 Education
Education
“Juice jacking” has become a modern cybersecurity myth — a catchy scare story built on a long-patched Android debugging issue and fueled by viral fear rather than facts. Despite years of warnings, there are no confirmed cases of real-world juice jacking attacks; the cost, effort, and low reward make it an impractical method for criminals. Yet the myth persists because it’s vivid, simple, and scary — everything our brains latch onto. The real danger is not the USB port at the airport, but the distraction such myths create. When people focus on imaginary threats, they waste precious attention that should go toward genuine risks like weak passwords, missing MFA, unpatched systems, and poor backups. So let’s take a bit of a deeper dive into this subject, because by it’s important to understand what to, and what not to focus on in my experience!
Real World Cyber Security in Business
Portfolio management in business is an important capability, so is risk management. We have to understand a lot of things to be able to reasonably conduct a risk assessment in a meaningful manner. Off the top of my head if may look something like this:
- What we have (ASSET)
- Who might be trying to negatively impact us (THREAT)
- How we are vulnerable (VULN)
How someone (THREAT) could use a capability to cause us harm and why (MOTIVE) - What negative outcomes could happen (IMPACT)
- What measures we could put in place to REDUCE/TRANSFER/AVOID/ACCEPT this (CONTROLS)
- What the residual likelihood, probability and impact of these actions would be given the controls (RESIDUAL RISK)
Now given my love for using LLMs these day’s let’s ‘upgrade this’ (it’s also about 0600 so the Robot friends can help here!)
1. What we have (ASSET)
Identify and describe the key asset(s) at risk — such as information, systems, infrastructure, personnel, or reputation.
2. Who might be trying to negatively impact us (THREAT)
Define potential threat actors (e.g., competitors, insiders, hackers, environmental factors) and their possible intentions.
3. How we are vulnerable (VULNERABILITY)
Explain the weaknesses, gaps, or exposures that could be exploited by the threat.
4. How someone (THREAT) could use a capability to cause us harm and why (MOTIVE)
Describe the methods a threat might use to exploit the vulnerability and their motivation for doing so.
5. What negative outcomes could happen (IMPACT)
Outline the potential consequences if the threat successfully exploits the vulnerability — such as financial loss, service disruption, or reputational damage.
6. What measures we could put in place to REDUCE / TRANSFER / AVOID / ACCEPT this (CONTROLS)
List the existing and proposed controls that could mitigate the risk and the chosen risk-management strategy.
7. What the residual likelihood, probability, and impact of these actions would be given the controls (RESIDUAL RISK)
Assess the remaining level of risk after controls are applied to determine if it is within acceptable limits.
To summarise (using chatGPT):
‘The above framework outlines a structured approach to identifying, evaluating, and managing risks that may affect our organization’s assets. It helps ensure that we understand what we have at stake, who or what poses a threat, how we might be vulnerable, and what steps we can take to reduce or manage potential impacts. This systematic view supports informed decision-making and effective risk mitigation strategies.’
this could then be fed into a process of managing risk which may look like the following:
Define Context / Scope
- Identify Assets
- Identify Threats
- Identify Vulnerabilities
- Determine Threat Motivation and Attack Scenarios
- Assess Inherent Likelihood and Impact
- Identify Existing Controls
- Propose Additional Controls / Mitigation Options (Reduce / Transfer / Avoid / Accept)
- Assess Residual Likelihood, Impact, and Risk Rating
- Assign Risk Ownership and Treatment Plan
- Monitor, Review, and Update
Cyber/Security/Risk is never one and done!
Now that we have some idea about how to think about risk, how to combine a range of intelligence outputs and how to contextualise and model, we can get back to the ever so important task of talking about juice jacking! The threat people make strange faces to in YouTube ‘influencer’ clips in the name of ‘awareness’ (awareness = clicks/likes/money probably!)
🧃 What is “juice jacking”?
“Juice jacking” refers to a supposed cyberattack where a hacker uses a public USB charging port (like at an airport or café) to install malware on your phone or steal your data when you plug in to charge.
The name comes from:
- “Juice” = power
- “Jack” = plug in
So, the idea is: you plug into a malicious USB port → malware is transferred → your device gets compromised.
