 Guides
Guides
Introduction
Ever needed to test active directory in a hurry? Well, here’s some common commands to test active directory domain services. In this post today we are going to focus on DNS and username enumeration, there are however a range of weaknesses you want to look for:
- SMB Null Session/Guest Access
- LDAP Null Bind
- Sensitive Information Disclosure
- Weak Password Policies
- Unpatched Software Vulnerabilities
Active Recon
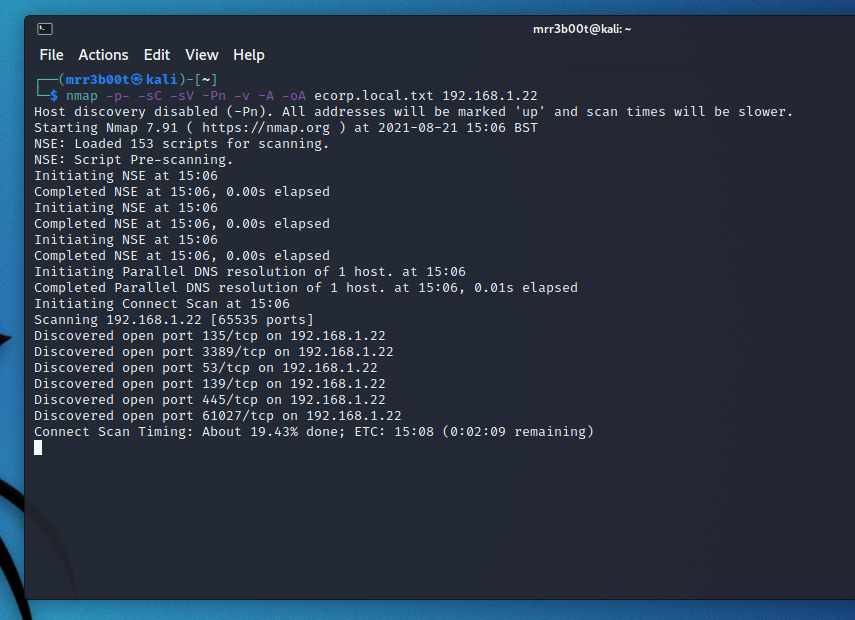
