 Threat Intel
Threat Intel
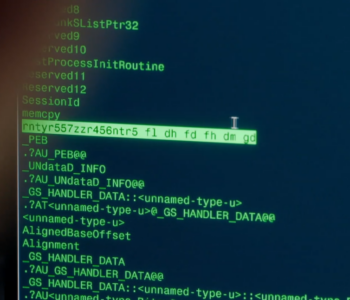
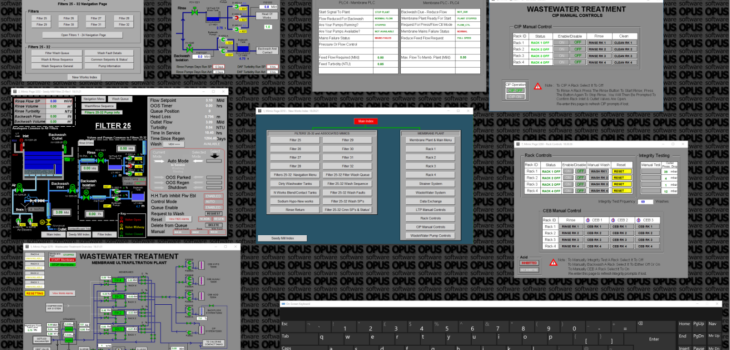
CLOP Ransomware Group Breaches Water Company and then misattributes…
We’ve all been there haven’t we! We’ve pwn3d a network, pivoted and moved around for months and then accidentally got the wrong company name… oh wait.
Well, this story isn’t fiction, CLOP ransomware group have breached a water company and then written it up as the wrong organisation. Read more “CLOP Ransomware Group Breaches Water Company and then misattributes to THAMES WATER”