 Leadership
Leadership
Everything is fine until it’s not
I’ve been travelling to different organisations and visiting different networks for a while and whilst each organisation is unique (they really are) their operating models, technology challenges and weak security postures generally aren’t as unique as the organisational itself.
One thing that does spring to mind however is that there is a massively common pattern we find with organisations.
- Those that invest well have better postures, better technology experiences and an improved security posture.
- Those that don’t historically invest well, well they have quite the opposite:
- They don’t train staff
- They have very weak postures
- They carry an extraordinary volume of business risk
One thing that is common though, is that all of this tends to link to financial investments, so executives and boards usually have some idea if they are spending or not in this space, what they commonly don’t have a good view on is they getting what they “thought they were buying”. Sadly, too often what they assumed was “in the box” with the “IT provision” with regards to quality and cyber security just simply isn’t the case. Everything is fine, until you look… then it’s less than fine! So, what can we do about it?
Security programs
There are a range of activities and associated cost of running a digital service. All of these should be familiar to people, however in practise we often find budgets (if these even exist) are missing key elements. Some of these are simply the “cost of doing business” in the modern world, others are things that will set you apart from your competition.
Security Program Activities
|
Activity |
Minimum Frequency |
Phase |
|
Cyber Security Strategy Review |
Yearly |
Identify |
|
Cyber Security Budget |
Identify | |
|
Cyber Security Review/Audit |
Yearly |
Identify |
|
Cyber Security Policy Review |
Yearly |
Identify |
|
Cyber Security Process Review |
Yearly |
Identify |
|
Supply Chain Audit |
Yearly |
Identify |
|
Attack Surface Review |
Quarterly/Continually |
Identify |
|
Cyber Security Accreditation |
Yearly |
Identify |
|
PCI DSS Submission |
Yearly |
Identify |
|
Backup and Recovery Testing |
Yearly |
Respond & Recover |
|
Incident Response Tabletop Exercise/Crisis Response Management Training |
Yearly |
Respond & Recover |
|
Incident Response Drills |
Quarterly |
Respond & Recover |
|
Cyber Security Awareness Training (User Base) |
Quarterly/Yearly |
Identify |
|
Specialist Cyber Security Training (Technical Staff) |
Yearly |
Identify |
|
Disaster Recovery Testing |
Yearly |
Respond |
|
Vulnerability Assessments |
Quarterly or in line with Rate of Change |
Identify, protect and detect |
|
Penetration Testing |
Yearly or inline with Rate of Change |
Identify, protect and detect |
|
Purple Team Exercises |
Yearly |
Identify, protect and detect |
|
Red Team Exercises |
Yearly |
Identify, protect and detect |
|
Secure Erase/Secure Disposal |
In line with equipment disposal |
Protect |
|
Cyber Security and Compliance Public Facing “Pack” Publish/Review |
Yearly |
Enable |
As you can see this is just the bread and butter of normal activity baseline that organisations “should” be doing. The reality is that many organisations do not do these, they limp along in an inefficient (higher cost, lower return) model, where the lack of these activities often leads to the following outcomes:
- Increased complexity
- Increased risk
- Competitive disadvantage
- Higher cost of technology management
- Increased compliance costs
- Loss of deals through being unable to demonstrate digital security capabilities
- Loss or reduction in customer confidence
- Increased incident frequency and increased incident impact
The key thing is that a weak security posture usually aligns with a low maturity digital capability maturity, the net effects of this over a multiyear period are commonly what could be described as toxic technology investments.
Cyber Security Operational Activities
Let’s also not forget security business as usual (BAU) activity which your organisation should be conducted as part of its daily business and cyber security operations activities, these include:
- Cyber Security Monitoring
- Threat Hunting
- Alert Response and Triage
- Incident Response
- Vulnerability Management
- Vulnerability Treatment
- Patching
- Cyber Security Engineering
- Research
- Training
So to answer the why?
Answering the why is difficult as a generalisation, however I’ve tried to use a model which I named “cyber inhibitors” to try and show some though processes as to WHY.
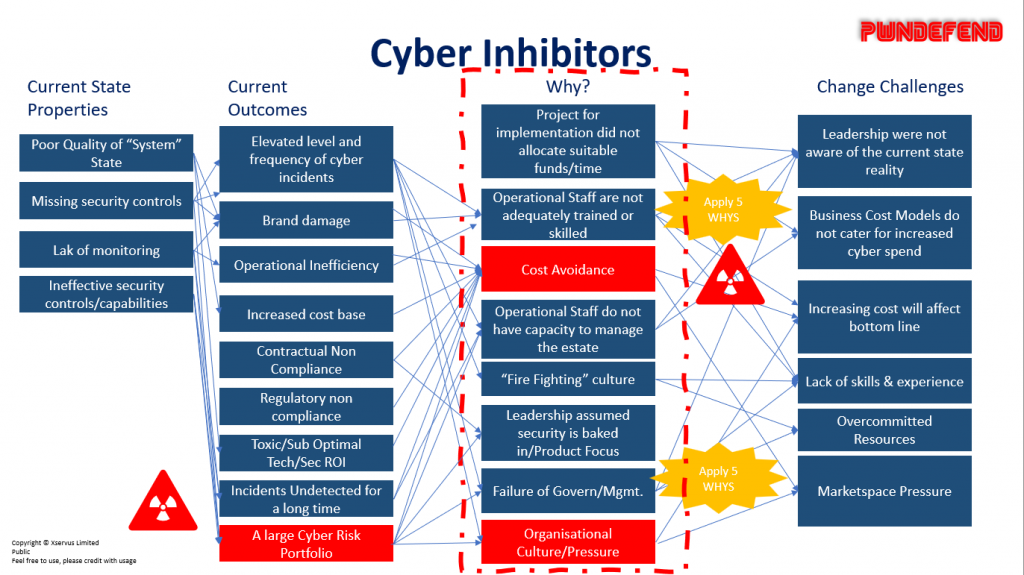
Each organisation will have it’s own views, risk appetites, tollerances and contraints. It’s important to not take the reality (most orgs ~80-90% are in the same position today!) as a kicking, it’s just a fact that technology has been deployed by the human race with a faster, cheaper and at ANY FUTURE cost model for a long time. I do however see this changing, I also forsee future legal and regulatory requirements as the potential impact of nagative cyber consequences to both countries and organisations is increasing.
Summary
Digital platforms are key to operating a business, they aren’t “nice to have’s”, most organisations will struggle to operate without access to information systems for a short period of time, order processing, sales, marketing activities, customer engagement and business operations in mot organisations rely upon access to an organisations information system. Even if your risk appetite and tolerance accept some loss of confidentiality and integrity, availability of digital systems is a key demand and requirement from most organisations to function.
You wouldn’t want your family being driven round in a car with faulty brakes and damaged seatbelts etc.…. So why would you not look after your digital ones?
The reality from my point of view is that “we don’t suck” at cyber, we have lots of the answesrs, lots of the solutions, lots of motivated people with good skills, what we have however failed to do is integrate this into the normality of businness technology deployment and management. So we have good cyber brakes and seatbelts, they just seem to often be stored in a warehouse. What we need to do is actually deploy them!