Port Scanning and Service Fingerprinting
nmap -p- -sC -sV -Pn -v -A -oA ecorp.local.txt 192.168.1.22
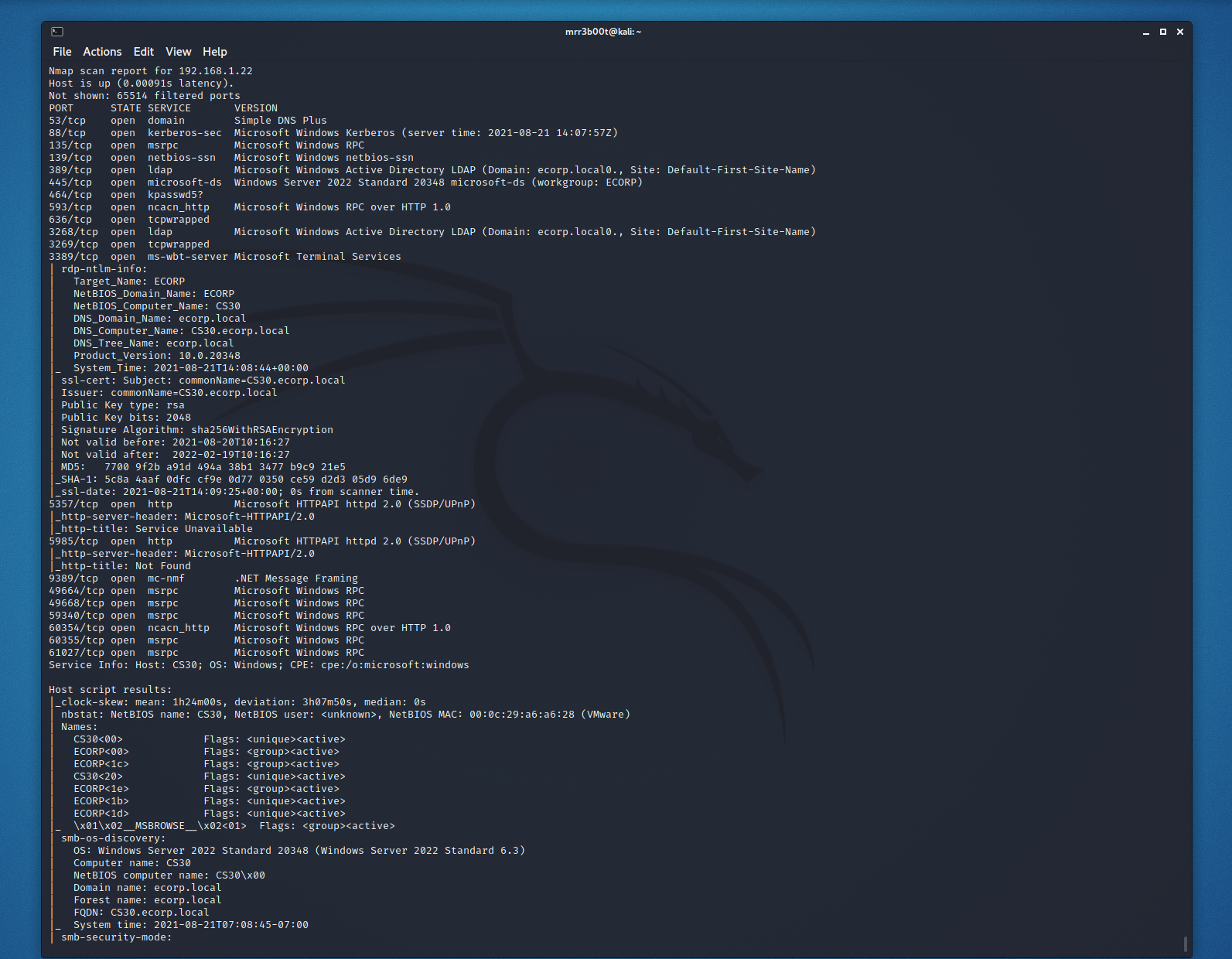
Domain Name and Domain Controller Enumeation
The server leaks the domain name as we can see here:
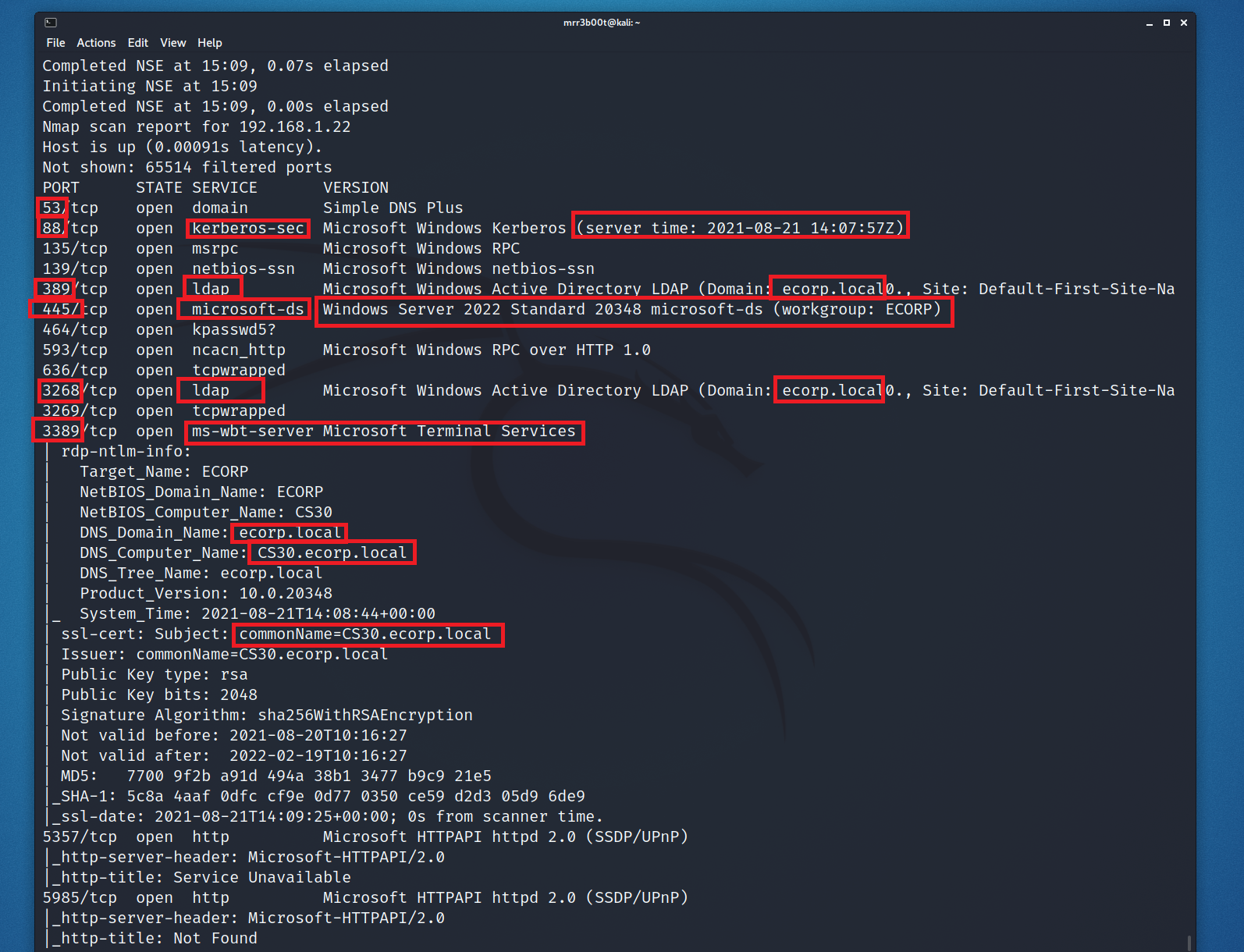
Here we are looking for key information:
- Services which indicate a domain controller.
- Domain name information
- Identification of additional service
