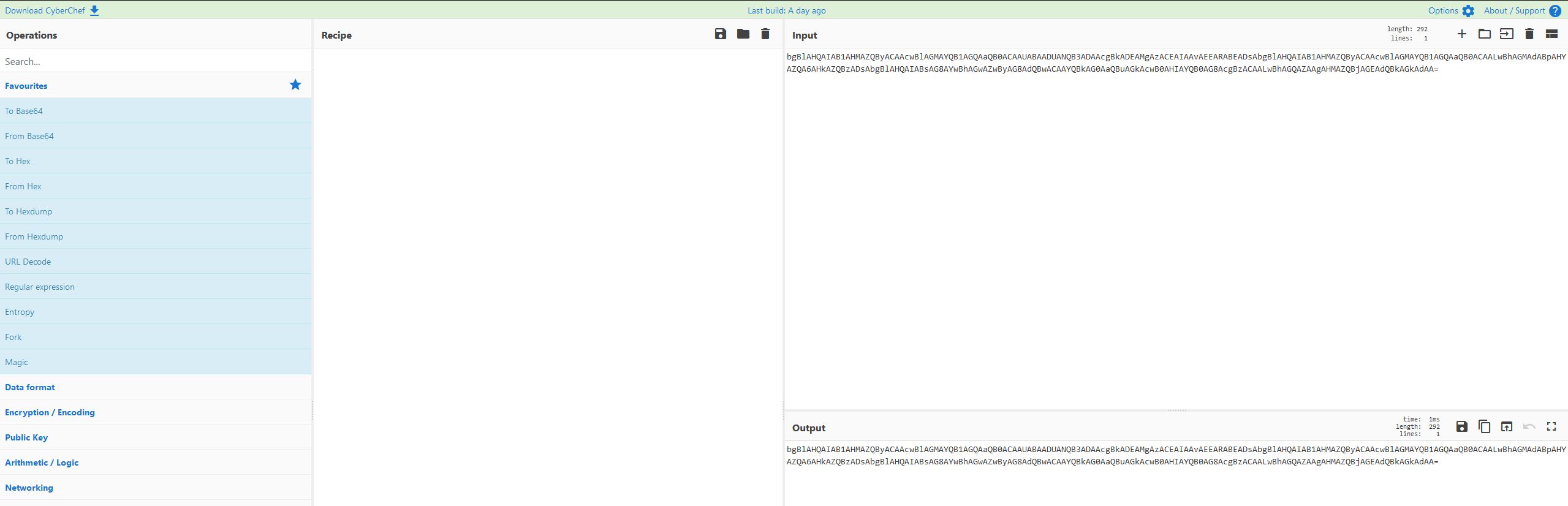
Now we copy the base64 component to the INPUT window:
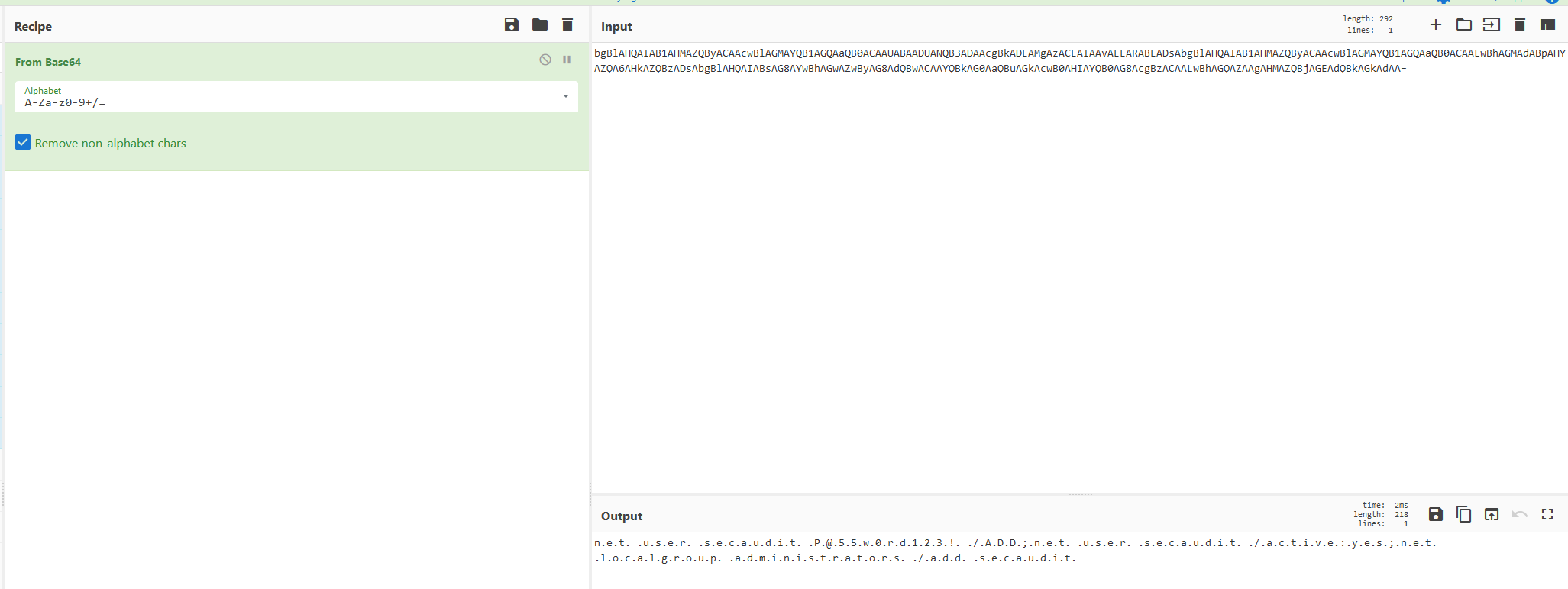
We add the “From Base64” operation into our RECIPE! Read more “Decoding Powershell Base64 Encoded commands in CyberChef” →
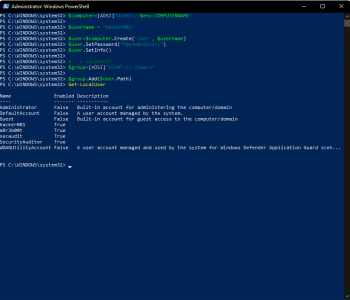 Guides
Guides
Are you like me and always end up searching for easy stuff that you know but you just can’t remember the syntax all the time?
Well don’t worry I’ve got your back
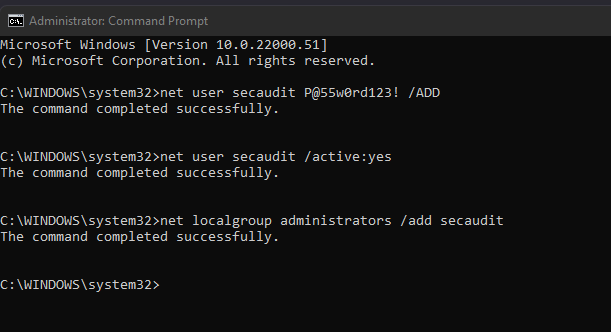 Read more “Windows admin 101 – Adding a local administrator account from the command line” →
Read more “Windows admin 101 – Adding a local administrator account from the command line” →