 Defense
Defense
Create PowerShell Session is failed using OAuth
When connecting to Exchange online (there was a reason I needed to do this) I had the following error:
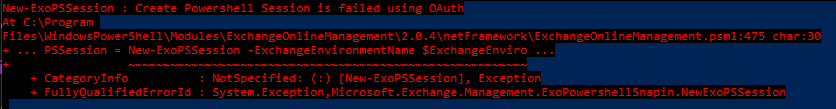
I did some googling that luckily someone has already posted how to fix this:
It turns out WINRM’s ability to use BASIC client authentication is disabled as part of the standard Windows 10 hardening baseline deployed via Intune.
To fix these we need to re-enable BASIC client side WINRM authentication.
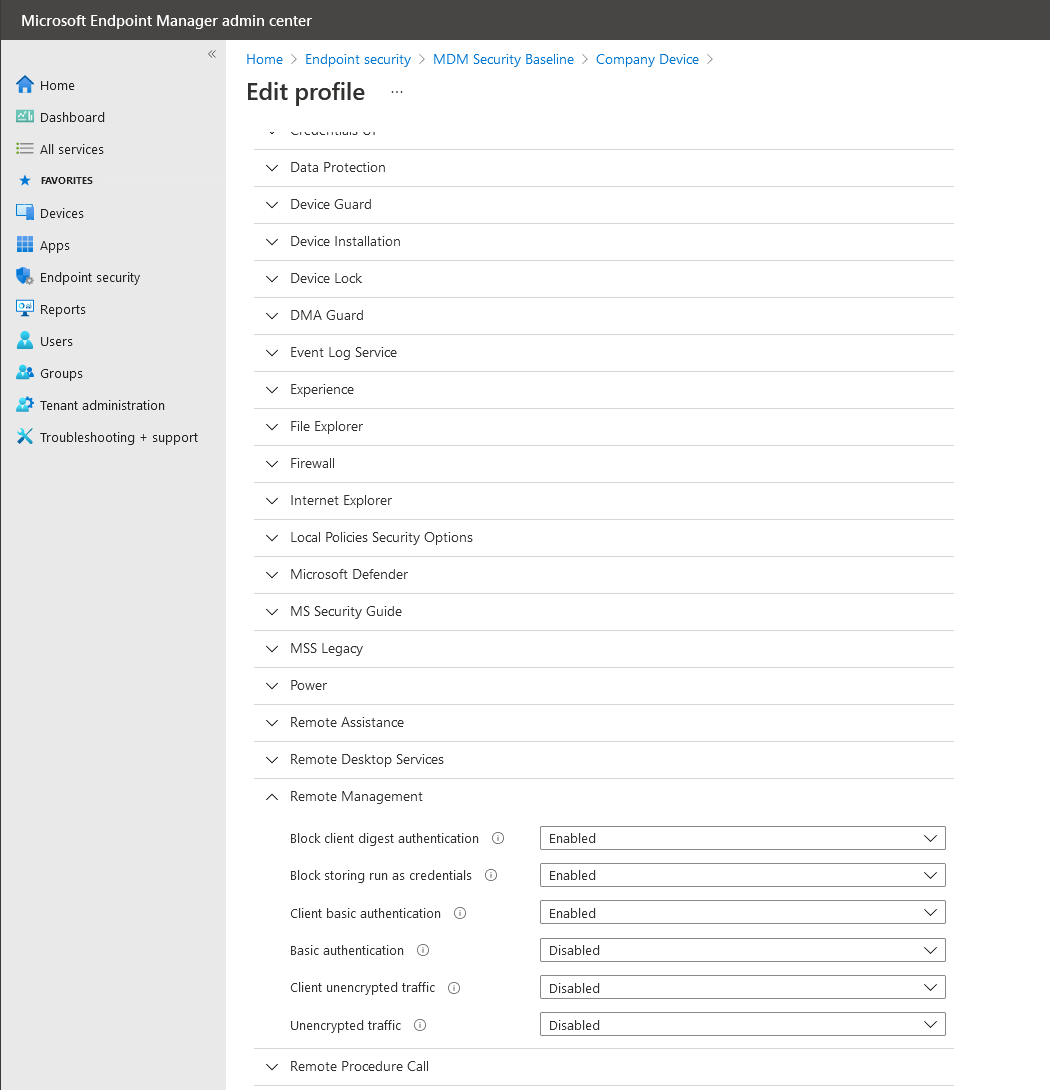
Configuring this policy and refreshing the client config enabled Exchange Online authentication work.
Summary
When hardening environments, it is often the case that something will ‘break’. The hardening process for systems is rarely (or ever!) a one attempt deployment, an iterative process should be planned for.
Out of the box there are a range of considerations to be made to MDM/Windows Client policies such as Bitlocker to go configuraiton, SMB hardening and loads more configurations that you need to considr and test for in your environment.
Overcoming this connection error was the first step in enabling a cool feature in Exchange Online – the use of plus sign aliases (+).
Here is what i wanted to run!
https://docs.microsoft.com/en-us/exchange/recipients-in-exchange-online/plus-addressing-in-exchange-online
winrm quickconfig
Install-module -name ExchangeOnlineManagement
Import-Module ExchangeOnlineManagement
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
Connect-ExchangeOnline -UserPrincipalName emailaddress[.]com
Get-OrganizationConfig | Select -Property AllowPlusAddressInRecipients
Set-OrganizationConfig -AllowPlusAddressInRecipients $true
Get-OrganizationConfig | Select -Property AllowPlusAddressInRecipients
Disconnect-ExchangeOnlineWith the MDM policy configured, and using an account with global administrator rights I was able to configre the use of plus signs.