- If the server is a global catalogue server
Name Resolution
Connect to the name services and check for reverse and forward lookup zones:
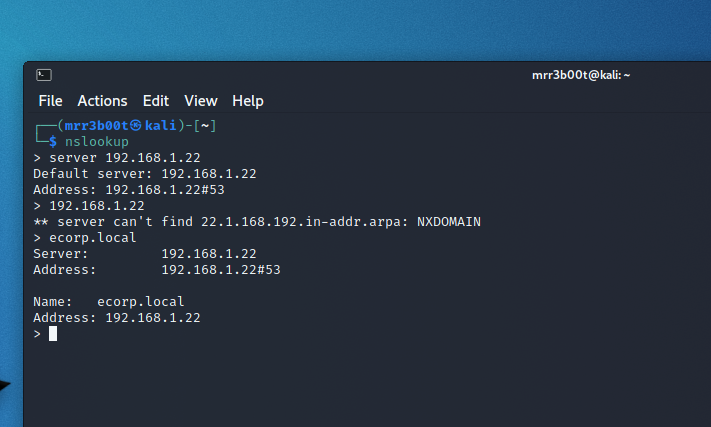
In this example we can see that the server does not respond to a reverse lookup request but does to a forward request. It is likely that the server is authoritative for this domain namespace.
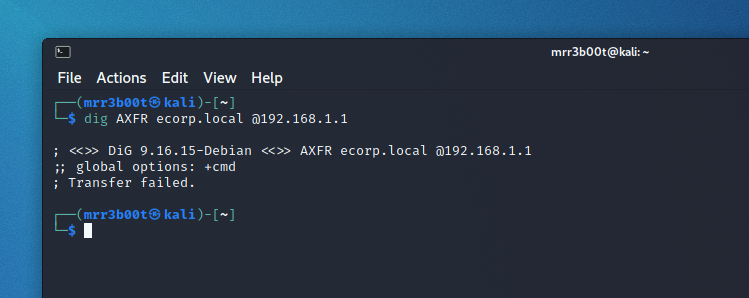
Zone Transfer
Attempt a zone transfer with DIG:
Active Directory Null Bind
