 News
News
Firewalls are often both a defended gate but also the front door to access corporate network. That is all lovely until it’s not! You see so many corporate network intrusion incidents occur from threat actors simply logging into the VPN (due to lack of VPN), and then we have the software vulnerabilities where they shell their way in, but did you think that another way could be from stealing all the backups from a ‘security’ provider? Well now you might! There’s been bit of an incident (one that started as it’s only 5% of customers but actually it was 100% of customers who used the backup feature! YIKES), but before that let’s look at the typical landscape!
Most enterprise firewalls (and nowadays personal ones) come with a range of features, which may include:
- VPN Services
- Cloud Management
- Cloud Backup
- IDS/IPS
- Content Filtering via Protective DNS
For this post we are going to focus on the Cloud Backup scenario. Why? Because this is part of a real world incident, it’s not theory:
The investigation confirmed that an unauthorized party accessed firewall configuration backup files for all customers who have used SonicWall’s cloud backup service. The files contain encrypted credentials and configuration data; while encryption remains in place, possession of these files could increase the risk of targeted attacks.
The files contain encrypted credentials and configuration data…

Well let’s talk about encryption. Until they were compromised, they backups were not fully encrypted, just the ‘key’ parts like credentials.
The credentials may be encrypted with AES-256 using a symmetric key (e.g. a password). This key could be susceptible to brute force!
So we have a configuration file in the hands of baddies which not only would likely leak sensitive information but the credentials are probably symmetrically encrypted with AES-256 or simply if the device was ‘older’ could have been BASE64 Encoded (which is instantly reversible)
This is well, quite bad!
So, if you had your SonicWall firewall backing up the the cloud, it is assumed a threat actor has your configuration and has your credentials.
That’s terrible! We have seen over many years password managers take lax approaches to security and storing many things in plain text. It appears this lesson will be played again and again for some time.
So what should you do? Throw the firewall into the sun? perhaps! but more sensibly you should take the steps outlined by the vendor which includes:
Reset: Reset all 7 credential categories (admin passwords, VPN secrets, API keys, SNMPv3, etc.) on live firewalls. Import SonicWall-provided remediation configs if offered.
Detect: Check logs for IOCs like listed IP addresses (published in the advisory). Use SIEM integration for API anomalies.Long-Term: Disable cloud backups; switch to on-premises or customer-managed encrypted storage. Only Gen 7+ firewalls encrypt credentials at AES-256 level—upgrade if using older models. Risk Note: Even encrypted, these files reveal attack surfaces (e.g., open ports, VPN setups), increasing phishing or exploitation risks.
Medium Term: Consider disabling cloud backups and using an alternative backup method. Or perhaps consider replacing the firewall with something else.. do your due diligence obviously! The appliance world is a murky place!
https://www.sonicwall.com/support/knowledge-base/essential-credential-reset/250909151701590
https://www.theregister.com/2025/10/09/sonicwall_breach_hits_every_cloud
Exposure
We can’t see inside SonicWalls firewall backup vaults (The criminals could though!) but we can take a look at the internet using Shodan!
The search: http.favicon.hash:631108382
https://www.shodan.io/search?query=http.favicon.hash%3A631108382
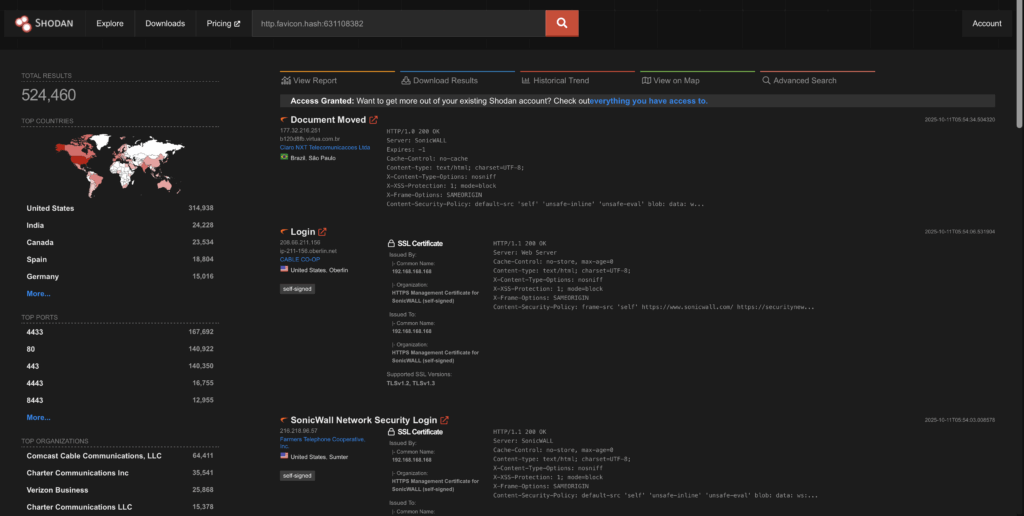
There’s over 500k exposures!
