 Guides
Guides
This is an experiment to combine a near real time thread on twitter and a blog… I have no idea if this will work. The premise is, we are conducting a adversary simulation against a target and want to see how this translates into a ‘plain language’ blog/story about how these things work. (I’ve also not included sales/scoping/documentaiton and clearly not all of this is in real time) but it is real!
The Fundamental Steps
Ok so first thing is first – the criminal part is a joke! We are here to help people. What we are going to do however is consider the general cyber threat landscape, look at the organisation from an ‘external threat actor’ perspective and then see what we can map out from an attack surface point of view.
RECON and ENUMERATION
- Who are the company?
- What vertical are they in?
- Do they have a lot of branding we can ‘borrow’?
- Can we understand anything about their supply chain?
- Can we discover about their technology/services/business landscape?
- Who are its employees?
- Who are the execs?
- Who are the IT staff?
- Who are developers?
- Who are the finance team etc?
- What domains do they own?
- What their phone numbers?
- How do they get IT support?
- How do they get ‘remote accesses?
- Can we get a list of phone numbers for them?
- What subdomains are there?
- Can we find email addresses?
- Can we find any breached/stolen credentials?
- Who hosts their email (mx record)?
- Do they have email security?
- What does their internet face attack surface look like?
- What lures could we use?
This isn’t exhaustive but we are starting to build a picture of the target. Let’s just take stock of what we have done so far?
Steps we have taken
- Stalked like hell over LinkedIn and other social media
- LinkedIn for ‘Pro’ Info
- Facebook and Insta for all the normies
- Googled (and other engines) till we cannot google no more on the company
- Read all the job adverts
- Find any published docs
- Create a library of brand material
- Try and find any suppliers who have logos or case studies for the target
- Enumerate all the domains
- Run subdomain enumeration
- Passive Enum
- Active Enumeration
- Run subdomain enumeration
- Conduct Light Touch Port Scans and Service Enumeration
- Started to create an ATTACK SURFACE/ATTACK TREE map
Profile the Target
- How much revenue do they turn over?
- Do they look like they have cash reserves?
- Do they look like they have cyber insurance? (if they have cyber essentials and they are small enough they almost certainly will with that)
- Do they look like they invest in security?
- Can we detect active security controls?
- Do they operate a VDP?
- Is there a .well-known/security.txt
- Do they have dedicated IT/Security Staff?
The Attack Map
Now this is a high level view of the landscape, we also want to think about the routes we could take and what obstacles etc. we might have to overcome, hopefully this does however give an indication as to the broad areas we will be looking at.
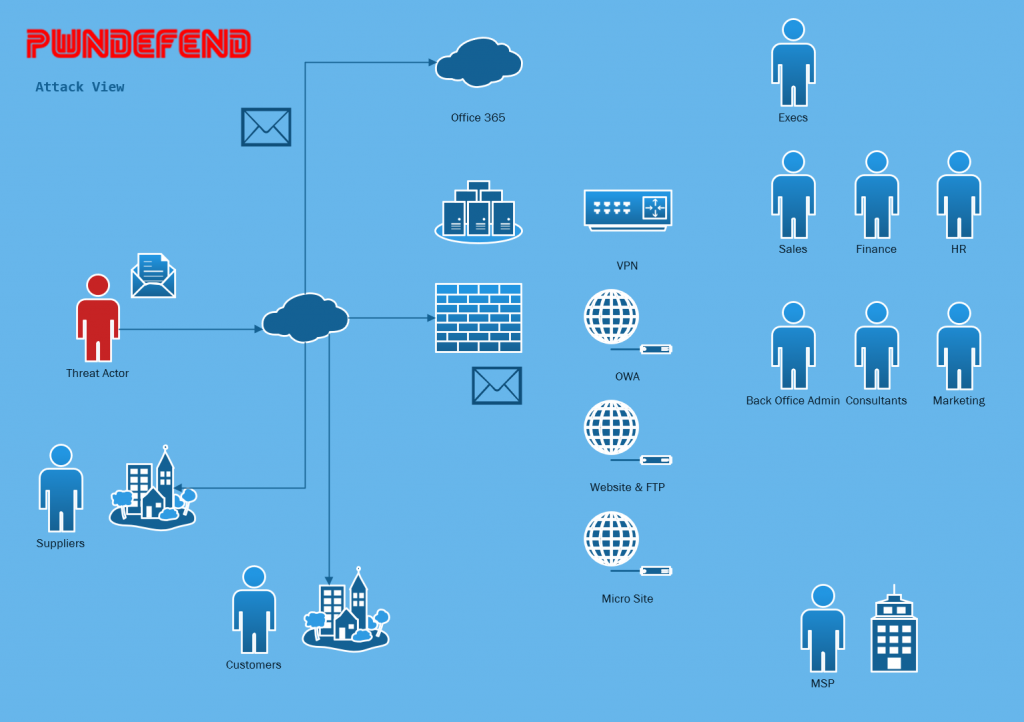
Itterative Recon and Enumeration
I think many people think that this parts are waterfall like in operation. In reality this stuff is itterative. Like making a painting, we sketch, we explore, we add more data to our “view” of the target.
