 Threat Intel
Threat Intel
We’ve all been there haven’t we! We’ve pwn3d a network, pivoted and moved around for months and then accidentally got the wrong company name… oh wait.
Well, this story isn’t fiction, CLOP ransomware group have breached a water company and then written it up as the wrong organisation.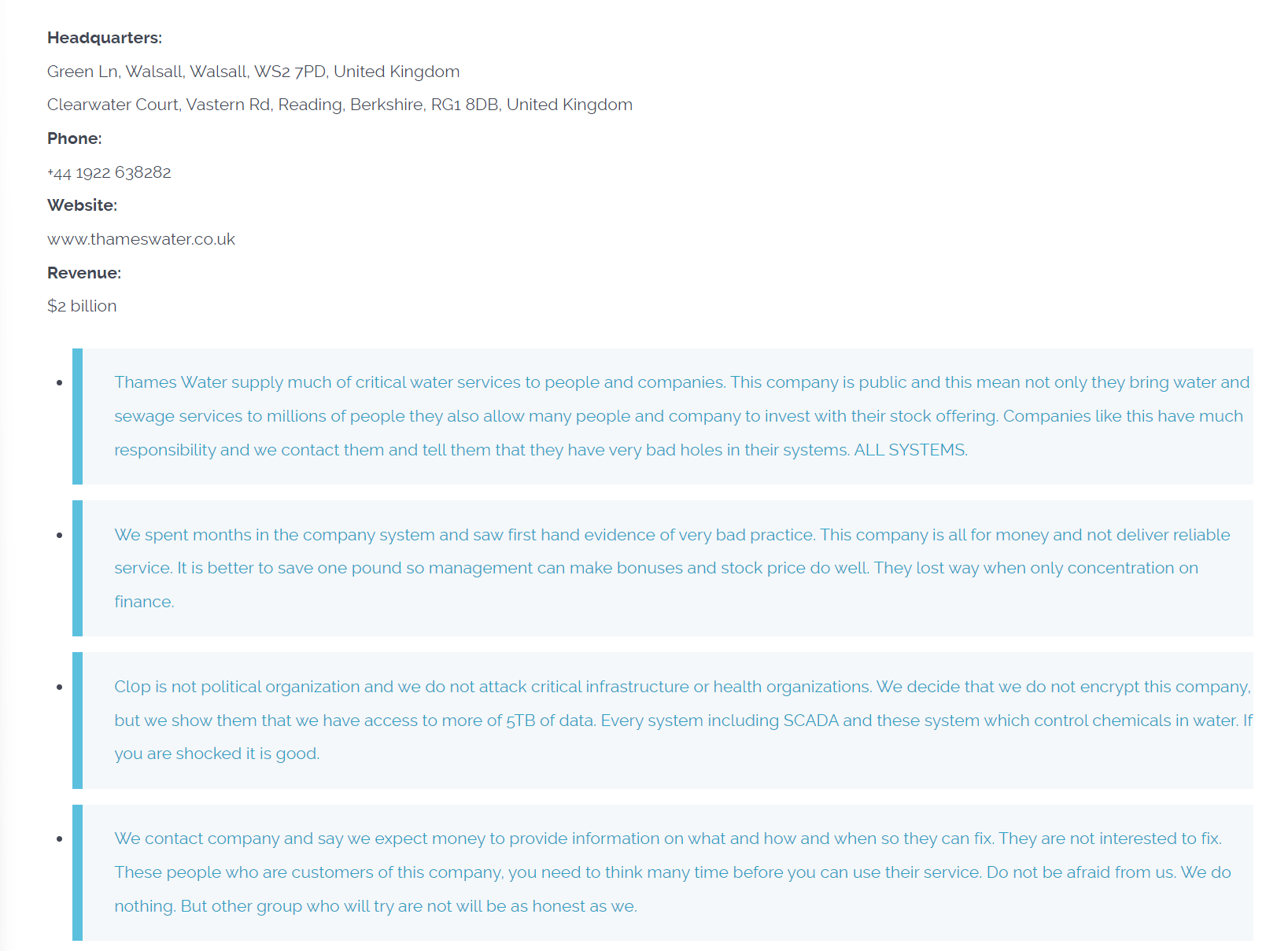
This must have come to quite a shock to THAMES WATER when the Express published this headline:
