 Defense
Defense
Only admins can use PowerShell, right? Wrong! In Office 365 and Azure AD standard users can connect using PowerShell.
In this quick post we are going to look at how to disable users from being able to read other users data using the MSOL cmdlets. (this also appears to limit AzureAD cmdlets access as well)
Disable MSOL Read Access
Run the following command as a global admin:
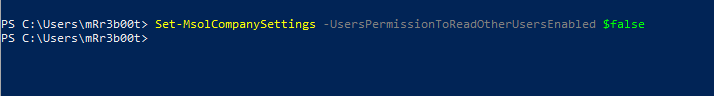
Following this a standard user cannot read other users data using PowerShell MSOL modules
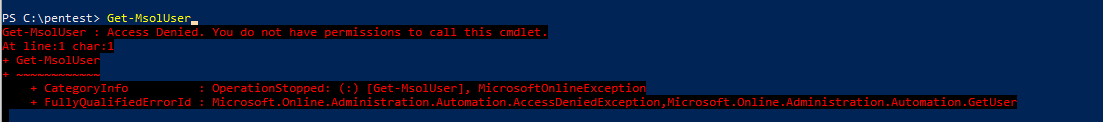
Code
| # Harden Azure AD against powershell usage for information gathering# this does not block graph access
Install-Module MSOnline Connect-MsolService #Read Current Config Get-MsolCompanyInformation #Hard Config against user recon Set-MsolCompanySettings -UsersPermissionToReadOtherUsersEnabled $false |
There are other areas that can be hardened as well:
| # Harden Azure AD against powershell usage for information gathering# harden against other user enabled facilities e.g. group additions, creating LOB apps etc.
# this does not block graph access Install-Module MSOnline Connect-MsolService #Read Current Config Get-MsolCompanyInformation #Hard Config against user recon Set-MsolCompanySettings -UsersPermissionToReadOtherUsersEnabled $false Set-MsolCompanySettings -AllowAdHocSubscriptions $false Set-MsolCompanySettings -UsersPermissionToCreateGroupsEnabled $false Set-MsolCompanySettings -UsersPermissionToUserConsentToAppEnabled $false Set-MsolCompanySettings -UsersPermissionToCreateLOBAppsEnabled $false |
Considerations
Obviously test this before simply deploying it to your environment. There may be legitimate use cases for the feature as well as this may impact other functional areas.






