Uncategorized
Uncategorized
A common way to deploy an encryption routine used in Ransomware scenarios is to create a scheduled task to launch a cyptor exe. This is commonly deployed via a Group Policy Object (GPO).
So I wanted to look at how with Microsoft Defender for Endpoint (MDE) we could detect this both on domain controllers but also on CLIENT devices (MEMBER SERVERS/PCs)
Domain Controller File Activity
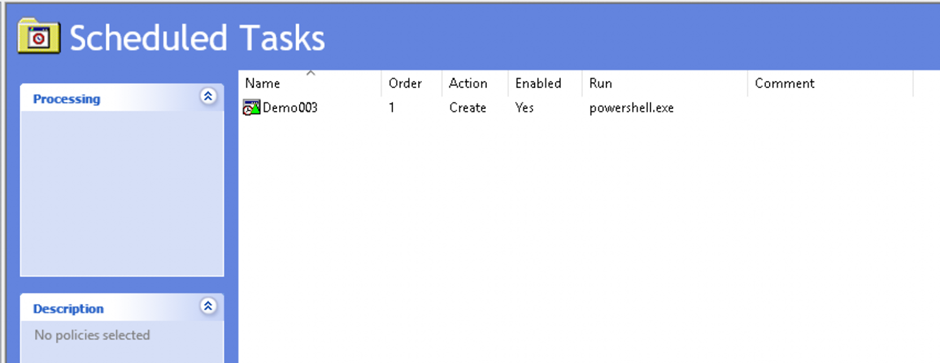
- Create a New GPO
- Create a NEW link
- Create a Scheduled Task in the GPO
How can we detect this with MDE?
| DeviceFileEvents | where FolderPath contains “Policies” | where FileName == “ScheduledTasks.xml” | sort by Timestamp |
This will catch this for create or modify (or delete)
So maybe we want to look for:
| DeviceFileEvents | where FolderPath contains “Policies” | where FileName == “ScheduledTasks.xml” | where ActionType == “FileModified” or ActionType == “FileCreated” | sort by Timestamp |
Client-Side Events
We can search for client-side events with a query like below:
| DeviceFileEvents | where FolderPath contains “Windows\\System32\\GroupPolicy\\DataStore\\” | where FileName == ” ScheduledTasks.xml” | sort by Timestamp |
Summary
As you can see this is really simply to create (it takes less than 1 minute to create a GPO with a PowerShell Scheduled task that runs as SYSTEM but also how easy this is to start detecting.
Now these are very late stage kill chain activities but they are worth detecting and alerting on, that will also possibly help against insider threat privilege abuse etc.