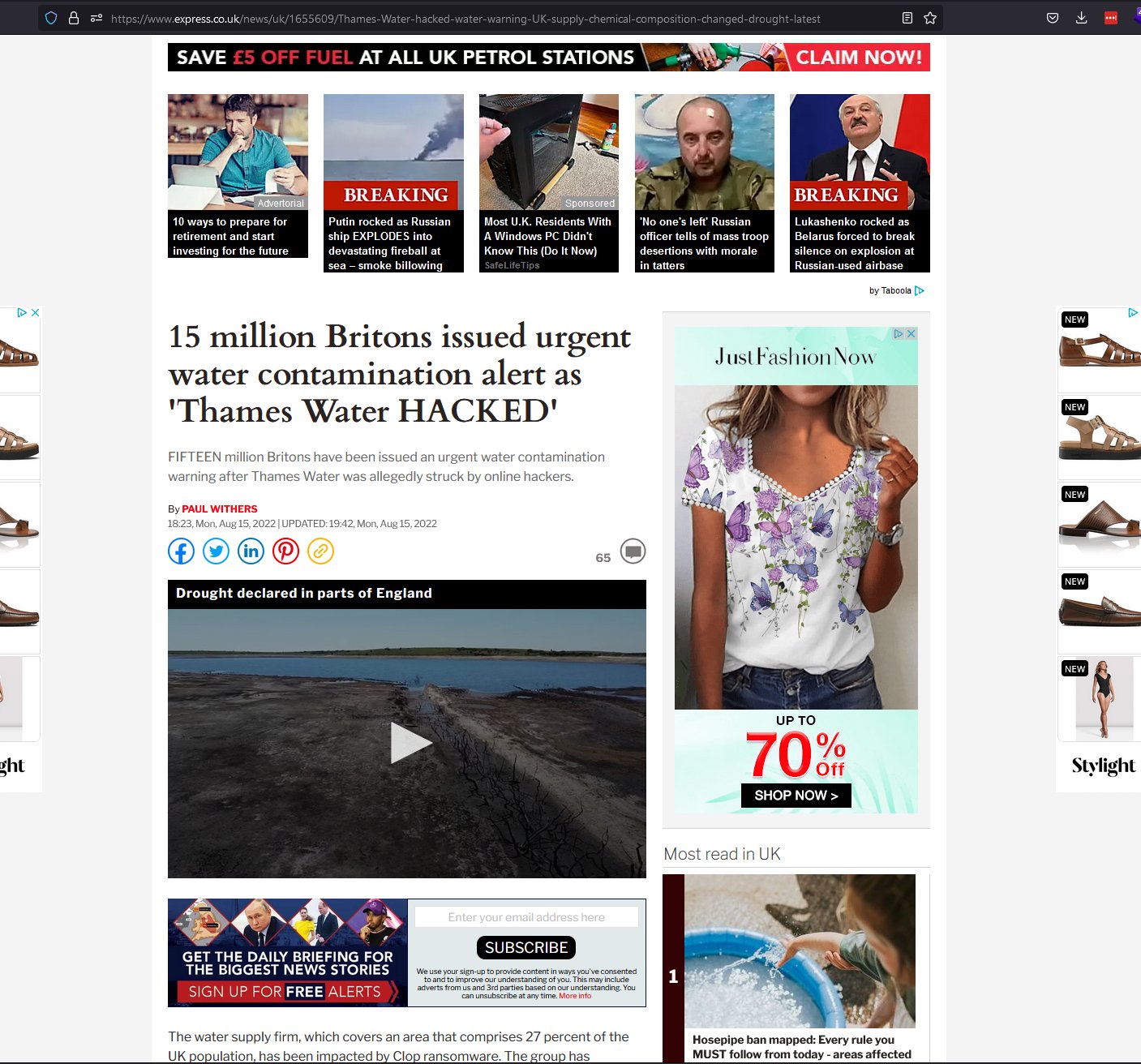
The Breach
According to data from the CLOP breach notification site (hosted on a TOR hidden service) CLOP have been inside the network for a significant period, have gained access to sensitive data including:
- PII
- Passports
- Driving Licenses
- Credentials
- Confidential Information
- Sensitive Information
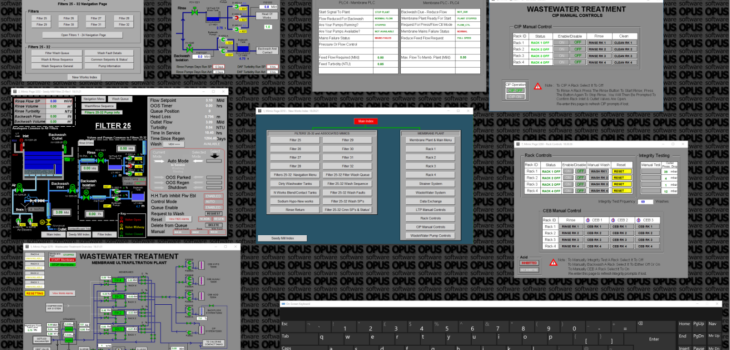
