Defense
Defense
Audit NTDS.DIT using DSINTERNALS
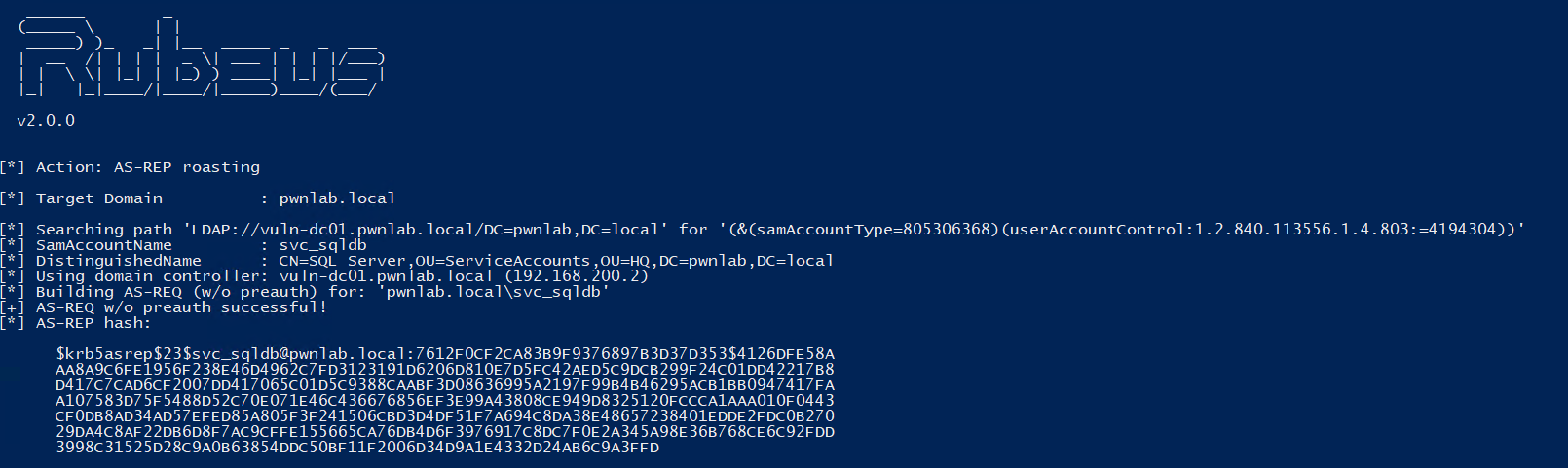
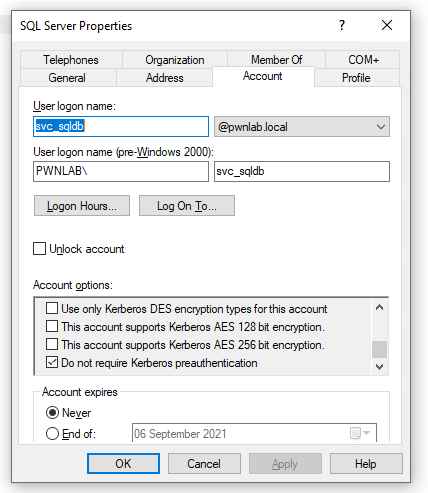
Ok this assumes you know how to get the NTDS.DIT and SYSTEM registry hive out from a domain controller, if you don’t go looking, we might have blogged a few ways to do that! Now then, firstly, let’s Install DSInternals. From PowerShell 5 onwards you can simply run:
|
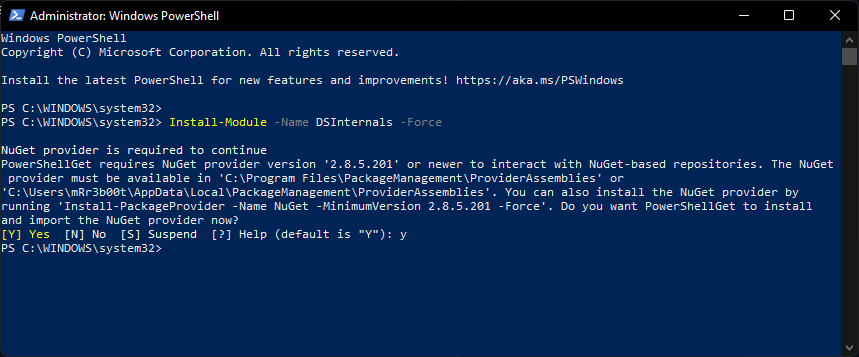
You will likely need to set your execution policy:
| Set-ExecutionPolicy -ExecutionPolicy Unrestricted |
Now to dump the hashes we use: Read more “Audit NTDS.DIT using DSINTERNALS”