Cool right, and look I’ve got a cool bag of OMG cables and flippers and all the gadgets! Mostly when people talk about Juice Jacking they use a term which was relating to a specific vulnerability with Android Debug, where on really old firmware some androids had ADB enabled so you could just connect to the debug interface and copy all the data. But the term juice jacking now is used by people to largely talk about the idea of HID attacks (which is oh so confusing to me! because they are two different attacks, oh well!)
so why is this a bit of a myth?
- Juice jacking was an ADB vulnerability in android smart phones that was fixed by vendors in 2016
- Modern firmware doesn’t allow this
- The feasibility of installing implants to public chargers is not very high
- The cost to attacker is high
- The effort for the attacker is very high
- The likely return to the attacker is low
- If we flip this to HID attacks the payload has to be keyed to the target, currently there’s no automatic payload target detection in HID attack devices
- Even if you do execute this, HID attacks are really hard (In my experience) to pull off given the number of variables at play with the target device
- There’s never been a public reported case of this, ever!
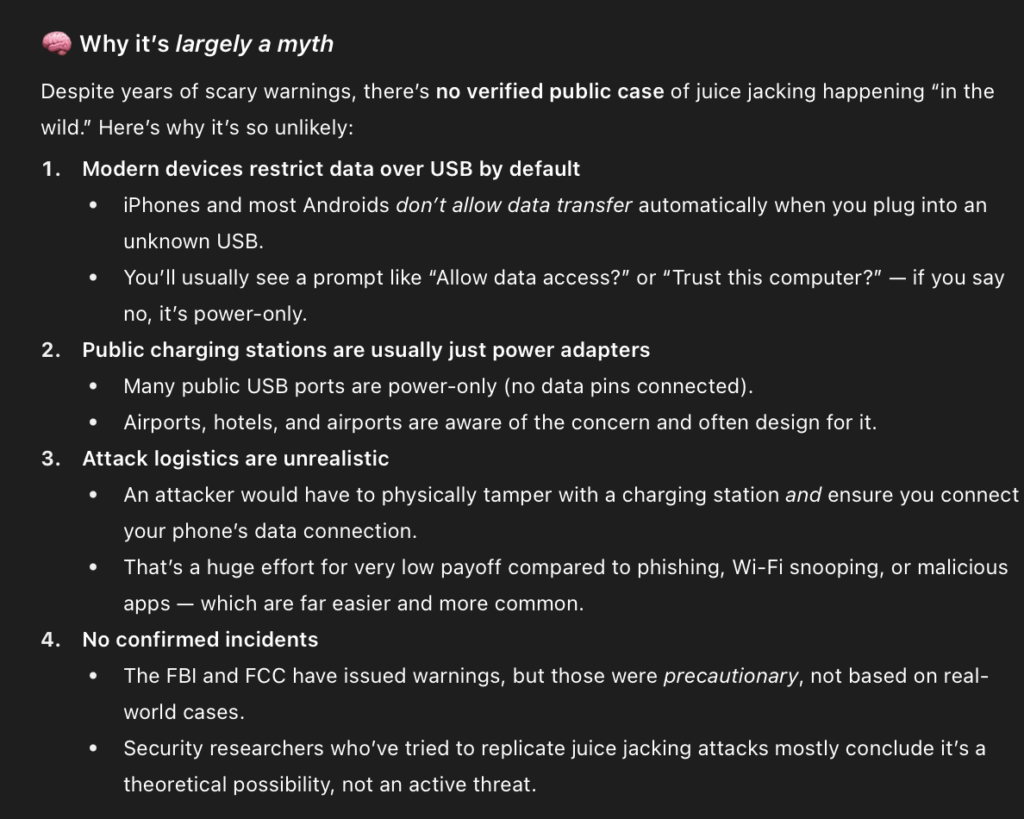
Some ChatGPT generated history of Juice Jacking with ADB:
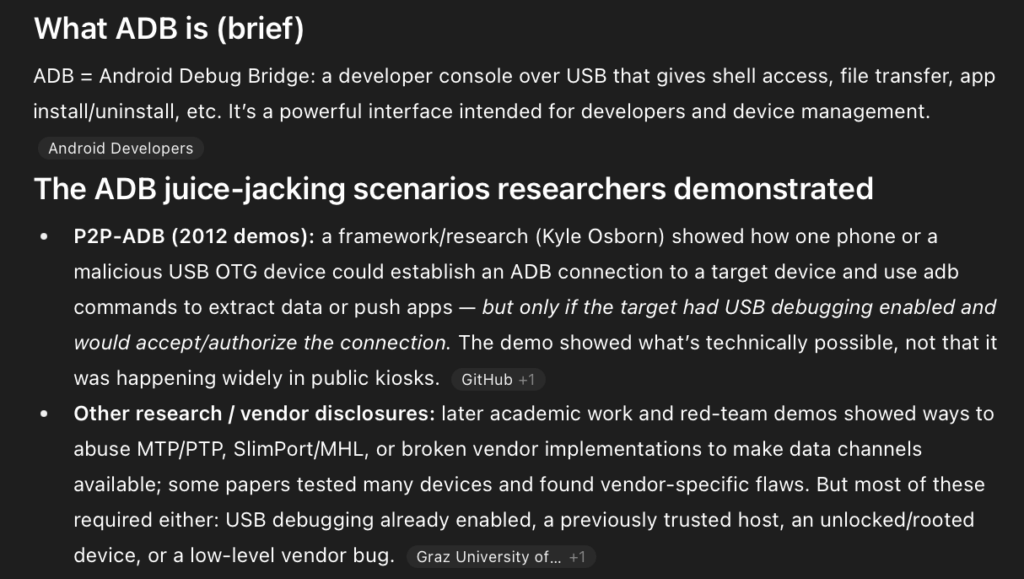
Model for Estimating Likelihood of Being Juice Jacked
To calculate the likelihood of being juice jacked (a cyberattack where a public USB charging port is tampered with to steal data or install malware on a device), I’ll use a quantitative probabilistic model based on the available data. The model incorporates the key factors you specified: reported police/court cases of deployments in the wild (as a proxy for actual incidents), world population, number of public charging points (focusing on USB ports for mobile devices where possible), and cost/effort for the attacker (which influences the plausibility of widespread deployment).
Important note: After extensive searches across web sources, including police records, court cases, cybersecurity reports, and news articles, there are 0 confirmed reported police or court cases of juice jacking deployed in the wild. All sources (e.g., Wikipedia, Ars Technica, Snopes, Krebs on Security, FCC, FBI, and LA District Attorney’s Office) consistently state that no credible, documented instances exist outside of research