They also appear to have gained access to the SCADA systems which control supply and waste systems:
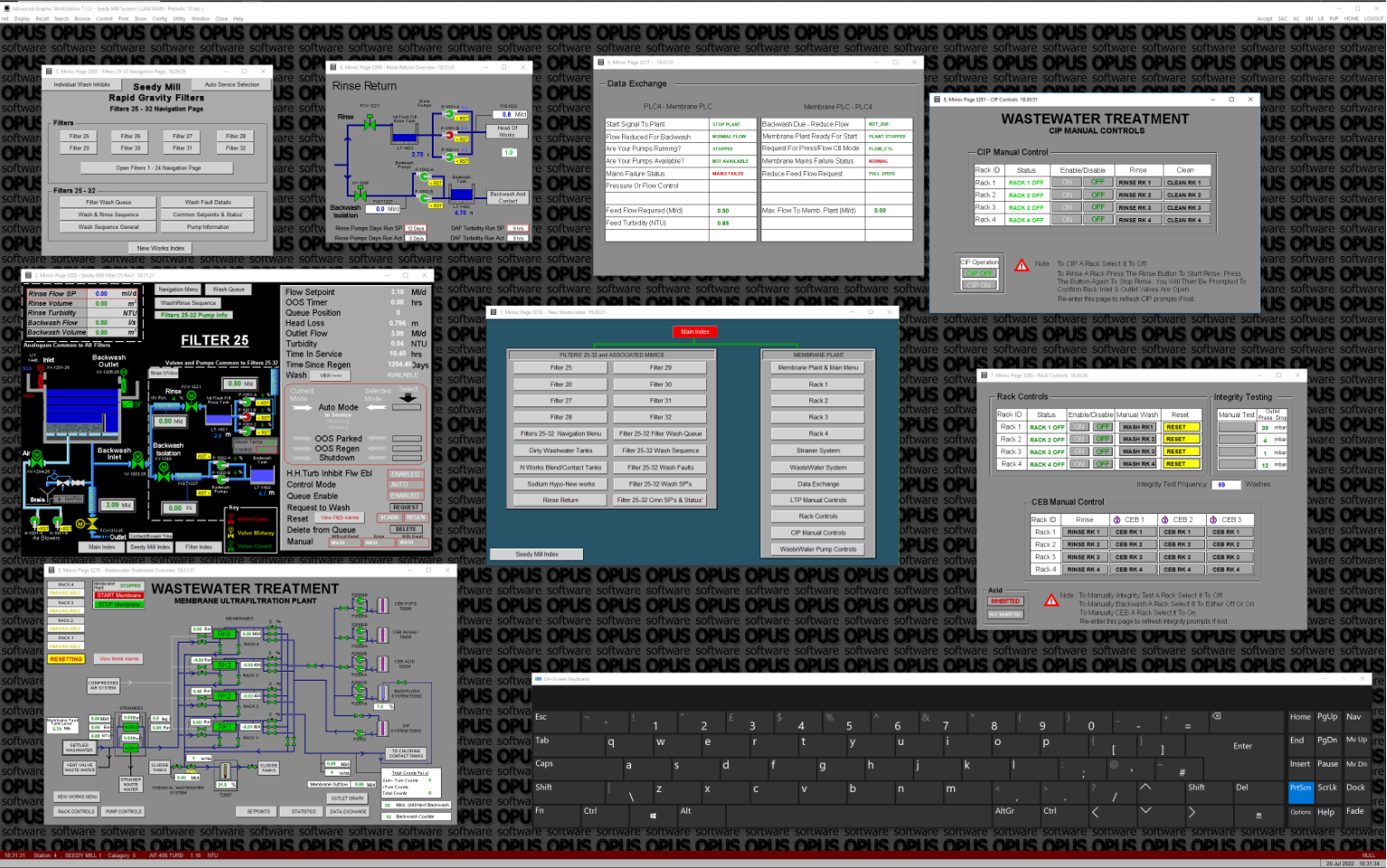
Open-Source Intelligence Gathering
When we look at the breach notice its quite apparent that this is NOT THAMES WATER and that it’s another organisation (South Staffs Water) there’s links to South Staffs all over the data, so it’s quite strange to see how wrong the group and the express could get the attribution. It took a few minutes of checking.