Now we are going to attempt a NULL bind on LDAP (please not you can’t run active directory without this port/service being exposed, AD uses LDAP and LDAPS by default on modern Windows Server editions)
ldapsearch -h 192.168.1.22 -p 389 -x -b “dc=ecorp,dc=local”
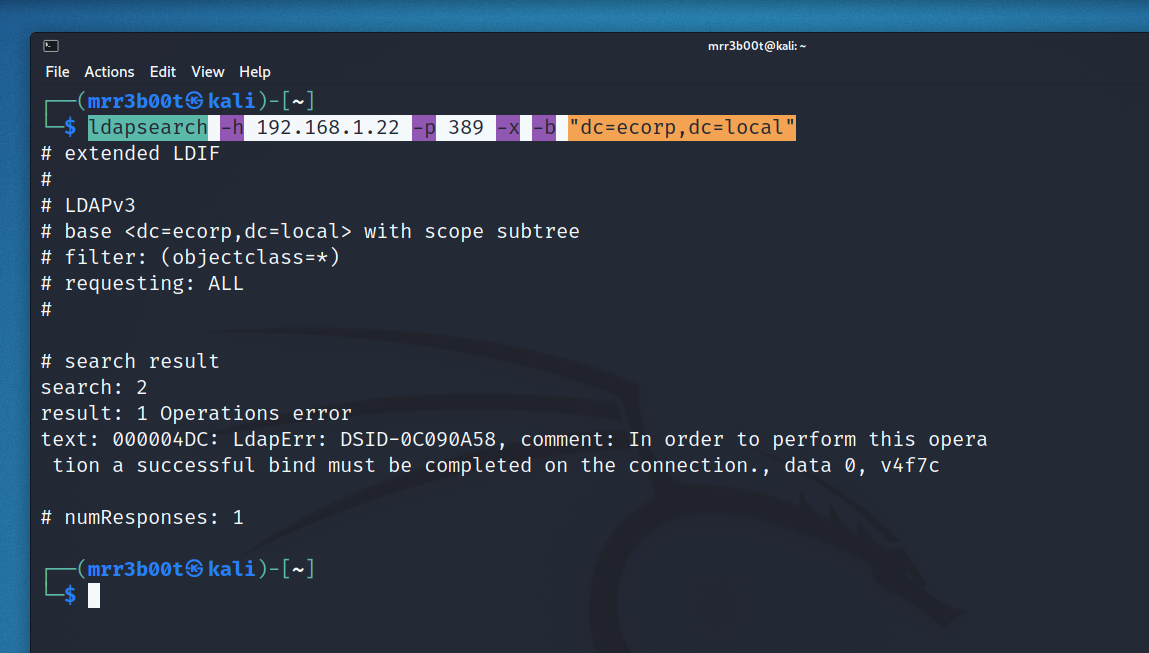
In modern domains NULL bind is disabled by default (it takes a bit of work to enable this. In server 2000 it was enabled by default)
Here we will show an authenticated example:
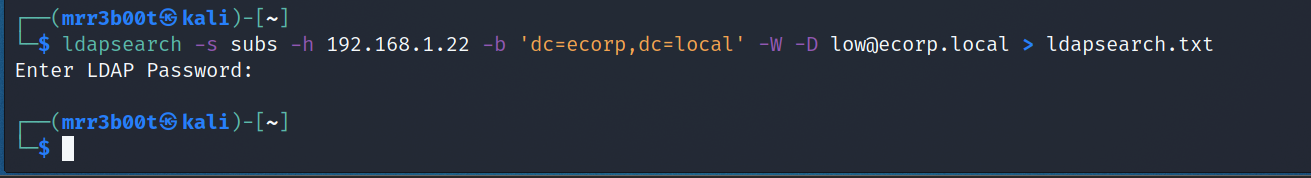
ldapsearch -s subs -h 192.168.1.22 -b ‘dc=ecorp,dc=local’ -W -D [email protected]
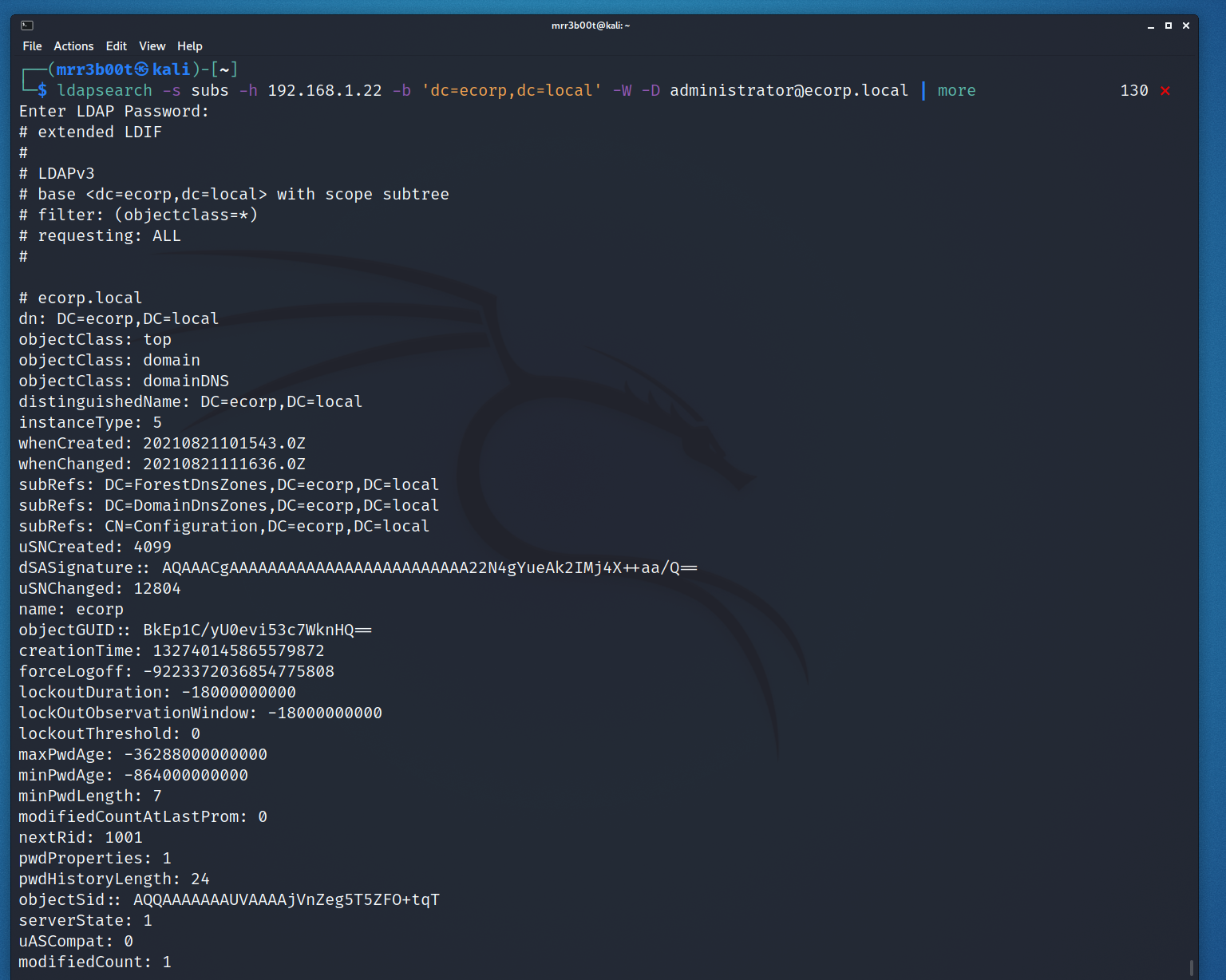
We authenticated using the domain administrator.
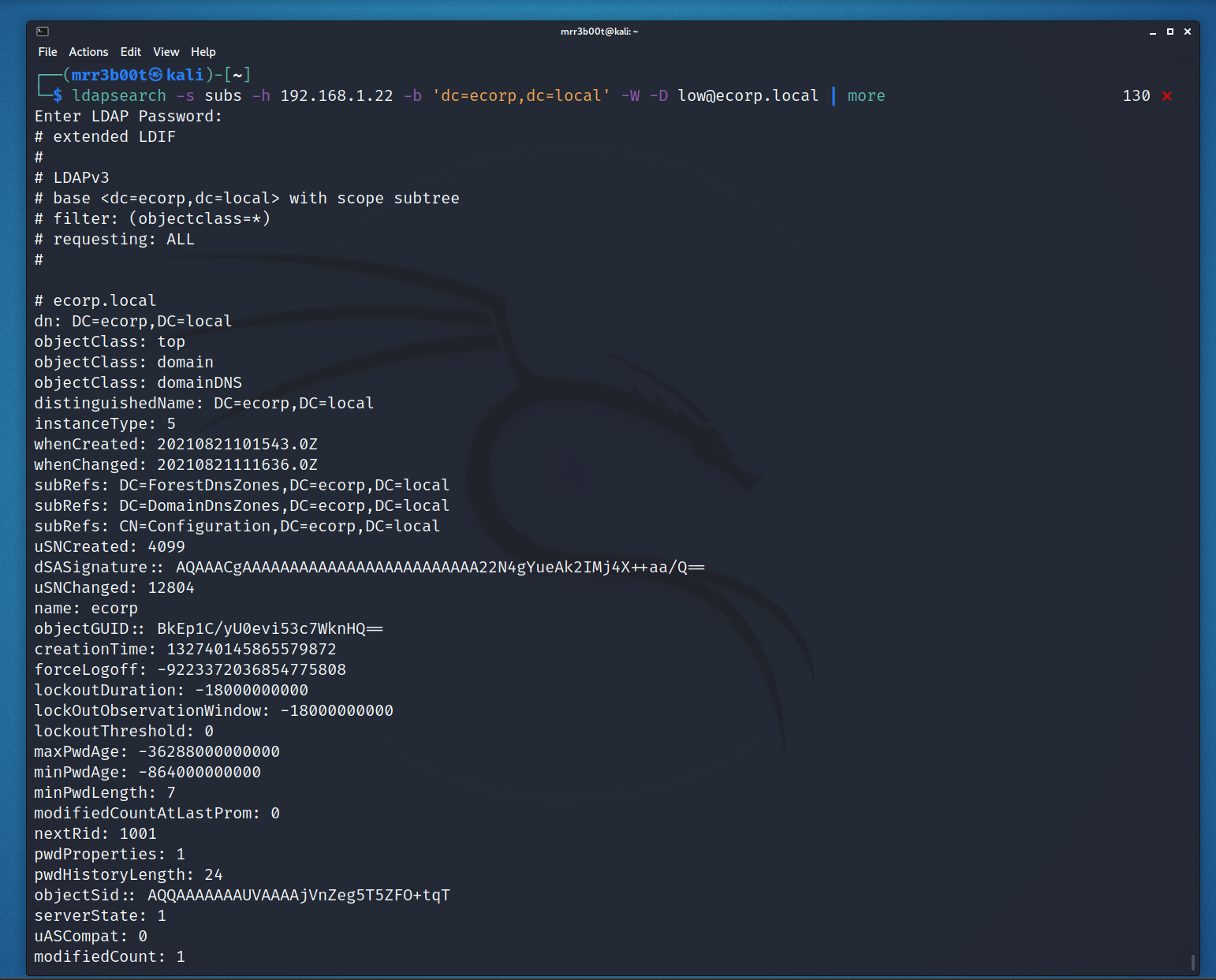
Here we show authentication using the user ‘low’ (a member of domain users and users)
Now we can craft specific searches here if we want or we could grep the output. Here we search only for user objects:
Ouput to a file