demonstrations or theoretical proofs-of-concept. Warnings from authorities like the FBI (2023) and LA DA (2019) were precautionary PSAs, not based on actual cases, and follow-up inquiries confirmed “no cases” on record. This means the model will reflect an empirical likelihood of 0, but I’ll also provide an upper-bound estimate to account for potential underreporting while adhering to your requirement to only use reported cases (i.e., treating unreported as unsubstantiated).
Step 1: Data Inputs
- Reported police/court cases of deployments/victims: 0 (no confirmed instances since the concept was demonstrated in 2011). Sources describe it as an “urban legend” or “theoretical threat” with no real-world victims in police records.
- World population: Approximately 8.2 billion in 2025.
- Number of public charging points: No exact global count for USB charging ports specifically for mobile devices (searches returned market sizes but not unit counts). Conservative estimate: ~5 million public charging points worldwide in 2025, based on analogous data for public EV chargers (which include USB-compatible stations) as a proxy, since dedicated mobile USB station data is sparse. Mobile phone charging station market value is ~$0.5-6.5 billion, suggesting millions of units if assuming average cost per station of $500-1,000, but this is imprecise. I’ll use 5 million for the model.
- Cost/effort for attacker: Low monetary cost (~$220 for basic hardware like off-the-shelf parts for a tampered cable or station). However, effort is high: Requires technical skills (e.g., embedding malware via Arduino/Raspberry Pi), physical placement in public without detection, data retrieval, and legal risk (e.g., tampering with public infrastructure could lead to vandalism charges). Reward is low (random data from users may not be valuable), deterring widespread deployment. This factor reduces the estimated number of malicious points to near-zero, consistent with 0 reported cases.
- Additional assumptions for quantification:
- Time period: 14 years (2011-2025, since first demonstration).
- Average uses per charging point per year: 1,825 (5 uses/day × 365 days, conservative estimate based on public spaces like airports/malls).
- Total global charging uses over 14 years: 5 million points × 1,825 uses/year × 14 years ≈ 1.28 × 10^11 uses.
- Average public charger uses per person per year: ~1 (conservative; many people never use them, but frequent travelers might use 10+).