I did a thread on twitter going through showing how analysis of the data in the sample leaks revealed it was not Thames Water and was instead South Staffs Water:
https://twitter.com/UK_Daniel_Card/status/1559252446320500741?s=20&t=PCBQbSSWzODeO-ET61Kmbg
Breach Site Notice
I’ve copied the exact text from the breach site, I thought it useful for people to see the language used, it’s fairly obvious the author/s of this are not native English speaking.
| Thames Water supply much of critical water services to people and companies. This company is public and this mean not only they bring water and sewage services to millions of people they also allow many people and company to invest with their stock offering. Companies like this have much responsibility and we contact them and tell them that they have very bad holes in their systems. ALL SYSTEMS.
We spent months in the company system and saw first hand evidence of very bad practice. This company is all for money and not deliver reliable service. It is better to save one pound so management can make bonuses and stock price do well. They lost way when only concentration on finance. Cl0p is not political organization and we do not attack critical infrastructure or health organizations. We decide that we do not encrypt this company, but we show them that we have access to more of 5TB of data. Every system including SCADA and these system which control chemicals in water. If you are shocked it is good. We contact company and say we expect money to provide information on what and how and when so they can fix. They are not interested to fix. These people who are customers of this company, you need to think many time before you can use their service. Do not be afraid from us. We do nothing. But other group who will try are not will be as honest as we. When negotiator for company come online we saw they only interest in buying time. They also start offering very low amount what show very simple that they are not putting right value on quality of service they provide. It would be easy to change chemical composition for their water but it is important to note we are not interested in causing harm to people. But if company choose not to pay they will just play game of media and publicity and we all know their word has no truth. Anything they do to save face but after behind close door nothing change. So take this joke of price you offer and keep it for you bonuses. Client of this