 Defense
Defense
Vulnerability Information
| Rating | Critical |
| CVE | cve-2022-26809 |
| MITRE | CVE – CVE-2022-26809 (mitre.org) |
| CVSS | CVSS:3.1 9.8 |
| Impact | Remote Code Execution (RCE) |
| Exploit in the wild | Currently not observed |
| Difficulty to Exploit (if PoC available) | Very Low |
| Network Position | TCP/IP Routable or Network Adjacent |
| Authentication Required to Exploit | No |
| Affected | Windows Client/Server OS |
| Typical Service Ports | TCP 135,139,445 |
| Vendor Patch Available | Yes |
| Exploitable in Default OOB (out of the box) configuration | Unknown |
| Exploitable Client/Server | Believed to be client and server side exploitable |
Vendor Information
Global Internet Exposure (RPC)
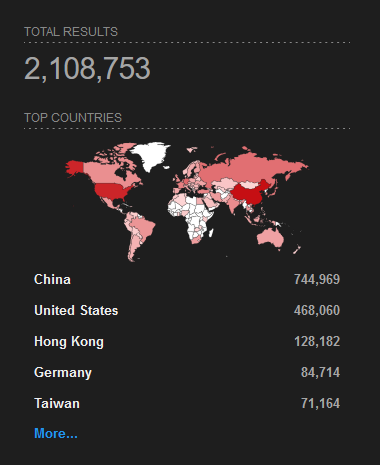
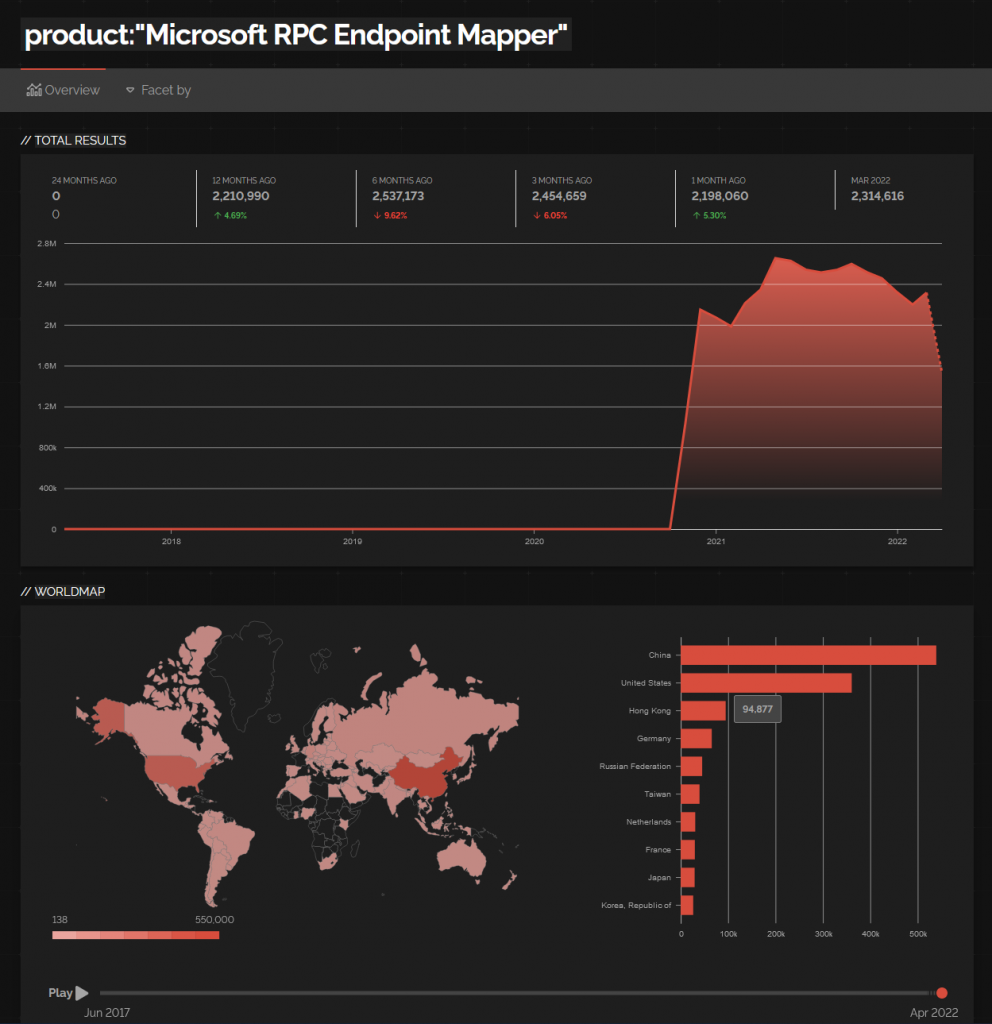
Guidance
- Ideally patch affected Windows Servers and Clients
Mitigation
- Ensure RPC is not exposed to the internet
- Restrict ingress network services that allow RPC (this could cause loss of availability)
- Restrict service based on role
- Restrict ingress services to specific segments/scopes e.g., use Windows Firewall to allow PAWS to connect via RPC for remote admin activities. Clearly consideration should be made for roles such as:
- Domain Controllers
- File & Print Servers
- Other services relying on RPC to operate
- Consider preparing a break glass GPO with restrictive host-based firewall rules allowing PAWS access)
Unknowns
- Does this affect RPC over HTTP?
Network Scanning
There’s no specific vulneability checker at present you could:
nmap -sV -p 135,139,445 -vvv -T4 -A --open 192.168.0.0/24RPC Dynamic Scan with XML HTML Report
Fast
nmap -Pn -sV -sC -p 135,139,445,49152-49160 -v -T4 -O -oA rpc-report --open --stylesheet https://raw.githubusercontent.com/honze-net/nmap-bootstrap-xsl/master/nmap-bootstrap.xsl [TargetIP/CIDR]Full Dynamic range
nmap -Pn -sV -sC -p 135,139,445,49152-49160 -v -T4 -O -oA rpc-report --open --stylesheet https://raw.githubusercontent.com/honze-net/nmap-bootstrap-xsl/master/nmap-bootstrap.xsl [TargetIP/CIDR]
nmap -Pn -sV -sC -p 135,139,445,49152-65535 -v -T4 -O -oA rpc-report --open --stylesheet https://raw.githubusercontent.com/honze-net/nmap-bootstrap-xsl/master/nmap-bootstrap.xsl [TargetIP/CIDR]or use WIRM or other tool to check for the required patch
Common RPC Ports
RPC Control TCP PORTS (WINDOWS)
135
139
445
Dyanmic RPC TCP range
49152-65535
Common Dynamic Ports In Use
Common RPC
49152
49153
49154
49157
RPC Information
Remote Procedure Call (RPC) dynamic port work with firewalls – Windows Server | Microsoft Docs