Step 2: The Probabilistic Model
I’ll use a simple risk model adapted from cybersecurity threat assessment:
P(juice jacked) = (M / T_c) × V × U
Where:
- M = Number of malicious charging points (estimated from reported cases). Since 0 reported deployments, M = 0. For upper bound, assume M < 10 (arbitrary conservative cap; if more existed, some would likely be detected/reported given media scrutiny).
- T_c = Total public charging points (~5 million).
- V = Vulnerability factor (probability of successful attack if connected to malicious point). Modern iOS/Android devices require user permission for data transfer (e.g., “Trust this device?”), reducing V to ~0.1 (10% success rate, accounting for unlocked devices or edge cases).
- U = User exposure (average public charger uses per person per year, ~1).
This gives per-person annual likelihood. To incorporate cost/effort, we scale M downward: High effort/low reward implies M is negligible (e.g., M adjusted by a deterrence factor of 0.001, but since reported = 0, we keep it at 0 base).
To arrive at the solution:
- Calculate base rate from historical data: Incidents / Total uses over time.
- Adjust for population and per-use risk.
Step 3: Calculations
- Empirical likelihood based on reported cases:
- Total confirmed victims/incidents = 0.
- Annual global risk per person = 0 / (8.2 billion × 14 years) = 0.
- Per charging use = 0 / 1.28 × 10^11 uses = 0.
- Upper-bound estimate (to provide a non-zero quantitative ceiling):
- Assume <10 undetected deployments ever (else reports would exist).
- M < 10 malicious points.
- Fraction malicious = <10 / 5 million = <2 × 10^-6.
- P(per use) = (2 × 10^-6) × 0.1 (V) = <2 × 10^-7.
- Annual P(per person) = <2 × 10^-7 × 1 (U) = <2 × 10^-7 (or 1 in 5 million).
- Over lifetime (assume 50 years of device use): <1 × 10^-5 (1 in 100,000).
- Adjusting for cost/effort: High barriers reduce M further by ~100x (e.g., few attackers bother), so adjusted upper bound P(per person per year) < 2 × 10^-9 (1 in 500 million).
Step 4: Interpretation
- Based strictly on reported police/court cases (0), the likelihood is 0. There are no known deployments in the wild to base a positive probability on.
- Even in an upper-bound scenario, the risk is extremely low (<1 in 500 million per person per year), far below common threats like phishing. The high cost/effort relative to reward explains why no cases are reported—attackers prefer easier methods.
- Limitations: Underreporting is possible, but your instructions limit us to reported cases. Charging use estimates are proxies due to lack of precise data on mobile USB ports (EV data used as benchmark).
This model shows the threat is negligible based on evidence. If you provide more specific assumptions (e.g., your personal charger usage), I can refine it.
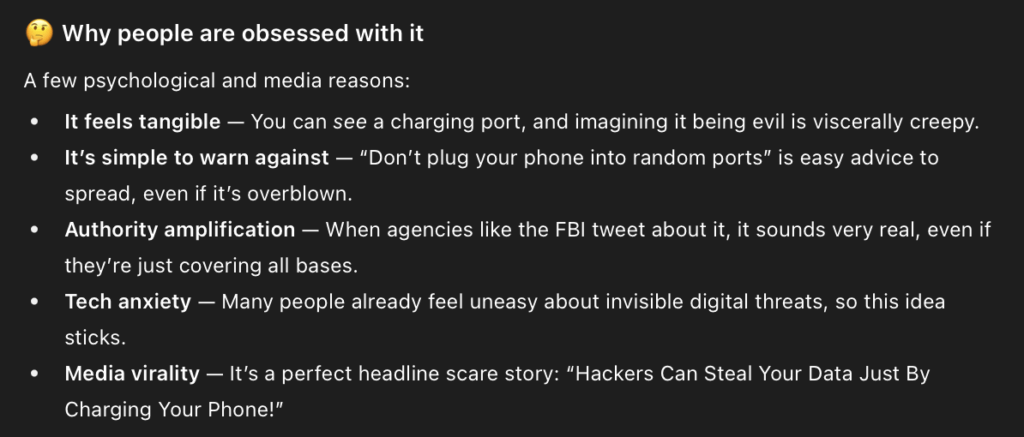
Why are people obsessed with this?