Or we can search for only user objects etc.
ldapsearch -s subs -h 192.168.1.22 -b ‘dc=ecorp,dc=local’ -W -D [email protected] -W “objectclass=user”
Username Enumeration
SID/RID Cycling
Kerberos Username Enumeration
NMAP
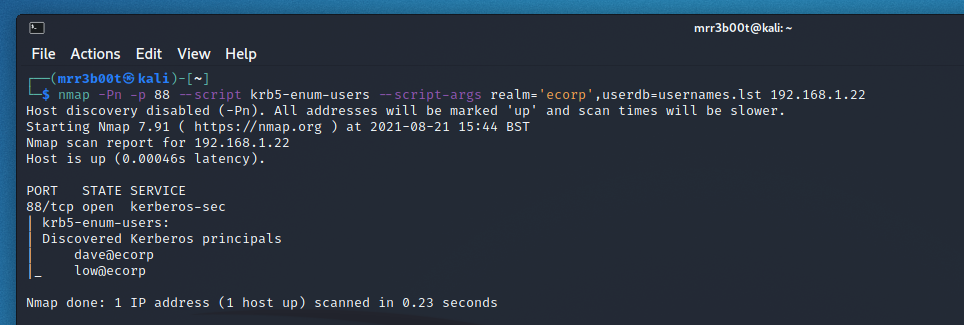
nmap -Pn -p 88 –script krb5-enum-users –script-args realm=’ecorp’,userdb=usernames.lst 192.168.1.22
The base command uses the NETBIOS domain name and a built-in dictionary. We’ve given it a username list.
