 Defense
Defense
Windows Remote Management is easy if you are using a domain joined machine and have a CA. But what if you are off the domain and you want to connect to WINRM that has an HTTPS listener? (by default WINRM uses HTTP on TCP 5985, you can clearly chop out the TLS related configs in the example scripts and they will work for plain old WINRM)
This is useful from a sysadmin and penetration testing/red team perspective. Now obviously you could export the certificates and import them into your store, however that’s more work. So, let’s look at how we ignore revocation, CA name and Computer Name checks.
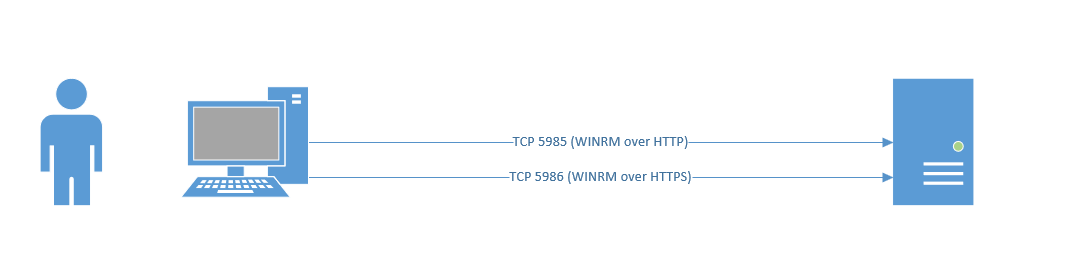
WinRM via HTTPS (self-signed)
Connect to a server where you don’t have the DNS name and you don’t trust the certificate authority
| $creds = Get-Credential
$sessionOptions = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck Enter-PSSession -ComputerName 192.168.1.10 -UseSSL -Credential $creds -SessionOption $sessionOptions |
Run a command (using invoke-command)
| $creds = Get-Credential
$sessionOptions = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck Invoke-Command -ComputerName 192.168.1.10 -UseSSL -SessionOption $sessionOptions -Credential $creds -ScriptBlock {ipconfig} |
Copying Files (upload/download)
Ok this is an important activity; you will want to be able to exfiltrate data but also you might need to drop tools (not everything in the world is executed in memory!)
Create a new PSSession and then use the copy command:
| $creds = Get-Credential
$sessionOptions = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck Enter-PSSession -ComputerName 192.168.1.10 -UseSSL -Credential $creds -SessionOption $sessionOptions new-PSSession -ComputerName 192.168.1.10 -UseSSL -Credential $creds -SessionOption $sessionOptions $session = Get-PSSession #copy to the target Copy-Item -Path C:\users\mRr3b00t\Downloads\7z1900-x64.msi -Destination c:\users\sarah\desktop\ -ToSession $session #copy from the target Copy-Item -Path c:\users\sarah\desktop\7z1900-x64.msi -Destination c:\temp\ -FromSession $session |
Now this is largely going to be useful in a small-scale environment or as a hop position. In a large business environment, you may have a few things being leveraged such as certificate-based authentication and Kerberos for authentication.
https://docs.microsoft.com/en-us/windows/win32/winrm/authentication-for-remote-connections
However, by default a non-domain joined client will use Negotiation (NTLM or Kerberos depending upon which protocols they client and server agree on) it uses a Windows implementation of SPNEGO to determine the authentication type.
Summary
You can connect to WINRM from a windows machine (as per this post) but you can also connect from Linux machines, a common tool from a security testing perspective is a RUBY implementation of WINRM called EVIL-WINRM. System administration activities and toolsets are useful from a range of perspectives, ensuring your attack surface is understood and hardened, well that’s another subject. Hopefull this is useful to understand how to create WINRM sessions, run command, upload/download files and ignore (where appropriate) pesky TLS errors!