Technical Indicators
Now aside from all the OSINT, people, business and general landsape view we are going to look for some technical indicators:
- MX Records
- Mail Flow path
- Mail Security Records (SPF/DMARC/DKIM)
- DNS Records
- Age
- Stale Records/Subdomain Takeovers
- DNS Provider
- History
- Origin IP Leakage
- Hosting Providers
- Web Platforms
- Web Applicaiton Quality/Age etc.
- Information Leakage
- Software Versions
- Platform Manufacturer/Versions etc.
- Identify Common Technology Groupings
- Leak Backend Data
- Can indicate a view on skills and capabilities
Going deeper
Ok so we are mapping through and enumerating, conducting OSINT and being selective with our prods of the system. We don’t need to use a battering ram when we might find an unlocked door or adjar window. Enumeration and Recon is really important and takes time. You don’t find what you don’t know fast (normally).
Updating the MAP
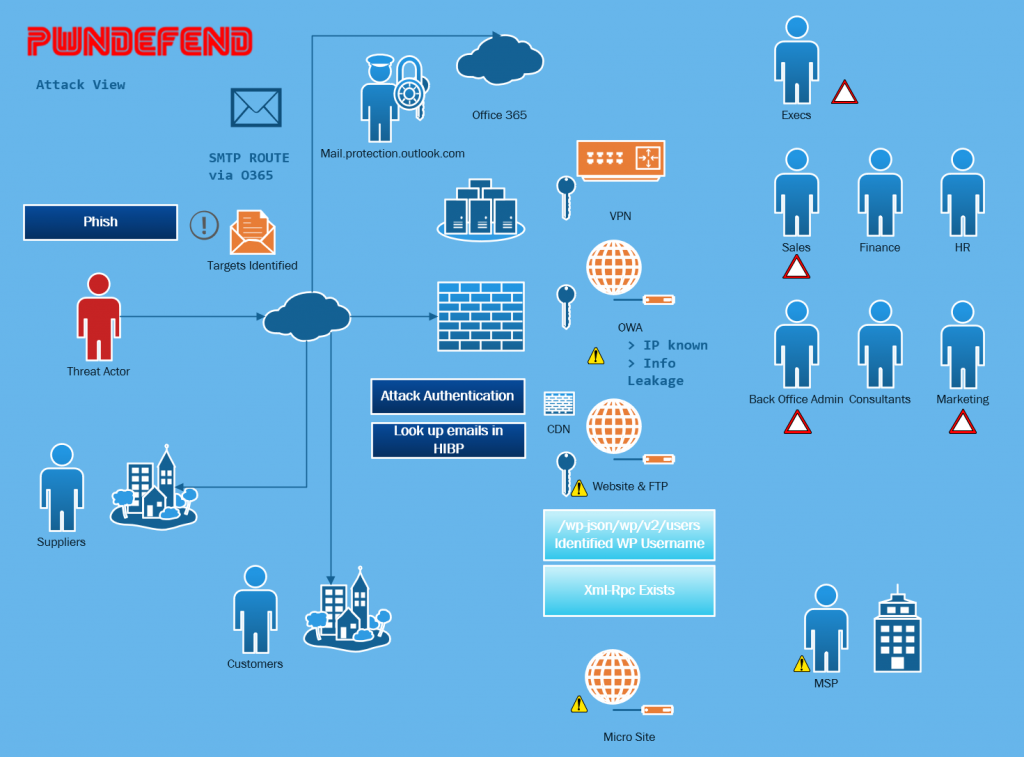
As we progress we need to keep our notes, evidence, methods and map updated. Wading through someone else’s network requires documentation to keep on track and to avoid missing things or heading too far down a rabbit hole.
List of Likely Routes of Attack
- Phishing of Staff
- Attack Corporate WordPress Site
- Attack Exposed Services Authentication
Key Target Intel
- Office.Protection.Outlook.Com/Office 365
- WordPress
- VPN Services
[TO BE CONTINUED]