A Breached
Take this with a grain of salt, but I asked GROK to create a table of recently Sonicwall incidents:
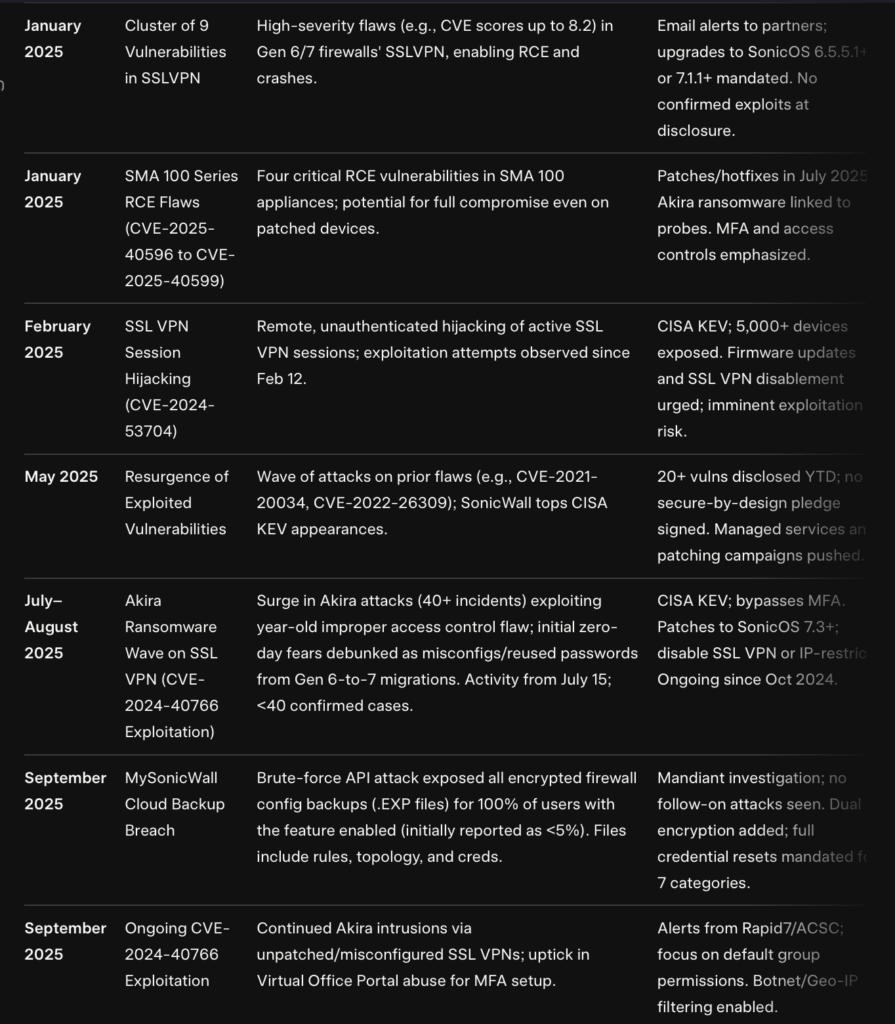
If true that’s a lot larger table than I was expecting! This has ransomware events written all over it! I’m also concerned about the timelines, there seems to have been a bunch of incidents in August. Now… they claim these are related to CVE-2024-40766 but let’s consider this: what if the backups were compromised and they misattributed this to an older CVE? It’s just a hunch, but it seems a bit fishy! There’s even a sort of marketing video about these breaches… it seems a touch odd… I would not be amazed if those breaches were in fact due to the credentials being compromised in the cloud backups….
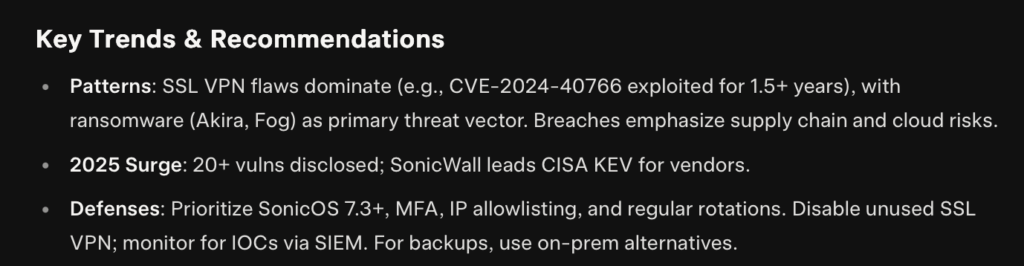
All I can say is, I’m glad I’m running a different firewall, however, I’m going to now go and ask the folks at Unifi how their backups are protected, as I have cloud backups enabled!
Summary
So, as with all incidents there’s a mix here:
- it sucks to be a victim
- it sucks to be a downstream victim
- vendors probably need to do much better with defenses and comms
- risk management is challenging
A key saying we have, is: ‘Criminals don’t hack in, they log in!’ Well that’s not always 100% true, sometimes it’s a combination of both! Or sometimes they log into one system and get credentials for many others, so they log in a lot!
Authentication and Authorization are really really important parts of Cyber Security, but so is credential management (and yes that includes backups!)
Security battles are fought and won in the details (in the weeds as some people say!)! Cyber details matter!
If you have a SonicWall firewall check out the vendor guidance, perhaps check your current state and see where you firewall backups are, and how they are being protected!