Honestly, because we all love magic and fantasy, the problem comes though is when we let magic and fantasy/fantastical rule out thinking… more on this in a minutes, but here’s what ChatGPT came up with:
Why is this a problem? You may argue it’s not, some people say ‘awareness’ is important, using this is helpful…. I would argue that’s not true. So, apparently does ChatGPT (clearly you can probably prompt anything you want but I’m doing one shot lazy prompts here!)
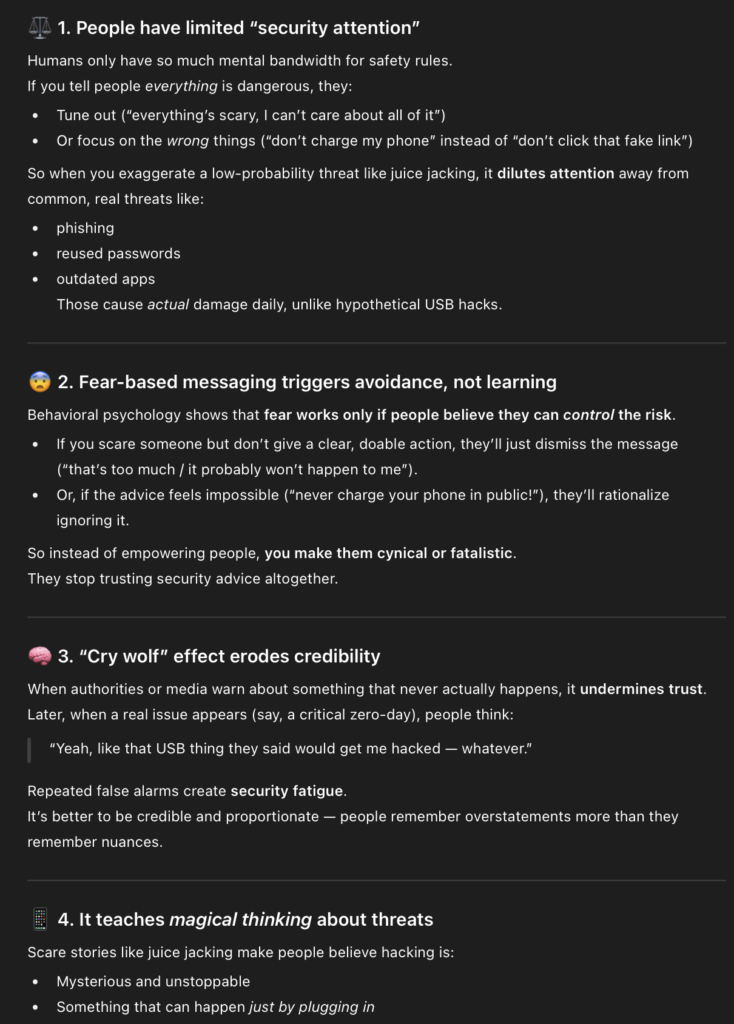
so I think this summarise it quite well:
Using “juice jacking” as a scare tactic to promote cybersecurity awareness is counterproductive because it exploits fear rather than understanding. People have limited attention for safety advice, and exaggerating rare or imaginary risks diverts focus from real, everyday threats like phishing or weak passwords. Fear-based messages without clear, achievable actions cause anxiety, cynicism, and ultimately apathy — a “cry wolf” effect that erodes trust in future warnings. Since humans respond better to credible, controllable, and relatable risks, effective awareness campaigns should emphasize realistic scenarios and empower users with simple, actionable steps instead of fueling superstition or helplessness.
We call this the ‘So many F’s to give’ model!
Our jobs in cyber security are to help people be safer in the digital world, which if you are a practitioner you will likely understand when I say that’s hard enough when we talk about credible, actual, likely threats. When we throw in magic, people literally just give up. I’ve watched this many times when talking to people about personal and organisational security. They get overwhelmed and go into shutdown/do something else mode.
So there you have it, some risk theory, some history, some psychology and hopefully some fun but educational understanding of why I talk about this subject! I talk about it to show what not to care about, so that when we get into the things like:
- Poor credentials
- Lack of MFA on internet facing services
- Poor/Slow/Non Exsistant Edge Device Patch Management
- Lack of segmentation
- Domain joined backups/Lack of backups/recovery
- Poor asset management
- and more
you have time and willing to focus on these! Because these are some of the vulnerabilities that real criminals will probably try and exploit!








