Defense
Defense
Would you know if these remote access tools were…
Introduction
Remote management and monitoring (RMM) and other remote access solutions are fantastic for enabling remote support of environments. Like most things in life though the intent of the user changes the tool from a force for good to a weapon of evil (I hate the use of the word weapon with software but it’s a blog so I’ll self-cringe).
Kill Chain Summary
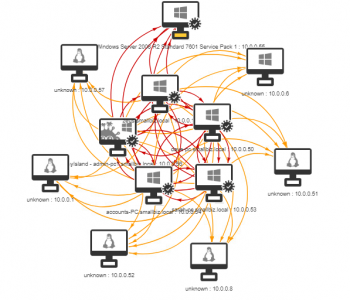
The kill chain in the attack outlind by sophos isn’t one that you will be suprised at:
- Initial access was via a known software vulnerability (unpatched Exchange server)
- The attackers dropped a web shell
- The attackers had SYSTEM level access
- The attackers dumped memory to obtain hashes
- The hashes were cracked (they escalated to domain admin)
- 7 (yes seven!) backdoors were implaneted into the target network (hence this blog post)
- Lateral movement was made to domain controllers
- Large volumes of data were exfiltrated
- The rest of the environment was then pwn3d
What might shock you more is the speed at which this was conducted. It’s not months or weeks, it’s hours and days (see the Sophos blog for more details!)
Conti Actors Remote Access Toolkits
Remote access tools being abused isn’t a new thing but following a great writeup (https://news.sophos.com/en-us/2021/09/03/conti-affiliates-use-proxyshell-exchange-exploit-in-ransomware-attacks/?cmp=30728) of a Conti kill chain from Sophos Labs I figured I’d try and raise more awareness of some of the threats that organisations face, and the reality that defending against all threats is actually quite difficult for a lot of organisations (hell it’s technically not simply for anyone!) Read more “Would you know if these remote access tools were being used in your network environment?”