company change where you get you water, if we can break in so can other group and they will cause damage because are only honest true to word group in this business. We invite media to contact us and we provide scoop to you about this company and some interesting facts about dishonest behaviour. Government contract who should not be and bad process to make water safe for drink. People unite and sue this company. If you are sick in past, and you a client, may be that company did this. Soon all information will all be publish to show this malpractice. Sell all stock before collapse. Hold your institution liable. Hold your people to higher standard. We are Cl0p. If you do wrong we find you and help you fix or make you fix. Decision is your. |
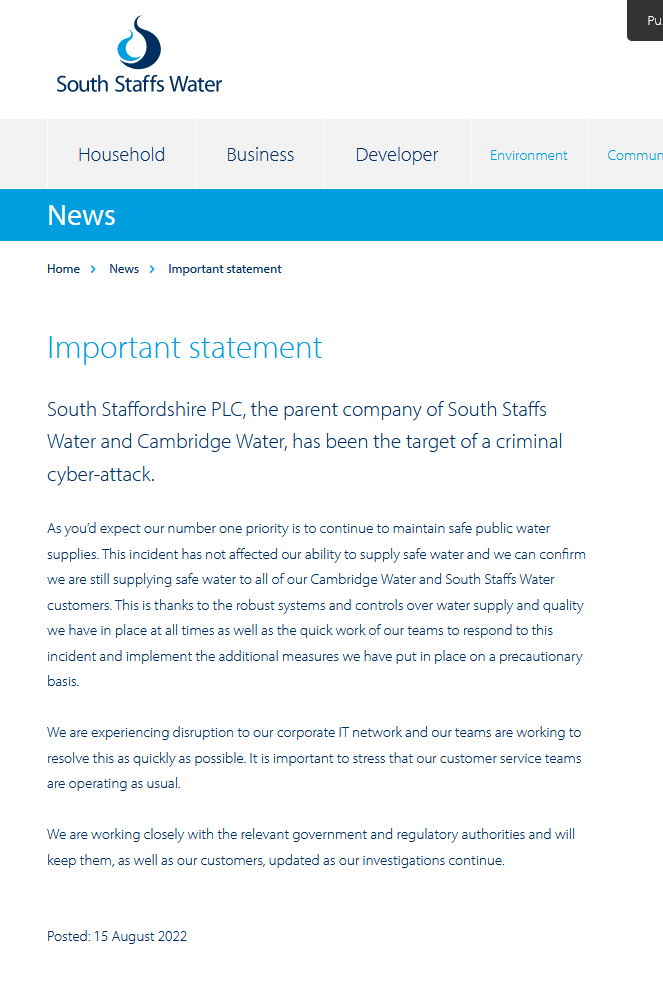
Notice from South Staffs Water
This appeared on the site I believe on the 15/08/2022 in the evening in response to news and social media chatter about the Thames Water attribution/mis attribution:
https://www.south-staffs-water.co.uk/news/important-statement
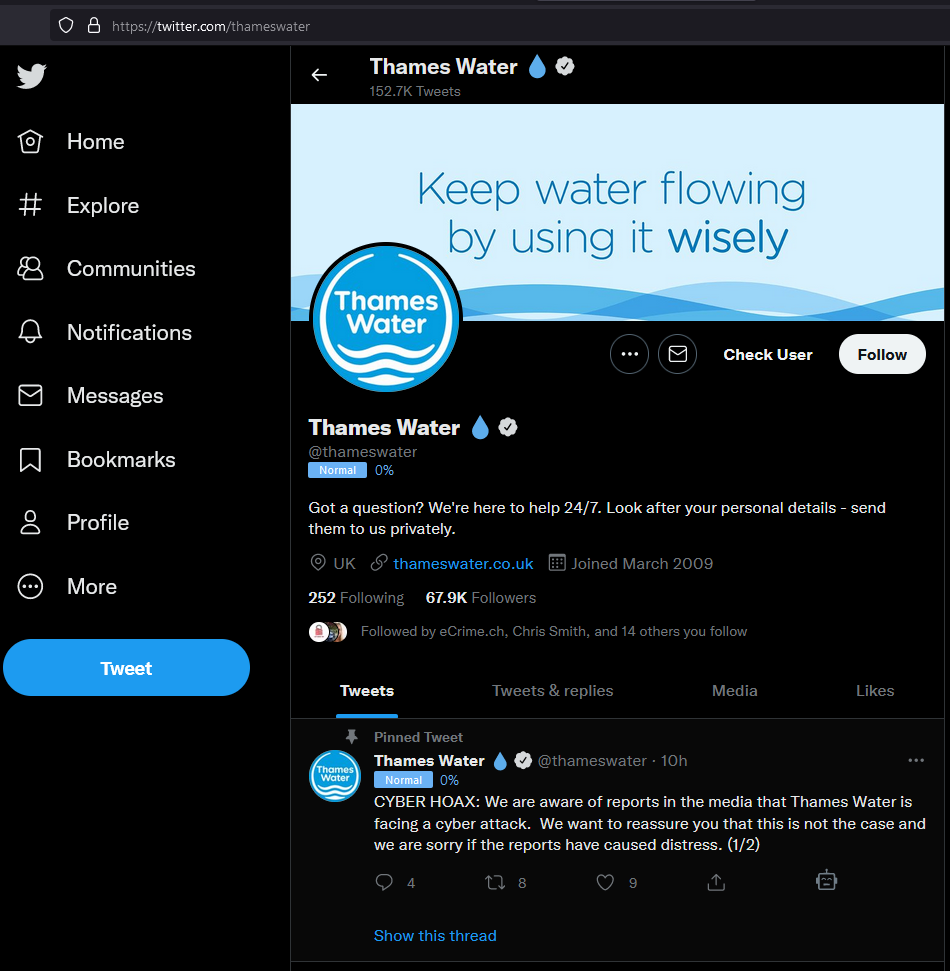
We also saw a tweet in the evening from Thames Water:
As we can see shortly after news started spreading across the internet a breach notification was posted on the South Staffs Site. Interestingly, this does raise the question about the ICO 72 hours breach reporting requirement and contacting affected data subjects, however, let’s be realistic… the reporting requirements and expectations someone will know who is affected in 72 hours is a bit of a moon-shot. If you have ever dealt with a breach such as business email compromise you will know how hard it is to work out what was accessed and who was affected from a single mailbox, let alone apparent wide network access for a prolonged period.
Summary
This is still a dynamic and evolving scenario, CLOP claim to have 5TB of data from SOUTH STAFFS, they didn’t deploy ransomware (according to them) but they have a trove of data they could mine or simply publish, the incident is far from over.
We can see in a world obsessed with time to market, with news outlets that seems to do little fact checking and where systems are vulnerable to attack from the internet, we have a long way to go with cyber security as a human race. Remember if you are failing to plan you are planning to fail!
There’s clearly lots of lessons in the last few weeks about network segmentation that organisations need to learn.