Now that’s with insider knowledge, let’s try with some honeypot usernames:
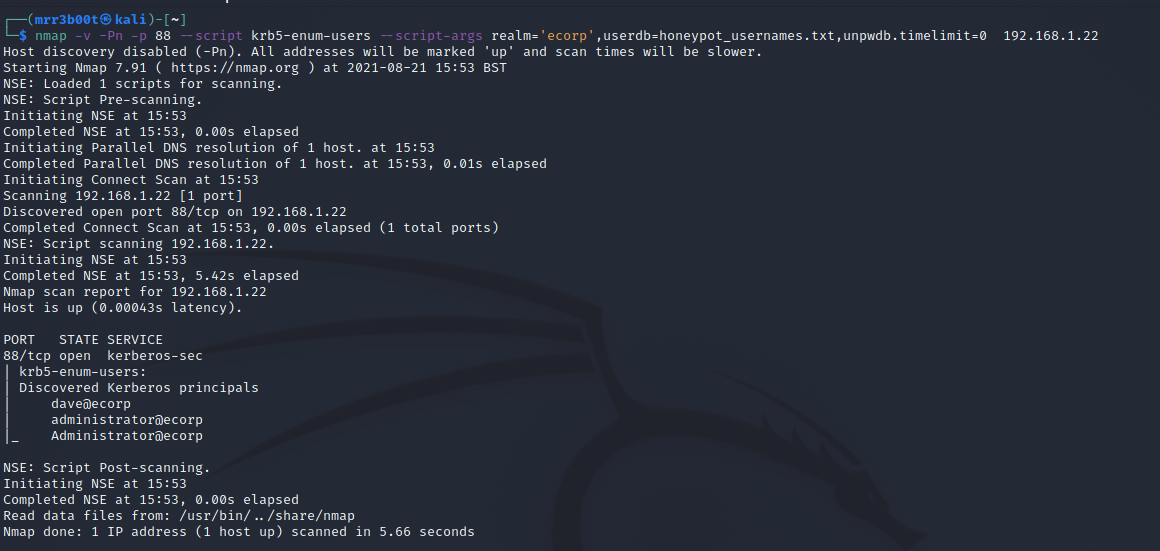
Now remember you will want to do OSINT to get names from the organisation.
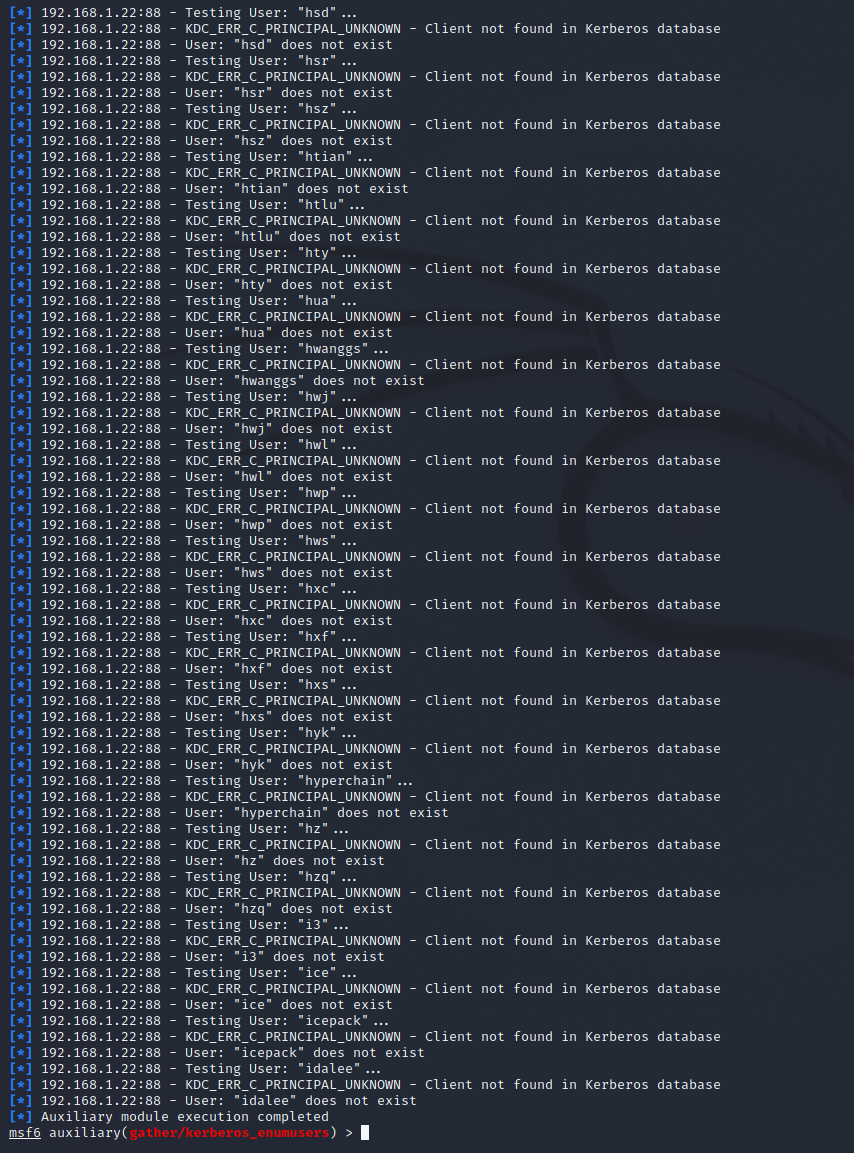
We can also run this using metasplpoit:
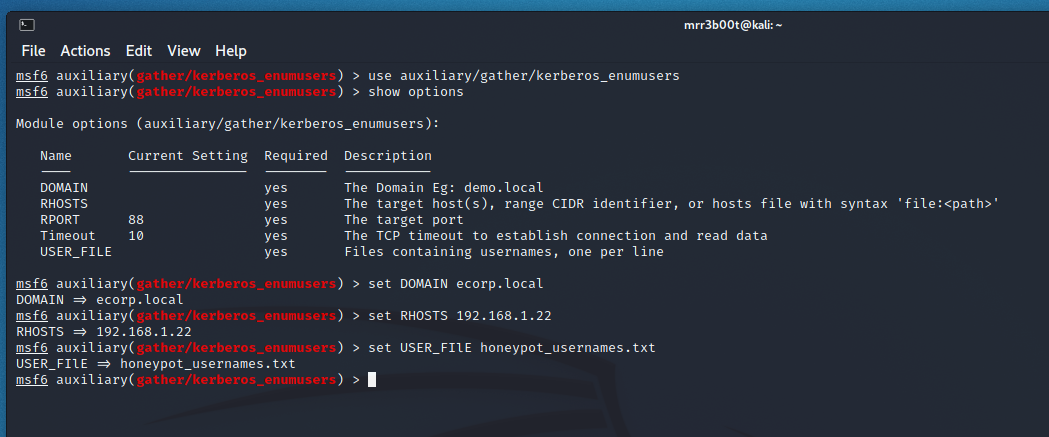
This is slightly more verbose in its output:
You can also perform this via Windows using Kerbrute (and clearly you could use nmap on a Windows machine as well): 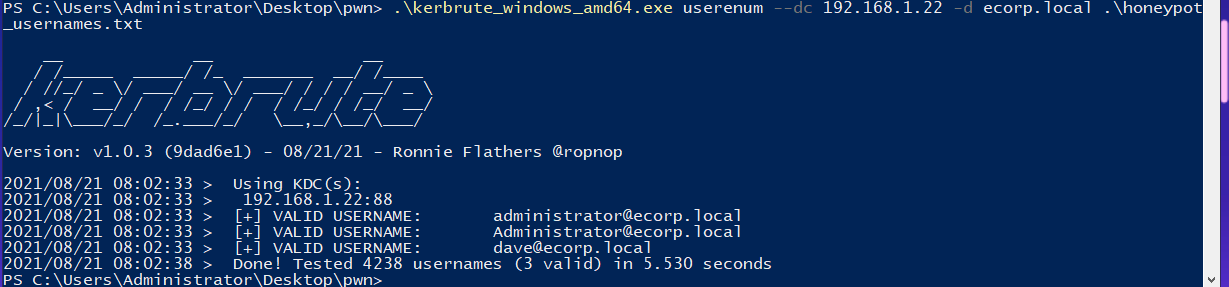
Summary
Here we’ve looked at a range of tools and services to both enumerate the attack surface and to start building up a list of known users. Once we have these, we are going to want to think about attacks we can conduct such as:
- Credential Stuffing
- Credential Sprays
- Brute Force Attacks
These aren’t our only position; we can obviously look at using responder but that is becoming less common these days (MDNS/LLMNR is disabled by Default on modern Windows builds).






